[Retracted] Data Encryption Technology Analysis of Robot Computer Network Information
Abstract
In order to ensure the security of robot computer network information, a data encryption technology is proposed. Through the comprehensive research of symmetric cryptography algorithm, open cryptography algorithm, hybrid encryption algorithm, AES algorithm, quantum cryptography technology, and ECC algorithm, a data encryption method suitable for robot computer network information is proposed. It is found that when analyzing the entanglement characteristics of the four-particle cluster state, the anomaly will inevitably disturb its state. In the eavesdropping detection, the communication parties can cooperate to detect the existence of abnormal conditions. In addition, in the formal communication stage, trial photons are introduced, whose confidentiality characteristics are guaranteed by the principle of quantum noncloning and the uncertainty principle. Therefore, this technology further ensures the confidentiality of communication.
1. Introduction
Today, with the widespread use of computer networks, more and more people are connected to this technology. The use of computers has been constantly improving and improving in all walks of life. With the advent of big data and cloud computing, data is emerging quickly and slowly in all areas of human life. However, with the widespread use of computers, information is still lost [1]. Therefore, the problem of computer network information security has become an urgent problem for relevant people to solve, and data encryption technology can prevent information leakage to a great extent (Figure 1). As a new network information protection measure, this technology has been recognized and accepted by more and more people in the shortest time after its emergence [2].

At present, all enterprises need to use computers to exchange information. In the process of using computers, data encryption technology plays an important role, which is related to the security of computer use. The continuous development of social economy has also expanded the application rate of electronic information technology and increased the challenges of technology application [3]. Because computer networks are open and can share information with everyone, it is easy to divulge personal information and lose business. As science and technology continue to advance, people are increasingly using computer information, and people are paying more attention to the security of computer information. In terms of computer network information security, we need to use data encryption technology to create a secure network for people.
The use of information technology in various fields in China has led to the frequency of network exchange. In addition, China continues to improve the openness of the network, which further increases people’s access to information, so it increases the risk of network information data. At present, people attach great importance to the security of network environment, so as to highlight the importance of data encryption technology. Through the analysis of this paper, this paper puts forward corresponding measures for the network security of robot computer [4].
2. Literature Review
The idea of publishing the key was first published in “New Cryptographic Concepts,” which laid a solid foundation for the development of public cryptosystem information [5]. Several important public cryptosystems were then requested one by one. Several important public cryptosystems were then requested one by one, for example, the famous RSA public key cryptosystem,knapsack cryptosystem,Rabin cryptosystem, ELGamal cryptosystem,elliptic curve cryptosystem and so on. An oval curve cryptosystem (ECC) based on the theory of the oval curve can solve the problem of a very large key, and it is the same. Security level is according to RSA and ElGamal. The DCF mechanism in the MAC layer of the IEEE802.11 protocol has been studied, researched, and developed [6]. The improvements improve the use of the channel and make it more robust in two stages of “virtual racing.” The simplicity and exclusion of IEEE802.11 validation protocol service support have been well studied. Based on the 802.1x protocol framework and the EAP protocol, we offer a concept to improve password-based authentication. For some people, the input can meet the security requirements of WLAN authentication and improve 802.11i authentication. To improve the security of the IEEE802.1x protocol, the concept can improve process security by preventing the authentication of the IEEE802.1x protocol by authenticating the authentication mark. It also sets out the principles that easily oppose the 802.1x protocol—incompatibility, incompleteness, integrity, and precision protection of the latest systems true. An improved version of bilateral cooperation and offline evaluation was planned and implemented [7].
However, the security performance of a WLAN is not as stable as that of a wired network. Currently, the most widely used WLAN is the 802.11 series. Although 802.1x has some disadvantages of the 802.11 standard, it still has some disadvantages. The protocol explains why there are no authentication methods between the user and the authenticator and prevents the authentication message from being encrypted. Illegal users can use these issues to detect various attacks [8]. There are three main types of attacks: one is a false witness attack, the other is a conversation-stolen attack, and the third is a denial of service termination. To some extent, these security vulnerabilities have led to the development of wireless network-based robotic remote control technology. Improving the security of wireless network-based robot remote control technology will not only make WLAN more important for robot development, research, and application but also make wireless remote control technology safer and easier to use. This is essential for the development and improvement of robotic remote control technology, the promotion and popularization of robots in various fields, and the robotics industry in China, especially the robotics industry. Therefore, how to ensure the security of data transmission during robotic wireless remote control is an important prerequisite to support the continuous expansion of robotic information. But so far, people have not seen the security of robotic remote control systems in wireless networks. Currently, the issues of wiretapping, forgery, and unauthorized surveillance are not given enough attention, like a remote-controlled bomb, and the remote control is in the hands of unauthorized people.
This paper mainly studies the security authentication access problem based on wireless network, that is, taking the wireless LAN security technology as the core, the improvement of IEEE802.1x/EAP-TLS protocol, and the research and application of quantum technology through symmetric cryptographic algorithm, public cryptographic algorithm, hybrid encryption algorithm, AES algorithm, quantum cryptographic technology, and ECC algorithm to improve the security performance of robot computer network [9].
3. Research Methods
3.1. Symmetric Cryptographic Algorithm
Symmetric encryption uses the same keys to encrypt and decrypt data. The algorithms used for symmetric encryption are simpler than for asymmetric encryption. Because these algorithms are simpler and use the same key to encrypt and decrypt data, symmetric encryption is faster than asymmetric encryption. Therefore, symmetric encryption is suitable for encrypting and decrypting large amounts of data. Figures 2 and 3 show the symmetric encryption process [10].
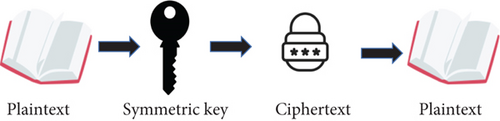
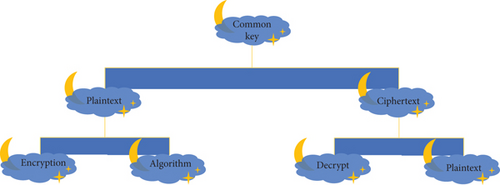
One disadvantage of multiple encryption is that it can encrypt and decrypt data using a single key. Therefore, all senders and recipients must know or have access to the encryption key. This requires organizations to consider the importance of environmental safety management and governance. The reason for the security management problem is that the organization must send this encryption key to any party that needs access to the encrypted data. Key management issues that an organization should consider include key indicators, allocation, resources, recovery, and life cycle. Symmetric encryption allows encrypted data [11]. For example, using symmetric encryption, you can be sure that only two parties with access to an organization’s shared encryption key can decrypt the encrypted text. However, symmetric encryption does not provide authentication. For example, when many users access a shared encryption key, symmetric encryption cannot identify the sender of the file.
3.2. Public Cipher Algorithm
Traditional symmetric encryption algorithms face key management problems. If the key is lost during distribution and transmission, the entire security system will be damaged. Asymmetric encryption algorithms effectively avoid problems with partitions and control keys. Pair combinations of public and private keys are used in asymmetric cryptography [12]. Encrypted text encrypted with a public key can only be decrypted with a private key. Conversely, encrypted text encrypted with a private key can only be decrypted with a public key. As we work, we place the public key to the outside world to let outsiders know. We keep the key secret and only we can know. If you want to send a password, all you have to do is take the public key and then encrypt the password with the public key. This encrypted message can only be decrypted with a private key. Instead, you can use a public key to keep your information private. The file was sent by a third party, but could not be decrypted.
Sometimes, messages are encrypted with a private key and decrypted with a public key used for digital signing. Although confusion can occur, these actions can be expressed in equations (1) and (2), respectively.
Currently, public key cryptographic algorithms are based on complex mathematical problems. For example, the widely used RSA algorithm is based on the popular mathematical problem of large integers. The advantage of a public key cryptosystem is that it can meet network openness requirements, and the management key is simple and knows the function of digital signature and ID verification. It is the mainstay of today’s e-commerce and other technologies [13]. The disadvantage is that the algorithm is complex and the speed and efficiency of data encryption is low. Therefore, in practice, symmetric encryption algorithms and asymmetric encryption algorithms are often used together. Symmetric encryption algorithms are used to encrypt large data files, while symmetric encryption algorithms are used to replace the key used by the symmetric encryption algorithm. This method can increase the efficiency of encryption and simplify key management [14].
3.3. Hybrid Encryption Algorithm
Hybrid encryption is an encryption method that performs data encryption with a combination of symmetric and asymmetric encryption. The hybrid encryption method takes advantage of these two encryption methods to allow only the desired recipient to read the data [15].
In the concept of hybrid encryption, an organization provides symmetric encryption with a randomly generated key to encrypt the data. These steps take advantage of symmetric encryption speeds. The organization then encrypts the symmetric encryption key using the public key of the asymmetric key pair. These steps take advantage of the high security of asymmetric encryption. Encrypted data is sent to the recipient’s data with an encrypted symmetry key [16].
To decrypt the data, the receiver first needs to decrypt the symmetric encryption key using the private key of the asymmetric key pair. The receiver then decrypts the data using the decrypted symmetric key.
3.4. AES Algorithm
The AES algorithm is an important symmetric teratonic block cipher algorithm. Its package length and key length are different. They can be listed as 128 items, 192 items, or 256 items. It contains plain text data files in the form of a two-dimensional byte array, called a state array. The array consists of 4 lines and Nb lines (Nb is equal to the length of the set divided by 32). Any changes to the AES algorithm are made on this state matrix. As an example, take AES-128 (key length 128 bits) and display the plain text input groups a0, a1, a2 … a15 in a state matrix between 4 lines and 4 lines. Many iterations are performed on this state matrix to achieve the goal of free data confusion, expansion, and data encryption. Each circular variable is called an environment and has a total Nr +1 environment [17].
From the above four transformations, it can be seen that the decryption of AES algorithm process only converts the transformation of each round of function into the corresponding inverse transformation and transforms the state matrix obtained from ciphertext mapping in the opposite order.
3.5. Quantum Cryptography
Traditional cryptography is based on the difficulty of mathematical calculation, while quantum cryptography is based on quantum mechanics. In fact, quantum cryptography is an absolutely secure cryptosystem based on quantum properties. This is because if eavesdroppers want to steal communication information, they must measure the quantum system, which disrupts the balance of quantum channels and causes both sides of communication to give up communication [18].
December 21, 2011, was a painful day on the milestone of China’s Internet. According to statistics, in less than ten days, major websites (or forums), including CSDN, Tianya, Renren, Netease, and Saipan, successively leaked important privacy information such as user account, password, and email. With the increasing number of Internet users, more and more people will suffer from the experience of password theft and website hacking.
The emergence of quantum cryptography will make this encounter disappear. The security of quantum cryptography depends on the physical laws based on quantum mechanics. Heisenberg uncertainty principle means that if a quantum state is measured, it will cause some interference to the original quantum state, and the measured quantum state will be different from the original state. Similarly, if a quantum system is measured, the measurement results obtained cannot include the complete information of the original system [19]. According to the uncertainty principle, both sides of communication can detect the existence of eavesdroppers at the first time. Because the eavesdropper cannot guarantee that the original state will not be disturbed when measuring the quantum state on the quantum channel, and once disturbed, the measurement results of both sides of the communication will change, and then, it is found that there is an eavesdropper. At present, the security of quantum state uncertainty principle has been proved, so even computers with supercomputing power are useless.
Data encryption/decryption technology is the basic premise and guarantee of information security. In recent years, quantum key distribution protocol has not only been improved and verified in theory but also made rapid progress in experiment. Although the classical information security technology is progressing day by day, the quantum information security technology has not stagnated. So far, researchers have made good achievements in the theoretical research and experimental research of quantum cryptography [20].
3.6. ECC Algorithm
3.6.1. Operation of Elliptic Curve
(1) Definition of Point Addition Operation. The point addition operation is defined as follows: let P and Q be any two points and l be the PQ connection. If P and Q coincide at one point, that is, P = Q, then l degenerates to the tangent point of P. Let L and curve intersect at another point R, and W is the connecting line between R point and infinity point O; that is, W is the parallel line of y axis through point R, and W and curve intersect at one point m, which is expressed as M = P + Q, that is, the result of point P and Q addition operation. The point addition operation of different points and the same points is shown in Figures 4 and 5.
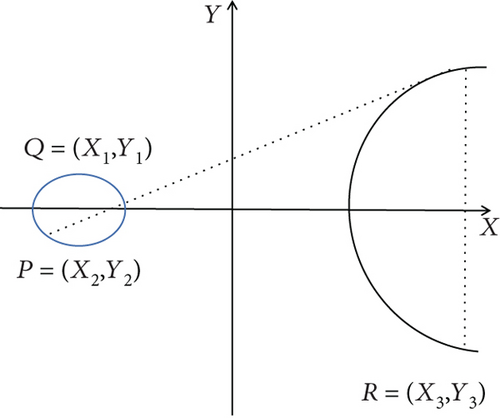
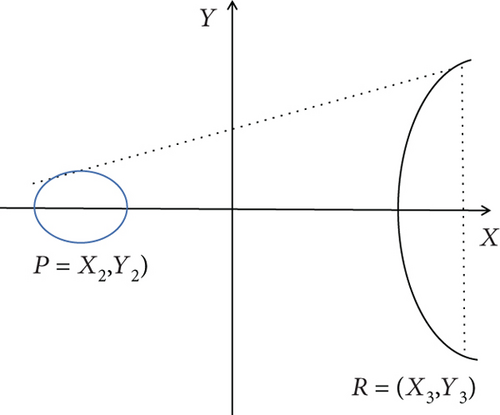
In particular, if P and Q are symmetrical or coincident about the x axis, then the straight line PQ is perpendicular to the x axis, and L and the elliptic curve intersect at infinity O.
- (1)
O + P = P, and P + O = P, then O is the infinity point
- (2)
−O = O
- (3)
P + Q = Q + P
- (4)
P(X, Y) then −P = (X, −Y)
- (5)
if the coordinates of P and Q are the same (their Y coordinates are opposite), then P + Q = O
- (1)
Point addition in affine coordinates
- (a)
Point addition operation of different points
- (a)
- (b)
Point addition operation of the same point
- (2)
Point addition operation in projective coordinates
The point addition operation in projective coordinates is also divided into (a) point addition operation at different points and (b) point addition operation at the same point.
(4) Definition of Point Multiplication. Point multiplication on elliptic curve is one of the core operations of elliptic curve cryptosystem. The point multiplication operation on an elliptic curve is defined as follows: given an elliptic curve E and a point P on the curve, the point multiplication xP of point P on curve e is defined as the sum of the addition of point P and x itself, that is, Xp = p + p + ⋯+p, a total of x P are added. Point multiplication operation (including double point and point addition operation) is one of the most time-consuming arithmetic operations in elliptic curve cryptosystem.
4. Result Analysis
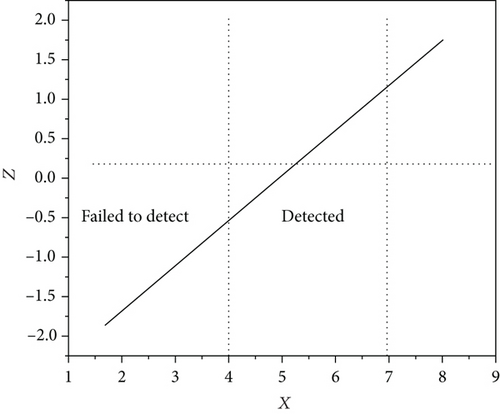
According to the famous Krull-Remak-Schmidt-Azumaya decomposition theorem, when Alice and Bob choose Z-basis for measurement, the error rate is 2FD. Similarly, when X-based measurement is selected, the error rate is 2FD.
To sum up, Eve will inevitably interfere with the entanglement characteristics of four particle cluster states when Alice and Bob analyze their entanglement characteristics [24, 25]. In eavesdropping detection, 2FD > 0, as shown in Figure 6, the existence of Eve can be detected by the cooperation of both communication parties. In addition, in the formal communication stage, exploratory photons are introduced, and their security characteristics are guaranteed by the quantum non cloning principle and uncertainty principle. Therefore, the existence of Eve eavesdropping will also be found, which further ensures the confidentiality of communication.
5. Conclusion
- (1)
The application of cryptography in network information security is deeply studied
- (2)
It is concluded that secret information can be transmitted directly without transmitting password
- (3)
It is concluded that using cluster state as information carrier, the entanglement degree is the largest, the correlation degree is the highest, and the communication efficiency is high
At present, the IEEE 802.11 family is very large, and the updating and improvement of its family protocol is also ongoing. In addition, many researchers outside IEEE organizations continue to study and improve the 802.11 protocol family. China has also put forward the WAPI Standard, but as long as it is announced, someone will find out the defects soon. Although this paper improves the IEEE802.1x/EAP-TLS authentication protocol, it still cannot completely solve the original security defects. Therefore, if we want to fundamentally solve the problem of information security, we must find an absolutely safe way. At present, quantum technology has been proved to be unconditionally safe. If quantum technology can be as developed and mature as computer technology, our information will not be stolen by others.
Conflicts of Interest
The authors declare that they have no conflicts of interest.
Acknowledgments
(1) This work was supported by the education and teaching research project of Xinxiang Medical University (Project No. 2019-XYJG-35). (2) This work was supported by the Henan Provincial Department of Education, Excellent grass-roots teaching organization construction project 2021. (3) This work was supported by the 2021 Higher Education Teaching Reform Research and Practice Project of Henan Province, Research on the construction of professional ideological and political three-dimensional model under CDIO engineering education mode, Project No. 2021SJGLX211.
Open Research
Data Availability
The data used to support the findings of this study are available from the corresponding author upon request.