Technology Acceptance Model 3 and a Research Agenda on Interventions
Effective July 1, 2008.
ABSTRACT
Prior research has provided valuable insights into how and why employees make a decision about the adoption and use of information technologies (ITs) in the workplace. From an organizational point of view, however, the more important issue is how managers make informed decisions about interventions that can lead to greater acceptance and effective utilization of IT. There is limited research in the IT implementation literature that deals with the role of interventions to aid such managerial decision making. Particularly, there is a need to understand how various interventions can influence the known determinants of IT adoption and use. To address this gap in the literature, we draw from the vast body of research on the technology acceptance model (TAM), particularly the work on the determinants of perceived usefulness and perceived ease of use, and: (i) develop a comprehensive nomological network (integrated model) of the determinants of individual level (IT) adoption and use; (ii) empirically test the proposed integrated model; and (iii) present a research agenda focused on potential pre- and postimplementation interventions that can enhance employees' adoption and use of IT. Our findings and research agenda have important implications for managerial decision making on IT implementation in organizations.
INTRODUCTION
While great progress has been made in understanding the determinants of employees' information technology (IT) adoption and use (Venkatesh, Morris, Davis, & Davis, 2003), trade press still suggests that low adoption and use of IT by employees are still major barriers to successful IT implementations in organizations (Overby, 2002; Gross, 2005). As ITs are becoming increasingly complex and central to organizational operations and managerial decision making (e.g., enterprise resource planning, supply chain management, customer relationship management systems), this issue has become even more severe. There are numerous examples of IT implementation failures in organizations leading to huge financial losses. Two high-profile examples of IT implementation failures are Hewlett-Packard's (HP) failure in 2004 that had a financial impact of $160 million (Koch, 2004a) and Nike's failure in 2000 that cost $100 million in sales and resulted in a 20% drop in stock price (Koch, 2004b). Low adoption and underutilization of ITs have been suggested to be key reasons for “productivity paradox”—that is, a contradictory relationship between IT investment and firm performance (Landauer, 1995; Sichel, 1997; Devaraj & Kohli, 2003). This issue is particularly important given that recent reports suggest that worldwide investment in IT will increase at a rate of 7.7% a year from 2004 to 2008 compared to 5.1% from 2000 to 2004 (World Information Technology and Service Alliance, 2004). It has been suggested in both the academic and trade press that managers need to develop and implement effective interventions in order to maximize employees' IT adoption and use (Cohen, 2005; Jasperson, Carter, & Zmud, 2005). Therefore, identifying interventions that could influence adoption and use of new ITs can aid managerial decision making on successful IT implementation strategies (Jasperson et al., 2005).
The theme of interventions as an important direction for future research is documented in recent research. For instance, Venkatesh (2006) reviewed prior research on IT adoption and suggested three avenues for future research that are pertinent to the editorial mission of Decision Sciences: (i) business process change and process standards; (ii) supply-chain technologies; and (iii) services. Within each of these three avenues, he noted interventions as a critical direction for future research that had significant managerial implications and the potential to enhance IT implementation success. More recently, other researchers have provided new directions in individual-level IT adoption research with a particular focus on interventions that can potentially lead to greater acceptance and effective utilization of IT (Benbasat & Barki, 2007; Goodhue, 2007; Venkatesh, Davis, & Morris, 2007). Our objective is to present a brief literature review, propose an integrated model of employee decision making about new ITs, empirically validate the model, and present a research agenda that identifies a set of interventions for researchers and practitioners to investigate to further our understanding of IT implementation.
The research on individual-level IT adoption and use is mature and has provided rich theories and explanations of the determinants of adoption and use decisions (e.g., Venkatesh et al., 2003; Sarker, Valacich, & Sarker, 2005 for group-level IT adoption research). Notwithstanding the plethora of IT adoption studies, there has been limited research on the interventions that can potentially lead to greater acceptance and use of IT (Venkatesh, 1999). The most widely employed model of IT adoption and use is the technology acceptance model (TAM) that has been shown to be highly predictive of IT adoption and use (Davis, Bagozzi, & Warshaw, 1989; Adams, Nelson, & Todd, 1992; Venkatesh & Davis, 2000; Venkatesh & Morris, 2000). One of the most common criticisms of TAM has been the lack of actionable guidance to practitioners (Lee, Kozar, & Larsen, 2003). Many leading researchers have noted this limitation in interviews reported in Lee et al. (2003). For example, Alan Dennis, a leading scholar in the field of information systems, commented, “imagine talking to a manager and saying that to be adopted technology must be useful and easy to use. I imagine the reaction would be ‘Duh!’ The more important questions are what [sic] makes technology useful and easy to use” (Lee et al., 2003, p. 766). Some work has been done to address this limitation by identifying determinants of key predictors in TAM, namely, perceived usefulness and perceived ease of use. Some researchers have developed context-specific determinants to the two TAM constructs—for instance, Karahanna and Straub (1999) for electronic communication systems (i.e., e-mail systems), Koufaris (2002) for e-commerce, Hong and Tam (2006) for multipurpose information appliances, Rai and Patnayakuni (1996) for CASE tools, and Rai and Bajwa (1997) for executive information systems—that have immense value in theorizing richly about the specific IT artifact (type of system) in question and identifying determinants that are specific to the type of technology being studied. Others have developed general and context-independent determinants that span across a broad range of systems (e.g., Venkatesh, 2000; Venkatesh & Davis, 2000). While each of these approaches has merits, and it is not our goal to debate generality versus context specificity in theorizing (Bacharach, 1989; Johns, 2006), in this article, we are choosing the general set of determinants of TAM as a basis for the identification of broadly applicable interventions that can fuel future research.
Venkatesh and Davis (2000) identified general determinants of perceived usefulness and Venkatesh (2000) identified general determinants of perceived ease of use. These two models were developed separately and not much is known about possible crossover effects—that is, could determinants of perceived usefulness influence perceived ease of use and/or could determinants of perceived ease of use influence perceived usefulness? Investigating and theorizing about potential crossover effects or ruling out the possibility of these effects is an important step in developing a more comprehensive nomological network around TAM. Further, interventions, based on the determinants of perceived usefulness and perceived ease of use, hold the key to helping managers make effective decisions about applying specific interventions to influence the known determinants of IT adoption and, consequently, the success of new ITs (Rai, Lang, & Welker, 2002; DeLone & McLean, 2003; Sabherwal, Jeyaraj, & Chowa, 2006). Given this backdrop, this article presents an integrated model of determinants of perceived usefulness and perceived ease of use, empirically validates the model, and uses the integrated model as a springboard to propose future directions for research on interventions.
BACKGROUND
TAM was developed to predict individual adoption and use of new ITs. It posits that individuals' behavioral intention to use an IT is determined by two beliefs: perceived usefulness, defined as the extent to which a person believes that using an IT will enhance his or her job performance and perceived ease of use, defined as the degree to which a person believes that using an IT will be free of effort. It further theorizes that the effect of external variables (e.g., design characteristics) on behavioral intention will be mediated by perceived usefulness and perceived ease of use. Over the last two decades, there has been substantial empirical support in favor of TAM (e.g., Adams et al., 1992; Agarwal & Karahanna, 2000; Karahanna, Agarwal, & Angst, 2006; Venkatesh et al., 2003, 2007). TAM consistently explains about 40% of the variance in individuals' intention to use an IT and actual usage. As of December 2007, the Social Science Citation Index listed over 1,700 citations and Google Scholars listed over 5,000 citations to the two journal articles that introduced TAM (Davis, 1989; Davis et al., 1989).
Theoretical Framework
Prior research employing TAM has focused on three broad areas. First, some studies replicated TAM and focused on the psychometric aspects of TAM constructs (e.g., Adams et al., 1992; Hendrickson, Massey, & Cronan, 1993; Segars & Grover, 1993). Second, other studies provided theoretical underpinning of the relative importance of TAM constructs—that is, perceived usefulness and perceived ease of use (e.g., Karahanna, Straub, & Chervany, 1999). Finally, some studies extended TAM by adding additional constructs as determinants of TAM constructs (e.g., Karahanna & Straub, 1999; Venkatesh, 2000; Venkatesh & Davis, 2000; Koufaris, 2002). Synthesizing prior research on TAM, we developed a theoretical framework that represents the cumulative body of knowledge accumulated over the years from TAM research (see Figure 1). The figure shows four different types of determinants of perceived usefulness and perceived ease of use—individual differences, system characteristics, social influence, and facilitating conditions. Individual difference variables include personality and/or demographics (e.g., traits or states of individuals, gender, and age) that can influence individuals' perceptions of perceived usefulness and perceived ease of use. System characteristics are those salient features of a system that can help individuals develop favorable (or unfavorable) perceptions regarding the usefulness or ease of use of a system. Social influence captures various social processes and mechanisms that guide individuals to formulate perceptions of various aspects of an IT. Finally, facilitating conditions represent organizational support that facilitates the use of an IT.
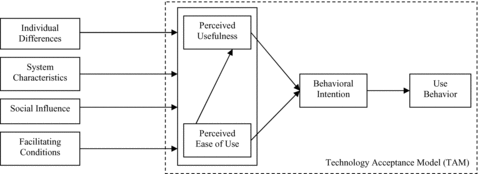
Theoretical framework.
Determinants of Perceived Usefulness
Venkatesh and Davis (2000) proposed an extension of TAM—TAM2—by identifying and theorizing about the general determinants of perceived usefulness—that is, subjective norm, image, job relevance, output quality, result demonstrability, and perceived ease of use—and two moderators—that is, experience and voluntariness. The first two determinants fall into the category of social influence and the remaining determinants are system characteristics as per the theoretical framework shown in Figure 1. Table 1 provides the definitions of the determinants of perceived usefulness. TAM2 presents two theoretical processes—social influence and cognitive instrumental processes—to explain the effects of the various determinants on perceived usefulness and behavioral intention. In TAM2, subjective norm and image are the two determinants of perceived usefulness that represent the social influence processes. Drawing on Kelman's (1958, 1961) work on social influence and French and Raven's (1959) work on power influences, TAM2 theorizes that three social influence mechanisms—compliance, internalization, and identification—will play a role in understanding the social influence processes. Compliance represents a situation in which an individual performs a behavior in order to attain certain rewards or avoid punishment (Miniard & Cohen, 1979). Identification refers to an individual's belief that performing a behavior will elevate his or her social status within a referent group because important referents believe the behavior should be performed (Venkatesh & Davis, 2000). Internalization is defined as the incorporation of a referent's belief into one's own belief structure (Warshaw, 1980). TAM2 posits that subjective norm and image will positively influence perceived usefulness through processes of internalization and identification, respectively. It further theorizes that the effect of subjective norm on both, perceived usefulness and behavioral intention will attenuate over time as users gain more experience with a system.
| Determinants | Definitions |
|---|---|
| Perceived Ease of Use | The degree to which a person believes that using an IT will be free of effort (Davis et al., 1989). |
| Subjective Norm | The degree to which an individual perceives that most people who are important to him think he should or should not use the system (Fishbein & Ajzen, 1975; Venkatesh & Davis, 2000). |
| Image | The degree to which an individual perceives that use of an innovation will enhance his or her status in his or her social system (Moore & Benbasat, 1991). |
| Job Relevance | The degree to which an individual believes that the target system is applicable to his or her job (Venkatesh & Davis, 2000). |
| Output Quality | The degree to which an individual believes that the system performs his or her job tasks well (Venkatesh & Davis, 2000). |
| Result Demonstrability | The degree to which an individual believes that the results of using a system are tangible, observable, and communicable (Moore & Benbasat, 1991). |
In TAM2, four constructs—job relevance, output quality, result demonstrability, and perceived ease of use—capture the influence of cognitive instrumental processes on perceived usefulness. Drawing on three different theoretical paradigms—that is, work motivation theory (e.g., Vroom, 1964), action identification theory (e.g., Vallacher & Wegner, 1987), and behavioral decision theory (e.g., Beach & Mitchell, 1996, 1998), Venkatesh and Davis (2000) provided a detailed discussion of how and why individuals form perceptions of usefulness based on cognitive instrumental processes. The core theoretical argument underlying the role of cognitive instrumental processes is that individuals “form perceived usefulness judgment in part by cognitively comparing what a system is capable of doing with what they need to get done in their job” (Venkatesh & Davis, 2000, p. 190). TAM2 theorizes that individuals' mental assessment of the match between important work goals and the consequences of performing job tasks using a system serves as a basis for forming perceptions regarding the usefulness of the system (Venkatesh & Davis, 2000). TAM2 posits that perceived ease of use and result demonstrability will have a positive direct influence on perceived usefulness. Job relevance and output quality will have a moderating effect on perceived usefulness such that the higher the output quality, the stronger the effect job relevance will have on perceived usefulness. Venkatesh and Davis found strong support for TAM2 in longitudinal field studies conducted at four organizations.
Determinants of Perceived Ease of Use
Building on the anchoring and adjustment framing of human decision making, Venkatesh (2000) developed a model of the determinants of perceived ease of use. Table 2 presents the definitions of the determinants of perceived ease of use. Venkatesh (2000) argued that individuals will form early perceptions of perceived ease of use of a system based on several anchors related to individuals' general beliefs regarding computers and computer use. The anchors suggested by Venkatesh (2000) are computer self-efficacy, computer anxiety, and computer playfulness, and perceptions of external control (or facilitating conditions). The first three of these anchors represent individual differences per Figure 1—that is, general beliefs associated with computers and computer use. Computer self-efficacy refers to individuals' control beliefs regarding his or her personal ability to use a system. Perceptions of external control are related to individuals' control beliefs regarding the availability of organizational resources and support structure to facilitate the use of a system. Computer playfulness represents the intrinsic motivation associated with using any new system. Venkatesh (2000) suggested that while anchors drive initial judgments of perceived ease of use, individuals will adjust these judgments after they gain direct hands-on experience with the new system. Two system characteristics–related adjustments—that is, perceived enjoyment and objective usability—were suggested by Venkatesh (2000) to play a role in determining perceived ease of use after individuals gain experience with the new system. Venkatesh (2000) theorized that even with increasing experience with the system, the role of two anchors—computer self-efficacy and perceptions of external control—will continue to be strong. However, the effects of the other two anchors—computer playfulness and computer anxiety—were theorized to diminish over time. Venkatesh (2000) further theorized that the effects of adjustments on perceived ease of use were stronger with more hands-on experience with the system. Although longitudinal studies were conducted, the specific moderating role by experience was not tested in Venkatesh (2000).
| Determinants | Definitions |
|---|---|
| Computer Self-Efficacy | The degree to which an individual believes that he or she has the ability to perform a specific task/job using the computer (Compeau & Higgins, 1995a, 1995b). |
| Perception of External Control | The degree to which an individual believes that organizational and technical resources exist to support the use of the system (Venkatesh et al., 2003). |
| Computer Anxiety | The degree of “an individual's apprehension, or even fear, when she/he is faced with the possibility of using computers” (Venkatesh, 2000, p. 349). |
| Computer Playfulness | “…the degree of cognitive spontaneity in microcomputer interactions” (Webster & Martocchio, 1992, p. 204). |
| Perceived Enjoyment | The extent to which “the activity of using a specific system is perceived to be enjoyable in its own right, aside from any performance consequences resulting from system use” (Venkatesh, 2000, p. 351). |
| Objective Usability | A “comparison of systems based on the actual level (rather than perceptions) of effort required to completing specific tasks” (Venkatesh, 2000, pp. 350–351). |
DEVELOPMENT OF TAM3
We combine TAM2 (Venkatesh & Davis, 2000) and the model of the determinants of perceived ease of use (Venkatesh, 2000), and develop an integrated model of technology acceptance—TAM3, shown in Figure 2. TAM3 presents a complete nomological network of the determinants of individuals' IT adoption and use. We suggest three theoretical extensions beyond TAM2 and the model of the determinants of perceived ease of use. In this section, we discuss these theoretical extensions and the rationale for the integration.
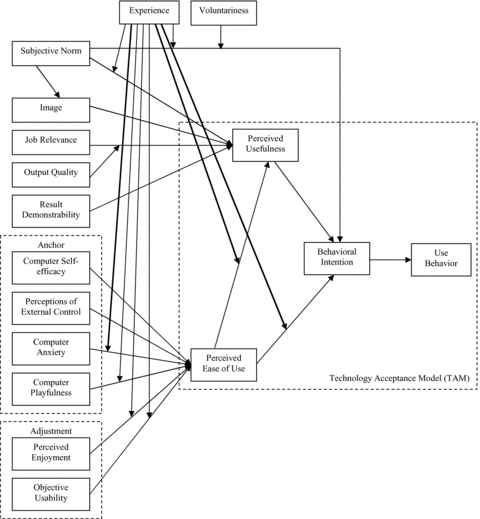
Technology acceptance model 3 (TAM3)a.
aThick lines indicate new relationships proposed in TAM3.
Crossover Effects
We expect the general pattern of relationships suggested in Venkatesh and Davis (2000) and Venkatesh (2000) to hold in TAM3. Further, we suggest that the determinants of perceived usefulness will not influence perceived ease of use and the determinants of perceived ease of use will not influence perceived usefulness. Thus, TAM3 does not posit any cross-over effects.
As noted earlier, two theoretical processes explain the relationships between perceived usefulness and its determinants: social influence and cognitive instrumental processes. The effects of the various factors—that is, subjective norm, image, job relevance, output quality, and result demonstrability—on perceived usefulness are tied to these two processes. We have no theoretical and empirical basis to expect that these processes will play any role in forming judgments about perceived ease of use. Perceived ease of use has been theorized to be closely associated with individuals' self-efficacy beliefs and procedural knowledge, which requires hands-on experience and execution of skills (Davis et al., 1989; Venkatesh, 2000; Davis & Venkatesh, 2004). Further, Venkatesh (2000) suggested that individuals form perceived ease of use about a specific system by anchoring their perceptions to the different general computer beliefs and later adjusting their perceptions of ease of use based on hands-on experience with the specific system. Social influence processes (i.e., compliance, identification, and internalization) in the context of IT adoption and use represent how important referents believe about the instrumental benefits of using a system (Venkatesh & Davis, 2000). Even if an individual gets information from important referents about how easy a system is to use, it is unlikely that the individual will form stable perceptions of ease of use based on the beliefs of referent others over and above his or her own general computer beliefs and hands-on experience with the system (e.g., Davis & Venkatesh, 2004). Further, the determinants of perceived ease of use represent several traits and emotions, such as computer self-efficacy, computer playfulness, and computer anxiety. There are no theoretical and empirical reasons to believe that these stable computer-related traits and emotions will be affected by social influence or cognitive influence processes.
We suggest that the determinants of perceived ease of use will not influence perceived usefulness. The determinants of perceived ease of use suggested by Venkatesh (2000) are primarily individual differences variables and general beliefs about computers and computer use. These variables are grouped into three categories: control beliefs, intrinsic motivation, and emotion. Perceived usefulness is an instrumental belief that is conceptually similar to extrinsic motivation and is a cognition (as opposed to emotion) regarding the benefits of using a system. The perceptions of control (over a system), enjoyment or playfulness related to a system, and anxiety regarding the ability to use a system do not provide a basis for forming perceptions of instrumental benefits of using a system. For example, control over using a system does not guarantee that the system will enhance one's job performance. Similarly, higher levels of computer playfulness or enjoyment from using a system do not mean that the system will help an individual to become more effective (e.g., Van der Heijden, 2004). Therefore, we expect that the determinants of perceived ease of use will not influence perceived usefulness.
New Relationships Posited in TAM3
TAM3 posits three relationships that were not empirically tested in Venkatesh (2000) and Venkatesh and Davis (2000). We suggest that experience will moderate the relationships between (i) perceived ease of use and perceived usefulness; (ii) computer anxiety and perceived ease of use; and (iii) perceived ease of use and behavioral intention.
Perceived ease of use to perceived usefulness, moderated by experience
We suggest that with increasing hands-on experience with a system, a user will have more information on how easy or difficult the system is to use. While perceived ease of use may not be as important in forming behavioral intention in a later period of system use (Venkatesh et al., 2003), users will still value perceived ease of use in forming perceptions about usefulness. We base this argument on action identification theory (Vallacher & Kaufman, 1996) that posits a clear distinction between high-level and low-level action identities. High-level identities are related to individuals' goals and plans, whereas low-level identities refer to the means to achieve these goals and plans. For instance, in the context of a word processing software use, a high-level identity can be writing a high quality report and a low-level identity can be striking keys or use of a specific feature of the software (Davis & Venkatesh, 2004). Perceived usefulness and perceived ease of use are considered high-level and low-level identities respectively (Davis & Venkatesh, 2004; Venkatesh & Davis, 2000). We suggest that, with increasing experience, the influence of perceived ease of use (a low-level identity) on perceived usefulness (a high-level identity) will be stronger as users will be able to form an assessment of their likelihood of attaining high-level goals (i.e., perceived usefulness) based on information gained from experience of the low-level actions (i.e., perceived ease of use).
Computer anxiety to perceived ease of use, moderated by experience
Experience will moderate the effect of computer anxiety on perceived ease of use, such that with increasing experience, the effect of computer anxiety on perceived ease of use will diminish. We expect that, with increasing experience, system-specific beliefs, rather than general computer beliefs, will be stronger determinants of perceived ease of use of a system. Venkatesh (2000) argued that system-specific objective usability and perceived enjoyment will be stronger determinants over time and the effects of general computer beliefs (e.g., computer anxiety) will diminish because with increasing experience, users will develop accurate perceptions of effort required to complete specific tasks (i.e., objective usability) and discover aspects of a system that lead to enjoyment (or lack thereof). Computer anxiety is theorized as an anchoring belief that inhibits forming a positive perception of ease of use of a system (Venkatesh, 2000). Research on anchoring and adjustment has found that while anchors influence judgments, the role of anchors declines over time as adjustment information becomes available (Yadav, 1994; Wasnik, Kent, & Hoch, 1998; Mussweiler & Strack, 2001). Drawing on this, we argue that the effect of computer anxiety on perceived ease of use will decline with increasing experience as individuals will have more accurate perceptions of the effort needed to use a system.
Perceived ease of use to behavioral intention, moderated by experience
We expect that experience will moderate the effect of perceived ease of use on behavioral intention such that the effect will be weaker with increasing experience. Perceived ease of use—that is, how easy or difficult a system is to use—is an initial hurdle for individuals while using a system (Venkatesh, 2000). However, once individuals get accustomed to the system and gain hands-on experience with the system, the effect of perceived ease of use on behavioral intention will recede into the background as individuals now have more procedural knowledge about how to use the system. Consequently, individuals will place less importance on perceived ease of use while forming their behavioral intentions to use the system.
METHOD
Longitudinal field studies were conducted to test TAM3. Data were collected from four different organizations—sites A through D—implementing new ITs. These organizations provided an opportunity to test our research model in real-world settings of IT implementations. The research sites represented different industries, organizational contexts, and functional areas. Further, the types of ITs were different across the sites. Such variability in organizational settings and types of technologies adds to the potential generalization of our findings. In two of these organizations, the use of the new system was voluntary. In all four organizations, we collected data over a 5-month period with four points of measurements. In this section, we describe the settings, participants, measurement, and data collection procedure.
Settings and Participants
Site A was a medium-sized manufacturing firm that introduced a proprietary operational system to manage daily operations such as floor and machine scheduling and personnel assignment. These operations were conducted manually by the floor supervisors before the implementation of the new system. The users received 2 days of formal training on the new system. The users of the new system were 48 floor supervisors of whom 38 completed the survey at all points of measurement. The use of the new system was voluntary.
Site B was a large financial services firm that was in the process of transitioning to a Windows-based environment from mainframe-based IT applications. The users were members of the personal financial services department. The system use was voluntary as the users were allowed to use the old systems. Formal on-site training about the system was conducted for 1.5 days. Out of 50 potential users of the system who participated in the training, 39 provided usable responses at all points of measurement.
Site C was a small accounting services firm that introduced a new Windows-based customer account management system replacing the old paper- and DOS-based systems. The users were from customer service representatives. The system use was mandatory as the old system was phased out immediately after the new system implementation. On-site system training was conducted for 1 day. Out of 51 potential users of the new system who attended the training, 43 provided usable responses at all points of measurement.
Site D was a small international investment-banking firm that implemented a new system to assist in analyzing and creating financially sound international stock portfolios. The users were analysts performing different functions related to domestic and international stock management. While the organization had an existing system to perform the activities related to analyzing and creating stock portfolios, the new system had substantially different features and was developed by a different vendor. The use of the system was mandatory. The potential users received a 4-hour training program to become familiar with the new system. Out of 51 potential users of the new system, 36 provided usable responses at all points of measurement.
Measurement
We used validated items from prior research to test TAM3. Appendix A presents a list of items for all the constructs. TAM constructs—that is, perceived usefulness (PU), perceived ease of use (PEOU), and behavioral intention (BI)—were operationalized using items adapted from Davis (1989) and Davis et al. (1989). Consistent with Davis (1989), use (USE) was operationalized by asking the respondents, “On average, how much time to you spend on the system every day?_____ hours and _____ minutes.” Our research design allowed us to collect the use data separate from its determinants (e.g., behavioral intention, perceived usefulness, etc.). Particularly, there was at least a 1-month gap between the collection of survey data and the measurement of use. Specifically the measurements of use and its determinants were separated by 1 month (T1–T2), 3 months (T2–T3) and 2 months (T3–T4). Such a design approach helped us overcome the problems associated with common method biases.
Operationalization of the determinants of perceived ease of use (i.e., computer self-efficacy, perceptions of external control, computer playfulness, computer anxiety, objective usability, and perceived enjoyment) was consistent with Venkatesh (2000). Computer self-efficacy (CSE) was measured using four items adapted from Compeau and Higgins (1995a). Perceptions of external control (PEC) were measured using four items adapted from the scale of facilitating conditions developed by Mathieson (1991) and Taylor and Todd (1995). Computer playfulness (CPLAY) was measured using four items adapted from Webster and Martocchio (1992). Computer anxiety (CANX) was measured using four items used in Venkatesh (2000). Following Venkatesh (2000) and human-computer interaction (HCI) research, objective usability (OU) was operationalized by computing a novice-to-expert ratio of effort. During the training program, each participant was asked to perform a set of tasks using the new system. The system recorded the time each participant took to accomplish the tasks. The time was then compared to the time taken by an expert to accomplish the same tasks to determine a ratio, which served as the measure of objective usability for each participant. Perceived enjoyment (ENJ) was measured using four items adapted from Davis, Bagozzi, and Warshaw (1992).
Determinants of perceived usefulness were measured using items from Venkatesh and Davis (2000). Subjective norm (SN) was measured using four items adapted from Taylor and Todd (1995). Image (IMG) and result demonstrability (RES) were operationalized using three and four items respectively from Moore and Benbasat (1991). Job relevance (REL) and output quality (OUT) were measured using three items each adapted from Davis et al. (1992). Voluntariness (VOL) was assessed using three items from Moore and Benbasat (1991). Even though we chose two sites where system use was voluntary and two sites where the use was mandatory, we collected data on user perceptions of voluntariness because, consistent with TAM2, TAM3 posits perceived, rather than actual, voluntariness as an important contextual variable.
Procedure
As noted earlier, formal training was conducted at each site to educate the potential users about the new system. While the duration and method of this formal training varied in different sites, our data collection approach was consistent across the four sites. In all four organizations, we administered questionnaires at three points in time: after initial training (T1), 1 month after implementation (T2), and 3 months after implementation (T3). We also measured self-reported usage at T2, T3, and 5 months after implementation (T4). We administered the T1 survey (Web-based) immediately after the formal training at each site. We captured each participant's login ID and assigned a unique barcode for each participant. This unique barcode helped us track individual survey responses in subsequent data collection periods (T2, T3, and T4). Self-reported use related to the previous period was measured (e.g., at T2, use from T1 to T2 was measured). The T2 and T3 surveys were paper-based. The paper-based surveys with the unique barcodes were delivered to the mailboxes of each participant who filled out surveys at T1 with a request to return the surveys within a week to the researchers. At T4, only self-reported use was measured.
RESULTS
We used Partial Least Squares (PLS), a component-based structural equation modeling technique, to analyze our data. PLS-Graph, version 3, build 1126 was used to analyze the data. Chin, Marcolin, and Newsted (2003) noted that PLS has minimal restrictions in terms of distributional assumptions and sample size. While analyzing data, we followed the guidelines specified in Chin et al. (2003) and other exemplars in IS research (e.g., Compeau & Higgins, 1995a). All constructs were modeled using reflective indicators. Consistent with Venkatesh and Davis (2000) and Venkatesh et al. (2003), voluntariness was coded per the score for each participant and experience was coded as an ordinal variable. When applicable, we mean-centered the variables at the indicator level prior to creating the interaction terms (Aiken & West, 1991; Chin et al., 2003). Mean-centering helps limit potential multicollinearity, evidenced by the low variation inflation factors (VIFs) for all constructs in our model. We employed a bootstrapping method (500 times) that used randomly selected subsamples to test the various PLS models.
Measurement Models
We assessed the measurement model separately for each time period (N= 156 for each time period). All constructs at each time period exhibited strong psychometric properties and satisfied the criteria of reliability and convergent and discriminant validity. Table 3 shows that the item loadings were greater than or at least equal to .70 for all constructs at all time periods. We did not find any cross-loadings of more than .30. Thus, convergent and discriminant validity was supported (Fornell & Larcker, 1981). As Table 4 shows, internal consistency reliabilities (ICRs) were greater than .70 for all constructs at all points of measurement. The square root of the average variance extracted (AVE) for each construct was higher than the correlations across constructs. Such strong psychometric properties were consistent with much prior research employing these constructs and measures (Davis, 1989; Davis et al., 1989; Mathieson, 1991; Taylor & Todd, 1995; Agarwal & Karahanna, 2000; Karahanna et al., 2006). The pattern of correlations shown in Table 4 is consistent with prior studies (e.g., Venkatesh et al., 2003). While the longitudinal design provided us a procedural remedy for common method bias, we conducted statistical analysis following the guidelines of Podsakoff, MacKenzie, Lee, and Podsakoff (2003) and Malhotra, Kim, and Patil (2006) to assess common method bias. Particularly, we conducted Harmon's single factor test and marker variable test (we used job satisfaction as a marker variable) and did not find any significant common method bias.
| Constructs | Items | T1 | T2 | T3 | Pooled | Constructs | Items | T1 | T2 | T3 | Pooled |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Perceived | PU1 | .88 | .84 | .90 | .88 | Subjective | SN1 | .84 | .88 | .80 | .83 |
| Usefulness | PU2 | .84 | .88 | .90 | .89 | Norm (SN) | SN2 | .88 | .82 | .75 | .78 |
| (PU) | PU3 | .90 | .90 | .89 | .90 | SN3 | .80 | .77 | .75 | .77 | |
| PU4 | .92 | .91 | .94 | .92 | SN4 | .80 | .78 | .70 | .76 | ||
| Perceived | PEOU1 | .90 | .89 | .88 | .90 | Voluntariness | VOL1 | .77 | .84 | .88 | .85 |
| Ease of Use | PEOU2 | .90 | .92 | .92 | .91 | (VOL) | VOL2 | .85 | .90 | .92 | .88 |
| (PEOU) | PEOU3 | .93 | .90 | .90 | .91 | VOL3 | .83 | .85 | .90 | .88 | |
| PEOU4 | .94 | .93 | .92 | .93 | Image (IMG) | IMG1 | .82 | .85 | .88 | .85 | |
| Computer | CSE1 | .84 | .80 | .77 | .80 | IMG2 | .86 | .78 | .79 | .82 | |
| Self-Efficacy | CSE2 | .78 | .75 | .70 | .74 | IMG3 | .90 | .92 | .90 | .90 | |
| (CSE) | CSE3 | .73 | .73 | .72 | .72 | Job Relevance | REL1 | .91 | .84 | .85 | .90 |
| CSE4 | .74 | .71 | .73 | .72 | (REL) | REL2 | .88 | .90 | .81 | .89 | |
| Perceptions | PEC1 | .80 | .77 | .75 | .76 | REL3 | .84 | .84 | .80 | .82 | |
| of External | PEC2 | .78 | .77 | .73 | .74 | Output Quality | OUT1 | .90 | .88 | .84 | .88 |
| Control | PEC3 | .77 | .74 | .74 | .74 | (OUT) | OUT2 | .83 | .80 | .70 | .79 |
| (PEC) | PEC4 | .75 | .75 | .73 | .73 | OUT3 | .77 | .72 | .74 | .72 | |
| Computer | CPLAY1 | .74 | .78 | .79 | .77 | Result | RES1 | .80 | .82 | .84 | .80 |
| Playfulness | CPLAY2 | .74 | .77 | .70 | .72 | Demonstrability | RES2 | .83 | .80 | .70 | .77 |
| (CPLAY) | CPLAY3 | .73 | .74 | .73 | .74 | (RES) | RES3 | .82 | .80 | .72 | .75 |
| CPLAY4 | .80 | .84 | .70 | .78 | RES4 | .73 | .72 | .80 | .71 | ||
| Computer | CANX1 | .77 | .70 | .74 | .73 | Behavioral | BI1 | .80 | .82 | .84 | .82 |
| Anxiety | CANX2 | .70 | .74 | .75 | .74 | Intention) | BI2 | .90 | .92 | .90 | .92 |
| (CANX) | CANX3 | .73 | .70 | .77 | .75 | (BI) | BI3 | .90 | .88 | .84 | .87 |
| CANX4 | .76 | .76 | .74 | .74 | Use (USE) | USE1 | 1.00 | 1.00 | 1.00 | 1.00 | |
| Perceived | ENJ1 | .85 | .88 | .82 | .84 | ||||||
| Enjoyment | ENJ2 | .84 | .85 | .82 | .80 | ||||||
| (ENJ) | ENJ3 | .80 | .84 | .84 | .83 | ||||||
- aThe loadings at T1, T2, T3, and pooled respectively are from separate measurement model tests.
- bAll cross-loadings were below .30.
| T1 Results | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| M | SD | ICR | PU | PEOU | CSE | PEC | CPLAY | CANX | ENJ | OU | SN | IMG | JREL | OUT | RES | BI | USE | |
| PU | 4.14 | 1.22 | .92 | .83 | ||||||||||||||
| PEOU | 3.98 | 1.07 | .93 | .30*** | .87 | |||||||||||||
| CSE | 4.66 | 1.33 | .80 | .17* | .40*** | .77 | ||||||||||||
| PEC | 3.98 | 1.27 | .76 | .15* | .36*** | .29*** | .74 | |||||||||||
| CPLAY | 4.41 | 1.09 | .82 | .08 | .35*** | .33*** | .17* | .74 | ||||||||||
| CANX | 3.88 | 1.23 | .83 | −.14* | −.38*** | −.20* | −.19* | −.33*** | .72 | |||||||||
| ENJ | 3.22 | 1.07 | .88 | .07 | .22** | .08 | .10 | .18* | −.19* | .82 | ||||||||
| OU | NA | NA | NA | .15* | .18* | .11 | .04 | .08 | .08 | .03 | NA | |||||||
| SN | 4.87 | 1.22 | .85 | .30*** | .19* | −.14* | .16* | −.17* | .20** | .10 | .08 | .81 | ||||||
| IMG | 3.94 | 1.45 | .83 | .26*** | .08 | .18* | .08 | .13 | .18* | .14 | .09 | .43*** | .82 | |||||
| JREL | 4.01 | 1.32 | .83 | .32*** | .23*** | .16* | .18* | .02 | .12 | .10 | .03 | .22*** | .11 | .78 | ||||
| OUT | 4.08 | 1.22 | .77 | .28*** | .24*** | .09 | .04 | .09 | .02 | .04 | .08 | .16* | .20** | .32*** | .76 | |||
| RES | 3.56 | 1.09 | .85 | .28*** | .17* | .04 | .09 | .00 | .05 | .10 | .08 | .25*** | .14* | .16* | .27*** | .71 | ||
| BI | 4.10 | 1.35 | .90 | .59*** | .30*** | .22*** | .26*** | .18* | −.19* | .17* | .17* | .17* | .26*** | .27*** | .26*** | .26*** | .85 | |
| USE | 7.85 | 3.33 | NA | .51*** | .27*** | .18* | .24*** | .16* | −.17* | .16* | .17* | .23*** | .24*** | .22** | .22** | .21** | .57*** | NA |
| T2 Results | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| M | SD | ICR | PU | PEOU | CSE | PEC | CPLAY | CANX | ENJ | OU | SN | IMG | JREL | OUT | RES | BI | USE | |
| PU | 4.41 | 1.21 | .94 | .85 | ||||||||||||||
| PEOU | 4.43 | 1.04 | .90 | .32*** | .85 | |||||||||||||
| CSE | 4.72 | 1.30 | .82 | .16* | .41*** | .75 | ||||||||||||
| PEC | 4.28 | 1.20 | .73 | .17* | .37*** | .30*** | .73 | |||||||||||
| CPLAY | 4.36 | 1.11 | .81 | .07 | .38*** | .30*** | .19** | .76 | ||||||||||
| CANX | 4.01 | 1.28 | .84 | −.18* | −.29*** | −.22** | −.18* | −.30*** | .71 | |||||||||
| ENJ | 3.85 | 1.22 | .89 | .09 | .27*** | .16* | .08 | .19** | −.20** | .82 | ||||||||
| OU | NA | NA | NA | .22** | .24*** | .14* | .02 | .03 | −.09 | −.19* | NA | |||||||
| SN | 4.56 | 1.30 | .83 | .25*** | .17* | −.17* | .15* | −.19** | .18* | .08 | .04 | .80 | ||||||
| IMG | 4.28 | 1.40 | .81 | .29*** | .08 | .20** | .03 | .10 | .16* | .10 | .03 | .40*** | .82 | |||||
| JREL | 4.29 | 1.36 | .85 | .29*** | .25*** | .18* | .19* | .03 | .10 | .10 | .05 | .18** | .16* | .80 | ||||
| OUT | 4.33 | 1.08 | .75 | .23*** | .21** | .04 | .02 | .07 | .04 | .05 | .07 | .19** | .22** | .27*** | .76 | |||
| RES | 3.87 | 1.23 | .84 | .32*** | .16* | .04 | .08 | .02 | .04 | .07 | .10 | .23*** | .10 | .14* | .26*** | .72 | ||
| BI | 4.41 | 1.51 | .91 | .59*** | .24*** | .21** | .26*** | .17* | −.17* | .17* | .19** | .12 | .12 | .24*** | .23*** | .22** | .80 | |
| USE | 11.23 | 4.29 | NA | .50*** | .22*** | .18* | .24*** | .15* | −.16* | .17* | .17* | .17* | .25*** | .22** | .24*** | .20** | .56*** | NA |
| T3 Results | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| M | SD | ICR | PU | PEOU | CSE | PEC | CPLAY | CANX | ENJ | OU | SN | IMG | JREL | OUT | RES | BI | USE | |
| PU | 4.55 | 1.27 | .94 | .84 | ||||||||||||||
| PEOU | 4.89 | 1.13 | .93 | .38*** | .88 | |||||||||||||
| CSE | 4.70 | 1.28 | .85 | .15* | .44*** | .78 | ||||||||||||
| PEC | 4.51 | 1.28 | .78 | .19** | .47*** | .05 | .75 | |||||||||||
| CPLAY | 4.40 | 1.20 | .84 | .10 | .28*** | .29*** | .20** | .75 | ||||||||||
| CANX | 4.10 | 1.35 | .84 | −.20** | −.25*** | −.22** | −.19** | −.24*** | .76 | |||||||||
| ENJ | 4.13 | 1.28 | .89 | .05 | .30*** | .07 | .09 | .18* | −.20** | .83 | ||||||||
| OU | NA | NA | NA | .26*** | .27*** | .18* | .17* | .10 | −.17* | .16* | NA | |||||||
| SN | 4.28 | 1.25 | .86 | .25*** | .23*** | −.14* | .18* | −.16* | .17* | .04 | .03 | .82 | ||||||
| IMG | 4.44 | 1.23 | .84 | .25*** | .08 | .22** | .04 | .04 | .16* | .07 | .05 | .41*** | .83 | |||||
| JREL | 4.39 | 1.29 | .82 | .32*** | .22** | .16* | .17* | .02 | .05 | .02 | .07 | .24*** | .17* | .81 | ||||
| OUT | 4.49 | 1.20 | .76 | .28*** | .20** | .02 | .03 | .01 | .02 | .04 | .08 | .23*** | .20** | .28*** | .79 | |||
| RES | 4.10 | 1.09 | .85 | .30*** | .15* | .06 | .07 | .05 | .03 | .05 | .04 | .20** | .15* | .10 | .27*** | .73 | ||
| BI | 4.54 | 1.33 | .88 | .58*** | .19** | .20** | .24*** | .16* | −.18* | .16* | .17* | .17* | .24*** | .22*** | .23*** | .23*** | .81 | |
| USE | 12.87 | 5.13 | NA | .49*** | .17* | .18* | .21** | .15* | −.15* | .17* | .16* | .17* | .22*** | .18* | .20** | .21** | .59*** | NA |
- aICR = internal consistency reliability; diagonal elements are the square root of the shared variance between the constructs and their measures; off-diagonal elements are correlations between constructs.
- bPU = perceived usefulness; PEOU = perceived ease of use; CSE = computer self-efficacy; PEC = perceptions of external control; CPLAY = computer playfulness; CANX = computer anxiety; ENJ = perceived enjoyment; OU = objective usability; SN = subjective norm; IMG = image; REL = job relevance; OUT = output quality; RES = result demonstrability; BI = behavioral intention; USE = use.
- c*p < .05, **p < .01, ***p < .001.
Explaining and Predicting Perceived Usefulness
Our findings regarding perceived usefulness were generally consistent with Venkatesh and Davis (2000). In particular, we found that perceived ease of use, subjective norm, image, and result demonstrability were significant predictors of perceived usefulness at all time periods (see Table 5). Also consistent with Venkatesh and Davis (2000), we found that job relevance and output quality had an interactive effect on perceived usefulness such that with increasing output quality, the effect of job relevance on perceived usefulness was stronger. We found that experience moderated the effects of subjective norm on perceived usefulness such that the effect was weaker with increasing experience. While not shown in Table 5, we found that the effect of image on subjective norm was significant at all points of measurements.
| T1 (N= 156) | T2 (N= 156) | T3 (N= 156) | Pooled (N= 468) | |
|---|---|---|---|---|
| R2 | .60 | .56 | .52 | .67 |
| Perceived Ease of Use (PEOU) | .22*** | .26*** | .33*** | .08 |
| Subjective Norm (SN) | .40*** | .32*** | .13* | .04 |
| Image (IMG) | .27*** | .20** | .23*** | .24*** |
| Job Relevance (REL) | .04 | .05 | .08 | .03 |
| Output Quality (OUT) | .06 | .01 | .02 | .03 |
| Result Demonstrability (RES) | .22*** | .26*** | .28*** | .26*** |
| Computer Self-Efficacy (CSE) | .07 | .03 | .01 | .04 |
| Perceptions of Ext. Control (PEC) | .04 | .01 | .04 | .03 |
| Computer Anxiety (CANX) | .03 | .04 | .02 | .03 |
| Computer Playfulness (PLAY) | .08 | .02 | .05 | .04 |
| Perceived Enjoyment (ENJ) | .02 | .05 | .02 | .04 |
| Objective Usability (OU) | .01 | .00 | .00 | .01 |
| Experience (EXP) | .03 | |||
| EOU × EXP | .39*** | |||
| SN × EXP | –.29*** | |||
| REL × OUT | .37*** | .34*** | .35*** | .35*** |
- aShaded areas are not applicable for the specific column.
- b*p < .05, **p < .01, ***p < .001.
TAM3 posits that: (i) the effect of perceived ease of use on perceived usefulness will be moderated by experience; and (ii) the determinants of perceived ease of use (i.e., computer self-efficacy, perceptions of external control, computer anxiety, computer playfulness, perceived enjoyment, and objective usability) will not have any significant effects on perceived usefulness over and above the determinants of perceived usefulness. As shown in Table 5, experience moderated the effect of perceived ease of use on perceived usefulness such that with increasing experience the effect became stronger. The table also shows that none of the determinants of perceived ease of use had significant effects on perceived usefulness at any point in time. Overall, TAM3 was able to explain between 52% and 67% of the variance in perceived usefulness across different time periods and models (see Table 5).
Explaining and Predicting Perceived Ease of Use
Consistent with Venkatesh (2000), we found that the anchors—that is, computer self-efficacy, perceptions of external control, computer anxiety, and computer playfulness—were significant predictors of perceived ease of use at all points of measurement (see Table 6). As expected, the adjustments—that is, perceived enjoyment and objective usability—were not significant at T1, but they were significant at both T2 and T3. As theorized, we found that experience moderated the effect of computer anxiety on perceived ease of use such that the effect became weaker with increasing experience (CANX × EXP). Our results indicated that none of the determinants of perceived usefulness had a significant effect on perceived ease of use. Overall, TAM3 explained between 43% and 52% of variance in perceived ease of use across different points of measurements and models (see Table 6).
| T1 (N= 156) | T2 (N= 156) | T3 (N= 156) | Pooled (N= 468) | |
|---|---|---|---|---|
| R2 | .43 | .45 | .44 | .52 |
| Subjective Norm (SN) | .03 | .01 | .04 | .04 |
| Image (IMG) | .04 | .04 | .00 | .00 |
| Job Relevance (REL) | .02 | .01 | .05 | .05 |
| Output Quality (OUT) | .05 | .04 | .07 | .07 |
| Result Demonstrability (RES) | .02 | .03 | .02 | .02 |
| Computer Self-Efficacy (CSE) | .35*** | .30*** | .28*** | .31*** |
| Perceptions of Ext. Control (PEC) | .37*** | .30*** | .30*** | .33*** |
| Computer Anxiety (CANX) | –.22*** | –.18** | –.14* | –.18** |
| Computer Playfulness (CPLAY) | .20** | .16* | .11* | .15** |
| Perceived Enjoyment (ENJ) | .02 | .22*** | .24*** | .04 |
| Objective Usability (OU) | .04 | .19** | .23*** | .03 |
| Experience (EXP) | .01 | |||
| CPLAY × EXP | –.22*** | |||
| CANX × EXP | .21*** | |||
| ENJ × EXP | .18** | |||
| OU × EXP | .20** | |||
- aShaded areas are not applicable for the specific column.
- b*p < .05, **p < .01, ***p < .001.
Explaining and Predicting Behavioral Intention and Use
We found that perceived usefulness was the strongest predictor of behavioral intention at all time periods (see Table 7). While perceived ease of use was significant at T1 and T2, it was not significant at T3, suggesting a moderating effect of experience in the relationship between perceived ease of use and behavioral intention. We found that experience, in fact, moderated the effect of perceived ease of use (PEOU × EXP) on behavioral intention such that with increasing experience the effect became weaker. We also found a significant three-way interaction among subjective norm, experience, and voluntariness (SN × EXP × VOL) on behavioral intention such that the effect of subjective norm on behavioral intention became weaker with increasing experience, particularly in the voluntary context. The two-way interaction between subjective norm and voluntariness (SN × EXP) indicated that the effect of subjective norm on behavioral intention was stronger in a mandatory context. Table 7 shows that TAM3 explained between 40% and 53% variance in behavioral intention across different time periods and models. Consistent with much prior research on IT adoption and social psychology, we found that behavioral intention was a significant predictor of use at all points of measurements. Table 8 shows that the variance explained in use was between 31% and 36%.
| T1 (N= 156) | T2 (N= 156) | T3 (N= 156) | Pooled (N= 468) | |
|---|---|---|---|---|
| R2 | .48 | .44 | .40 | .53 |
| Perceived Usefulness (PU) | .55*** | .56*** | .57*** | .56*** |
| Perceived Ease of Use (PEOU) | .24*** | .17* | .05 | .04 |
| Subjective Norm (SN) | .03 | .04 | .02 | .02 |
| Experience (EXP) | .02 | |||
| Voluntariness (VOL) | .02 | .02 | .04 | .07 |
| PEOU × EXP | –.24*** | |||
| SN × EXP | .04 | |||
| SN × VOL | .29*** | .22*** | .17* | .03 |
| SN × EXP × VOL | –.46*** | |||
- aShaded areas are not applicable for the specific column.
- b*p < .05, **p < .01, ***p < .001.
| T2 (N= 156) | T3 (N= 156) | T4 (N= 156) | Pooled (N= 468) | |
|---|---|---|---|---|
| R2 | .32 | .31 | .36 | .35 |
| Behavioral Intention (BI) | .57*** | .56*** | .60*** | .59*** |
- a*p < .05, **p < .01, ***p < .001.
INTERVENTIONS AND FUTURE RESEARCH DIRECTIONS
The development and validation of TAM3 was an important first step in understanding the role of interventions in IT adoption contexts. In this section, we discuss important interventions, based on the determinants of perceived usefulness and perceived ease of use, and offer future research directions related to these interventions. We classify the interventions into two categories: preimplementation and postimplementation interventions. Our classification approach was motivated by the stage models of IT implementation suggested by Cooper and Zmud (1990) and Saga and Zmud (1994). These stage models identified important activities and user reactions during pre- and postimplementation phases of IT implementation. The preimplementation phase is characterized by stages leading to the actual roll-out of a system—that is, initiation, organizational adoption, and adaptation—while the postimplementation phase entails stages that follow the actual deployment of the system—that is, user acceptance, routinization, and infusion (Cooper & Zmud, 1990). These stages are defined as follows: initiation: identification of organizational problems/opportunities that warrant a technology solution; adoption: organizational decision to adopt and install a technology; adaptation: modification processes directed toward individual/organizational needs to better fit the technology with the work setting; acceptance: efforts undertaken to induce organizational members to commit to the use of technology; routinization: alterations that occur within work systems to account for technology such that these systems are no longer perceived as new or out-of-the ordinary; infusion: technology becomes more deeply embedded within the organization's work system (Cooper & Zmud, 1990; Saga & Zmud, 1994). Table 9 presents a summary of pre- and postimplementation interventions and their potential influence on the determinants of perceived usefulness and perceived ease of use. We use this table as a framework in the subsequent discussion.
| Preimplementation Interventions | Postimplementation Interventions | ||||||
|---|---|---|---|---|---|---|---|
| Design Characteristics | User Participation | Management Support | Incentive Alignment | Training | Organizational Support | Peer Support | |
| Determinants of Perceived Usefulness | |||||||
| Subjective Norm | X | X | X | X | |||
| Image | X | X | X | ||||
| Job Relevance | X | X | X | X | X | X | X |
| Output Quality | X | X | X | X | X | X | X |
| Result Demonstrability | X | X | X | X | X | X | X |
| Determinants of Perceived Ease of Use | |||||||
| Computer Self-Efficacy | X | ||||||
| Perceptions of Ext. Control | X | X | X | X | |||
| Computer Anxiety | X | X | X | ||||
| Computer Playfulness | X | X | |||||
| Perceived Enjoyment | X | X | X | X | |||
| Objective Usability | X | X | X | ||||
- aX indicates a particular intervention can potentially influence a particular determinant of perceived usefulness or perceived ease of use.
Preimplementation Interventions
Preimplementation interventions represent a set of organizational activities that take place during system development and deployment periods and can potentially lead to greater acceptance of a system. These interventions are important for at least two interrelated reasons: (i) minimization of initial resistance to a new system; and (ii) providing a realistic preview of the system so that potential users can develop an accurate perception regarding system features and how the system may help them perform their job. As systems are becoming increasingly complex and central to managerial and employee decision making and work processes (e.g., enterprise resource planning, supply chain management, customer relationships management systems) requiring substantial changes to organizational business processes, implementation of such complex, disruptive systems are subject to severe resistance from employees (see Venkatesh, 2006). Employees may feel that the new system will threaten their existing routines and habits, change the nature of their job and relationships with others, and degrade their status in the organization (Markus, 1983; Beaudry & Pinnsonnealt, 2005; Lapointe & Rivard, 2005). Proactive implementation of interventions is thus necessary to minimize such resistance. Further, employees may perceive that the complexity of a new system will add quantitative and qualitative overload to their jobs and reduce autonomy and control over their work environment (Ahuja & Thatcher, 2005). This perception may result from an inaccurate understanding of system characteristics and instrumental benefits of the system (Davis & Venkatesh, 2004). Therefore, interventions that ensure accurate perceptions of system characteristics and instrumental benefits of a system are of immense importance during preimplementation phase.
Design characteristics
Design characteristics of a system can positively influence user acceptance and system success (e.g., DeLone & McLean, 1992, 2003; Davis, 1993; Wixom & Todd, 2005). These characteristics can be broadly categorized into information- and system-related characteristics (DeLone & McLean, 1992). We suggest that information-related characteristics of a system will influence the determinants of perceived usefulness, while the system-related characteristics will influence the determinants of perceived ease of use. For example, in the context of group support systems, prior research has suggested the information-related design characteristics help users improve productivity and performance (e.g., Dennis & Valacich, 1993, 1999; Valacich, Dennis, & Connolly, 1994; Dennis, Valacich, Carte, Garfield, Haley, & Aronson, 1997; Speier, Valacich, & Vessey, 1999). If a system can provide users relevant information in a timely manner, accurately, and in an understandable format and help them make better decisions (Speier, Valacich, & Vessey, 2003), it is more likely that users will perceive greater job relevance of the system, high output quality, and greater result demonstrability—the important determinants of perceived usefulness. Related yet distinct from this, if a system is reliable (e.g., no downtime), flexible, and user friendly—important aspects of system-related characteristics—it is more likely that the users will perceive their use experience to be enjoyable and have less system-related anxiety. The system-related characteristics will enhance objective usability of the system because users will be able to perform their tasks quickly. Further, it is possible that if the system is user friendly, a user may feel that they have a greater control over the system, thus enhancing their self-efficacy toward using the system. Design characteristics are particularly important for enterprise systems because these systems are inherently difficult to understand and use.
We urge IS researchers to examine the influence of design characteristics on user acceptance, particularly on the determinants of perceived usefulness and perceived ease of use. While prior research (e.g., Wixom & Todd, 2005) found that information and system quality influenced perceived usefulness and perceived ease of use, we suggest that it is important to drill down into what design characteristics influence what specific aspects of perceived usefulness and perceived ease of use in order to enhance our ability to identify and improve specific design characteristics to enhance certain determinants of perceived usefulness and perceived ease of use. From a methodological point of view, we understand that manipulating design characteristics in a field setting can be difficult and expensive. Simulation and agent-based modeling approaches (e.g., Macy & Willer, 2002; Raghu, Rao, & Sen, 2003) offer low-cost alternatives to investigate the impact of design characteristics on IT adoption and use. These approaches can be used to manipulate different design characteristics and isolate the effects of these characteristics on various determinants of IT adoption. Example research questions related to design characteristics are:
- (i)
What specific design characteristics will influence the determinants of perceived usefulness and perceived ease of use?
- (ii)
How can users be helped so that they develop accurate perceptions of design characteristics during the implementation phases of IT implementation, particularly for enterprise systems that are traditionally perceived as difficult to understand and use?
- (iii)
Will perceived usefulness and perceived ease of use formed based on early preview of design characteristics of complex systems remain stable throughout the implementations process?
User participation
User participation refers to the assignments, activities, and behaviors that users or their representatives perform during the systems implementation process (Barki & Hartwick, 1994). It is an important intervention that has been shown to lead to greater user involvement, system acceptance, and system success (Swanson, 1974; Ives & Olson, 1984; Hartwick & Barki, 1994). We suggest that user participation is even more important for complex systems, (e.g., enterprise systems) as these systems are expected to cause substantial disruptions of organizational work processes. Even though user participation and involvement have been used interchangeably in the IS literature, Barki and Hartwick (1994) and Hartwick and Barki (1994) provided conceptual distinctions between the two. They argue that user participation refers to the actual partaking in a project, whereas user involvement refers to a subjective psychological state reflecting the importance and personal relevance of a new system to the user. The three dimensions of user participation—that is, overall responsibility (e.g., leadership and accountability in the system implementation process), user-IS relationship (e.g., user-IS communication and influence), and hands-on activity (e.g., specific tasks related to system implementation performed by the users)—will help users develop accurate perceptions of system characteristics and the benefits of the system (Barki & Hartwick, 1994; Hartwick & Barki, 1994). We suggest that if users or their representatives participate in the system development and implementation activities (e.g., system evaluation and customization, prototype testing, business process change initiatives), it is more likely that they will be able to form judgments about job relevance, output quality, and result demonstrability—the important determinants of perceived usefulness. Participation and involvement will lead to a greater understanding of top management's view toward the system and thus, form opinions regarding the social pressure—that is, subjective norm. We further suggest that participation through hands-on activity may reduce anxiety related to system use and can potentially enhance favorable perceptions of external control, perceived enjoyment, and objective usability because the users will have a better understanding of the system features, organizational resources, and supports pertinent to the system.
While prior research has suggested the importance of user participation and involvement in predicting system success, there is a need to understand whether, how, and why user participation and involvement influence the determinants of perceived usefulness and perceived ease of use, particularly in the context of complex systems. Such an understanding will help managers make decisions about effective change management strategies. Some illustrative research questions are:
- (i)
For what type of system is user participation an effective preimplementation intervention?
- (ii)
Should all potential users be involved in a project or can a subset of users be involved? What is the optimal number of users who should be involved?
- (iii)
What are the effects of the different ways of user participation (e.g., joint application development, membership in project team, preview of system, and business process characteristics) on the key determinants of perceived usefulness and perceived ease of use and consequently, perceived usefulness and perceived ease of use?
Management support
Management support refers to the degree to which an individual believes that management has committed to the successful implementation and use of a system. While management support has been suggested as an important antecedent of IT implementation success (e.g., Markus, 1981; Leonard-Barton & Deschamps, 1988; Jarvenpaa & Ives, 1991; Sharma & Yetton, 2003; Liang, Saraf, Hu, & Xue, 2007), it was not conceptualized as an intervention that can influence the determinants of user acceptance. Jasperson et al. (2005) suggested that managers (e.g., direct supervisors, middle managers, and senior executives) are important sources of interventions. Management can intervene indirectly (e.g., sponsoring or championing, providing resource, and issuing directives and/or mandates) or directly (e.g., using features of IT, directing modification or enhancement of IT applications, incentive structures, or work tasks/processes) in the implementation process of an IT (Jasperson et al., 2005). Prior research has suggested one of the most critical success factors for complex systems (e.g., enterprise systems) is management support and championship (Holland & Light, 1999; Purvis, Sambamurthy, & Zmud, 2001; Chatterjee, Grewal, & Sambamurthy, 2002; Liang et al., 2007). Because the implementation of these systems often requires substantial changes to organizational structure, employees' roles and jobs, reward systems, control and coordination mechanisms, and work processes, top management's support in the form of commitment and communication related to system implementation is absolutely critical for the legitimacy of the implementation process and employee morale following the implementation. We suggest management support can influence users' perceptions of subjective norm and image—two important determinants of perceived usefulness. We further suggest that management support, particularly in the form of direct involvement in the system development and implementation processes (Jasperson et al., 2005), will help employees form judgments regarding job relevance, output quality, and result demonstrability of a system. The direct involvement of management in the modification of system features, incentive structures, and work processes will reduce anxiety related to the impact and use of the system and, hence, will influence the determinants of perceived ease of use such as perceptions of external control.
While management support has been conceptualized and operationalized as organizational mandate and compliance, particularly in the individual-level IT adoption literature, we suggest that there is a need to develop a richer conceptualization of management support to enhance our understanding of its role in IT adoption contexts. We suggest that social network theory and analysis (e.g., Burkhardt & Brass, 1990; Burt, 1992), and leader–member exchange (LMX) theory (e.g., Liden, Sparrowe, & Wayne, 1997) can be used to understand the influence of management support in IT adoption and use. Social network analysis can help pinpoint the mechanisms through which management support can influence the determinants of perceived usefulness and perceived ease of use. Examples of research questions are:
- (i)
What forms of management support (e.g., indirect or direct actions) are important in creating favorable perceptions toward a new system?
- (ii)
What are the effective modes of managerial communication to express support toward a new system?
- (iii)
How does organizational mandate differ from managerial support? Which one of these is more effective for complex systems implementations?
Incentive alignment
Incentive alignment has been suggested as the third dimension in systems design (Ba, Stallaert, & Whinston, 2001). The other two dimensions are software engineering and technology acceptance (Ba et al., 2001). Ba et al. (2001) argued that while aspects of software engineering (e.g., system characteristics) and technology acceptance (e.g., perceived usefulness, perceived ease of use, user satisfaction) are important considerations for system development processes, organizations may fail to gain expected benefits from employees' effective utilization of a system unless employees find that the system features and capabilities are aligned with their interests and incentives. For example, even if a system is of high quality, from a system engineering point of view and users may develop positive attitudes toward the system from a technology acceptance point of view, it may not lead to positive organizational outcomes if there are no incentives in place for the users for using the system effectively. There is limited research on the role of incentive alignment in IT adoption contexts. However, in decision support systems and group support systems use contexts (e.g., Mennecke & Valacich, 1998; Speier et al., 2003), incentive has been found to be an important factor (see Todd & Benbasat, 1999). We suggest that incentive alignment can be an important intervention in the preimplementation stage that can potentially enhance user acceptance. According to Ba et al. (2001), incentive alignment does not necessarily mean organizational rewards for using a system. It is a broad concept that entails an individual's perception that the IT fits with his or her job requirements and value system. For example, in the context of enterprise systems, if an individual perceives that his or her use of the system does not benefit the members of his or her work units but rather benefits members from other work units, the user will perceive a lack of incentive alignment that may lead to low user acceptance and use of the system. Incentive alignment can potentially influence employees' perceptions of job relevance, output quality, and results demonstrability of a system. Given that their use of the system will be noticed and rewarded by the management, incentives can influence subjective norm and image. Further, incentive alignment, and an important extrinsic reward, may reduce anxiety and increase perceived enjoyment as extrinsic rewards are considered important drivers of intrinsic motivations (Vallerand, 1997; Deci, Koestner, & Ryan, 1999; Ryan & Deci, 2000).
We believe that there can be many fruitful avenues of research on the role of incentive alignment in the context of IT adoption. Two examples of relevant research questions are:
- (i)
What is the role of incentive alignment in determining perceived usefulness and perceived ease of use of a system?
- (ii)
How can organizational incentive structure be incorporated in the configuration of a system? How does such incorporation enhance user acceptance of such systems?
Postimplementation Interventions
Postimplementation interventions represent a set of organizational, managerial, and support activities that take place after the deployment of a system to enhance the level of user acceptance of the system. While preimplementation interventions are designed and implemented in order to reduce initial resistance and develop realistic perceptions of system features, capabilities, and relevance, postimplementation interventions can be crucial to help employees go through the initial shock and changes associated with the new system. When employees start using a new system, as noted earlier, they are more likely to experience substantial changes to their intrinsic job characteristics, work processes, routines, and habits (Millman & Hartwick, 1987). Some employees may react favorably to these changes, while the others may perceive these changes as a threat to their well-being (Orlikowski, 2000; Boudreau & Robey, 2005). During postimplementation stages, employees attempt to cope with the new system in different ways depending on whether they perceive the system as a threat (or an opportunity) and whether they have control over the system (Beaudry & Pinsonneault, 2005). For example, if employees perceive that a new system is a threat to their well-being and they do not have necessary resources and abilities to use the system, it is more likely that they will try to avoid the new system (Beaudry & Pinsonneault, 2005). In keeping with this, postimplementation interventions should make employees feel that a new system is an opportunity to enhance their job performance and they have abilities and necessary resources to use the new system effortlessly.
Training
Training has been suggested as one of the most important postimplementation interventions that leads to greater user acceptance and system success (see Sharma & Yetton, 2007). While training can be conducted before or during implementation of a new system, we consider training as a postimplementation intervention because, in most cases, training is conducted after a system is deployed and ready to be used by potential users. Much prior research has suggested the critical role of training in enhancing IT adoption and use (e.g., Wheeler & Valacich, 1996; Venkatesh, 1999; Venkatesh & Speier, 1999). One of the key reasons for training to be an important intervention is that different modes of training can be used to manipulate different determinants of IT adoption. For example, Venkatesh (1999) found that game-based training was more effective than traditional training to enhance user acceptance of a new system. He also found that the effect of perceived ease of use on behavioral intention to use a system was stronger for individuals who received game-based training. Venkatesh and Speier (1999) investigated the effect of mood during training on user acceptance and found that mood during training played an important role in forming individuals' perceptions of a new IT. These findings indicate that training can be used to help users develop favorable perceptions of different determinants of perceived usefulness and perceived ease of use. However, much of the prior research on training in the context of IT adoption has been conducted for simple ITs, such as word processing and e-mail. We suggest that the role of training will be even more important in the context of complex systems (e.g., enterprise systems) that are more central to employees' work life. As these systems are more likely to invoke negative reactions from employees because of their disruptive nature, effective training interventions can mitigate these negative reactions and help employees form favorable perceptions toward these systems.
The research on modes and effectiveness of training in the context of IT use is rich (e.g., Davis & Bostrom, 1993; Venkatesh, 1999; Venkatesh & Speier, 1999; Davis & Yi, 2004). But there is still a need for more granular understanding of the effects of different training modes on the determinants of IT adoption. Some examples of research questions are:
- (i)
Which training method is the most effective for enhancing the determinants of perceived usefulness and perceived ease of use?
- (ii)
To achieve greater user acceptance, when is the appropriate time for training—early in the development stage or later part of the development?
- (iii)
Should there be separate training for business processes during the implementation of complex systems that require business process changes? How and why does training on business process influence user acceptance of these technologies?
Organizational support
Organizational support refers to informal or formal activities or functions to assist employees in using a new system effectively. Organizations can provide support in various forms—providing necessary infrastructure, creating dedicated helpdesks, hiring system and business process experts, and sending employees to off-the-job training. In the postimplementation stage, the presence of different types of support is very important, particularly in the context of complex systems, (e.g., enterprise systems) that are inherently difficult to understand and use (e.g., Bajwa, Rai, & Brennan, 1998). Prior research has suggested that employees' perceptions regarding organizational support—that is, facilitating conditions or perceptions of external control (Taylor & Todd, 1995; Venkatesh, 2000; Venkatesh et al., 2003)—will lead to greater user acceptance of new systems. Jasperson et al. (2005) noted the importance of internal or external experts as sources of interventions. Organizational support captures the role of both internal and external experts who can help users deal with the complexity associated with new systems as well as business processes. These experts can help users modify or enhance the IT applications or work processes (Jasperson et al., 2005). Thus, organizational support can play a key role in determining perceived usefulness and perceived ease of use. For example, experts can help employees modify certain aspects of a new system, thus increasing job relevance, output quality, and results demonstrability of a system. TAM3 posits that perceptions of external control are important and stable determinants of perceived ease of use. Organizational support is a key source of perceptions of external control. Further, the presence of organizational support, particularly in the context of complex systems, can reduce anxiety associated with system use.
While the notion of organizational support has been captured in the IT adoption literature through facilitating conditions and/or perceptions of external control, we suggest that it is important to understand the specific role of different types of organizational support that may influence different determinants of perceived usefulness and perceived ease of use. Examples of research questions are:
- (i)
How should organizational support structure be designed for complex systems (e.g., enterprise systems) that require both technology and domain-specific business process knowledge for the users and support personnel?
- (ii)
How and why do different forms of organizational support (e.g., infrastructure, helpdesks, system and business process experts, and off-the-job training) influence the determinants of perceived usefulness and perceived ease of use?
Peer support
Peer support refers to different activities and/or functions performed by coworkers that may help an employee effectively use a new system. Jasperson et al. (2005) suggested that coworkers from the same or different business units and workers in other organizations can be important sources of interventions leading to greater user acceptance of a system. They suggested three intervention actions related to peers: (i) formal or informal training; (ii) direct modification or enhancement of IT system or work processes; and (iii) joint (with users) modification or enhancement of work processes. We suggest that these interventions can influence the determinants of perceived usefulness and perceived ease of use in several ways. First, peer support through formal and informal training can enhance users' understanding of a system. Thus, users may get insights from their peers on job relevance, output quality, and result demonstrability of a system. Second, the modification and enhancement activities performed by peers will increase job relevance of a system, improve the output quality of a system, and reduce anxiety related to system use. Finally, peer support may also influence subjective norm and image associated with using a system. If coworkers are favorable toward a new system, it is more likely that employees will form favorable perceptions toward the system through social influence processes (Venkatesh & Davis, 2000).
While peer support is potentially an important intervention that can lead to greater user acceptance, there is little or no research on the role of peer support in the context of IT adoption. We urge IS researchers to investigate how peer support can enhance user acceptance by influencing the determinants of perceived usefulness and perceived ease of use. We believe that social network theory and analysis, and team member exchange (TMX) theory (Seers, 1989) can be used to understand the influence of peer support in IT adoption and use. Some research questions are:
- (i)
How and why does peer support enhance perceived usefulness and perceived ease of use of a system? Does peer support have a differential influence on perceived usefulness and perceived ease of use in different cultural contexts (e.g., Straub, Keil, & Brenner, 1997)?
- (ii)
What types of intervention actions related to peer support are more effective in enhancing perceived usefulness and perceived ease of use of systems?
DISCUSSION
We had three objectives in this research: (i) developing a comprehensive nomological network (integrated model) of the determinants of individual level (IT) adoption and use; (ii) empirical testing of the proposed integrated model; and (iii) presenting a research agenda focused on potential pre- and postimplementation interventions that could enhance employees' adoption and use of IT. To accomplish our first objective, we integrated the models proposed by Venkatesh and Davis (2000) and Venkatesh (2000) and developed a comprehensive nomological network of IT adoption and use—TAM3. We accomplished the second objective by testing the integrated model in longitudinal field studies conducted at four different organizations. Finally, we accomplished the third objective by presenting a set of interventions and an agenda of future research on these interventions. We discussed how and why these interventions may influence the determinants of perceived usefulness and perceived ease of use.
Theoretical Contributions
Our research makes several important theoretical contributions. We present a complete nomological network of the determinants of IT adoption and use—TAM3. The key strength of TAM3 is its comprehensiveness and potential for actionable guidance. While TAM presented a parsimonious model, the follow-up research on the general determinants of perceived usefulness and perceived ease of use presented pointers to constructs that could be levers. The current work adds richness and insights to our understanding of user reactions to new ITs in the workplace. Comprehensiveness and parsimony have their own merits in theory development (e.g., Dubin, 1976; Bacharach, 1989; Whetten, 1989). While comprehensiveness ensures whether all relevant factors are included in a theory, parsimony dictates whether some factors should be deleted because they add little value to our understanding of a phenomenon (Whetten, 1989). We suggest that the comprehensiveness of TAM3 is important as we now move more toward a research agenda related to various interventions.
TAM3 emphasizes the unique role and processes related to perceived usefulness and perceived ease of use and theorizes that the determinants of perceived usefulness will not influence perceived ease of use and vice versa. This is an important theoretical contribution by itself because there have been many inconclusive findings regarding the relationships among some of these determinants, perceived usefulness, and perceived ease of use. For example, Agarwal and Karahanna (2000) found that computer self-efficacy was a significant determinant of perceived usefulness. However, Venkatesh (2000) found that perceived ease of use fully mediated the effect of computer self-efficacy on behavioral intention. We provided the theoretical justification and empirical support of why the determinants of perceived ease of use (e.g., computer self-efficacy) will not have significant effects on perceived usefulness over and above the known determinants of perceived usefulness that are driven by the social influence and cognitive instrumental processes. For example, while self-efficacy may have weak influence on perceived usefulness as shown in Agarwal and Karahanna (2000), we argue that this influence will become nonsignificant in the presence of other important social and cognitive constructs.
TAM3 posits new theoretical relationships such as the moderating effects of experience on key relationships. Experience is an important moderating variable in IT adoption contexts because, as suggested in much prior research, individuals' reactions toward an IT may change over time (Karahanna et al., 1999; Bhattacherjee & Premkumar, 2004). The changing perceptions can play an important role in determining individuals' continuance intention and long-term use of a system (Bhattacherjee, 2001). While initial adoption is important, long-term use of a system is a key measure of ultimate success of a system (Rai et al., 2002; DeLone & McLean, 2003). Therefore, it is important to understand the role of experience in IT adoption and use contexts (Venkatesh et al., 2003). TAM3 posits that with increasing experience, while the effect of perceived ease of use on behavioral intention will diminish, the effect of perceived ease of use on perceived usefulness will increase. This clearly indicates that perceived ease of use is still an important user reaction toward IT even if users have substantial hands-on experience with the IT. This important theoretical relationship has significant practical utility as there has been increasing concerns about the ease of use of various ITs, particularly enterprise systems that are inherently complex to understand and use. There have been numerous cases of enterprise system failures because of user resistance. In many cases, the users stopped using an enterprise system, as they saw no benefits of using the new system. It is possible that a lack of perceived ease of use contributed to unfavorable perceptions of perceived usefulness in the context of those systems.
Finally, our most important theoretical contribution is the delineation of relationships among the suggested interventions and the determinants of perceived usefulness and perceived ease of use. While prior research (e.g., Venkatesh, 1999) has suggested important relationships between interventions (e.g., training) and key IT adoption determinants, we extend this research by providing a comprehensive list of interventions, suggesting potential relationships of these interventions with the determinants of perceived usefulness and perceived ease of use, and offering important future research directions. Our key argument in this article is that unless organizations can develop effective interventions to enhance IT adoption and use, there is no practical utility of our rich understanding of IT adoption. However, there is little or no scientific research aimed at identifying and linking interventions with specific determinants of IT adoption. The importance of interventions in enhancing IT adoption was underscored by Venkatesh (1999) who provided an example of how different modes of training can be used to manipulate system-specific enjoyment which enhanced the salience of perceived ease of use of a system as a determinant of behavioral intention. Our theoretical arguments about the relationships between the interventions and the determinants of IT adoption are thus an important contribution that could direct future research.
Implications for Decision Making
We suggest that our findings and research agenda focusing on interventions have direct implications for two types of decision making in organizations—(i) employees' IT adoption decisions; and (ii) managerial decisions about managing IT implementation process. Further, given that ITs are becoming increasingly complex and pertinent to employees' decision making and work processes, this research has implications for broad IT-enabled organizational decision making (e.g., collaborative forecasting, inventory management, replenishment, service delivery). Our discussion of interventions primarily focuses on these complex ITs to understand how pre- and postimplementation interventions can help employees make better adoption decisions about these complex systems and managers make effective implementation decisions. This is consistent with Venkatesh (2006) who argued that in order to be relevant to organizational decision-making processes, individual-level IT adoption research should focus on phenomena that are pertinent to decision making (e.g., knowledge sharing, business process outsourcing) and ITs that are critical for organizational decision making (e.g., enterprise resource planning, supply chain management, collaborative forecasting, inventory management systems). The interventions and future research agenda discussed here have implications for these types of phenomena and systems.
Due to the complexity of ITs, it is increasingly difficult for employees to make effective decisions about adoption, utilization, and coping with new ITs. As discussed earlier, implementation of complex ITs (e.g., enterprise systems, interorganizational systems) and associated changes in business processes have a profound impact on employees' job and cause changes in their job characteristics, relationships with others in the workplace, and other aspects of their job (Boudreau & Robey, 2005; Lapointe & Rivard, 2005). Consequently, employees' job outcomes (e.g., job satisfaction and job performance) can be affected. Due to the magnitude of these impacts, employees are reluctant to adopt new ITs (Lapointe & Rivard, 2005). Other types of reactions, such as avoidance, sabotage, workarounds, and shortcuts are also prevalent. Interventions that we discuss here can help employees make appropriate decisions about adopting and utilizing a new IT. For example, in the context of enterprise systems, certain design characteristics (e.g., extent of customization or complexity of the system) can reduce changes in employees' jobs as these characteristics can potentially enhance the fit between a system and employees' jobs. Some other interventions (e.g., user participation, training) can help employees decide how to cope with or adapt a new IT (Beaudry & Pinsonneault, 2005). Venkatesh (2006) called for work on employees' reactions to business process changes and process standards implementation. We suggest that interventions discussed in this article can help organizations generate favorable individuals' reactions toward business process changes and process standards implementation.
Our findings and discussion of interventions can support managerial decision making in two ways. First, managers will now have a framework to decide what interventions to apply during pre- and postimplementation stages and for what types of system. For instance, (i) for a complex system, perhaps, interventions that will create favorable ease of use perceptions will be relevant (e.g., design characteristics, user participation, training, and peer support); (ii) for a voluntary system, interventions that will influence the determinants of perceived usefulness will be important to implement (e.g., design characteristics, user participation, incentive alignment, training, organizational and peer support); and (iii) for interorganizational systems that affect organizational business processes (e.g., Saeed, Malhotra, & Grover, 2005) or a customer relationship management system that is critical to service delivery (e.g., Froehle, 2006), interventions, such as user participation, peer support, and management support, will be particularly relevant. Second, managers can decide on resource allocation for interventions based on the impact of interventions on different determinants of IT adoption and type of systems. For example, if design characteristics cannot be changed in a system, managers can allocate more resources to training and user participation to make employees familiar with the systems. The implementation of interventions is, of course, not a silver bullet for greater IT adoption and effective utilization. Implementation of interventions can increase system development costs substantially. Hence, managers have to be mindful in their decisions about implementing interventions and our work identifies specific interventions that can serve as levers for managers.
CONCLUSIONS
ITs are becoming increasingly complex and implementation costs are very high. Implementation failures of many of today's ITs cost millions of dollars for organizations. Further, low adoption and high underutilization of ITs have been a major problem for organizations in terms of realizing the benefits (both tangible and intangible) of IT implementations (Jasperson et al., 2005). If we can develop a rich understanding of the determinants of IT adoption and use and interventions that can favorably influence these determinants, managers can proactively decide on implementing the right interventions to minimize resistance to new ITs and maximize effective utilization of ITs. Based on a comprehensive nomological network of IT adoption and use—TAM3—we presented a set of pre- and postimplementation interventions that we believe should be the object of future scientific inquiry.
Appendix
| Constructs | Itemsa | |
|---|---|---|
| Perceived Usefulness (PU) | PU1 | Using the system improves my performance in my job. |
| PU2 | Using the system in my job increases my productivity. | |
| PU3 | Using the system enhances my effectiveness in my job. | |
| PU4 | I find the system to be useful in my job. | |
| Perceived Ease of Use (PEOU) | PEOU1 | My interaction with the system is clear and understandable. |
| PEOU2 | Interacting with the system does not require a lot of my mental effort. | |
| PEOU3 | I find the system to be easy to use. | |
| PEOU4 | I find it easy to get the system to do what I want it to do. | |
| Computer Self-Efficacy (CSE) | I could complete the job using a software package … | |
| CSE1 | … if there was no one around to tell me what to do as I go. | |
| CSE2 | … if I had just the built-in help facility for assistance. | |
| CSE3 | … if someone showed me how to do it first. | |
| CSE4 | … if I had used similar packages before this one to do the same job. | |
| Perceptions of External Control (PEC) | PEC1 | I have control over using the system. |
| PEC2 | I have the resources necessary to use the system. | |
| PEC3 | Given the resources, opportunities and knowledge it takes to use the system, it would be easy for me to use the system. | |
| PEC4 | The system is not compatible with other systems I use. | |
| Computer Playfulness (CPLAY) | The following questions ask you how you would characterize yourself when you use computers: | |
| CPLAY1 | … spontaneous | |
| CPLAY2 | … creative | |
| CPLAY3 | … playful | |
| CPLAY4 | … unoriginal | |
| Computer Anxiety (CANX) | CANX1 | Computers do not scare me at all. |
| CANX2 | Working with a computer makes me nervous. | |
| CANX3 | Computers make me feel uncomfortable. | |
| CANX4 | Computers make me feel uneasy. | |
| Perceived Enjoyment (ENJ) | ENJ1 | I find using the system to be enjoyable. |
| ENJ2 | The actual process of using the system is pleasant. | |
| ENJ3 | I have fun using the system. | |
| Objective Usability (OU) | No specific items were used. It was measured as a ratio of time spent by the subject to the time spent by an expert on the same set of tasks. | |
| Subjective Norm (SN) | SN1 | People who influence my behavior think that I should use the system. |
| SN2 | People who are important to me think that I should use the system. | |
| SN3 | The senior management of this business has been helpful in the use of the system. | |
| SN4 | In general, the organization has supported the use of the system. | |
| Voluntariness (VOL) | VOL1 | My use of the system is voluntary. |
| VOL2 | My supervisor does not require me to use the system. | |
| VOL3 | Although it might be helpful, using the system is certainly not compulsory in my job. | |
| Image (IMG) | IMG1 | People in my organization who use the system have more prestige than those who do not. |
| IMG2 | People in my organization who use the system have a high profile. | |
| IMG3 | Having the system is a status symbol in my organization. | |
| Job Relevance (REL) | REL1 | In my job, usage of the system is important. |
| REL2 | In my job, usage of the system is relevant. | |
| REL3 | The use of the system is pertinent to my various job-related tasks. | |
| Output Quality (OUT) | OUT1 | The quality of the output I get from the system is high. |
| OUT2 | I have no problem with the quality of the system's output. | |
| OUT3 | I rate the results from the system to be excellent. | |
| Result Demonstrability (RES) | RES1 | I have no difficulty telling others about the results of using the system. |
| RES2 | I believe I could communicate to others the consequences of using the system. | |
| RES3 | The results of using the system are apparent to me. | |
| RES4 | I would have difficulty explaining why using the system may or may not be beneficial. | |
| Behavioral Intention (BI) | BI1 | Assuming I had access to the system, I intend to use it. |
| BI2 | Given that I had access to the system, I predict that I would use it. | |
| BI3 | I plan to use the system in the next <n> months. | |
| Use (USE) | USE1 | On average, how much time do you spend on the system each day? |
- aAll items were measured on a 7-point Likert scale (where 1: strongly disagree; 2: moderately disagree, 3: somewhat disagree, 4: neutral (neither disagree nor agree), 5: somewhat agree, 6: moderately agree, and 7: strongly agree), except computer self-efficacy, which was measured using a 10-point Guttman scale.
Viswanath Venkatesh is a professor and the George and Boyce Billingsley Chair in Information Systems at the Walton College of Business, University of Arkansas. His research focuses on understanding technology in organizations and homes. His research has been published in leading information systems, organizational behavior, and psychology journals. He has served on or is currently serving on the editorial boards of MIS Quarterly, Information Systems Research, Management Science, Journal of the AIS, and Decision Sciences.
Hillol Bala will start, effective July 2008, as an assistant professor of information systems at the Kelley School of Business, Indiana University, Bloomington. He is expected to complete his PhD in Information Systems at the Walton College of Business, University of Arkansas in 2008. He received his MBA and MS degrees from Texas Tech University. His research interests are IT-enabled business process change and management, post-adoption IT use and impact, and strategic use of IT in health care. His research articles have been accepted for publication or published in MIS Quarterly, Information Systems Research, Communications of the ACM, MIS Quarterly Executive, and The Information Society.




