Quantum approximate optimization of the coset leader problem for binary linear codes
Funding information: Gobierno del Principado de Asturias, FC-GRUPIN-IDI/2018/000193; FC-GRUPIN-IDI/2018/000226; Ministerio de Ciencia e Innovación, RTI2018-098085-B-C44; PID2020-119082RB-C22; Ministerio de Economía y Competitividad, MINECO-16-TEC2015-67387-C4-3-R; MTM-2017-83506-C2-2-P
Abstract
The security of a broad family of coding-based cryptographic techniques relies on the hardness of the Syndrome Decoding Problem (SDP). In this problem, the aim is to find a word with a given syndrome and of Hamming weight smaller than a prefixed bound. If this last condition is replaced by “of minimum weight,” then we have the Coset Leader Problem (CLP), being Finding Low Weight Codewords (FLWC) a particular case (when the zero syndrome is considered). An algorithm that has been proposed in order to obtain approximate solutions of problems of these kind (NP-complete) is the Quantum Approximate Optimization Algorithm (QAOA), a variational hybrid quantum-classical algorithm. In this paper, we apply the QAOA to the CLP for binary linear codes. We model the problem, make the theoretical analysis the case of the first level, and introduce some experiments to test its performance. The experiments have been carried out on quantum computer simulators with codes of different lengths and QAOA of different depth.
1 INTRODUCTION
The security of a broad family of coding based cryptographic techniques relies on the hardness of the Syndrome Decoding Problem (SDP). In this problem, given natural numbers , and w such that , and a parity-check matrix of a binary linear code , and a syndrome vector , the aim is to find a word with syndrome , of Hamming weight smaller than w.1 In cryptography, for instance, the interest is on random binary linear codes of code rate , and w slightly higher than the Gilbert–Varshamov bound.2 Other case of interest is when the code is a binary Goppa code of coding rate , and the weight bound is taken as , as the Classic McEliece cryptosystem, as submitted to the NIST Post-Quantum Cryptography standardization process relies on Reference 3.
When the condition of the SDP is replaced by “e of minimum weight,” then we have the Coset Leader Problem (CLP), that is, finding a word of minimum weight among those having the same syndrome s. A particular case of this problem is Finding Low Weight Codewords (FLWC), when the zero syndrome is considered. The decision version of these problems is known to be NP-complete,4 hence their importance from the cryptographic point of view. Also, the problem remains difficult when the binary code is randomly chosen and w is taken close to the Gilbert–Varshamov bound.5 Other concrete instances such as the ones mentioned above based on binary Goppa codes, are apparently hard too.
Because of this computational hardness, Quantum Computers (QC) are not believed to be able to solve these problems in polynomial time.6 However, it might occur that the solution to some instances of these problems could be approximated by a quantum computation technique. One of the proposals in this direction is the Quantum Approximate Optimization Algorithm (QAOA), a variational hybrid quantum-classical algorithm introduced in 2014.7 Originally applied to one particular NP-complete problem (MaxCut), this algorithm combines the power of classical minimization of certain parameters and the power of discrete time evolution of QC based on such parameters. Because of its apparent quantum error robustness, it has become a promising candidate to use in the NISQ (Noisy Intermediate-Scale Quantum) era, that is, with a-few-hundred-qubit quantum-error-nonfree QC.
In this paper, we apply the QAOA to the CLP for binary linear codes. This is not the first time that QAOA has been considered in the context of coding theory. In Reference 8, a maximum likelihood channel decoding methodology based on QAOA was proposed. In our paper, we follow some of the ideas introduced there but taking into account the hamming weight of the solutions. This yields to a framework in which a new Hamiltonian models the problem, in the sense that finding minimizing states corresponds to solutions of the posed instance. This is accomplished in the second section of the paper, which also contains background on the QAOA algorithm. Next, we introduce some experiments to test the performance of the QAOA methodology, not only of the first level, but also of levels –5. For the experiments we have selected the smallest instances of the SDP for random binary linear codes and for the Goppa–McEliece setting contained in the site https://decodingchallenge.org, a webpage devoted to assess the practical hardness of problems in coding theory. Conclusions and future work are given in the final section of the paper.
2 QAOA FOR CLP
Adiabatic quantum computation is a polynomially equivalent model to the standard gate model of quantum computation9, 10 that has been applied to solving -complete problems.11 Its theoretical foundation is the Quantum Adiabatic Theorem12 that states, roughly speaking, that if a quantum system is prepared in the ground state of an initial Hamiltonian , and that if the system is driven by a sequence of slightly changing Hamiltonians of the form then, if T is sufficiently large, the final state will be also in the ground state of the final Hamiltonian .13 In order to solve an complete problem, a final Hamiltonian is introduced, so that its ground states encode its solutions. These solutions are achieved from the evolution of an easy-to-prepare ground state of an initial Hamiltonian, according to the time-dependent Hamiltonian mentioned above.
Proposition 1.Let n and k be natural numbers with , let be a parity-check matrix of a binary linear code, and let be a syndrome vector (). Let us define , for all . If , and e is any vector such that , then , for all such that . On the other hand, if , then there exists a parity-check matrix , a syndrome , and two vectors such that , , but .
Proof.For the first part we have since makes , and gives .
On the other hand, if , then take , . Then, .
Next, we introduce the Hamiltonian related to the cost function C, in the sense that any ground state of corresponds to a vector minimizing the function C. The weight function can be written as , that can be translated into the addition , where is the Z Pauli operator on the th qubit. Observe that , and so minimizing the weight function corresponds to finding ground states of such a Hamiltonian. On the other hand, following Reference 8, the Hamming distance , which can be written as , can be modeled as .
Definition 1.Let n and k be natural numbers with , let be a parity-check matrix of a binary linear code, and let be a syndrome vector (). Let us define the matrix , the cost coefficients , and the indices of cardinality , for all . We define the cost Hamiltonian
Example 1.Consider the parity-check matrix of a repetition binary code of length 3, with parity-check matrix . Then, corresponding to a syndrome , we have .
Remark that the previous Hamiltonian corresponds to an Ising model. In general, is an Ising Hamiltonian if and only if , for all . Observe also that different parity-check matrices of the same code yield different cost Hamiltonians, and that these may correspond or not to Ising models, since different values of may occur.
Example 2.Consider the linear code obtained by the instance generator of Reference 2, with length , and seed equal to 3822. It is a code of dimension , minimum distance 1 with parity-check matrix
3 EXPERIMENTAL RESULTS ON QAOA FOR CLP
In this section, we present some experimental results concerning the application of the QAOA methodology to several codes. All of them were taken from the webpage2 (Table 1). The codes were generated as random instances of the SDP with lengths , where as the codes are Goppa codes of length related to the Classic McEliece cryptosystem.
| Code | Parameters | s | w | Generation | |
|---|---|---|---|---|---|
| 4 | seed 3822 | 2 | |||
| 4 | seed 3822 | 2 | |||
| 4 | seed 1020938 | 2 | |||
| 5 | seed 18768 | 4 | |||
| 1 | Inria Paris | 9 | |||
| 1 | Univ. de Rennes 1 | 11 | |||
| 1 | Univ. de Limoges | 11 |
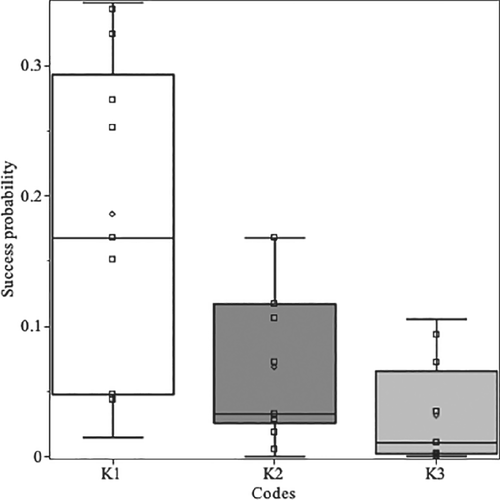
Experiments have been programmed in ProjectQ,15 and carried out on a simulator, using exact energy estimation (through the wavefunction) and classical optimizer L-BFGS-B.16 In a first experiment, we have run 100 instances of level-1 QAOA for codes , computing the exact success probability of finding a vector e with prescribed syndrome, and Hamming weight upper bounded by w, that is, of solving the SDP. Table 2 shows the average, maximum, minimum, and SD of such probabilities. Also, a boxplot based on the experiments carried out for codes (level-1 QAOA) can be found on Figure 1.
| Code | s | w | Average | Max | Min | SD |
|---|---|---|---|---|---|---|
| 4 | 0.186 | 0.349 | 0.015 | 0.120 | ||
| 4 | 0.068 | 0.168 | 0 | 0.060 | ||
| 4 | 0.031 | 0.106 | 0 | 0.035 |
We have used the outcome data to establish accumulated probabilities of success, based both on the average value, and also on the concrete probabilities of the experiments to , to simulate an increasing number () of independent experiments. Figure 2 contains the results. As we can see, the success probability decreases with the length n of the code (the rest of the parameters is the same: , , ). This is somehow expected, since the number of qubits required by the QAOA is exactly such a length.
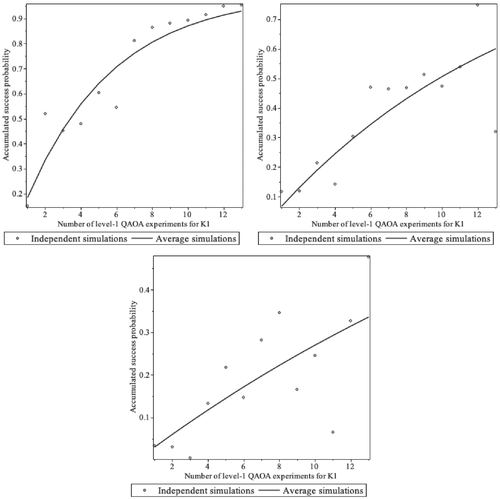
The same experiment was run with 10 instances of level-1 QAOA for codes . Table 3 shows the average, maximum, minimum, and SD of the accumulated success probabilities, whereas Figure 3 shows the accumulated success probability based on the average probability obtained in the simulations. Again, we can observe the tendency to obtain smaller success probability with random codes of higher length (here , for ). On the other hand, it has to be noticed that two out of the three Goppa codes () have significantly higher success probabilities than the random code (). This might suggest that these two codes have an inner structure that favors the QAOA. It might be possible that the higher dimension of the Goppa codes have also an effect in the algorithm. However, the success probability of the third Goppa code () apparently goes against this conclusion.
| Code | s | w | Average | Max | Min | SD |
|---|---|---|---|---|---|---|
| 5 | 1.513 | 5.052 | 0 | 1.972 | ||
| 1 | 24.767 | 84.115 | 0.002 | 37.818 | ||
| 1 | 124.551 | 351.927 | 0 | 128.060 | ||
| 1 | 543.092 | 2713.267 | 0.025 | 1085.087 |
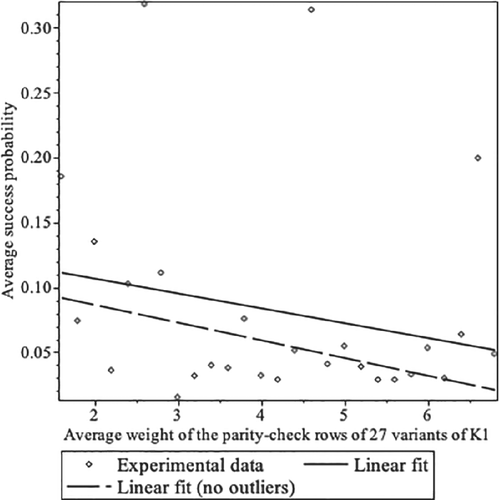
A third experiment was run with the 27 variants of code introduced above. In all cases, 100 level-1 QAOA simulations where carried out. The average, maximum, minimum, and SD of the success probabilities are collected in Table 4. Figure 4 shows how the success probability changes when increasing the average number of ones per row of the parity-check matrix H. The data show a certain tendency toward higher success probabilities among those variants with smaller number of ones. This might suggest the cryptographic use of codes presented through parity-check matrices with as many ones as possible.
| Variant | s | Average | Max | Min | SD | |
|---|---|---|---|---|---|---|
| 1 | 0.186 | 0.349 | 0.016 | 0.112 | ||
| 2 | (00001) | 0.074 | 0.242 | 0 | 0.087 | |
| 3 | (10001) | 2 | 0.135 | 0.244 | 0.027 | 0.063 |
| 4 | (00001) | 0.036 | 0.219 | 0 | 0.057 | |
| 5 | (00001) | 0.103 | 0.246 | 0.007 | 0.080 | |
| 6 | (00001) | 0.318 | 0.958 | 0.008 | 0.333 | |
| 7 | (10001) | 0.111 | 0.216 | 0.007 | 0.066 | |
| 8 | (11001) | 3 | 0.015 | 0.094 | 0 | 0.018 |
| 9 | (11001) | 0.032 | 0.192 | 0 | 0.038 | |
| 10 | (01001) | 0.040 | 0.168 | 0 | 0.045 | |
| 11 | (11001) | 0.038 | 0.179 | 0 | 0.049 | |
| 12 | (10001) | 0.076 | 0.215 | 0.010 | 0.070 | |
| 13 | (11001) | 4 | 0.032 | 0.164 | 0 | 0.050 |
| 14 | (11001) | 0.029 | 0.149 | 0 | 0.033 | |
| 15 | (01001) | 0.051 | 0.164 | 0.007 | 0.049 | |
| 16 | (11001) | 0.314 | 0.960 | 0.004 | 0.365 | |
| 17 | (11101) | 0.041 | 0.142 | 0 | 0.044 | |
| 18 | (11101) | 5 | 0.055 | 0.133 | 0 | 0.044 |
| 19 | (11101) | 0.039 | 0.129 | 0.001 | 0.038 | |
| 20 | (11111) | 0.029 | 0.151 | 0 | 0.033 | |
| 21 | (11111) | 0.029 | 0.138 | 0.001 | 0.028 | |
| 22 | (10100) | 0.033 | 0.131 | 0.005 | 0.024 | |
| 23 | (10110) | 6 | 0.053 | 0.125 | 0.003 | 0.033 |
| 24 | (01110) | 0.030 | 0.101 | 0 | 0.0202 | |
| 25 | (11100) | 0.064 | 0.125 | 0.024 | 0.030 | |
| 26 | (01110) | 0.200 | 0.961 | 0.008 | 0.317 | |
| 27 | (01111) | 0.049 | 0.153 | 0.002 | 0.036 |
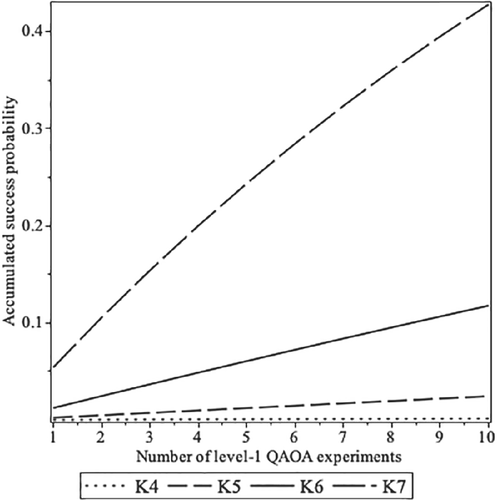
We have tested higher level QAOA for the codes (10 independent experiments each). The average, maximum, minimum, and SD of the success probabilities are collected in Tables 5–7. Figure 5 shows the success probability change when the level p is increased from 1 to 5. As expected, the higher the depth, the better results that the QAOA yields. Since the Hamiltonian cost of those codes is an Ising model (), we have tested 5000 experiments in the DWave Quantum Annealer.17 The same figure plots the average success probability of these experiments. It should be noticed that the QAOA is a remarkable alternative to the adiabatic computation performed by the quantum annealer (at least for the codes studied, with lengths ).
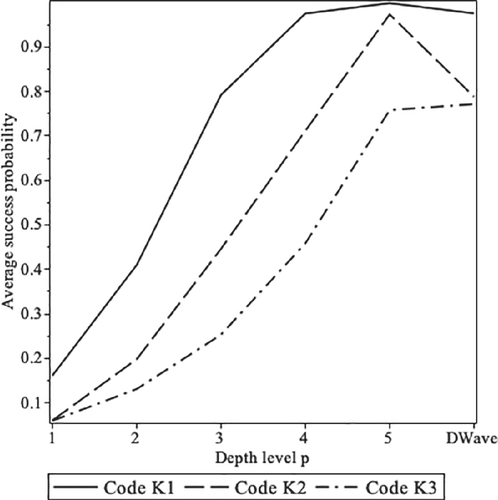
| p | Average | Maximum | Minimum | SD |
|---|---|---|---|---|
| 1 | 0.161 | 0.349 | 0.015 | 0.137 |
| 2 | 0.410 | 0.560 | 0.310 | 0.075 |
| 3 | 0.793 | 0.959 | 0.573 | 0.105 |
| 4 | 0.976 | 0.999 | 0.925 | 0.025 |
| 5 | 0.999 | 0.999 | 0.995 | 0.001 |
| p | Average | Maximum | Minimum | SD |
|---|---|---|---|---|
| 1 | 0.060 | 0.168 | 0 | 0.062 |
| 2 | 0.198 | 0.470 | 0.037 | 0.103 |
| 3 | 0.446 | 0.871 | 0.0560 | 0.255 |
| 4 | 0.712 | 0.970 | 0.173 | 0.225 |
| 5 | 0.974 | 1 | 0.932 | 0.025 |
| p | Average | Maximum | Minimum | SD |
|---|---|---|---|---|
| 1 | 0.059 | 0.094 | 0.002 | 0.038 |
| 2 | 0.131 | 0.441 | 0.001 | 0.123 |
| 3 | 0.253 | 0.776 | 0.001 | 0.200 |
| 4 | 0.459 | 0.683 | 0.222 | 0.160 |
| 5 | 0.759 | 0.999 | 0.337 | 0.188 |
4 CONCLUSIONS AND FUTURE WORK
In this paper, we have applied the QAOA to an -complete problem from Coding Theory upon which relies the security of several postquantum cryptographic schemes. We have modeled the problem in suitable terms to apply the hybrid classical-quantum algorithm and we have experimentally checked its correctness. We have made some experiments from codes obtained from the site.2 Among them, the (accumulated) success probabilities for seven different codes (including 3 binary Goppa codes), for 27 variants of the same random code for QAOA of depth level 1. We have also experimented with higher level QAOA (–5) for the same code. The experiments suggests that random codes with a higher length, and presented by parity-check matrices of high density, are more resistant to the QAOA algorithm, at least for small depths and on simulations. Unfortunately, because of the current state of quantum technology, we have been able to test any Quasi-Cyclic code of those contained in.2 Experimenting with codes of higher length, or the modification of the Hamiltonian to cope with the challenge of the Large weight syndrome decoding problem2 is future work.
ACKNOWLEDGMENTS
This work was supported in part by the MINECO under Grant MTM-2017-83506-C2-2-P and Grant MINECO-16-TEC2015-67387-C4-3-R, and in part by the MICINN under Grant RTI2018-098085-B-C44, Grant FC-GRUPIN-IDI/2018/000193, and under Grant FC-GRUPIN-IDI/2018/000226.
Biographies

Markel Epelde received the B.S. and M.S. degrees in mathematics from the University of the Basque Country, Spain, in 2015, and 2016, respectively. Currently, he is a Ph.D. student in the University of the Basque Country.

Elías F. Combarro received the B.S. degree in mathematics, the M.S. degree in computer science, and the Ph.D. degree in mathematics from the University of Oviedo, Oviedo, Spain, in 1997, 2001, and 2002, respectively, where he is currently an Associate Professor. He has authored more than 30 research papers in topics such as computability theory, the theory of fuzzy measures, and the computational classification of semifields and text categorization. His current research interest includes quantum computing.

Ignacio F. Rúa received the B.S., M.S., and Ph.D. degrees in mathematics from the University of Oviedo, Oviedo, Spain, in 1999, 2001, and 2004, respectively, where he is currently an Associate Professor. From 2004 to 2007, he was a Research Fellow of the Spanish Juan de la Cierva Program with the Universidad de Cantabria. He has coauthored 30 research papers on nonassociative finite rings and their applications in coding theory and cryptography. His current research interests include computer algebra and quantum computing.




