Integrating carrier selection with supplier selection decisions to improve supply chain security
Abstract
Supply chain security is a major concern for logistics managers who have responsibility for inbound and outbound shipments to and from both domestic and international locations. We propose here that logistics decisions concerning security in the supply chain will be made more effectively when made in concert with decisions in related supply chain processes, especially supplier and carrier selection. Indeed, managers may minimize cost, transit time, and security risk by integrating decision processes internally, as well as with their carrier's and supplier's operations. Thus, we account for both intra-firm collaboration between logistics and purchasing managers, as well as inter-firm collaboration among buyers, suppliers, and carriers in a supply chain. In this paper, we propose a decision process that features a set of security rules and a multi-objective optimization model to accomplish this aim. We then provide an illustration to demonstrate the potential usefulness of these concepts in practice.
1 Introduction
Supply chain security is an important consideration for logistics managers who have responsibility for shipments to and from both domestic and international locations. Concerns about theft and damage have long been a problem in the transportation industry; more recently, apprehension about terrorism has motivated governments to impose regulations to prevent unauthorized people, contraband, or weapons of mass destruction from entering the country (Closs et al., 2008). Both shippers and carriers now need to respond to security mandates that were put in place to reduce terrorist threats (Williams et al., 2008). Similarly, firms are developing risk response plans for recovering from the aftermath of a terrorist attack that would influence their business operation (Sheffi and Rice, 2005).
At the same time, transportation carriers and port operators have implemented policies, procedures, and technologies for cross border shipments to aid in the protection of supply chain assets that include product, facilities, equipment, information, and personnel. Shippers can minimize security-related impacts by selecting these security-conscious carriers, shipping via secure ports, meeting packaging security requirements, and providing background information on key personnel (Rinehart et al., 2004). Thus, a key decision that relates to cargo security is the selection of the transportation mode and carrier to move the firm's inbound and outbound freight. Managers typically consider multiple attributes such as price, transit time, and equipment availability when making this decision (Meixell and Norbis, 2008). For international shipments, the attention that a carrier pays to security practices is also an important criterion, as discussed in Voss et al. (2006).
A second decision that affects cargo security is in the field of supply management, i.e. the selection of suppliers. Supply managers typically consider multiple attributes such as cost, quality, and delivery. Security concerns are often not rigorously factored into supplier selection, however, even though considerable risk is introduced into the supply chain through this decision (Rogers et al., 2004). Depending on the criticality of the material or component being sourced, the buying firm may not even visit the company's originating site or may rely on a third party to assess the supplier and their facility. Certainly cost is a key factor in managing supply chain security; the cost of funding additional security initiatives has been estimated at $151 billion (Russell and Saldanha, 2003).
Transportation carrier and supplier decisions are typically made sequentially – first suppliers are selected then carriers. Here, we argue that these decisions be made collaboratively and simultaneously, and then develop an advanced mechanism that concurrently improves security while minimizing total cost. This mechanism allows for analysis of tradeoffs between these two important criteria; we show in this research that the tradeoff between security and cost can be better achieved in a practical, real-world setting if these decisions are made concurrently. Furthermore, we address the benefits of collaboration by incorporating constructs into the modeling framework that encapsulate the security-related synergies that occur when these decisions are integrated. In this research, then, we aim to show that collaboration between logistics managers and purchasing managers as well as among buyers, suppliers, and carriers in a supply chain can result in improved supply chain security performance.
To accomplish these aims, we tackle a critical issue in supply chain security, i.e. the difficulty of quantifying security to enable its application in a mathematical decision model. We develop a mechanism for quantifying and measuring supply chain security to enable the evaluation of potential suppliers and carriers within the multi-objective structure of the selection model. This approach prescribes how a firm may introduce ordinal data into a mathematical program, and integrate the construct into a decision process that addresses both supplier and carrier selection.
In the next section, we review the literature that aids in addressing these questions, followed by a discussion of security measurement issues in supplier–carrier selection. The next section describes the mathematical formulation for the optimization of the selection problem. This section is followed by a description of the proposed decision process for selecting carriers and suppliers. We then provide a numerical example to illustrate the concept of security scales and thresholds in this context of mathematical modeling. The paper closes with conclusions and a discussion of next steps.
2 Literature review
There are three areas of literature that are helpful in addressing this particular security-modeling problem: carrier selection, supplier selection, and supply chain security measurement. We discuss each in this section.
The carrier selection problem has received a good deal of attention in the literature, which may be partitioned into selection criterion and selection models. Sources such as Coulter et al. (1989), Gibson et al. (1993), Murphy and Farris (1993), and Evers et al. (1996) report that logistics managers use a variety of attributes to select carriers, including rate, reliability, transit time, flexibility, customer service, claims handling, equipment availability, service frequency, rate changes, loss and damage, and financial stability. Similarly, the research literature has reported numerous models developed to aid managers when making these mode-choice and carrier selection decisions. Some of these models address multiple supply chain decisions, as in joint selection of carrier and destination port (Garrido and Leva, 2004), customer assignment and order aggregation for “milk runs” (Caputo et al., 2005), shipment size, number of segments in the transport chain, use of consolidation and distribution centers, and mode choice for each segment (deJong and Ben-Akiva, 2007).
Some authors in this area have developed single objective optimization models for the carrier selection problem, as in Moore et al. (1991), which minimizes freight cost by coordinating front haul and back haul lanes. Other authors advocate for three-way supply chain coordination among buyer, supplier, and carrier, as in Carter and Ferrin (1995) and Walters (1988). In Miller and deMatta (2003), the authors developed a multi-plant production and transportation model that includes the mode-choice decision. Dobie (2005) analyzes how carriers and shippers may select each other such that their joint cost of compliance, transit time, and transit time variation are all reduced. In another case (Liao and Rittscher, 2007), the authors integrated lot sizing, supplier selection, and carrier selection in their multi-objective model that minimizes cost, number of rejected items, and late deliveries subject to demand satisfaction and capacity constraints. However, little attention has been given to security as a carrier selection criterion or as a construct in associated models (Meixell and Norbis, 2008). One exception is Voss et al. (2006) in which the authors identify security as a carrier selection attribute in their Theory of Reasoned Action model.
Supplier selection also has received a great deal of attention in the academic research literature. Several literature reviews can be found that addresses this research, including Ho et al. (2010), Aissaoui et al. (2007), Wilson (1994) and the classic review by Weber et al. (1991). Some of this literature addresses the total cost of ownership concept (Ellram and Siferd, 1993; Degraeve and Roodhooft, 1999; Zsidisin et al., 2003). Certainly total cost of ownership will include logistics-related costs, as discussed in Ghodsypour and O'Brien (2001) and Liao and Rittscher (2007). Other supplier selection research recognizes the multi-objective nature of the selection decision, as in Weber and Current (1993), Dulmin and Mininno (2003), Narasimhan et al. (2006), and Basnet and Weintraub (2009). Finally, some authors adopt a supply chain management perspective, and argue for integration of processes both within the organization and across enterprise boundaries, as in Lee et al. (2001), Liao and Rittscher (2007), and Kheljani et al. (2009). Voss et al. (2009b) survey managers and use conjoint analysis to assess the degree to which managers in food supply chains trade-off price and delivery reliability for supply chain security. Overall, few of the supplier selection models in the literature address security.
A third area of literature is that of supply chain security. Here, we are particularly interested in security-related measurement schemes as in Rinehart et al. (2004), Autry and Bobbitt (2008), and Williams et al. (2009). One study in particular (Closs and McGarrell, 2004) suggests that the degree to which a supplier/carrier employs sound supply chain security practices can be assessed by evaluating relationships, security efforts within existing processes, and incident security management. Also in this literature are empirical studies such as Voss et al. (2009a) who analyze the relationship between strategic priority and security performance. Other researchers discuss the collateral benefits that result from implementing enhanced supply chain security procedures (Rice and Spayd, 2005), especially important to organizations undertaking a cost–benefit analysis of improvements to security practices.
Consequently, relatively little attention has been given to the problem of incorporating supply chain security measures into carrier and supplier choice decision models. At the same time, there has been little research on the topic of joint carrier and supplier choice, and the benefits that would likely result from such a coordinative effort. This research addresses these gaps with a multi-objective optimization model that includes carrier and supplier choice as decision variables, with an objective function structure that includes the security dimension.
3 Supply chain security and supplier–carrier selection
A premise of this research is that collaboration improves the overall performance of the operation, which occurs because the simultaneous selection of carriers and suppliers allows for opportunistic yet judicious security combinations. Similarly, problematic security combinations must also be avoided when simultaneously selecting supplier and carriers. A central issue, then, is the quantification and integration of security criteria into this decision process. In this section, we describe a method that allows for security rating of both suppliers and carriers, followed in the next two sections by the development of a decision process that features this data as part of a multi-objective mathematical model to aid in managing the trade-offs that result from this expanded view of carrier and supplier selection.
3.1 Security measurement
In this research, we measure security for the purposes of evaluating potential suppliers and carriers. Evaluating supply chain security requires a framework for assessment, a scheme for summing across multiple items within a security category, and a threshold, or minimum, below which a supplier or carrier would be deemed inadequate and rejected. Our framework is based in part on Closs and McGarrell (2004), who propose separate categorization schemes for suppliers and carriers. Under this framework, supplier security practices can be categorized into three themes: relationships, security efforts within existing processes, and incident management.
The first theme, relationships, is based on the notion that a supplier that builds and maintains strong relationships with customers, suppliers, government, carriers, and port operators will bring a higher level of security to the venture than one who does not. The second theme addresses the degree to which security considerations have been incorporated into existing processes and include, for example, the thoroughness of background checks when screening personnel at the time of hiring along with training programs on security practices. These suppliers obviously present a lower security risk than those who do not utilize such practices. The third theme addresses incident security, and the degree to which a supplier has set up management processes for security planning, mitigation, detection, response, and recovery. Planning for response to security incidents puts both the supplier as well as the buyer in better position to react in the event an incident occurs.
For each of these themes, Closs and McGarrell (2004) provide guidance on assessing each dimension based on a firm's practices, which may be rated as basic, enhanced, or advanced. Here, we adapt these themes and measurement indicators, as listed in Table 1. In practice, the values used for any of these indicators could be based on observations made by a buyer within the firm, or perhaps an independent rating agency could support the assessment process by collecting this information for suppliers and making it available to a firms potentially interested in purchasing from the supplier.
| Supplier 1 score | Supplier 2 score | Supplier 3 score | |
|---|---|---|---|
| Relationships | 4 (80%) | 2 (40%) | −1 (0%) |
| Supplier | 3 | 1 | 0 |
| Government | 1 | 1 | 1 |
| Carrier | 3 | 2 | 2 |
| Terminal/port operator | 3 | 1 | 1 |
| Customer | 2 | 2 | 0 |
| Security efforts within existing processes | 12 (100%) | 5 (42%) | −2 (0%) |
| Personnel security | 3 | 1 | 0 |
| Information security | 3 | 2 | 1 |
| Facility security | 3 | 1 | 0 |
| Inventory security | 3 | 2 | 1 |
| Transportation security | 3 | 3 | 0 |
| Transportation tracking and visibility | 3 | 2 | 2 |
| Receiving management | 3 | 0 | 0 |
| Storage management | 3 | 1 | 1 |
| Shipping management | 3 | 2 | 1 |
| Management education | 3 | 2 | 2 |
| Internal operations management | 3 | 2 | 1 |
| Supply chain education | 2 | 0 | 1 |
| Incident security management | 3 (60%) | 0 (0%) | −3 (0%) |
| Planning management | 3 | 1 | 1 |
| Mitigation management | 3 | 0 | 0 |
| Detection management | 2 | 1 | 1 |
| Response management | 1 | 3 | 0 |
| Recovery management | 1 | 1 | 0 |
- *Rating scheme adapted from Closs and McGarrell (2004).
For transportation carriers, Closs and McGarrell (2004) identify several essential security practices which we categorize into two themes: “risk and response,” and “supply chain relationships.” Risk and response indicators include practices that are in place at the carrier that either reduce risk or improve response in the event of an incident; for example, a security education program for drivers reduces the risk of an incident. Supply chain relationships are important here too, because a carrier that builds and maintains strong relationships with shippers, government, and port operators will bring a higher level of security. One means by which carriers demonstrate a security-oriented relationship in a supply chain is through participation in the Known Shipper Program (KSP), which indicates that a carrier has had experience or is otherwise knowledgeable about the shippers they serve. When practical, using the same carrier repeatedly for international shipments greatly enhances not only the ease but also the security of shipping. Thus, building a collaborative relationship with a carrier improves security for both the buyer and the supplier. These themes and indicators are listed in Table 2.
| Carrier 1 score | Carrier 2 score | Carrier 3 score | |
|---|---|---|---|
| Risk and response | 4 (36%) | 7 (64%) | −2 (0%) |
| Inspection standards | 1 | 2 | 2 |
| Security measurement process | 1 | 1 | 2 |
| Inspection execution | 2 | 2 | 0 |
| Security education for drivers | 2 | 2 | 0 |
| Customer role in driver requirements | 0 | 0 | 1 |
| Employee background checks | 2 | 3 | 1 |
| License requirements | 2 | 2 | 0 |
| Policies for high-risk shipments | 2 | 3 | 0 |
| Tracking technology | 2 | 2 | 0 |
| Incident response plans | 1 | 2 | 2 |
| Testing for incident response plans | 0 | 1 | 1 |
| Shipper relationship | 3 (100%) | 0 (0%) | 0 (0%) |
- *Rating scheme adapted from Closs and McGarrell (2004).
To operationalize the scheme presented in these tables into the supplier and carrier selection decision process, performance in each thematic area must be assessed. Closs and McGarrell (2004) recommend a system that includes basic, enhanced, and advanced levels. We add a fourth level for inadequate performance, i.e. the carrier/supplier has not achieved a basic level. Closs and McGarrell (2004) provide a list of practices for each security level for each indicator. For example, a supplier that relies on passive measures such as locked doors and fences for facility security would be evaluated as basic, while another supplier that also uses video and human inspection would be assessed as advanced. In the relationship theme in the carrier security framework, we allow for a carrier to be assessed at only two different levels: basic, which designates no relationship, or advanced which designates the existence of a relationship.
The overall security score for each supplier and carrier is then computed based on achievement of a minimally acceptable performance level for each indicator in each thematic area. For the purposes of illustration, we propose setting the acceptable level at the enhanced level, and then assess based on the count of indicators that meet or exceed the target. We treat indicators at a basic level as neutral with 0 points, and impose a penalty of 1 point for indicators that are deemed inadequate. So, for the hypothetical scenarios in Table 1, supplier 3 has achieved enhanced or advanced level on just one indicator relating to the relationship theme, with a basic rating on two indicators, and penalties for inadequate performance on two indicators, computed as 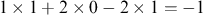 . This mechanism is similar to quality scoring systems that have a customer requirement that must be met or exceeded.
. This mechanism is similar to quality scoring systems that have a customer requirement that must be met or exceeded.
The total score for a candidate supplier, then, is the aggregation of the theme level security scores, expressed as a vector of three values. For example, supplier 1 scores (4, 12, 3), i.e. 4 on relationships, 12 on processes, and 3 on incident management. The security score vector for carriers is expressed as a vector of two values. For example, carrier 1 in Table 2 evaluates at (4, 3). In this way, we can compare suppliers (or carriers) on different themes; when a single security score that integrates all themes is necessary, weights can be assigned. The relative importance of themes would differ by industry or perhaps by firm.
The illustration in Tables 1 and 2 shows hypothetical security indicator ratings for three suppliers and three carriers based on this security rating scheme. Note that the column values under each supplier and carrier provide a score for each theme expressed as both a count (e.g. “4” for supplier 1 relationships) and a percentage of the number of areas achieving a top score of 2 or 3 (e.g. 80% for the same).
Next, we develop a security threshold level that allows for screening out suppliers or carriers who do not meet a minimum-security performance level. Our approach is based on the best-in-class paradigm that selects the highest performing suppliers and carriers relative to firms in the same sector, thereby ruling out those with the lowest rankings. After the security scores are computed, potential suppliers and carriers are ranked, from which the top performing firms are selected for further consideration in the tradeoff analysis. This best-in-class approach for setting thresholds is used to select investment alternatives for sustainability portfolios, as described in Schafer (2005) and Benijts (2008).
For the purposes of our illustration, we set a threshold at 40%, which means that the top 60% of the best performing companies have security levels deemed as minimally acceptable or better. In practice, each buying firm would choose the threshold level based on individual circumstances, making the list of approved suppliers and carriers more or less inclusive as appropriate. Note that in this research, we use the security performance dimension twice; first as a classification tool to eliminate poor candidates and then as an optimization criterion to select the best. This double round process allows us to be more flexible in the first round and set the threshold at a lower level, say 20%, knowing that the criterion will be maximized to the extent possible within the multi-objective optimization framework.
3.2 Collaborative security
In the scope of this research we analyze security associated with each individual supplier and carrier as well as the enhanced security resulting from collaboration between shippers and carriers. In logistics practice, shippers and carriers can collaborate to improve transportation capacity utilization while reducing inventory cost (Cooke, 2000; Feng and Yuan, 2007), to coordinate empty backhauls (Esper and Williams, 2003; Ergun et al., 2007), or to synchronize load planning and delivery schedules (Dutton, 2003). In this research, we adopt the definition proposed by Fugate et al. (2009), who defined collaboration in terms of joint information sharing and decision making that leads to shared responsibility for outcomes in the supply chain.
Sharing information and integrating decision processes also improves supply chain performance relative to security (Sheffi, 2001; Russell and Saldanha, 2003; Autry and Bobbitt, 2008). Supply chain partners contribute to security through the sharing of timely and valid information, through the use of RFID for tracking purposes, and through the level of security committed by the partner for their own information systems (Voss et al., 2009b). Additionally, decision processes, both within the firm and between firms, may be integrated to improve supply chain security. In this paper, we allow for this type of collaborative security improvement to be factored into the carrier and supplier selection process.
Specifically, the enhanced information in this context allows for the security requirements to be reduced below the threshold value if either the carrier or supplier is highly trusted. Under the themes utilized above for individual classification of carriers, any supplier, regardless of its individual qualifications, will be allowed if it utilizes a carrier that has an existing association with this shipper and if this carrier also ranks over 50% in risk and response. This judgment is based on the assumption that a carrier with this qualification has a strong security orientation, and provides a level of oversight in its interaction with any supplier for which it ships.
Similarly, if a supplier ranks over 50% in all three categories (relationships, process, and incident management), then any carrier that ranks over 50% in risk and response may be used, even if the carrier does not have an existing relationship with the buyer. If a high-performing supplier knows and trusts a certain carrier, the attenuation of the security criteria for carrier selection can be justified.
4 Mathematical formulation for the supplier–carrier selection model
In this section, we develop a mathematical optimization model to aid in the process of jointly selecting suppliers and carriers in a manner that incorporates a security criterion. The key assumptions used in formulating this model are:
- The model is formulated from the point of view of a single buyer.
- The buyer's demand is always 100% satisfied by one or more supplier in combination with one or more carrier. This is concomitant with classical transportation models.
- Because demand and capacity are time dependent the model needs to adopt a time base of one period.
The process developed in this paper, and the model developed in this section, form a set of decisions that are typically encountered in the firm at the strategic level. Specifically, the model integrates the selection of the supplier and the carrier, both of which are decisions that can be and often are made relatively early in the product development process. Note that the primary decision variable for commodity quantity is not time indexed, as it represents an allocation, on average, over the life of a product program.
This formulation incorporates transportation as a “carrier–mode” combination, where the choice of a carrier implies the choice of a mode. If a carrier offers more than one mode, then each of them will be represented as a different alternative. We refer to this “carrier–mode” combination in the model as “carrier,” with no loss of precision. For routes that employ multiple modes in series, we identify it using the mode that dominates the route, i.e. that establishes the cost and service level for that shipping alternative.
Note also that security is represented in the model as either a triad (for suppliers) or a dyad (for carriers), and computed as described earlier. The security score is first used to disqualify suppliers and carriers that do not reach the threshold individually or in collaboration. The score is then used as part of an objective in the multi-objective formulation, and measured as a deviation from the perfect rating in each category, with all categories equally weighted.
4.1 Decision variables and parameters
The following decision variables are utilized in the model:
| qijk: | quantity of commodity k purchased from supplier i and delivered by carrier j |
| xik: | 1 if the buyer uses supplier i for commodity k, 0 otherwise |
| yjk: | 1 if the buyer uses carrier j for commodity k, 0 otherwise |
| ssd: | Overall security deviation from goal for suppliers (constrained to be positive) |
| scd: | Overall security deviation from goal for carriers (constrained to be positive) |
The formulation of this model includes I suppliers, indexed as i, J carriers, indexed as j, and K commodities, indexed as k. Known parameters include: cost, security, and capacity parameters. There are also weight parameters for the objectives and auxiliary parameters needed for the formulation.
Cost will include more than one component, among them, unit purchasing cost of the item, transportation cost, in-transit inventory cost, lateness cost, and rejected items (i.e. quality) cost. The last two costs penalize the firm an amount equivalent to the cost to expedite a late product or producing and expediting a replacement for a low quality product. Note that quantity discounts for purchase cost are not considered here.
An important issue in this model is the representation of transportation cost in the objective function, as there are different approaches used in practice (Coyle et al., 2003, 2006; Murphy and Wood, 2011). In this research, we base our modeling of transportation rates on the cost of providing service, and allow for both fixed and variable components that reflect the sum of the modes on the route, thereby reflecting the transportation cost structure in total. We posit here that this type of rate model reflects the cost of service, which has advantages in a collaborative supply chain where customers recognize costs incurred by their suppliers and carriers, and take them into account in their decision-making processes.
For a particular commodity, the cost incurred by the transportation company often varies with distance shipped and with weight of the shipment. Since we model transportation cost for a purchase unit of a given commodity, the weight-based variable costs associated with the shipment can be treated as fixed. The variable costs associated with mileage, including costs such as fuel, labor, and equipment maintenance, are factored into the rate model as a variable cost. Using a mileage-based model of this type, which originates in the economics of transportation, allows for a truer representation of carrier cost than a simple rate quoted for an origin to destination. This is especially important in this research as we wish for our selection model to allocate logically to more than one carrier when policy dictates. This type of transportation cost model also provides a necessary feature as multiple carriers on a route would indeed impose their own fixed cost, which certainly may differ from one carrier to the next.
We note here that the decisions made by the shipper with respect to suppliers and carriers may affect the routing decisions of the carriers. We do not, however, include in this rate model the benefits that buyers and their carriers might accrue by jointly considering selection and routing decisions. This is, however, an interesting topic for future research.
| Among the cost parameters: | |
| Cik: | unit cost of commodity k by supplier i |
| Rij: | distance on which transportation cost is based |
| Fik: | fixed cost for using supplier i for commodity k |
| Gjk: | fixed cost for using carrier j for commodity k |
| TTij: | transit time from supplier i utilizing carrier j |
| Tjk: | unit transportation cost for carrier j per unit of commodity k and per unit distance |
| H: | in-transit inventory holding cost per dollar and per unit of time |
| Eijk: | unit cost for replacing/expediting one unit of commodity k from supplier i through carrier j |
| Nijk: | percentage of late deliveries from supplier i and carrier j for commodity k |
| πijk: | percentage of rejected items from supplier i and carrier j for commodity k |
| Security parameters and goals are: | |
| SSil: | security score for supplier i in theme l |
| SCjm: | security score for carrier j in theme m |
| SSGl: | security goal for suppliers in theme l |
| SCGm: | security goal for carriers in theme m |
| Capacity parameters are: | |
| Dk: | buyer demand for commodity k |
| Qik: | total capacity for supplier i for commodity k |
| Pjk: | total capacity for carrier j for commodity k |
| Weight parameters: | |
| Ωn: | weight for objective function n, where n=1, 2, 3 |
| Auxiliary parameter: | |
| M: | a very large number |
4.2 Objectives
Managers typically consider multiple attributes such as price, delivery and quality when making supplier (Monczka et al., 2005) and carrier choice decisions (Meixell and Norbis, 2008). In our optimization model we also incorporate security as one of the objectives along with delivery and quality. These are organized into three objective functions; the first minimizes cost (1), the second minimizes deviation from a security goal of a 100% (2), and the third minimizes number of late and rejected items (3).
In this collaborative planning problem, costs incurred by the buyer, the supplier, and the carrier in the supply chain are all included. Supply management decisions, including supplier and carrier selection, are best managed when integrated with the firm's competitive strategy (Benton, 2007). In our approach we minimize the overall cost incurred by the supply chain, disregarding which section of it (buyer, supplier, or carrier) actually incurs the cost. We note that some buyers engage a third party logistics provider (3PL) to arrange for transportation and other services on their behalf. As such, the 3PL is sometimes an agent in the problem we present here, but one without explicit costs beyond their fees. Although 3PLs are a major participant in supply chain collaboration today, they are not explicitly modeled here as they are peripheral to our discussion.
Costs objectives here include the minimization of the five cost components: purchasing price, transportation cost, in-transit inventory cost, lateness, and quality. The number of late and rejected items also provides a measure of the quality and as such they are minimized in the third objective function; but as they also represent a cost of item repositioning, this cost is minimized as part of the first objective function.
4.3 Constraints
The model has the typical capacity constraints including demand, which is described in constraint number (4), supplier capacity (5), and carrier capacity (6), all defined for each commodity. In this formulation, we allow for a restriction on the amount of the quantity purchased from any one supplier, and the amount of the quantity shipped on any one carrier using capacity constraints (5) and (6). Then, logical constraints establish that if a quantity other than zero is received from a supplier, that supplier is active (9), same for the carrier (10). In this model, security constraints that will normally guarantee that each selected supplier and each selected carrier has a security score above the threshold are not necessary because the suppliers and carriers are pre-screened to ensure they are qualified. Security goal constraints are, however, used to measure the deviation from the goal (7 and 8). Domain constraints are then listed in (11) through (15).
4.4 Overall formulation
The model is thus formulated as follows:
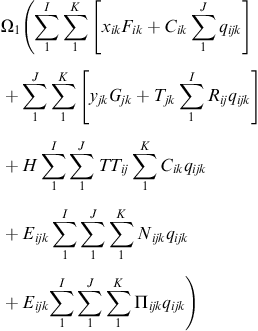 (1)
(1)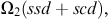 (2)
(2)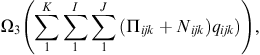 (3)
(3)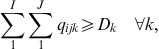 (4)
(4)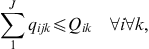 (5)
(5)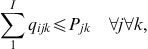 (6)
(6)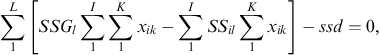 (7)
(7)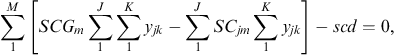 (8)
(8)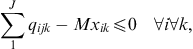 (9)
(9)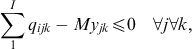 (10)
(10)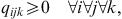 (11)
(11)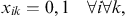 (12)
(12)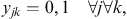 (13)
(13)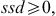 (14)
(14)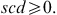 (15)
(15)5 A decision process for supplier–carrier selection
Earlier sections address two key components of a collaborative supplier–carrier selection process: (1) quantifying security information for incorporation into a mathematical model and (2) structuring the model to select the supplier and carrier in combination. In this section, the authors propose a multi-tier interactive approach to accomplish this joint selection process, which is represented in Fig. 1. This decision process is based in part on commonly used supplier selection processes from industry, as described in sources such as Fawcett et al. (2007), adapted to include security pre-screening and collaborative supplier–carrier selection.

This approach begins with the buyer issuing a request for quotation (RFQ) for materials and for transportation services. Suppliers and carriers answering this RFQ enter the POOL of possible candidates. Supplier quotes may be requested first, as carrier quotes are typically based on knowledge of the shipment origin. The suppliers and carriers in the POOL are then evaluated according to a set of RULES based on security qualifications as described earlier. It is here that the candidates are compared with established security thresholds.
The suppliers and carriers who qualify are next screened for triviality or incoherence by the buyer in the pre-screen (PS) module. If the qualified pool at this point does not provide any acceptable supplier–carrier combination, the buyer goes back to either redefine (i.e. relax) the rules for security screening, or generate a new RFQ to acquire new candidates. For example, if a 75% threshold results in too few suppliers and carriers, a relaxed threshold of 60% might be used (i.e. CH). If, however, the 75% threshold is essential, then a new search for suppliers and carriers through a new RFQ would be required (i.e. RFQ).
The accepted supplier and carriers from the pool then enter the optimization (OPT) module described in the last section, where a multi-objective MIP will select the best combination of suppliers and carriers. The OPT module may be run multiple times to generate alternative solutions, i.e. non-inferior solutions for the tradeoffs in accordance with a given set of weights. For each new run of the OPT module, weights are changed in the module RR, solutions are retained for further comparison in STORAGE and the buyer decides whether to further explore alternative tradeoffs by re-running (RR) to generate another instance with a different set of weights for the objectives, or to stop (STOP).
Note that we use two early steps in the decision process to accomplish security checks, followed by a security constraint in the optimization model that measures the deviation from security goals for suppliers and carriers. Also note that the optimization procedure provides a mechanism for integrating the carrier and the supplier selection processes.
Through a numerical illustration in the next section, we demonstrate that collaborative planning in this process improves performance in two ways. The first is through an intra-firm collaboration mechanism between logistics and purchasing managers that allows for both security and cost synergies to be created. Second is an inter-firm collaboration mechanism between buyers and suppliers/carriers, as suppliers and carriers share security-related information about each other in this process. Additionally, this illustration demonstrates how the tradeoffs generated by the multi-objective MIP are useful to the manager faced with a collaborative decision as described here.
6 Numerical illustration
In this example, we consider a firm that sources a component with one or more domestic or international suppliers, with a specific goal to incorporate supply chain security into the supplier and carrier selection process. We assume that management is willing and able to undertake the steps necessary to minimize the cost of providing a secure supply chain, which in this case, includes internal coordination when choosing suppliers and carriers. The firm also coordinates with the suppliers and/or the carriers to maximize supply chain security in this situation. Thus, security is a necessary criterion in carrier and supplier selection, in addition to the typical criteria of price, delivery, and quality. As such, we simulate the process described in Fig. 1, incorporating both the security measurement scheme and the optimization model developed in earlier sections. The decision process is broken into three groups of steps: generating candidates (RFQ and POOL), applying the pre-screening rules (RULES, PS, and CH), and the optimization process (OPT, STORAGE, and RR).
6.1 Generating supplier and carrier candidates
We simulate this planning process for a hypothetical buyer using randomly generated but realistic values for the parameters. Supplier and carrier alternatives are constructed in a systematic fashion, by varying the values for the price, security, and distance parameters using high and low settings. For each parameter, a range was established for “high” and another for “low” and within that range values were randomly generated.
For the suppliers, the values for the fixed and per unit costs were drawn from a uniform distribution with bounds 10 and 20 for fixed costs and 2 and 5 for variable cost per unit. Individual supplier capacities were set as a percentage of the demand, between 10% and 25% of the total demand to allow for the selection of multiple suppliers and carriers. The quality rating for suppliers was expressed as a percentage of products of acceptable quality, and drawn from a uniform distribution with limits of 75% and 100%. Distances in miles from the buyer were set to either high (1200) or low (200).
For the carriers, the transportation cost was specified in the simulation in terms of fixed and per mile costs. The values for these cost components were then drawn from a uniform distribution with bounds of 100 and 200 for fixed costs and 1 and 3 for the mileage cost. The carriers' rejection rate was expressed as percentage of good shipments, and delivery rate was expressed as on-time percentage. Both were randomly generated from a uniform distribution between the limits of 75% and 100%. Carrier capacities were all set to a fixed value of half of the demand, allowing for multiple carriers to be selected.
Individual security scores for suppliers and carriers in each category were generated as explained in “Security measurement” and shown in Tables 1 and 2. The percentage value is computed as the percentage of categories on which the supplier/carrier achieves a top score of 2 or 3. For example, supplier 1 achieves a top score on four of the five categories in the relationships theme, and is thus evaluated at 80%. Security goals were all set to 100, for suppliers [SSG(l)] for each of the three themes and for carriers [SCG(m)] for each of the two themes.
This scheme resulted in 32 suppliers and 32 carriers, as there are five criteria with two levels (high and low) for each set of candidates. We present a sample of 15 in Tables 3 and 4. As an example, supplier 1 has a high price with high performance on each of the three security themes (relationships, processes, and incidents). Similarly, carrier 1 has a high price with high performance on each of the two carrier security parameters (risk/response and relationship). Note that an “ideal” supplier and carrier (i.e. lowest price and highest delivery/quality/security) were omitted from the study, as including it provides a predictable case where the ideal supplier and carrier always dominate. Here, we are interested in exploring the tradeoffs. In this way we simulate the first steps of the process in Fig. 1, RFQ and POOL, which systematically generates supplier and carrier candidates and places them in the POOL.
| Security levels | Costs | Security values | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Price | Theme 1 | Theme 2 | Theme 3 | Distance | Variable | Fixed | Relationships | Process | Incidents | |
| Supplier 1 | H | H | H | H | L | 0.046 | 1.52 | 97 | 95 | 60 |
| Supplier 2 | H | H | H | L | H | 0.043 | 1.53 | 66 | 63 | 9 |
| Supplier 3 | H | H | L | H | L | 0.037 | 1.65 | 69 | 8 | 96 |
| Supplier 4 | H | H | L | L | H | 0.037 | 1.50 | 97 | 36 | 38 |
| Supplier 5 | H | L | H | H | L | 0.043 | 1.70 | 21 | 94 | 58 |
| Supplier 6 | H | L | H | L | H | 0.037 | 1.57 | 18 | 60 | 4 |
| Supplier 7 | H | L | L | H | L | 0.045 | 1.74 | 17 | 0 | 93 |
| Supplier 8 | H | L | L | L | H | 0.046 | 1.79 | 0 | 20 | 50 |
| Supplier 9 | L | H | H | H | L | Ideal case | ||||
| Supplier 10 | L | H | H | L | H | 0.021 | 1.18 | 89 | 65 | 39 |
| Supplier 11 | L | H | L | H | L | 0.032 | 1.13 | 83 | 46 | 84 |
| Supplier 12 | L | H | L | L | H | 0.030 | 1.13 | 94 | 47 | 25 |
| Supplier 13 | L | L | H | H | L | 0.034 | 1.27 | 40 | 96 | 55 |
| Supplier 14 | L | L | H | L | H | 0.033 | 1.28 | 40 | 61 | 17 |
| Supplier 15 | L | L | L | H | L | 0.021 | 1.23 | 23 | 43 | 59 |
| Security levels | Shipping rate | Security values | |||||
|---|---|---|---|---|---|---|---|
| Price | Theme 1 | Theme 2 | Variable | Fixed | Risk and response | Relationships | |
| Carrier 1 | H | H | H | 0.000017 | 0.15 | 84 | 100 |
| Carrier 2 | H | H | H | 0.000021 | 0.16 | 57 | 100 |
| Carrier 3 | H | H | L | 0.000021 | 0.14 | 73 | 0 |
| Carrier 4 | H | H | L | 0.000017 | 0.15 | 53 | 0 |
| Carrier 5 | H | L | H | 0.000016 | 0.14 | 26 | 100 |
| Carrier 6 | H | L | H | 0.000019 | 0.14 | 4 | 100 |
| Carrier 7 | H | L | L | 0.000018 | 0.15 | 11 | 0 |
| Carrier 8 | H | L | L | 0.000021 | 0.15 | 0 | 0 |
| Carrier 9 | L | H | H | Ideal case | |||
| Carrier 10 | L | H | H | 0.000014 | 0.11 | 70 | 100 |
| Carrier 11 | L | H | L | 0.000013 | 0.13 | 63 | 0 |
| Carrier 12 | L | H | L | 0.000014 | 0.12 | 69 | 0 |
| Carrier 13 | L | L | H | 0.000013 | 0.12 | 7 | 100 |
| Carrier 14 | L | L | H | 0.000014 | 0.11 | 32 | 100 |
| Carrier 15 | L | L | L | 0.000014 | 0.11 | 47 | 0 |
6.2 Applying the security rules
In this set of steps, we illustrate the nature of collaboration in this example by building scenarios with two sets of optimization runs: one scenario that reflects independent decisions for carrier and supplier choice, followed by a scenario where carrier and supplier selection decisions are made jointly and with the benefit of shared supplier and carrier security information. The same set of suppliers and carriers from the POOL were run under these two sets of rules.
In the first (individual) scenario, suppliers and carriers are qualified to be candidates based on their individual security scores and the thresholds set by the RULES described earlier for individual organizations. Suppliers are rated on relationships, existing processes, and incident management, and then an overall score is compared to a threshold level. Carriers are similarly rated and compared based on risk/response and relationships.
For the second (collaborative) scenario, the RULES are changed to value the enhanced security provided by collaboration, i.e. the security requirements may be reduced below the threshold value if the other member of the supplier–carrier pair is highly trusted. The supplier and carriers that qualify based on security scores enhanced by the collaboration-based rules join those that qualify individually. Similarly, if a particular supplier and carrier combination represents a security risk even though their individual performances with respect to security are evaluated as favorable, the combination may be prohibited. In this way, the security RULES described earlier are applied to the candidates in the POOL and those that satisfy the security thresholds will feed into the optimization procedure (OPT). A previous passage through the PS module eliminates incongruent cases that will generate obvious solutions like when choosing from a set of one supplier and one carrier.
6.3 The optimization process
A key component of this decision structure is the multi-objective optimization model (OPT), which allows managers to generate alternative solutions to the carrier–supplier selection problem, and then evaluate them based on cost, security, and quality/delivery. This module is implemented for this example using LINGO v11.0, while the supplier and carrier security screening described in the previous section is performed for this illustration via Excel.
The optimization model that is described in an earlier section executes for a specific set of weights, for the individual scenario and again for the collaborative scenario. Managers using a decision support tool such as this one do well to exercise the model in an interactive fashion. Multi-objective formulations are especially well suited to interactive approaches because they provide a set of non-inferior solutions (the efficient frontier) where managers can ask and answer “what if” questions and select the solution that best suits their individual situation.
Accordingly, the choice of these weights is important when selecting suppliers and carriers in this decision process. The decision process provides for these alternative weighting schemes in the ReRun (RR) step in Fig. 1, where instances are generated by varying the weights of the objectives.
As such, it is especially important to try a reasonable set of alternative weighting schemes, as the solutions to the optimization problem are sensitive to the weights chosen for each of the objective functions (cost, security, and quality/delivery). Yet managers may not be confident in the weights they choose for a multi-objective model; similarly, they may not be familiar with schemes for selecting weights for generating meaningful alternative solutions that are not inferior to the others already created. It is not useful when considering cost, quality, delivery, and security tradeoffs to compare an efficient solution to an inferior solution.
We recommend, then, the use of the efficient frontier concept to facilitate the generation of useful instances by systematically varying weights based on a procedure described in Cohon (1978). Cohon's method provides a clever way to generate non-inferior (NI) solutions that formulate the efficient frontier, which serves as alternatives to aid in the evaluation of tradeoffs among cost, security, and quality/delivery in this decision process. In this illustration, we use Cohon's procedure to generate 27 instances for each of the scenarios. These instances, which are collected in STORAGE as the procedure iterates, then allow for a comparison of performance on the optimization criteria under the different weighting schemes – first for individual decision-making scenario, and then for collaborative decision-making scenario. After the 27 instances are run in the ReRun (RR) step, the manager would end the looping as all useful instances would have been generated (STOP).
6.4 Simulation results and discussion
In our simulation, we generate 27 instances for each scenario, and then eliminate solutions that are repeated or inferior in both scenarios. This leaves eleven instances, which are listed in Table 5. In order to make a meaningful comparison we chose instances with the same set of weights in both scenarios even if it includes some repeated solutions. Nine of the 11 instances in the individual scenario are unique solutions (instances number 1–6-8-9-12). Eight of these nine unique solutions are NI, with instance three as an inferior solution. Of the eight unique solutions in the collaborative scenario (instances 1–4-8-9-12-24), seven are NI, with instance 2 as an inferior solution.
| Instance number | 1 | 2 | 3 | 4 | 5 | 6 | 8 | 9 | 12 | 24 | 27 |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Weights: Ω1–Ω2–Ω3 (cost–security–quality) | 1–0–0 | 0–1–0 | 0–0–1 | 1–0–1 | 1–0–2 | 1–0–3 | 1–1–0 | 1–1–1 | 1–1–4 | 1–4–1 | 1–4–4 |
| Individual | |||||||||||
| Total cost | 100 | 110 | 138 | 123 | 129 | 136 | 103 | 117 | 120 | 117 | 117 |
| Security gap | 752 | 690 | 1022 | 1002 | 920 | 1022 | 690 | 714 | 756 | 714 | 713 |
| Late and rejected items | 514 | 512 | 277 | 283 | 279 | 277 | 516 | 313 | 302 | 313 | 313 |
| Collaborative | |||||||||||
| Total cost | 85 | 117 | 134 | 119 | 119 | 134 | 116 | 114 | 118 | 117 | 114 |
| Security gap | 922 | 619 | 928 | 917 | 917 | 928 | 619 | 678 | 720 | 619 | 677 |
| Late and rejected items | 588 | 415 | 216 | 222 | 222 | 216 | 414 | 243 | 232 | 413 | 243 |
This experimental setting of two scenarios each with a multi-objective formulation allows for the analysis of the tradeoffs among cost, security, quality, and delivery in each of the scenarios, individual and collaborative. In this analysis it can be noted that as weights for any of the objectives increase within the individual or within the collaborative instances (i.e. across the table), the model responds as expected. But this experiment also allows for comparison between equally weighted solutions in the two scenarios. It can be seen that in nine out of the 11 instances, the collaborative scenario provides better answers than the individual scenario. The inconsistent performance observed in instances 8 and 24 is likely attributable to the heuristic branching choices of the optimization procedure. Note also that in instances 3–6 the collaborative scenario improves the security gap over the individual scenario even when the security objective is not weighted.
From a practical point of view, the results of the efficient frontier analysis can be useful to a manager. He/she can choose and compare solutions from the non-inferior list, and based on the choice, may then determine the appropriate quantity for a supplier–carrier pair associated with the solution. For example, let us say that the manager chooses and compares the results of the individual runs for instances number 1, 8, and 9, listed in Table 5. Instance 1 provides the lower cost alternative (100) while instance 8 reduces the security gap by 8% while increasing cost by 3% and keeping the level of late and rejected items virtually unchanged. Instance 9 relative to instance 1 shows the security gap reduced by 5% and the number of rejected items reduced by 39%, with a 17% cost increase. The final choice will depend of each manager's scheme of priorities and once it is made there will be a set of supplier–carrier–quantity associated with it. For example, if instance 9 is chosen, carrier 1 will be used to ship 444 units from supplier 1, 416 units from supplier 3, and 141 units from supplier 11; meanwhile carrier 5 will bring the rest of the demand from suppliers 10 (260), 11 (186), 17 (352), and 25 (203).
Importantly, these results demonstrate that security measures can be scaled and represented as qualitative information in a mathematical program, which allows for explicit trade-offs of objectives, given a set of suppliers and carriers that meet the minimum threshold values. We also show that security considerations can be factored into a multi-objective mathematical program that also considers cost, delivery, and quality.
This illustration demonstrates the use of the security rules which removes suppliers and carriers from further consideration if they fail to meet the minimum required performance, in both the individual and collaborative cases. Importantly, carrier and supplier selection in the collaborative case also allows for combinations that are mutually supportive that would have otherwise been rejected.
Furthermore, this illustration provides a numerical confirmation for the intuitively appealing conclusion that collaboration between logistics managers and purchasing managers and among buyers, suppliers, and carriers in a supply chain, can result in improved supply chain security performance. Additionally, there is collaboration between firms in this process, as both carriers and suppliers share security information about security rankings.
7 Conclusions and future research
Supply chain security is a major concern for logistics managers who have responsibility for inbound and outbound shipments to and from both domestic and international locations. We propose here that logistics decisions concerning security in the supply chain will be made more effectively when made in concert with decisions in related supply chain processes.
Specifically, we argue that decisions concerning transportation choice and supplier selection may be integrated to improve security. We develop a decision process and illustration to demonstrate the usefulness of these concepts in practice. We also address how a firm may then introduce ordinal data into a mathematical program in a security context, and integrate the construct into a decision model that addresses both supplier and carrier selection.
Collaborative decision-making aids in improving performance in this case by allowing for modified rules when different functional areas in a firm collaborate to select carriers and suppliers jointly. Poor security combinations continue to be ruled out as they would be with individual decision making, but a strong supplier or carrier can be enlisted to compensate for a weakness of its supply chain ally.
This research contributes to the literature with the development of a decision process that incorporates security scales in a quantitative and rigorous way. We expand a traditional multi-objective supplier selection model to include carrier selection, and at the same time allow for trade-offs involving cost, security, quality, and delivery.
Future research could include investigation into modeling issues, such as including the cost of collaboration in the fixed cost of adopting a specific supplier or carrier, and perhaps addressing quantity discounts for purchase quantity. Also, the analysis could be extended to include additional trade-offs, such as between quality and delivery. Other investigation may address the conditions and potential resolution for collaboration that results in uneven improvements among departments, as well as with suppliers and carriers. Finally, additional research could investigate the value of collaboration in different business contexts, such as transportation cost in comparison to purchase price.




