Chaotic Image Encryption Algorithm Based on Circulant Operation
Abstract
A novel chaotic image encryption scheme based on the time-delay Lorenz system is presented in this paper with the description of Circulant matrix. Making use of the chaotic sequence generated by the time-delay Lorenz system, the pixel permutation is carried out in diagonal and antidiagonal directions according to the first and second components. Then, a pseudorandom chaotic sequence is generated again from time-delay Lorenz system using all components. Modular operation is further employed for diffusion by blocks, in which the control parameter is generated depending on the plain-image. Numerical experiments show that the proposed scheme possesses the properties of a large key space to resist brute-force attack, sensitive dependence on secret keys, uniform distribution of gray values in the cipher-image, and zero correlation between two adjacent cipher-image pixels. Therefore, it can be adopted as an effective and fast image encryption algorithm.
1. Introduction
With the rapid development of the computer network, it becomes more and more convenient to communicate in digital form. However, the transmitted information may be intercepted, copied, and even modified illegally. Aiming at the security and protection of digital images, many image encryption algorithms or technologies such as DNA sequence [1], chaotic map [2], circular bit shift and XOR operations [3], quantum logistic map [4], and Hartley transform [5] have been developed. Among these encryption algorithms, the chaos-based approach has become a hot research topic because of many unique characteristics of the chaotic system itself such as sensitive dependence on initial conditions and system parameters, nonperiodicity, pseudorandom property, and topological transitivity. These properties lead to efficient methods for image encryption.
One-dimensional and two-dimensional chaotic maps are usually employed in chaos-based image encryption algorithms. One-dimensional chaotic maps such as Logistic map, Sine map, and skew tent map have the advantages of simplicity and easy implementation [6]. In particular, Logistic map was widely used for image encryption [7–9]. However, it is not secure enough to use only one-dimensional chaotic map because of its small key space and weak security [7]. Many studies [10–13] were carried out to improve its security. For example, Singh and Sinha combined the Hartley transform and Logistic map in [5], Gao et al. [6] increased the number of parameters to six, and Ye [10] adopted the matrix property of Toeplitz and Hankel. Reference [11] proposed a total shuffling algorithm using Logistic map. In [12], two Logistic maps were employed to enlarge the key space. In other schemes [14, 15], the security has been improved by shuffling the positions and changing the pixel values simultaneously. Li and Yuan [15] reported the weakness of DCT-based encryption algorithm and proposed the full interblock shuffle approach. The authors in [16] studied the hyperchaotic systems with uncertain parameter for image encryption.
A good encryption algorithm must satisfy some requirements such as large key space, sensitive dependence on secret keys, and no correlation between two adjacent pixels [17, 18]. Here we propose an image encryption algorithm based on the time-delay Lorenz system and the unique properties of chaotic systems. It performs the position permutation according to a chaotic sequence and the diffusion stage by blocks. The rest of this paper is arranged as follows. In Section 2, Circulant matrix and time-delay Lorenz system are introduced. The proposed image encryption algorithm and its mathematical model are described in Section 3. Numerical experiments are reported in Section 4 while the related security analysis is given in Section 5. Finally, some conclusions are drawn in Section 6.
2. Circulant Matrix and Time-Delay Lorenz System
2.1. Circulant Matrix
Definition 1. Suppose that there is an n × n matrix Cn having the following form:
Definition 2. Suppose that there is an m × n matrix Gm×n (m ≤ n) possessing the following form:
We can also consider Gm×n as a generalized Circulant matrix when m > n, considering that GT has the same form as (2).
2.2. The Time-Delay Lorenz System
2.3. Random Chaotic Sequence
Given initial values x0, y0, and z0, a set of values {x0, y0, z0, x1, y1, z1, …} can be obtained by iterating (3). A parameter p can be added to drop the former p iterated values; that is, we only keep the values {xp+1, yp+1, zp+1, xp+2, yp+2, zp+2, …}. Collect the first component {xp+1, xp+2, …, xp+M} since the plain-image size is M × N. Do the preprocessing for {xp+1, xp+2, …, xp+M} by updating the values as xp+i = abs(xp+i × 1014) − floor(abs(xp+i × 1014)), i = 1,2, ⋯, M.
Sort the updated sequence and we obtain . By finding the position of in {xp+1, xp+2, …, xp+M}, a sequence H = {h1, h2, …, hM} can be generated. Similarly, do the same process for the second component {yp+1, yp+2, …, yp+N}, and we can get another sequence L = {l1, l2, …, lN}.
3. Image Encryption Scheme
In general, the adjacent pixels in the plain-image have high correlation. In order to reduce this correlation and resist known-plaintext attacks, position permutation is considered as the first encryption operation.
3.1. Position Permutation Based on Circulant Matrix
Based on the Circulant matrix, we can perform position permutation along the diagonal or antidiagonal lines in the upper and lower triangular matrices. This approach is different from the traditional method of row and column position shuffling. Of course, it will have problems if we apply the chaotic sequences to the diagonal and antidiagonal lines directly because the number of elements on these lines is not equal. This is the main reason why the existing approaches do not perform position shuffling along the diagonal and antidiagonal instead of row and column. Here we can solve this problem using the properties of the Circulant matrix.
In the decryption process, we just need to rewrite (5), (6), (8), and (9) reversely. In fact, the traditional permutation is a special case of our method. Of course, the method can be extended to image shuffling of any size according to the generalized Circulant matrix (here we do not discuss this in detail; please refer to the Appendix). After being permutated along the diagonal and antidiagonal directions, the process of position permutation is finished. For example, Figure 1(b) is the cipher-image of Rice shown in Figure 1(a) using three rounds of our method. Figure 1(c) is the cipher-image using traditional row and column method, also by three rounds. The figures show that the proposed method has a better shuffling performance.

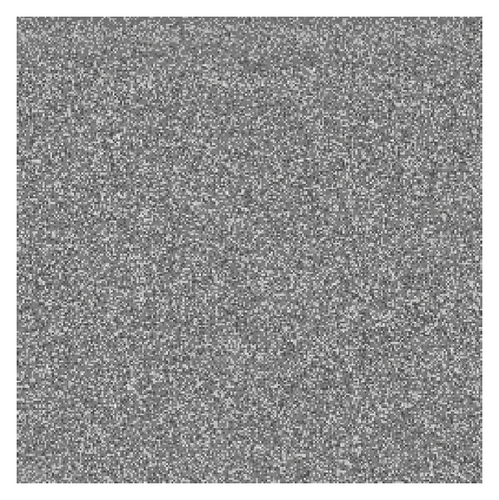
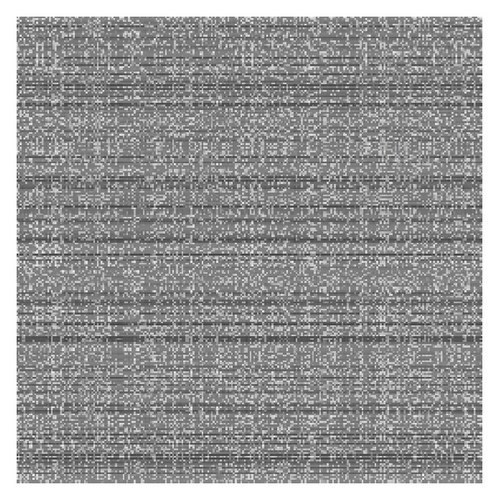
3.2. Block-Based Diffusion
To make a bit-change in the plain-image result in a big difference in the cipher-image, we adopt block-based diffusion for a fast implementation. The diffusion steps are stated as follows:
Step 1. Read the permuted image to a M × N matrix E. Then divide E into two equal blocks, that is, E = [E1; E2]. Each block has size (M/2) × N. We can add a random row to E if M is not an even number.
3.3. Encryption Procedures
The detail procedures of the proposed image encryption algorithm based on time-delay Lorenz system and Circulant matrix are described as follows.
Step 1. Read the plain-image and put its pixels in a two-dimensional matrix A.
Step 2. Generate two chaotic sequences H and L by iterating the time-delay Lorenz system from the initial condition x0, y0, z0, p.
Step 3. Perform position permutation on A using H and L according to the property of the Circulant matrix. A new permuted matrix E is then formed.
Step 4. Generate the pseudorandom matrix W of size (M/2) × N from the chaotic system again.
Step 5. Divide the matrix E into two parts, that is, E = [E1; E2], and compute the control parameter t = mod (∑ E2, M/2) + mod (∑ E2, N) + mod (∑ E2, M/2 + N) + 1.
Step 6. Perform pixel value diffusion according to (12). Then the cipher-image is obtained as .
To enhance the security, we can perform more rounds from Step 5 to Step 6, that is, multiple diffusion. In this paper, we take 5 rounds. The decryption process is just the reverse of the encryption one.
4. Numerical Experiments
In this section, some experimental results of the proposed image encryption method are presented. The work is accomplished in a computer of Intel(R) Core(TM) i3-2350M, 2.30 GHz CPU, running Windows 7. The plain-image is Lena with size 256 × 256 shown in Figure 2(a). Figure 2(b) is the cipher-image obtained by the proposed method using the initial values x0 = −0.175, y0 = 0.216, z0 = −0.811, and p = 30.

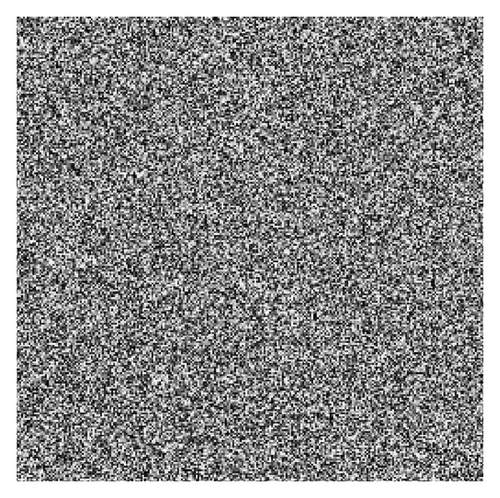
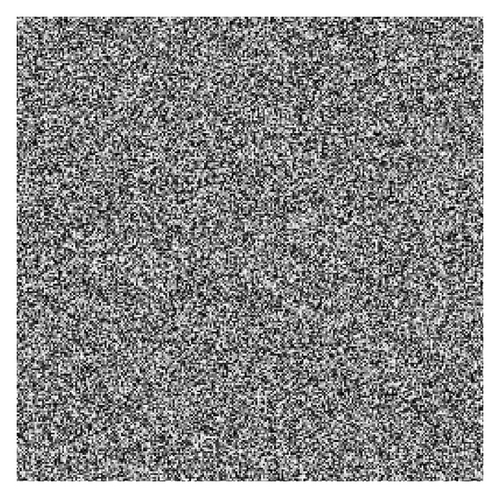
5. Security Analysis
(1) Key Space. The key space refers to the total number of distinct keys which can be used in the algorithm. A good encryption algorithm should have a large key space to avoid brute-force attacks. In the proposed algorithm, the size of the key space can reach p × 1042 if the computation precision is 10−14. This value justifies that our encryption algorithm has a sufficiently large key space.
(2) Sensitivity Analysis. High key sensitivity means that a little change in the key will cause a huge change in the decrypted image. In our algorithm, with the original keys x0 = −0.175, y0 = 0.216, z0 = −0.811, and p = 30, we encrypt the plain-image Lena to the cipher-image shown in Figure 2(b). The decrypted image using a key with only a tiny difference, that is, x0 = −0.17500000000001, is depicted in Figure 2(c). Figure 2(d) shows the decrypted image with a wrong key of y0 = 0.21600000000001. Figures 2(e) and 2(f) are similar wrong decrypted images. They all indicate that the new algorithm is very sensitive to the key.
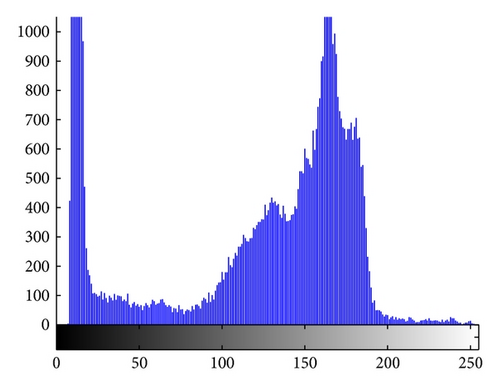
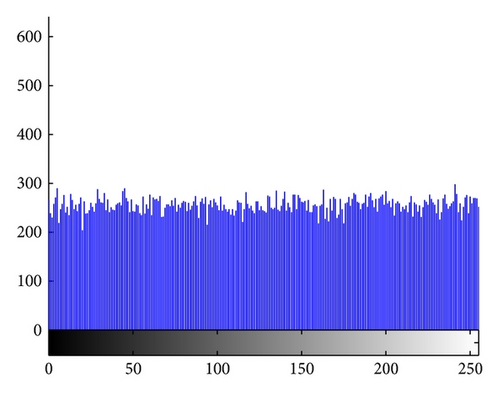
(3) Histogram Analysis. The histogram, also called the gray scale distribution, displays and reflects the distribution of pixel values in an image. Figures 3(a) and 3(b) are the plain-image and cipher-image of Cameraman while Figures 3(c) and 3(d) are their histograms, respectively. These diagrams show that an attacker can hardly launch any statistical attack because the gray values are distributed uniformly.

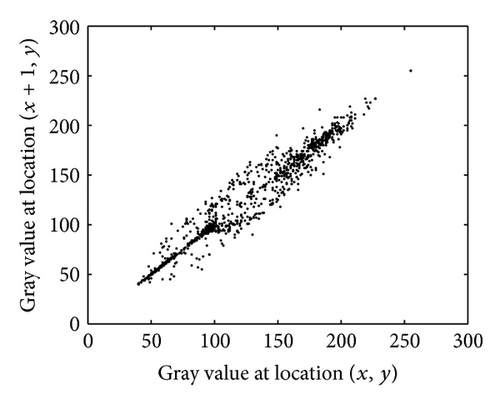
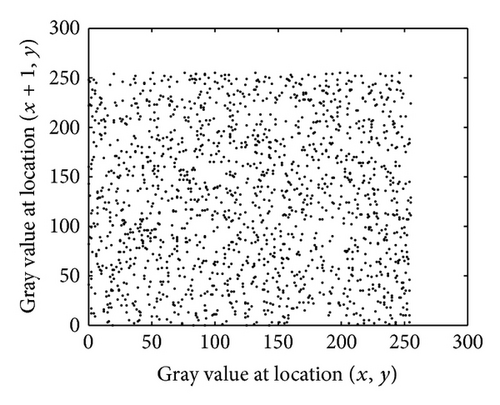
First of all, 2500 pairs of adjacent pixels of the Rice image (Figure 4(a)), in horizontal, vertical, and diagonal directions, are randomly selected. The results are listed in Table 1, in which we find that the correlation coefficients of two adjacent pixels in the cipher-image are almost zero. Figures 4(b) and 4(c) show the gray-level distribution of two horizontally adjacent pixels in the plain-image and the cipher-image, respectively.
| Model | Plain-image | Cipher-image |
|---|---|---|
| Horizontally | 0.97799 | − 0.02068 |
| Diagonally | 0.98125 | − 0.04076 |
| Vertically | 0.96017 | 0.04687 |

In the proposed method, a small difference in the plain-image can affect the whole cipher-image. The results can be found in Table 2 (here, we randomly choose a pixel at position (201,100)). The percentage of pixel changed in the cipher-image is over 99.5% even with a one-bit difference in the plain-image. The UACI values are over 33.4%, as required for good protection [22, 23, 25]. Thus, the proposed encryption method is able to resist the differential attack.
| Image | Size | UACI | NPCR |
|---|---|---|---|
| Cameraman | 256 × 256 | 0.33589 | 0.99579 |
| Lena | 256 × 256 | 0.33562 | 0.99578 |
| Straw | 512 × 512 | 0.33446 | 0.99594 |
| Gravel | 512 × 512 | 0.33457 | 0.99594 |
(6) Speed Analysis. There are already many image encryption algorithms suggested. Here, we compare the speed of our method with [10, 11, 21], which is also composed of two stages of permutation and diffusion. The average time cost is listed in Table 3. The data show that the proposed method is fast and efficient, which is more suitable to encrypt large images.
| Image | Lena | Grass | Cameraman | Straw |
|---|---|---|---|---|
| Value | 7.990 | 7.992 | 7.990 | 7.991 |
(8) Other Comparisons. Compared with the existing methods [2, 22, 26], the proposed one using the time-delay chaotic system can show more natural phenomena when generating the chaotic sequence. Besides, only two blocks are decomposed with a new control parameter t which is determined by the plain-image and so the implementation time is shorter. To make the attack infeasible, any algorithm should have the ability to resist the chosen-plaintext, the chosen-ciphertext, and the known-plaintext attacks. However, in spite of good randomness and high computational efficiency, the keystream remains unchanged in the encryption process of [27], which cannot offer the security requirement [28]. In [26], the UACI is less than 28% while we can reach 33% in our method. All these show good performance by using the proposed scheme.
6. Conclusions
In this paper, a novel image encryption method based on chaotic maps and Circulant operation has been proposed. Position scrambling is employed to remove the high correlation between adjacent pixels in the plain-image. Meanwhile, to avoid statistical attacks, the modular function by blocks is adopted in the diffusion stage. Security analyses on (1) key space and key sensitivity, (2) histogram, (3) correlation between two adjacent pixels, (4) differential attacks, and (5) operating speed have been carried out. All the results are satisfactory which justify the effectiveness of the proposed algorithm for image encryption. Furthermore, the algorithm can be extended to images at any aspect ratio by the generalized Circulant matrix (see Definition 2 and appendix).
Acknowledgments
This project was supported by the National Natural Science Foundation of China (no. 11226091), the grant from CityU (Project no. 7008106), the Science & Technology Program Foundation of Zhanjiang City of China (no. 2011C3109002), and the Natural Science Foundation of Guangdong Ocean University of China (no. 1212334).




