An Intrusion Detection Scheme Based on Repeated Game in Smart Home
Abstract
Smart Home brings a new people-oriented home life experience. However, the edge devices in this system are facing severe threats such as data security and equipment safety. To solve the above problems, this paper proposes an intrusion detection scheme based on repeated game. We first use the K-Nearest Neighbors (KNN) algorithm to classify edge devices and equip the intrusion detection system to cluster heads. Secondly, we use the regret minimization algorithm to determine the mixed strategy Nash equilibrium of the one-order game and then take a severe punishment strategy to domesticate malicious attackers. Thirdly, the intrusion detection system can detect malicious attackers by reduction of payoff. Finally, the detailed experimental results show that the proposed scheme can reduce the loss of attacked intrusion detection system and then achieve the purpose of defending against the attacker.
1. Introduction
Internet of things (IoT) is entering people’s lives and makes the production and life of human beings more intelligent and convenient. Smart Home is a typical application of the IoT [1]. Smart Home integrates integrated wiring technology and network communication technology and is an effective management system [2]. However, Smart Home is facing severe security threats such as data security and device security [3]. The distribution of edge devices is too scattered to apply security technologies in a Smart Home. Besides, some equipment uses outdated versions that are unable to remotely upgrade weaknesses and vulnerabilities, making Smart Home devices vulnerable to attacks. For instance, equipment such as cameras and smart thermostats collect information about people’s daily lives which can be traced directly or indirectly back to the person. Once the data of Smart Home devices is stolen, users’ private information will be disclosed. Therefore, it is urgent to design an effective security protection scheme to ensure user data security in the Smart Home.
Intrusion detection technology is a method to resist the attacker invasion, which can monitor, analyze, and deal with a variety of intrusions without affecting network performance as much as possible to improve the ability of networks to deal with external threats. According to the technology used, intrusion detection technology can be divided into three categories: anomaly detection, misuse intrusion detection, and hybrid intrusion detection. The abnormal detection technology can detect the new intrusion, but it is difficult to establish the attacker’s behavior model [4]. Misuse detection technology has high detection accuracy, but it is difficult to collect and update intrusion information [5]. Hybrid intrusion detection technology combines misuse detection and anomaly detection, inherits the advantages of both, improves the detection rate, and decreases false positive rate [6]. To sum up, the existing intrusion detection technologies mainly have the following shortcomings: the volume of data is too difficult to process and the data dimension is too high to be reduced.
- (1)
To reduce the cost of equipping the intrusion detection system, this paper uses the K-Nearest Neighbors (KNN) algorithm to classify edge devices and equips the intrusion detection system for cluster heads to achieve the purpose of protecting Smart Home system.
- (2)
To defend against attackers, we build interactions between attackers and intrusion detection systems as a repeated game model, use the regret minimization algorithm to determine the mixed strategy Nash equilibrium of this game, and set the severe punishment mechanism to force the attacker to take good action.
- (3)
For the part of the simulation experiment, we compare the proposed scheme with Winner, ALL-S, ALL-P, and ALL-R with three factors: the intrusion detection rate, the attacker’s payoff, and the intrusion detection system’s payoff. The experimental results show that the proposed scheme can resist attackers.
The remainder of this paper is organized as follows: Section 2 describes the representative achievements of intrusion detection technology. We propose an intrusion detection scheme based on repeated game in Smart Home in Section 3. Section 4 shows the performance of intrusion detection scheme based on repeated game. Finally, Section 5 summarizes the possible expansion and research directions in the future.
2. Related Work
Intrusion detection technology [7] can be divided into three types: anomaly detection, misuse detection, and hybrid intrusion detection. This section mainly summarizes two kinds of techniques of anomaly detection and misuse detection.
The anomaly intrusion detection [8] takes the intrusion activity as a subset of the anomaly activity, which is divided into feature selection-based anomaly detection, Bayesian inference-based anomaly detection, and pattern prediction-based anomaly detection. The feature selection-based anomaly detection is to accurately predict or classify detected intrusions by selecting a subset of metrics that can detect intrusions [9, 10]. However, the metric set cannot encompass all the various intrusion types; and the preidentified specific metric set may miss intrusions in a particular environment alone. The Bayesian inference-based anomaly detection is to judge whether the system has an intrusion event by measuring the variable [11, 12]. However, this method requires correlation analysis of each variable for determining the relationship between each variable and the intrusion event. The pattern prediction-based anomaly detection considers the sequence of intrusion events and their correlation [13, 14], but the unrecognized behavior pattern is judged as an abnormal event in this method.
Misuse intrusion detection [15, 16] detects intrusion events by matching the defined intrusion pattern with the observed intrusion behavior, which can be divided into contingent probability-based misuse intrusion detection, state transition analysis-based misuse intrusion detection, and keyboard monitoring-based misuse intrusion detection. The contingent probability-based misuse intrusion detection maps the intrusion to an event sequence and then infers the intrusion occurrence by observing the event [17, 18]. However, in this method, the prior probability is hard to give, and the event independences are hard to be satisfied. The state transition analysis-based misuse intrusion detection regards an attack as a series of state transitions of monitored systems [19, 20]. However, the attack mode can only describe the sequence of events and is not suitable for describing complicated events. The keyboard monitoring-based misuse intrusion detection assumes that the intrusion corresponds to a specific keystroke sequence pattern and then monitors the user keystroke pattern and matches this pattern with the intrusion pattern to detect intrusion [21, 22]. But this approach, without operating system support, lacks a reliable way to capture users’ keystrokes, and users can easily cheat the technique by using alias commands.
To solve the above problems, we no longer detect the intrusion based on the characteristics of the attacker but consider intrusion detection system’s payoff; that is, the intrusion detection system detects the attacker invasion by observing its payoff decrease.
3. Intrusion Detection Scheme Based on Repeated Game
This section describes how the intrusion detection system detects the attacker’s malicious action and how to educate the malicious attackers to take good strategy. The notations definitions are shown in Table 1.
| Notations | Definition |
|---|---|
| Ci | The ith cluster head |
| S | Attackers and intrusion detection systems’ strategy space |
| ci | The cost of attacking cluster heads Ci |
| The cost of attacking cluster heads Ci after T times | |
| ri | The cost of persistently protecting cluster heads Ci |
| The cost of protecting cluster heads Ci after T times | |
| The payoff of attacking cluster heads Ci | |
| The payoff of intrusion detection systems against attacks | |
| M | The strategy matrices of attacker and intrusion detection system |
| X | Attackers’ payoff matrix |
| Y | Intrusion detection systems’ payoff matrix |
| Ue | The cumulative payoff of player e |
| δ | The discount factor which measures how much players value future payoffs |
3.1. One-Order Game
3.2. Repeated Game
During the process of interaction between the attacker and intrusion detection system, the intrusion detection system can detect attackers’ invasion by observing the changes of their payoff. However, the attacker does not have the effect of his current strategy on the future payoff, that is, he only considers the payoff of one interaction; therefore, it is difficult to prevent the attacker in the one-order game. But if the intrusion detection system punishes the attacker, the attacker will have to consider the cost of the penalty brought by the intrusion detection system in the repeated game; and if the punishment cost of attacking exceeds the payoff of attacking, the attacker will be forced to take a nonattack strategy. Thus, the intrusion detection system does not need to implement supervision and then achieve the purpose of maintaining the normal order of the entire network.
By comparing the attacker’s payoffs over the two penalty cycles, it can be seen that the attacker’s payoffs decrease with increasing the number of betrayals. Besides, if the number of defections by an attacker exceeds the threshold of the intrusion detection system, the attacker will be eliminated; and the cluster-head node will no longer interact with the attacker.
4. Simulation Experiment
This paper uses Anaconda integrated development tool to verify the intrusion detection scheme based on repeated game. Firstly, we simulate the classification process of KNN algorithm and set four newly added nodes to prove its effectiveness. Secondly, we compare the payoffs of attackers and the intrusion detection systems in penalty cycles and regular interaction cycles to verify the effectiveness of the penalty mechanism. Thirdly, we determine the optimal strategy for each round of interaction between the attacker and intrusion detection system by using the regret minimization algorithm. Finally, we compare the proposed scheme with four interaction strategies, Winner (take the strategy of the winner), ALL-S (remain strategy Scissor), ALL-P (remain strategy Paper), and ALL-R (remain strategy Rock), to prove that the proposed scheme can improve the player’s payoff. The experimental parameters are shown in Table 2.
| Parameters | pe | ci | δ | η | T | q | |
|---|---|---|---|---|---|---|---|
| Value | 5 | 3 | 3 | 0.7 | 1 | 5 | 0.6 |
4.1. The Classification Results of KNN
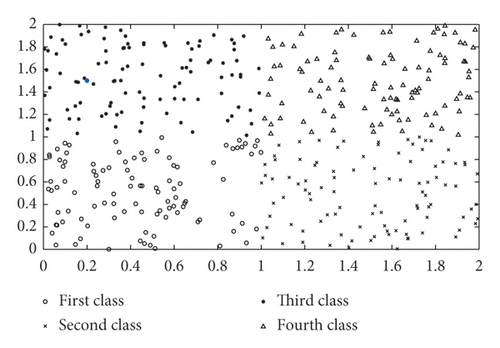
Figure 1 depicts the classification results of the KNN algorithm. Figure 1(a) shows the original distribution of edge device nodes. Figure 1(b) shows the classification results of the KNN algorithm, with each symbol representing a class of edge devices.
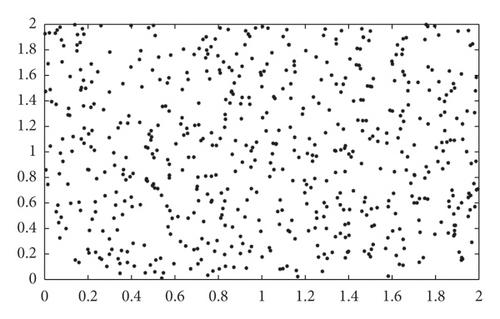
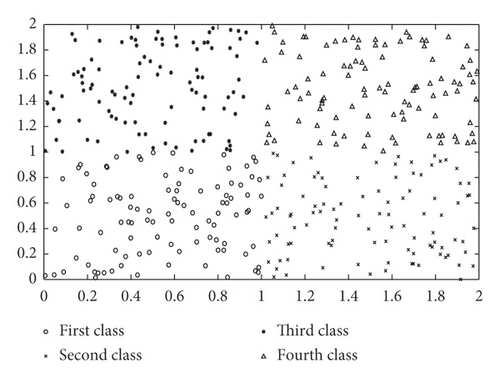
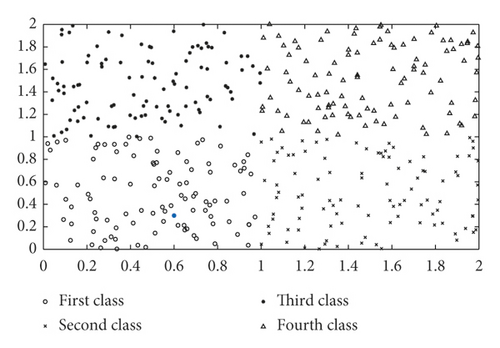
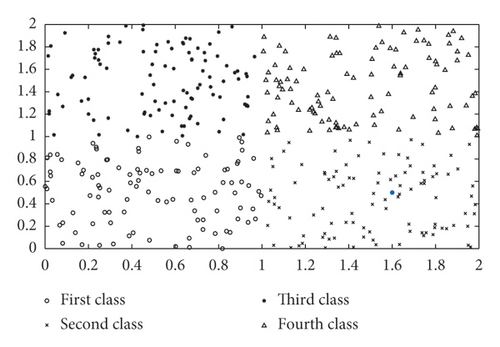
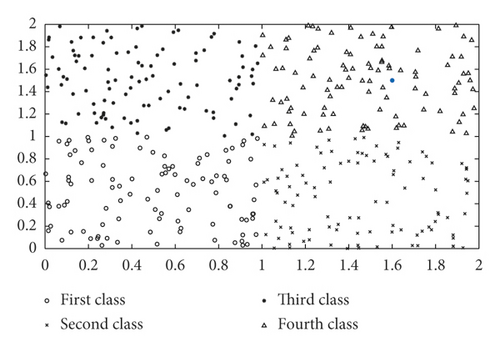
Figure 2 analyzes the results of the classification of the newly added nodes, with the newly added nodes marked in blue. For example, in Figure 2(a), the blue node (the newly added node) is classified as a first class.
4.2. The Comparison of the Attacker’s Payoff and Intrusion Detection System’s Payoff
Figure 3 compares the attackers’ payoffs in regular interaction cycles and penalty cycles. As you can see in Figure 3(a), the attacker’s payoff does not change during regular interaction cycles, because the intrusion detection system does not play the defensive strategy. Figure 3(b) shows that the attacker’s payoff gradually decreased with increasing the number of interactions. In the 4th interaction, the attacker’s payoff tends to zero. Besides, the longer the penalty cycle is, the faster the attacker’s payoffs will go to zero, and the larger the losses will be. This happened due to the punishment mechanism in this paper. Therefore, for a rational attacker, it must normally interact with the intrusion detection system to maximize its payoff.

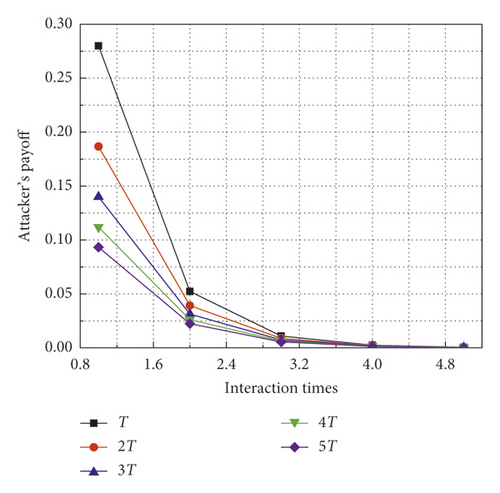
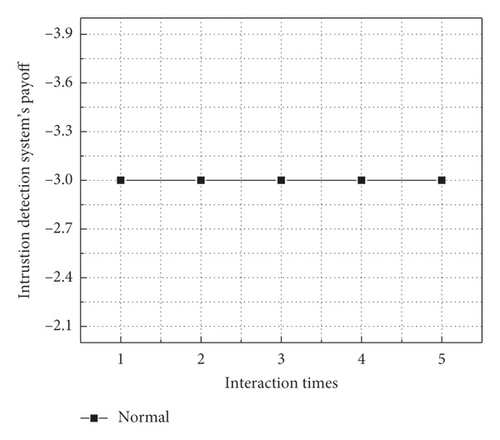
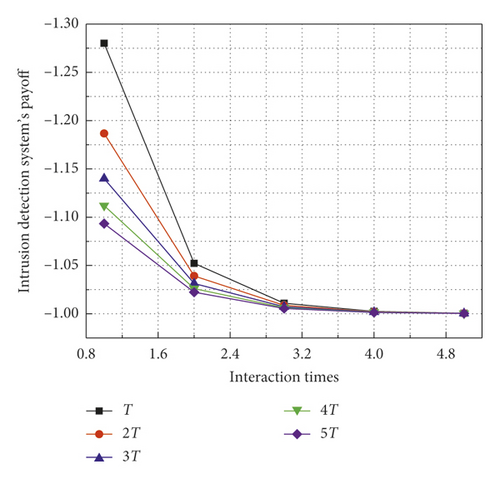
Figure 4 compares the intrusion detection system’s payoffs in the regular interaction cycle and the penalty cycle. It can be seen from Figure 4(a) that the intrusion detection system’s payoff is −3 during the regular interaction cycle. This is because the attacked intrusion detection system does not play any defective strategy. Figure 4(b) shows that the loss of the intrusion detection system decreases with increasing the number of penalty cycles; and the payoff of the intrusion detection system is the lowest when the penalty period is 5. To sum up, the proposed scheme can reduce the loss of intrusion detection systems when attackers launch attacks.
4.3. Application of Regret Minimization Algorithm in Rock-Paper-Scissors Game
Table 3 defines the payoff matrix of two players in the rock-paper-scissors game. In this table, the rows represent the strategy of player A, the columns represent the strategy of player B, the first element in the tuple (0, 0) represents the payoff of player A, and the second element represents the payoff of player B.
| Player A\B | Scissor | Rock | Paper |
|---|---|---|---|
| Scissor | 0, 0 | −1, 1 | 1, −1 |
| Rock | 1, −1 | 0, 0 | −1, 1 |
| Paper | −1, 1 | 1, −1 | 0, 0 |
Table 4 analyzes how player A determines its optimal strategy based on the regret minimization algorithm. For example, in the first round, player A and player B choose Rock and Paper, respectively, and then player A’s regret values when playing Scissor, Rock, and Paper are 0, 2, and 1, respectively; thus the probabilities of player playing Rock, Scissor, and Paper are 0, 2/3, and 1/3, respectively. Similarly, we can obtain the optimal strategy of player A in each round.
| Iteration number | Player A | Optimal strategy | ||
|---|---|---|---|---|
| Rock | Scissor | Paper | ||
| 1 | 0 | 2 | 1 | (0, 2/3, 1/3) |
| 2 | 1 | 0 | 2 | (1/6, 2/6, 3/6) |
| 3 | 2 | 1 | 0 | (1/3, 1/3, 1/3) |
| 4 | 0 | 2 | 1 | (3/12, 5/12, 4/12) |
| 5 | 1 | 0 | 2 | (4/15, 5/15, 6/15) |
| 6 | 2 | 1 | 0 | (1/3, 1/3, 1/3) |
| 7 | 0 | 2 | 1 | (6/21, 8/21, 7/21) |
| 8 | 1 | 0 | 2 | (7/24, 8/24, 9/24) |
| 9 | 2 | 1 | 0 | (1/3, 1/3, 1/3) |
| 10 | 0 | 2 | 1 | (9/30, 11/30, 10/30) |
| Cumulative regret | 9 | 11 | 10 | — |
4.4. The Payoff Comparison between Player A and Player B
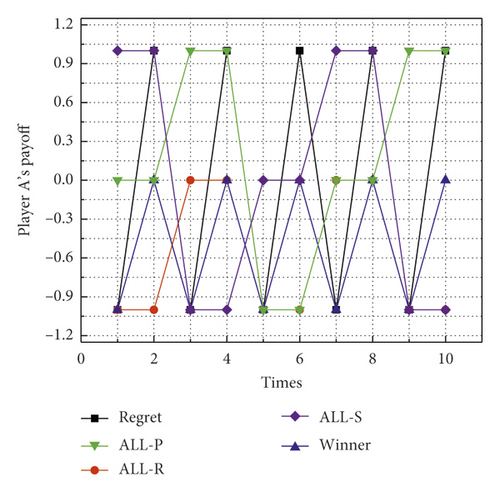
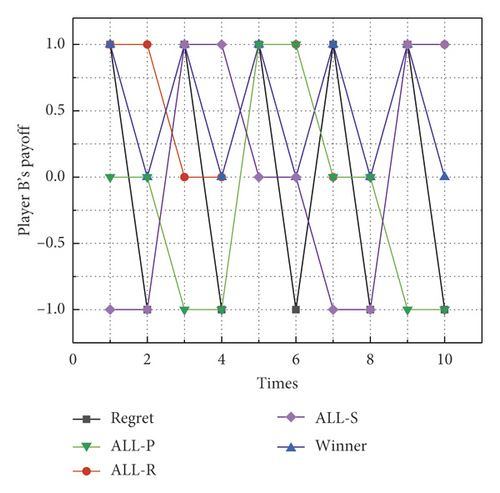
Table 5 compares the payoffs of player A and player B when player A adopts five strategies: regret minimization strategy (Regret), ALL-R, ALL-P, ALL-S, and Winner, while player B adopts a regret minimization strategy. As can be seen from Table 5, when and only if player A adopts ALL-P, player B adopts Regret to obtain a lower payoff than player A, but the difference in payoff between player A and player B is small. However, under several other strategies, player B obtains the highest payoff by taking Regret. This is because player B maximizes the probability of the strategy with the maximum regret value. The payoff change curves of players A and B are shown in Figure 5. In this figure, the sharp increase and decrease in the payoffs of player A and player B are due to the adjustment of both players’ strategies.
| Number | Payoff | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| A | B | A | B | A | B | A | B | A | B | |
| 1 | −1 | 1 | −1 | 1 | −1 | 1 | 0 | 0 | 1 | −1 |
| 2 | 1 | −1 | −1 | 1 | 0 | 0 | 0 | 0 | 1 | −1 |
| 3 | −1 | 1 | 0 | 0 | −1 | 1 | 1 | −1 | −1 | 1 |
| 4 | 1 | −1 | 0 | 0 | 0 | 0 | 1 | −1 | −1 | 1 |
| 5 | −1 | 1 | −1 | 1 | −1 | 1 | −1 | 1 | 0 | 0 |
| 6 | 1 | −1 | −1 | 1 | 0 | 0 | −1 | 1 | 0 | 0 |
| 7 | −1 | 1 | 0 | 0 | −1 | 1 | 0 | 0 | 1 | −1 |
| 8 | 1 | −1 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | −1 |
| 9 | −1 | 1 | −1 | 1 | −1 | 1 | 1 | −1 | −1 | 1 |
| 10 | 1 | −1 | −1 | 1 | 0 | 0 | 1 | −1 | −1 | 1 |
| Total | 0 | 0 | −6 | 6 | −5 | 5 | 2 | −2 | 0 | 0 |
5. Conclusion
Designing an efficient and safe protection scheme is the key to promoting the application of the system. This paper proposes a security protection scheme based on repeated game. In this scheme, the intrusion detection system detects the malicious attackers by observing its payoff change and punishes the attackers who adopt malicious strategy severely to educate the attackers to take good action. The experimental results show that the proposed scheme can effectively defend against the attackers.
In future research studies, we will continue to explore new methods to determine the player’s optimal strategy in the finite model.
Conflicts of Interest
The authors declare that they have no conflicts of interest.
Acknowledgments
This research was supported by the National Natural Science Foundation of China (NSFC) under Grant no. 61872205, the Shandong Provincial Natural Science Foundation under Grant no. ZR2019MF018, and the Source Innovation Program of Qingdao under Grant no. 18-2-2-56-jch.
Open Research
Data Availability
The data used to support the findings of this study are included within the article.




