Multiobjective Cognitive Cooperative Jamming Decision-Making Method Based on Tabu Search-Artificial Bee Colony Algorithm
Abstract
For the future information confrontation, a single jamming mode is not effective due to the complex electromagnetic environment. Selecting the appropriate jamming decision to coordinately allocate the jamming resources is the development direction of the electronic countermeasures. Most of the existing studies about jamming decision only pay attention to the jamming benefits, while ignoring the jamming cost. In addition, the conventional artificial bee colony algorithm takes too many iterations, and the improved ant colony (IAC) algorithm is easy to fall into the local optimal solution. Against the issue, this paper introduces the concept of jamming cost in the cognitive collaborative jamming decision model and refines it as a multiobjective one. Furthermore, this paper proposes a tabu search-artificial bee colony (TSABC) algorithm to cognitive cooperative-jamming decision. It introduces the tabu list into the artificial bee colony (ABC) algorithm and stores the solution that has not been updated after a certain number of searches into the tabu list to avoid meeting them when generating a new solution, so that this algorithm reduces the unnecessary iterative process, and it is not easy to fall into a local optimum. Simulation results show that the search ability and probability of finding the optimal solution of the new algorithm are better than the other two. It has better robustness, which is better in the “one-to-many” jamming mode.
1. Introduction
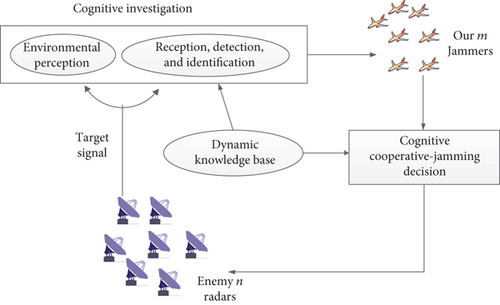
With the advent of net-defender technology, information confrontation has played a more and more important role in the modern war, and multiattackers in various patterns have been the main way as electronic attack. The conventional jamming resource allocation algorithms based on point-to-point allocation are not suitable for modern war due to its low efficiency. Cognitive cooperative jamming will become a trend in the information confrontation due to the ability of cognitive technology for autonomous environment perception and real-time optimization of operating parameters [1, 2]. Cognitive confrontation is a closed-loop learning processing system based on the dynamic knowledge base of perception-recognition decision-making action-perception, and it is used to improve the combat effectiveness of electronic equipment under a complex electromagnetic environment [3]. Decision-making plays a vital role in this closed-loop system, directly affecting combat effectiveness and benefits [4–6].
One major goal of decision-making is to improve the jamming benefit, which is mainly measured by power, frequency, jamming space, and jamming patterns in the existing research [7–11]. These studies, however, which cannot reflect the real battlefield situation, only considered how to maximize the jamming benefit from the attacker and ignore the jamming cost. Literature [12] takes the jamming cost in to account, but it is rather vague. In order to be closer to the actual application scenario, this paper takes the jamming benefit and jamming cost into account together and selects the detection probability as the attacker cost to measure the attacker effect with power, frequency, jamming space, and jamming patterns.
Decision-making is a nonlinear integer combinatorial optimization problem [13, 14]. At present, intelligent algorithms such as genetic algorithms (GA), improved ant colony (IAC) algorithms, and particle swarm optimization (PSO) are widely used to solve this problem. Literature [15] used a genetic algorithm to solve multi-UAV (unmanned aerial vehicle) mission planning problems. Literature [16] proposed a quantum genetic algorithm that uses a qubit to encode communication parameters. It used quantum rotation gates to update the population and assign nonlinear characteristics to the algorithm. However, this algorithm is high in complexity and slow in convergence. Literature [17] introduced the ant colony algorithm to the intelligent decision problem and improved the speed of convergence. Literature [18] proposed an IAC algorithm to optimize the allocation of multitarget defender jamming resources and accelerate the speed of searching optimization. Literature [19] uses particle swarm optimization for decision-making. However, most intelligent algorithms need many complicate parameters, and there still is some room for improvement to convergence speed. To this issue, literature [20] applied the artificial bee colony algorithm to make antijamming communication decisions, which reduces the number of parameters and intensified convergence. However, the conventional ABC algorithm is easy to fall into the local maximum with poor robustness. This paper combines the ABC algorithm with the tabu search algorithm and proposes a new rule for searching new solutions. The optimization probability of the algorithm is improved while ensuring fewer parameters and fast convergence.
2. The Model of Multiobjective Cognitive Collaborative Jamming Decision
Suppose there are m attackers to jam n defenders, shown in Figure 1. The matrix X used to represent the jamming decision scheme can be achieved by the artificial intelligence algorithm, where xij = 1 means the attacker is assigned to jam the defender; otherwise, xij = 0. Different from the previous research, we propose the concept of jamming cost and convert the traditional model into the multiobjective collaborative jamming decision-making model.
2.1. Jamming Benefit and Jamming Cost
In this paper, the jamming benefit is measured by four elements (power suppression benefit, frequency alignment benefit, jamming coverage space benefit, and jamming pattern benefit), which can be represented by vector Q = [q1ij, q2ij, q3ij, q4ij].
All of the above indicators are for maximizing the m jamming benefits and ignoring the jamming cost. According to the jamming effect factors mentioned above, this paper will form a multiobjective cognitive collaborative jamming decision model. Thus, the purpose is to maximize the jamming benefits while minimizing the probability that the attacker is discovered.
2.2. Objective Functions and Constraints
We obtain different decision-making schemes corresponding to different decision matrixes X through simulation. Finally, the decision matrix X that maximizes the objective function is selected as the final decision-making scheme.
3. Tabu Search-Bee Colony Algorithm
- (1)
Initialize bee populations. There are three population parameters:
- (a)
The total number of bees: N (bees produce nectar as jamming decision matrix)
- (b)
Maximum iterations: maxCycle
- (c)
The single largest number of searching for each food source: limit
- (a)
-
Because all bees are scouts with no prior information, the algorithm randomly generates N jamming decision matrix X overall situation corresponding to N food sources. The jamming effect of every decision scheme is its profitability ffit.
-
At this time, all bees are scouts with no prior information. The algorithm randomly generates N jamming decision matrix X overall situation corresponding to N food sources. The jamming effect of every decision scheme is its profitability ffit.
(13) - (2)
Divide all bees into employed foragers and onlookers according to the jamming effect of every decision matrix X in step (1). Among them, the N/2 bees with a higher ffit value are employed foragers, and the other N/2 bees are onlookers. Onlookers select employed foragers to follow according to the probability P of the ffit value of the former N/2 decision matrix.
- (3)
Every employed forager searches for a new decision matrix around the old one and calculates its profitability. If it is greater than the old, then replace it according to the greedy criterion. The search formula is in
(15)where(16)rand 1, and rand 2 are unequal random integers between [1, n]. - (4)
Onlookers change the distribution mode of the attacker corresponding to employed foragers to get a new decision matrix after selecting them to follow, similar as in step (3).
- (5)
If employed foragers and onlookers search more than limited times for a decision matrix and find no decision scheme with better profitability, then give up this decision matrix, turn the role of the bee into scouts, and generate a new decision matrix that satisfies the constraints.
- (6)
Record the decision matrix of the maximum jamming effect and turn to step (2), until the maximum iteration number maxCycle is satisfied. The decision matrix which makes the profitability maximal is the decision scheme with the best jamming effect.
The jamming decision based on the ABC algorithm can not only ensure the optimization speed of the algorithm but also solve the problem that the IAC algorithm requires a large number of early parameters depending on manual selection. It is an effective improvement of the IAC algorithm.
However, there are some major problems faced by the ABC algorithm. When the optimization domain is large or in a flat area, the new solution sometimes overlaps with the already searched solution and further results in unnecessary repeated searches. As a result, the global search ability of the algorithm is reduced, and it is sometimes easy to fall into the local maximum. Due to the limitation of the taboo table in the tabu search algorithm, the probability of falling into the local optimal solution can be greatly reduced [22–24]. In order to avoid the algorithm falling into the local optimum and increase the probability of getting the optimal solution, we introduce the tabu search algorithm to the jamming decision-making field and introduce the new tabu search-artificial bee colony (TSABC) algorithm to the problem of jamming decision-making.
It is the first time that the TSABC algorithm is introduced to the problem of jamming decision-making. The elements in the taboo table are the decision matrices corresponding to different decision schemes, and the Euclidean distance cannot be calculated. Due to this, the conventional method of using the Euclidean distance between elements to represent the threshold has lost its significance in jamming decisions. We propose a new method for calculating the threshold value and a novel strategy to generate a new solution. The specific improvements are as follows.
If the difference of the fitness between the new solution and the solution in the taboo list is smaller than the threshold, we think that this new solution is in the range of the taboo list, and the new solution will be repeatedly generated until it is out of the taboo list.
The application of tabu search in the ABC algorithm in the jamming decision is shown in Algorithm 1.
-
Algorithm 1: The application of tabu search in ABC algorithm in jamming decision.
-
1: send employed foragers
-
2: calculate the jamming effect of the current decision matrices
-
3: if optimal solution updated after limit times
-
then
-
4: keep the updated solution
-
5: else
-
6: update tabu list
-
7: search for new solution through the Tabu Search Algorithm
-
8: while distance ≤ thresholdvalue do
-
9: keep the solution as the new solution
-
10: end while
-
11: end if
-
12: send onlookers
-
13: repeat
4. Simulation Analysis
To verify the robustness and the ability of the improved tabu search-artificial bee colony algorithm for multiobjective collaborative jamming decision-making, we set two different jamming modes named “one-to-one” and “one-to-many” for simulation verification using the above objective function.
“One-to-one” jamming mode: suppose that the number of attackers is m = 10, and the number of defenders is n = 10. Each attacker can jam one defender. Calculate the weighted sum of the jamming benefit and jamming cost of attacker ui(i = 1, 2, …, m) to defender Rj(j = 1, 2, …, n); the jamming effect matrixes are then shown in (18) and (19).
We design two sets of experiments to verify the optimization speed and optimization probability of the tabu search artificial bee colony algorithm. In the two experiments, NP = 40, limit = 100, and maxCycle = 100.
Experiment 1: the IAC algorithm, ABC algorithm, and TSABC algorithm are used to simulate the jamming decision in the “one-to-one” and “one-to-many” modes, which verifies that the optimization ability of the TSABC algorithm is better than that of the IAC algorithm and ABC algorithm. Then, the comparison of the simulation results of the three algorithms is exhibited in Figures 2 and 3.
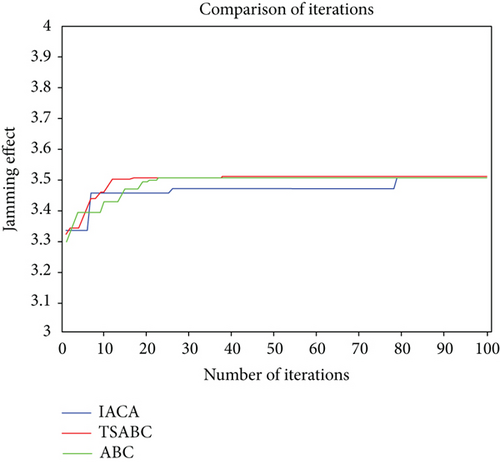
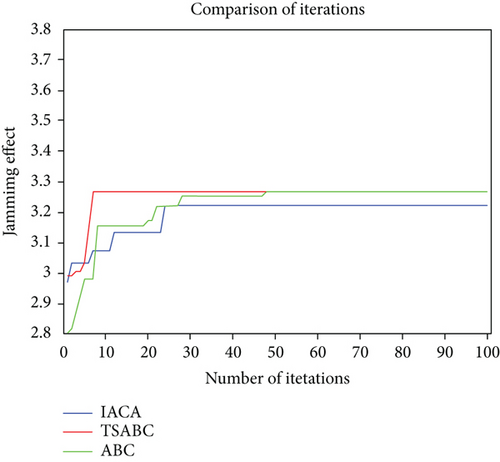
It can be seen from Figures 2 and 3 that the IAC algorithm requires more iterations in the “one-to-one” mode. Although it is reduced in the “one-to-many” mode, the search ability is reduced too. The TSABC algorithm need not repeat the search process in the ABC algorithm because of the tabu list, which helps reach the optimal value with fewer iterations. The above results show that the optimization ability of the TSABC algorithm is better.
Next, we can obtain the respective optimal decision matrixes X in two modes through the simulation. The corresponding jamming decision schemes are shown in Tables 1 and 2.
| Rader number | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 |
|---|---|---|---|---|---|---|---|---|---|---|
| Attacker number | 4 | 9 | 1 | 2 | 7 | 6 | 3 | 10 | 8 | 5 |
| Defender number | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|
| Attacker number | 1 | 4 | 3 | 5 | 2 | 1 | 4 | 2 |
Tables 1 and 2 show the jamming matching schemes. It can be seen from the tables that each defender has a corresponding attacker to jam. The number of defenders jammed per attacker is 1 in the one-to-one mode and does not exceed 2 in the “one-to-many” mode, which meets the constraint set.
In order to avoid the fortuity of a single optimization, we introduce Monte Carlo simulation to perform the decision-making process under the two modes 100 times, respectively, and record the average number of iterations after each operation. The optimization ability of three algorithms in two modes is shown in Figures 4 and 5.
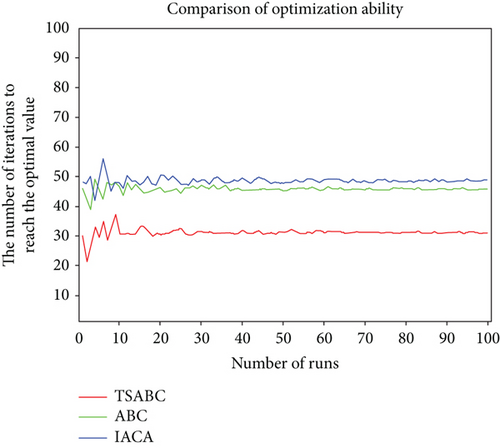
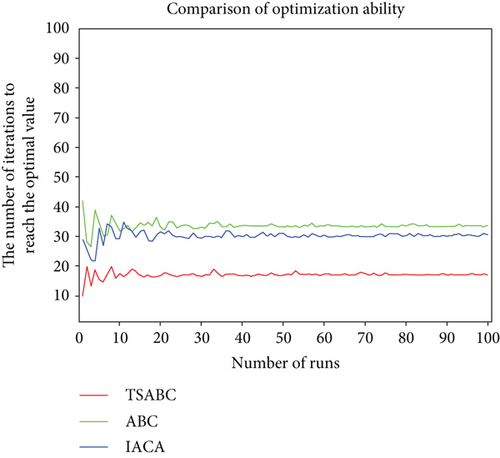
It is obviously seen in Figures 4 and 5 that the number of iterations fluctuates around a fixed value. The number of iterations of the TSABC algorithm is less than the other two, which further indicates that the TSABC algorithm has a stronger optimization ability.
Experiment 2: Monte Carlo simulation is ulteriorly used to perform the decision-making process in the two modes 100 times, respectively, and record the average optimized value and the optimization probability of each algorithm after each decision. The average optimized values in two modes are shown in Figures 6 and 7.
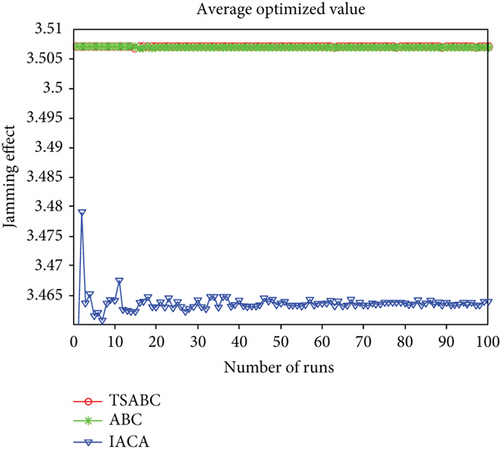
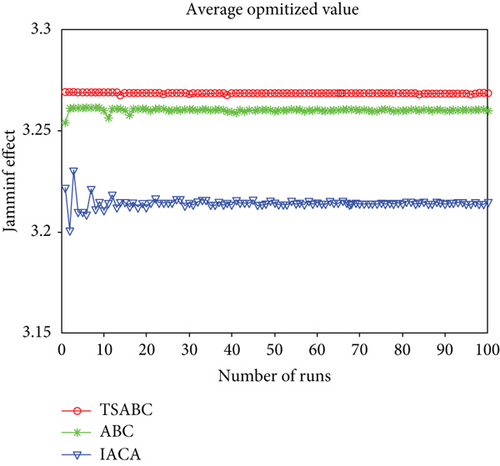
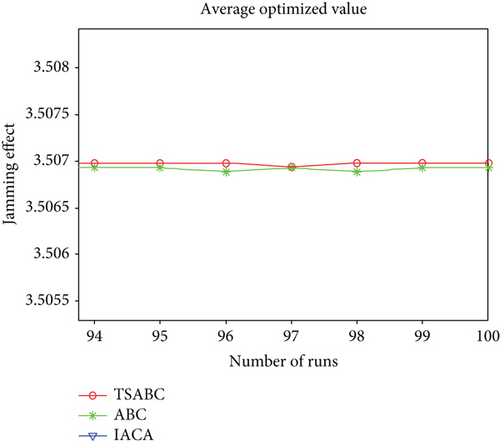
The difference of the average optimized value in the one-to-one mode is small between the TSABC algorithm and ABC algorithm, and partial enlargement is shown in Figure 8.
It can be seen from Figures 5 and 6 that the optimization probability of the TSABC algorithm is better than that of the IACA algorithm and ABC algorithm. This phenomenon indicates that compared with the other two algorithms, the TSABC algorithm can jump out of the local optimum more effectively to find the optimal solution and improve the search probability. Thus, the robustness of the proposed algorithm is verified.
To further demonstrate the superiority of the proposed algorithm, the performance comparison of the three algorithms is shown in Table 3.
| One-to-one | One-to-many | |||||
|---|---|---|---|---|---|---|
| IACA | ABC | TSABC | IACA | ABC | TSABC | |
| Average optimized value | 3.46498 | 3.50676 | 3.50688 | 3.22874 | 3.26611 | 3.26794 |
| The average number of iterations to obtain the optimal value | 50 | 48 | 31 | 31 | 34 | 19 |
| Optimization probability | 0.72 | 0.94 | 0.97 | 0.65 | 0.84 | 0.95 |
In Table 3, we take the weighted sum of the jamming benefit and jamming cost as the objective function of the multiobjective cognitive cooperative jamming decision, which ensures that the simulation solution can pay a very small jamming cost while obtaining great jamming benefits. It can be seen from Table 3 that the average number of iterations of the TSABC algorithm is less than the other two algorithms. Most importantly, the probability of the TSABC algorithm getting the optimal solution is far greater than the other two, which means its optimization probability is greater. Apparently, the optimization ability and the optimization probability of the proposed algorithm are both enhanced. In addition, the TSABC algorithm has better robustness. The advantages are more obvious in one to many modes.
5. Conclusion
In the modern war, information confrontation plays an increasingly important role where cognitive cooperative jamming will become a trend due to the ability of cognitive technology for autonomous environment perception and real-time optimization of operating parameters. Jamming decision-making plays a vital role in the closed loop of cognitive confrontation. Aiming at the problem of maximizing the jamming benefit as the decision target in the existing jamming decision model, in this paper, two objective functions as jamming benefit and jamming cost are proposed to measure the jamming effects, and the calculation methods of specific indicators and their revenue values are given, respectively. The increase in the objective function transformed the collaborative jamming decision-making problem into a multiobjective optimization problem and refined the model of multiobjective cognitive collaborative jamming decision. In the aspect of the decision algorithm, aiming at the deficiency of the improved ant colony algorithm in the jamming decision-making problem, this paper introduces the tabu search artificial bee colony algorithm to the jamming decision-making problem, and the superiority of the algorithm is proved by simulation. The simulation results show that the improved TSABC algorithm is greater than comparison methods both in the optimization ability and the optimization probability and has better robustness and higher application value in cognitive confrontation.
Conflicts of Interest
The authors declare that there is no conflict of interest regarding the publication of this paper.
Acknowledgments
This paper is funded by the National Natural Science Foundation of China (Grant No. 61701134), the National Key Research and Development Program of China (Grant No. 2016YFF0102806), the Natural Science Foundation of Heilongjiang Province, China (Grant No. F2017004), and the Fundamental Research Funds for the Central Universities of China (No. HEUCFM180802).
Open Research
Data Availability
The research data and software code used to support the findings of this study are available from the corresponding author upon request.




