Journal list menu
Export Citations
Download PDFs
FEATURED COVER
Cover Image Volume 33, Issue 8
- First Published: 29 August 2022

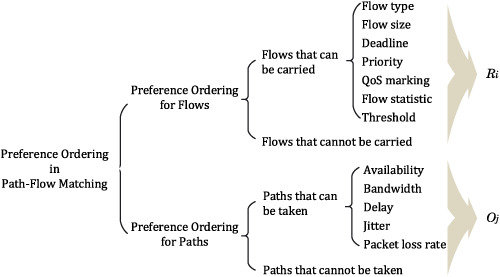
The cover image is based on the Original Article Path-flow matching: two-sided matching and multi-objective evolutionary algorithm for traffic scheduling in cloud data center network by Li-zhuang Tan et al., https://doi.org/10.1002/ett.3809
ISSUE INFORMATION
EDITORIAL
Context aware mobility in Internet of Things enabling technologies, applications, and challenges
- First Published: 15 August 2022
SPECIAL ISSUE ARTICLES
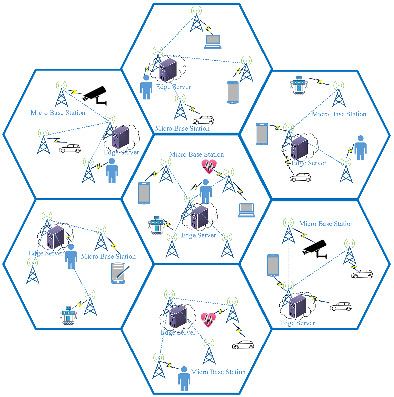
Cognitive Internet of Vehicles and disaster management: A proposed architecture and future direction
- First Published: 02 May 2019
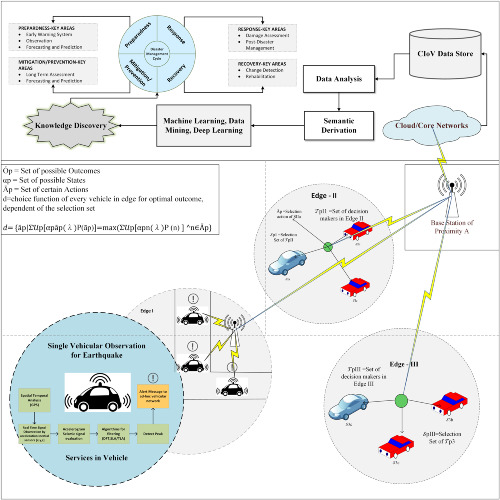
This paper presents Cognitive Internet of Vehicles (CIoV) insights and capabilities by identifying the immense potential of IOV to enhance the ability to learn, understand, and respond without human interaction and use these cognitive abilities to create sophisticated scanning and sensing algorithms and real-time transformation over the respective edge/cloud network for disaster management and recovery.
A privacy-preserving framework for smart context-aware healthcare applications
- First Published: 16 May 2019

This paper is focused on privacy preservation within smart context-aware healthcare emphasizing privacy assurance challenges within Electronic Transfer of Prescription. Based on a thorough analysis of existing models, we propose an enhancement to the widely used Salford model to achieve privacy preservation against masquerading and impersonation threats. The proposed model improves privacy assurance for smart healthcare while addressing unique challenges with respect to context-aware mobility of such applications.
Enhanced time-slotted channel hopping
- First Published: 23 May 2019
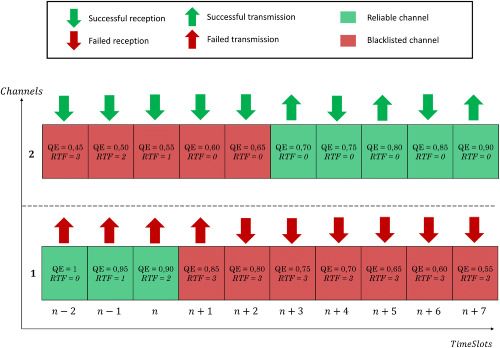
We investigated the external interference problem generated by the coexistence of different wireless technologies in the same spectrum band (2.4 GHz). We proposed a blacklisting technique dedicated to Time Slotted Channel Hopping (TSCH) proposed by the IEEE 802.15.4e standard, to improve the reliability of the network. The technique dynamically blacklists the poor-quality channels affected by the external interference and multi-path fading. We also suggested a new channels' quality estimation technique based on shared links' nature to accurately estimate the channels' quality.
Context-aware cognitive disaster management using fog-based Internet of Things
- First Published: 27 May 2019
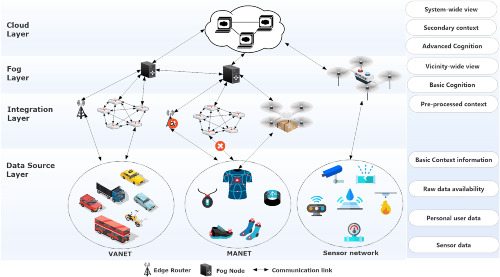
This article analyzes different stages of disaster management systems, and existing IoT solutions are also discussed that are focused on prevention, preparation, response and recovery from disasters. It also proposes a context-aware fog-based IoT architecture to realize a cognitive disaster management system that can learn from the collected and synthesized data to reduce the impact of catastrophic events by taking immediate actions. Furthermore, the significance of the architecture is validated in different scenarios and inherent open research challenges are emphasized.
Clustering-based real-time anomaly detection—A breakthrough in big data technologies
- First Published: 11 June 2019
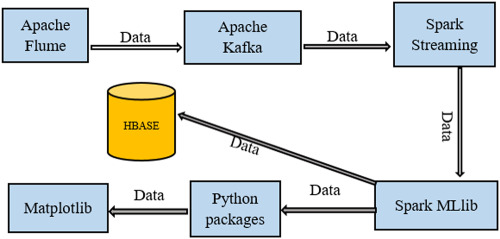
In this paper, an experimental study has been conducted to investigate the accuracy rate, execution time and memory consumption of existing anomaly detection algorithms. A composite clustering algorithm and a novel framework has been proposed based on big data technologies to detect anomaly in real time. The proposed framework which comprises BroIDS, Flume, Kafka, Spark streaming, Spark MLlib, Matplot, and HBase has been evaluated in terms of accuracy, memory consumption and execution time against the existing approaches.
A constrained framework for context-aware remote E-healthcare (CARE) services
- First Published: 17 June 2019
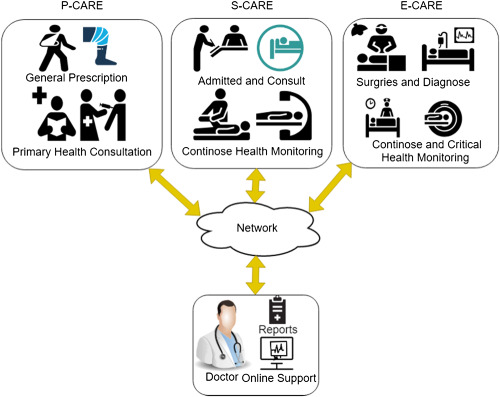
E-healthcare services are categorised mainly into three categories: primary care (P-CARE), secondary care (S-CARE), and emergency care (E-CARE). The result shows that the proposed algorithms for the P-CARE and S-CARE do not make more difference in the routing. However, the selection of the path for the E-CARE shows that the hop count of the path has been increased which leads to an increase the time complexity. Further, major characteristics of the algorithm has been explored and analysed for the E-healthcare services using comparative study with existing algorithms and average qualified service set (QSS).
A Quality-of-Things model for assessing the Internet-of-Things' nonfunctional properties
- First Published: 17 June 2019
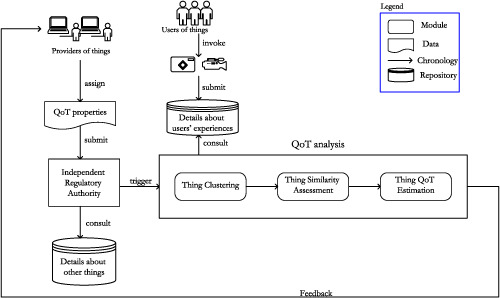
In this paper we present a novel approach for thing selection and recommendation in the context of IoT. The paper first discusses how things' non-functional properties are captured into a QoT model based on the performance of things' duties in the form of sensing, actuating, and communicating. It, then, evaluates how fair the QoT properties' values of things are, so that fair competition between things' providers occurs. Different from other existing QoS prediction approaches, we address the problem of lack of data usage of things-to-evaluate.
A multivariant secure framework for smart mobile health application
- First Published: 06 August 2019
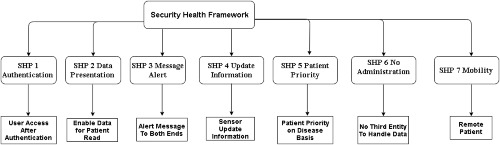
The paper is explaining the concept of Context aware computing in IOT. Further security issues while using the context aware computing for eHealth applications. More Over in this paper we propose a security framework for smart mobile health applications and analyse with existing frameworks in detail.
Towards a trusted unmanned aerial system using blockchain for the protection of critical infrastructure
- First Published: 29 July 2019
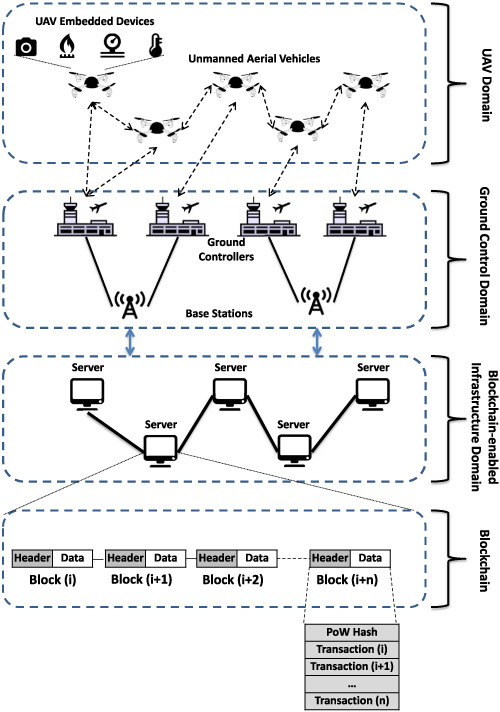
This paper presents a novel BC-based trust management solution for unmanned aerial system(UAS) communication. The proposal named BC-based UAS (BUAS) involves different communicating domains staring from the UAV embedded sensors to the BC. In addition, BUAS is also based on the Bayesian inference (BI) approach,18 which is known to offer high accuracy when estimating a given event credibility.
Smart-city medium access for smart mobility applications in Internet of Things
- First Published: 28 August 2019
Context aware ontology-based hybrid intelligent framework for vehicle driver categorization
- First Published: 29 August 2019
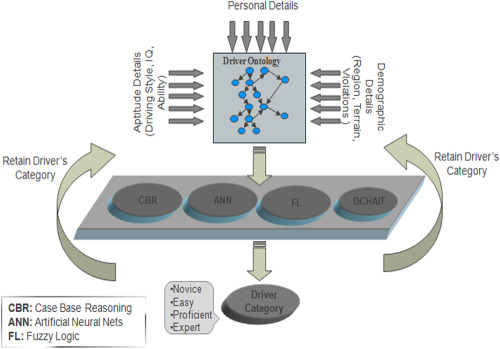
1. Vehicle driver profiling and categorization is imperative for assuring safety of passengers while having an insight to driver's level of expertise. 2. Machine learning-based dynamic and adaptive technique named D-CHAIT is proposed for driver categorization considering implicit as well as explicit characteristics of drivers. 3. Empirical quantifications assert D-CHAIT as a better technique than contemporary ones.
Quality of service in IoT protocol as designs and its verification in PVS
- First Published: 09 October 2019
Unifying Theories of Programming (UTP) semantic framework is used in this paper to provide the design models for the Quality of Service (QoS) levels in the Message Queue Telemetry Transport (MQTT) protocol. Moreover, the design models are encoded in Prototype Verification System (PVS). Some important properties and the refinement relation between QoS levels is proved with the PVS proof assistant
NADEEM: Neighbor node approaching distinct energy-efficient mates for reliable data delivery in underwater WSNs
- First Published: 11 December 2019
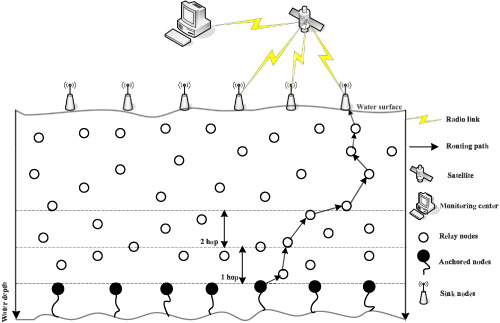
The proposed NADEEM routing scheme considers three metrics (energy, depth and number of neighbors) to select neighbor node and priorities the forwarders for data packets transmission at the destination. The second proposed protocol FA-NADEEM uses backward transmissions to avoid void node. It selects a node which is closest to it in the backward direction and finds route towards the destination. This avoids the void node, however, tradeoff of energy consumption exists. Whereas, the third routing protocol TA-NADEEM adjusts the transmission range of void node adaptively to forward the data packet at the destination successfully.
EDITORIAL
Intelligent resource management in cloud computing and networking
- First Published: 15 August 2022
SPECIAL ISSUE ARTICLES
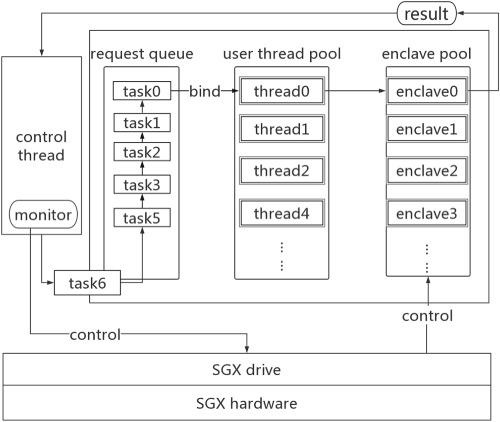
SGXPool: Improving the performance of enclave creation in the cloud
- First Published: 29 August 2019
Detection of multipath routing with passive delay measurements: Hypothesis testing approaches
- First Published: 22 October 2019
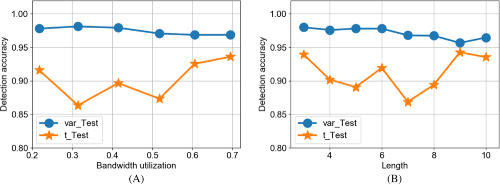
We propose to utilize passive delay measurements between endhosts, to detect multipath routing with two different hypothesis testing approaches, ie, t-Test and variance test. The motivation is that the obtained distributions of passive delays between end-to-end communication flows can be very similar to each other when they are routed by the identical end-to-end path, whereas distinct differences are observed among the ones of different end-to-end paths. Simulations based on NS2 validate the efficiency of both t-Test and variance test and demonstrate the robustness of t-Test against asynchronous measurements between different flows.
SD-MAC: Design and evaluation of a software-defined passive optical intrarack network in data centers
- First Published: 23 October 2019
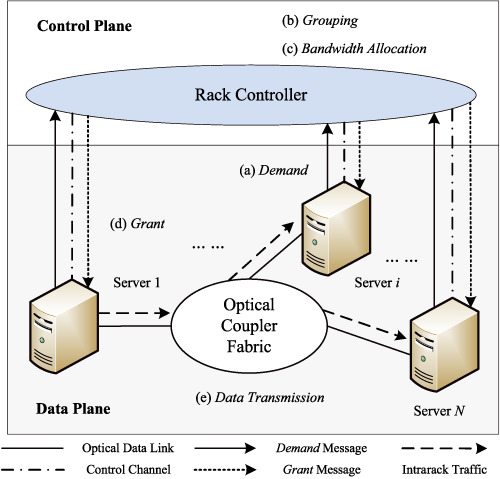
This paper presented a software-defined passive optical intrarack network SD-POIRN based on optical coupler fabrics. This paper proposed a software-defined media access control SD-MAC protocol in the control plane for scheduling intrarack data transmissions. The SD-MAC uitlizes dynamic server grouping methods and max-min fair share bandwidth allocation algorithms to improve network throughput and to reduce average packet delay.
Credible and economic multimedia service optimization based on game theoretic in hybrid cloud networks
- First Published: 20 November 2019
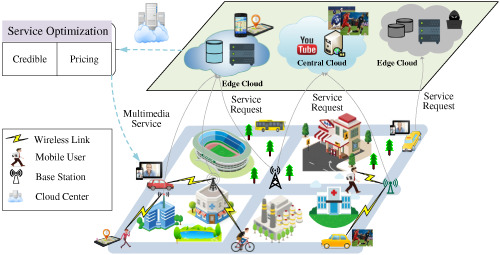
In this paper, a novel multimedia service optimization mechanism is proposed hereby to meet the user's requirements mentioned above while guaranteeing the reliability of service. Firstly, a credible scheme is designed to help the mobile users distinguish the reliable cloud providers; Meanwhile, a blockchain-based content credibility approach is further designed to guarantee the reliability and integrity of video contents. Moreover, a non-cooperative Stackelberg game model is presented to maximize the profit of each party.
Path-flow matching: Two-sided matching and multiobjective evolutionary algorithm for traffic scheduling in cloud data* center network
- First Published: 29 November 2019
SmartX Multi-View Visibility Framework for unified monitoring of SDN-enabled multisite clouds
- First Published: 09 December 2019
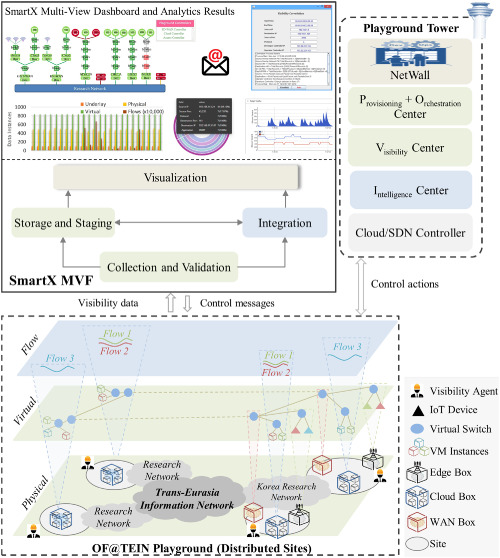
This paper has presented SmartX MVF, a multilayer visibilility framework for SDN-enabled multisite clouds. With unique monitoring pipeline, SmartX MVF delivers unified monitoring across physical and virtual resource entities. After framework deployment in the live infrastructure of OF@TEIN playground, the systematic and seamless integration among different visibility stages are verified and fond it capable of supporting sustained operations.
Fog-cloud distributed intrusion detection and cooperation
- First Published: 01 December 2019
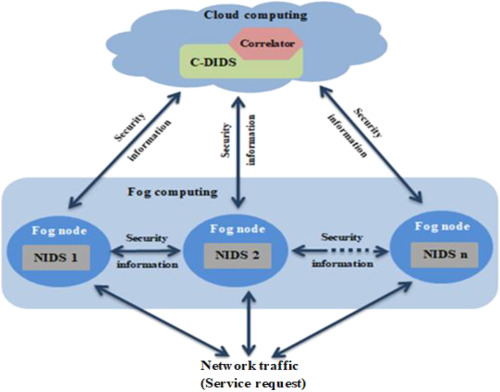
The proposed fog-cloud distributed and cooperation intrusion detection has given efficient results in terms of detection accuracy and low number of false alerts, which enhance the security of both fog and cloud computing environments. Then, the contribution of the proposed intrusion detection approach has been justified by the high improvement of the security of cloud technology by passing through the fog computing by implementing intrusion detection cooperation between those two technologies firstly and between cloud service layers secondly.
Load balancing approach for heterogeneous 2-tiered wireless sensor networks
- First Published: 13 March 2020
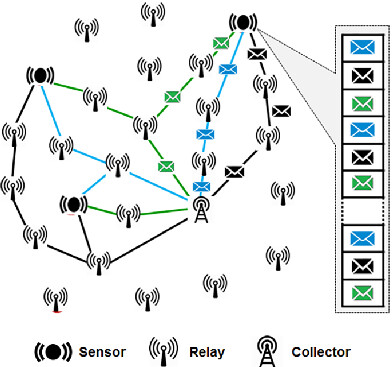
This article addresses the problem of managing power consumption in a heterogeneous Wireless Sensor Network, composed of Sensor Nodes (SNs), Relay Nodes (RNs), and a Collector Node (CN), where the aim is to extend the RNs lifetime. The proposed approach consists in creating, from the initial topology, several 2-tiered subtopologies, linking the SNs to the CN. Obtained simulation results demonstrate the effectiveness of the proposed approach.