Damage Identification in Bridge Structures Based on a Novel Whale-Sand Cat Swarm Optimization Algorithm and an Improved Objective Function
Abstract
Structural damage identification (SDI) serves as an indirect approach that has the potential to meet real-time monitoring of structures. However, the identification accuracy and efficiency of some methods need to be improved, especially when there are some uncertain interfering factors or noise. This paper presents a new optimization algorithm and an improved objective function for inverse problems of SDI, offering an effective solution for bridge damage identification under uncertain noise interference and incomplete modal data. In this study, by hybridizing the whale optimization algorithm and the sand cat swarm optimization, a novel whale-sand cat swarm optimization (W-SCSO) method is proposed for SDI. The cubic chaotic mapping is introduced for initialization of the W-SCSO method, and then the lens opposition-based learning and the stochastic differential mutation are employed to enhance the search capability and convergence accuracy of the proposed algorithm. Besides, the mode shape curvature, the frequency change ratio, and the L1/2 sparse regularization are used to improve the objective function. Four other existing state-of-the-art methods are used to verify the performance of the proposed W-SCSO method by the CEC2017 benchmark functions and a simply supported beam finite model. The comparative analysis highlights the feasibility and effectiveness of the proposed method in the considered cases. Moreover, an aluminum alloy simply supported beam was conducted for the SDI experiment to further prove the effectiveness of the improved method in practice. Simulation and experimental results show that the proposed method effectively locates and quantifies stiffness reduction in bridge structures, which maintains high accuracy in damage identification despite potential modal incompleteness and uncertain measurement noise interference.
1. Introduction
Bridge structures are easy to be damaged owing to excessive loading, temperature changes, reinforcement corrosion, vehicle impacts, etc. The occurrence of sudden and high-risk structural failures can be avoided if the damage is detected and addressed in a timely manner. Hence, structural health monitoring systems play a crucial role in ensuring the safety and durability requirements throughout the entire service life of structures [1–3].
Structural damage identification (SDI) methods can be divided into two categories: nondestructive testing methods and vibration-based methods [2]. The majority of nondestructive testing methods are used for localized identification, which are more sensitive to localized damage but cannot easily detect the damage located within structures [4–6]. Vibration-based methods are capable of examining changes in the overall vibration characteristics of a structure and are considered to be global identification methods, which contain both static and dynamic methods [7, 8]. Static methods commonly utilize static displacement or strain changes for structural condition assessment [9, 10]. Dynamic methods include modal parameter-based methods [11], Bayesian methods [12], and finite element (FE) model updating methods [13]. Modal parameters, including natural frequencies and mode shapes, have proven effective for damage identification [14–16]. However, complete modal information needs to be acquired to ensure the accuracy of modal parameter-based methods, which are susceptible to environmental factors and difficult to realize in practical engineering structures [17]. Modal parameters are nonlinear functions of the damage index, which presents challenges in the computational processes of Bayesian methods [18].
FE model updating methods can quantitatively identify the location and degree of damage by establishing an accurate calculation model. With FE model updating methods, the SDI process can be transformed into solving the minimum value of an objective function, which can evaluate the difference between the measured and calculated dynamic responses. The objective function can be composed of different modal parameters, such as modal assurance criterion (MAC), frequency change ratio (FCR), and mode shape curvature (MSC) [19, 20]. However, the objective function typically exhibits ill-posedness when formulated based on the alteration of vibration properties with incomplete modal data [21]. There are often two strategies to overcome this specific challenge. The first strategy is introducing the proper approach to circumvent the issues of ill-posedness and uncertainty within the function [22]. Sparse regularization approaches can convert the ill-posed function to be well-posed, and sparsity can be used as a priori information in favor of practical damage identification [23–25]. Another strategy is developing more efficient calculation methods to optimize the objective function, such as swarm intelligence optimization algorithms [26]. These algorithms are not only independent of gradient estimation and specific formulas but they also demonstrate a remarkable effect on solving inverse issues with ill-posedness. Minh et al. [27] proposed a new K-means Optimizer and applied the method to SDI in a complex 3D concrete structure. Zhang et al. [28] proposed a hybrid algorithm based on Jaya and a differential evolution algorithm for SDI. Ding, Li, and Hao [29] put forward a new objective function for SDI and employed an improved Jaya algorithm for model updating and optimization analysis. Chen et al. [30] developed a novel hybrid whale-chimp optimization algorithm for SDI based on the whale optimization algorithm (WOA) [31] and the chimp optimization algorithm, which could identify single and multiple damages in the presence of noise interference. Huang et al. [32, 33] employed a genetic algorithm and shuffled frog leaping algorithm for damage identification in bridge structures while taking into account environmental uncertainty factors. Although many algorithms have proven successful in SDI, some algorithms have the problem of intricate parameters and convoluted calculations, which are not conducive to their application in engineering. In addition, the FE model updating methods still have some drawbacks, such as high measurement noise and temperature changes that can affect the reliability of the model update [34]. Furthermore, during the practical mode identification process, only a few low-order modes can be acquired via a limited number of sensors. Hence, the issue of structural modal incompleteness needs to be addressed through the application of model expansion or model reduction techniques. Modal expansion broadens the error into whole freedom, while model reduction diminishes the error only for the master degree of freedoms (DOFs) such as the Guyan reduction scheme. Thus, the latter technique is more widely employed than the former [35].
In addition to model-based SDI methods, data-driven approaches, particularly machine learning techniques, have also gained significant attention in SDI [36]. Machine learning techniques can learn complex patterns from datasets without relying on physical models of the structure [37]. For example, convolutional neural network (CNN) [38] and long short-term memory neural network (LSTM) [39] have been proven to be effective in feature extraction for SDI, which significantly enhances the accuracy and reliability of damage identification. Swarm intelligence optimization algorithms can play an important role in deep learning-based SDI methods, which are often used to optimize machine learning models by fine-tuning hyperparameters and improving iteration efficiency [40, 41]. However, machine learning techniques require large datasets for training; otherwise, these techniques are prone to overfitting when the data are limited [42]. Optimization algorithms also need to exhibit strong optimization performance to avoid obtaining local optima in the convergence result.
With the development of optimization techniques, many advanced algorithms demonstrate the potential to efficiently optimize ill-posed objective functions. Thereinto, the sand cat swarm optimization (SCSO) algorithm is a recently developed swarm intelligence algorithm [43]. The optimization algorithm possesses several advantages, including a simple structure, few numbers of parameters, and the ability to adaptively balance the exploration and exploitation phases, which has been applied and enhanced by researchers to address optimization problems [44–46]. However, it still has some disadvantages, such as the tendency to fall into local search stagnation and low convergence accuracy.
To overcome the challenges mentioned above in swarm intelligence algorithms and FE model updating methods, a novel whale-SCSO (W-SCSO) algorithm and an improved objective function have been developed for damage identification in bridge structures. This approach provides an effective solution for SDI, particularly under conditions of uncertain noise interference and incomplete modal data. In Section 2, the definition of structural damage is briefly introduced. Additionally, an improved objective function for SDI is established by MSC, FCR, and L1/2 sparse regularization. In Section 3, several improvements are applied based on the original SCSO algorithm, and the performance of the proposed W-SCSO algorithm is confirmed utilizing CEC2017 benchmark functions. In Section 4, numerical simulations of a simply supported beam are performed using incomplete modal data with Gaussian white noise. In Section 5, an experimental beam was established to validate the proposed SDI method. Finally, the conclusions of this study are briefly summarized in Section 6.
2. Theory of Structural Damage
2.1. Structural Damage Definition
2.2. Improved Objective Function of Damage Identification
3. W-SCSO Algorithm
3.1. SCSO
The SCSO algorithm is inspired by the natural behavior of sand cats [43]. Sand cats are capable of detecting noise below 2 kHz. Exploration and exploitation phases represent the two main actions of sand cats in the algorithm. Sand cats choose whether to attack or search for prey according to the frequency of the emitted sound. Optimal values are regarded as prey within the search space, and the values obtained from the objective function are used to ascertain whether the position of the sand cat should be updated during each iteration.
3.2. Improved Algorithm
3.2.1. Cubic Chaotic Mapping
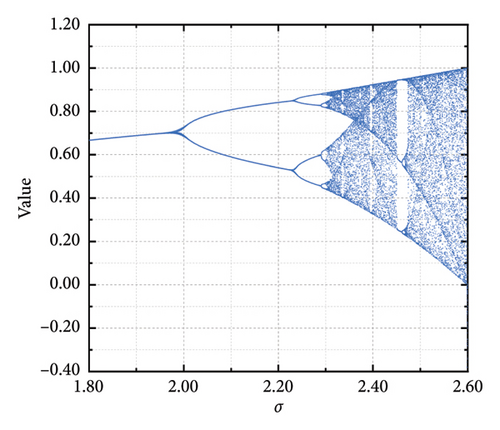
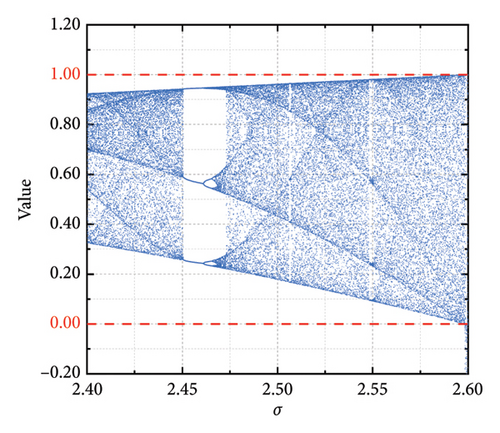
Assuming an initial value of β1 = 0.1, the value of the parameter σ is determined using the bifurcation diagram of the cubic chaotic mapping. Taking σ as the horizontal axis, the parameter space is divided into 1000 segments. For each σ within the range [1.8, 2.6], the value of β is iterated 100 times. By sweeping through the entire parameter range, the bifurcation diagram of the cubic chaotic mapping is obtained, as shown in Figure 1(a). Figure 1(b) presents a local zoomed-in bifurcation diagram for σ within the range [2.4, 2.6]. It can be observed that when σ = 2.59, the generated values lie within the range [0, 1], which aligns with the search space of the SDI problem. Upon testing, it is found that the values yielded by the cubic chaotic mapping in one dimension exhibit good chaotic traversal properties when β1 = 0.1 and σ = 2.59.
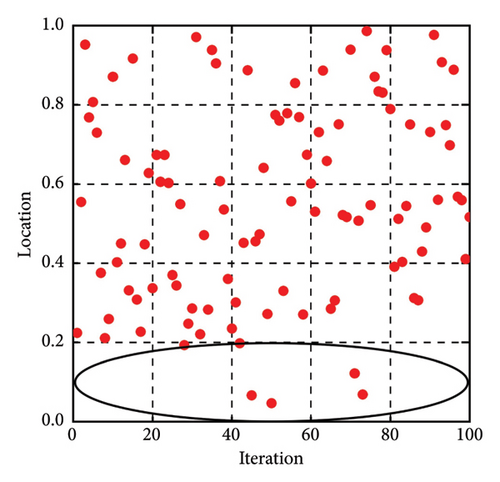
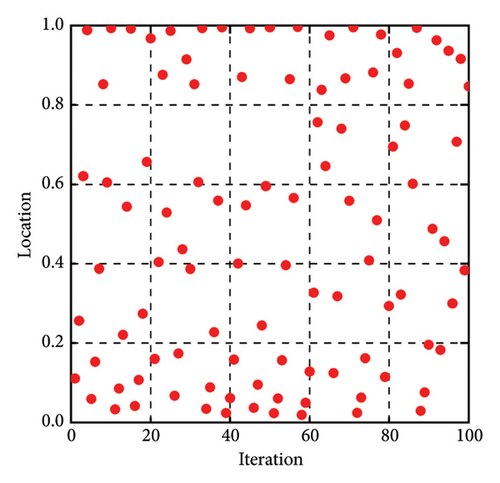
The distributions of the cubic chaotic mapping sequence and pseudo-random sequence are given in Figure 2. The number of iterations for both methods is set as 100, and the search space is between [0, 1]. Compared with the pseudo-random sequence, the cubic chaotic mapping sequence is unevenly distributed and most of the generated values tend to concentrate near the lower bound of the search space. This kind of distribution is more applicable to optimizing the problem of identifying minor damages. The β1 is iterated (n − 1) times in each dimension according to equation (10) to accomplish the initialization in the improved algorithm.
3.2.2. WOA
3.2.3. Lens Opposition-Based Learning
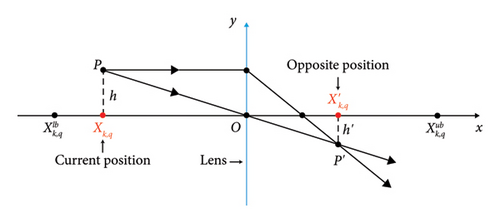
3.2.4. Stochastic Differential Mutation
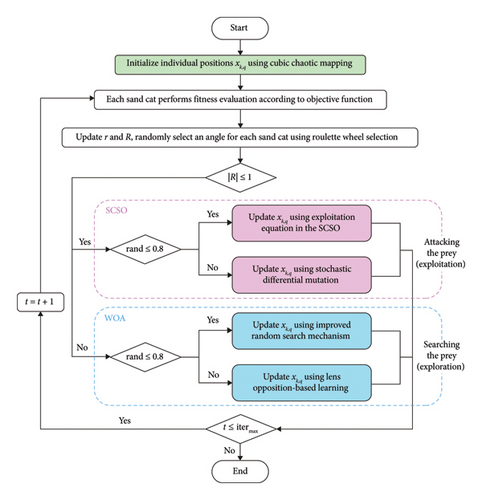
Through these improvements mentioned above, a new algorithm is developed named the W-SCSO algorithm based on the SCSO algorithm. The flowchart of the new algorithm is shown in Figure 4. It is worth noting that the algorithm chooses only one of the methods to update the position of individuals through simple judgments in each iteration. The iterative strategy does not generate much complexity in the calculation.
3.3. Benchmark Function Test
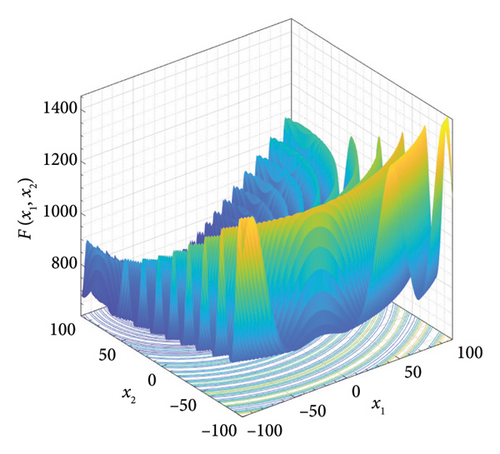
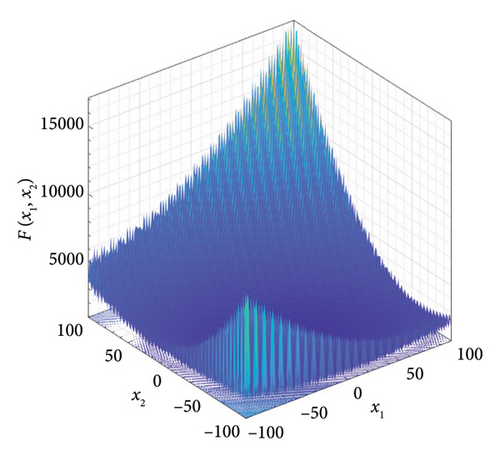
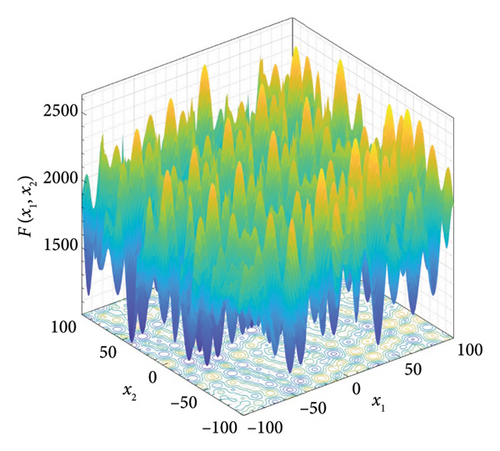
Five multimodal benchmark functions from CEC2017 have been selected for testing the exploration and exploitation ability of the W-SCSO algorithm [54]. The search domain and global minimum value fmin are presented in Table 1.
| F | Benchmark function | Domain | fmin |
|---|---|---|---|
| 1 | Shifted and rotated expanded Scaffer’s F6 function | [−100, 100] | 600 |
| 2 | Shifted and rotated Lunacek Bi_Rastrigin function | 700 | |
| 3 | Shifted and rotated noncontinuous Rastrigin’s function | 800 | |
| 4 | Shifted and rotated Levy function | 900 | |
| 5 | Shifted and rotated Schwefel’s function | 1000 |
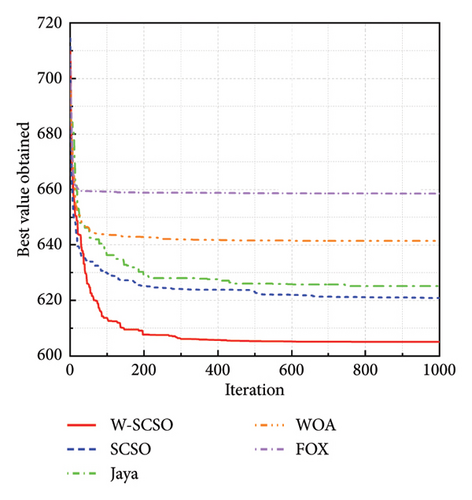
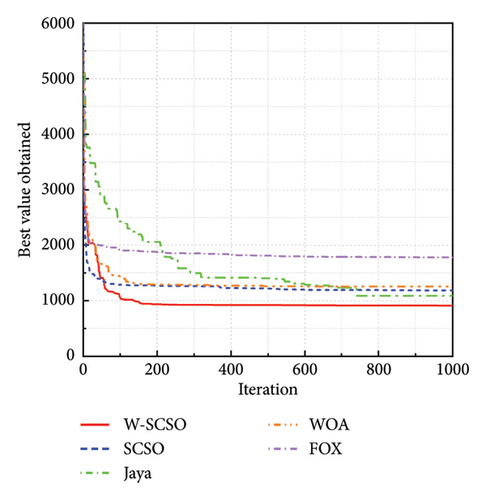
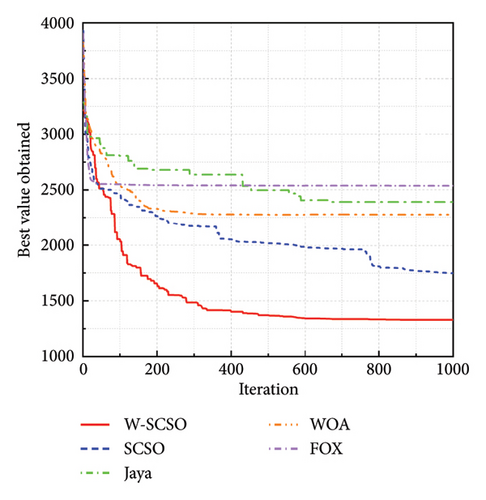
In the study, simulations are performed using MATLAB 2020b software (MathWorks, US) on the Core i7-8700 processor with 32 GB of RAM computer. The proposed algorithm is compared with the SCSO algorithm [43], Jaya algorithm (Jaya) [55], WOA [31], and Fox optimizer (FOX) [56] to show its superior optimization performance. The parameters for each optimization algorithm are shown in Table 2. The number of individuals for all algorithms is set as 30, and the maximum of iterations is set as 500. The dimension of each benchmark function is set to 10, with additional tests conducted for F1, F2, and F3 at a dimension of 30. Both algorithms are calculated 10 times for each benchmark function to acquire the best value, mean, and standard deviation of the results, and the better values between algorithms are highlighted in bold in Table 3. The convergence process of five algorithms for three typical benchmark functions in a 10-dimensional space is shown in Figure 5. According to Table 3 and Figure 5, the best value and mean of the results obtained by the proposed algorithm are lower than those of other algorithms, and the W-SCSO algorithm maintains a low standard deviation, indicating better computational accuracy and stability. Considering that the proposed algorithm maintains good accuracy and stability without significantly increasing computational complexity, it demonstrates higher efficiency compared to other algorithms. The simulation results demonstrate that the new algorithm outperforms the other four algorithms in terms of both convergence efficiency and calculation accuracy.
| Algorithm | Parameter | Value |
|---|---|---|
| W-SCSO | Sensitivity range (rG) | [0, 2] |
| Random angle (θ) | [0, 360] | |
| A′ | [0, 2] | |
| λ | 1.2 | |
| SCSO | Sensitivity range (rG) | [0, 2] |
| Random angle (θ) | [0, 360] | |
| Jaya | Without algorithm-specific control parameters | |
| WOA | a | [0, 2] |
| A | [0, 2] | |
| l | [−1, 1] | |
| C | 2·rand (0, 1) | |
| b | 1 | |
| FOX | c1 | 0.18 |
| c2 | 0.19 | |
| Time_S_Tit | [0, 1] | |
| F | Dimension | Result | W-SCSO | SCSO | Jaya | WOA | FOX |
|---|---|---|---|---|---|---|---|
| 1 | 10 | Best | 602.95 | 609.37 | 620.88 | 625.71 | 651.57 |
| Mean | 605.08 | 620.86 | 625.21 | 641.50 | 658.52 | ||
| Standard deviation | 1.77 | 7.43 | 5.41 | 10.01 | 5.13 | ||
| 30 | Best | 637.46 | 648.25 | 674.18 | 652.96 | 664.09 | |
| Mean | 639.72 | 662.73 | 689.63 | 672.54 | 666.59 | ||
| Standard deviation | 1.32 | 8.72 | 14.78 | 18.74 | 1.68 | ||
| 2 | 10 | Best | 733.37 | 785.68 | 764.44 | 755.31 | 811.27 |
| Mean | 738.29 | 790.61 | 783.16 | 768.48 | 818.79 | ||
| Standard deviation | 4.10 | 3.71 | 11.73 | 8.91 | 8.92 | ||
| 30 | Best | 957.99 | 1170.7 | 1284.9 | 1332 | 1283.1 | |
| Mean | 986.91 | 1259.23 | 1417.08 | 1359.43 | 1311.78 | ||
| Standard deviation | 22.89 | 85.07 | 93.88 | 20.14 | 23.41 | ||
| 3 | 10 | Best | 811.28 | 826.37 | 838.77 | 830.63 | 833.83 |
| Mean | 813.71 | 827.53 | 853.20 | 843.06 | 848.75 | ||
| Standard deviation | 1.94 | 0.73 | 13.32 | 7.74 | 21.95 | ||
| 30 | Best | 941.76 | 964.04 | 1126.10 | 999.59 | 990.04 | |
| Mean | 953.33 | 1002.06 | 1157.20 | 1012.47 | 1010.93 | ||
| Standard deviation | 15.27 | 26.56 | 19.49 | 13.49 | 26.11 | ||
| 4 | 10 | Best | 900.56 | 1008.00 | 1063.20 | 1136.40 | 1742.20 |
| Mean | 913.33 | 1185.73 | 1088.98 | 1256.68 | 1781.65 | ||
| Standard deviation | 20.57 | 200.69 | 32.85 | 123.63 | 34.34 | ||
| 5 | 10 | Best | 1172.10 | 1522.70 | 2301.40 | 1835.60 | 1934.70 |
| Mean | 1328.58 | 1749.03 | 2388.98 | 2275.03 | 2535.98 | ||
| Standard deviation | 96.53 | 210.75 | 54.54 | 363.54 | 443.86 | ||
4. Numerical Simulations
The FE model of a simply supported beam is composed of 15 elements and 14 measured nodes, as shown in Figure 6. The left support of the beam is completely fixed, and the right support is constrained in vertical freedom. Deformation along the axial direction of the beam is neglected in the simulation. Vertical DOFs are measured at the nodes on the beam. Two scenarios with different sensor configurations were considered. When 14 DOFs are measured, sensors are placed at all nodes, while for 7 DOFs, sensors are positioned at nodes 1, 3, 5, 7, 9, 11, and 13. The length and Young’s modulus of the beam are set as 6.00 m and 70 GPa, respectively. The rectangular sectional area, density, and moment of sectional inertia are defined as 3.00 × 10−2 m2, 2750 kg/m3, and 1.10 × 10−5 m4, respectively. Figure 7 illustrates the first-order MSC of the simply supported beam in different damage elements with a 10% degree of damage in a noise-free condition. It can be found that the MSC at the location of the intact element remains smooth, whereas the MSC at the damaged element changes significantly. In order to locate and quantify structural damage effectively, the first five modal data of the structure are selected for both obj 1 and obj 2 in simulations [20]. The W-SCSO algorithm, SCSO algorithm [43], WOA [31], and FOX [56] are applied in simulations. The initial number of individuals for four algorithms is set as 30, and the maximum number of iterations is set as 100. Each damage case is calculated 30 times to avoid singularity results. Subsequently, the result with the lowest fitness value is obtained to determine the effective SDI consequence.

To acquire the optimal performance of the improved objective function, different regularization parameters ϵ are selected for analysis. The triple damage of the simply supported beam is used as a case study, and the W-SCSO algorithm along with obj 1 is employed for computation. Table 4 shows the SDI results with different regularization parameters. The symbol “5@10%” in Table 4 indicates that the stiffness of element “5” has been decreased by “10%.” The symbol “0.15%&5%” represents a noise level of ±0.15% in natural frequencies and ±5% in mode shape data [58]. Results show that when ϵ = 0.001, the SDI result achieves the highest accuracy without any misidentifications compared to other parameters. Therefore, ϵ = 0.001 is used to improve the robustness of both obj 1 and obj 2 in the simulations.
| ϵ | Damage element | Noise level | Identified damage | Misidentification |
|---|---|---|---|---|
| 0 | 5@10%, 8@10%, 13@10% | 0.15%&5% | [email protected]%, [email protected]%, [email protected]% | [email protected]% |
| 0.0001 | [email protected]%, [email protected]%, [email protected]% | [email protected]% | ||
| 0.001 | [email protected]%, [email protected]%, [email protected]% | None | ||
| 0.01 | [email protected]%, [email protected]%, [email protected]% | None | ||
| 0.1 | [email protected]%, [email protected]%, [email protected]% | [email protected]% | ||
| 1 | [email protected]%, [email protected]%, [email protected]% | [email protected]% |
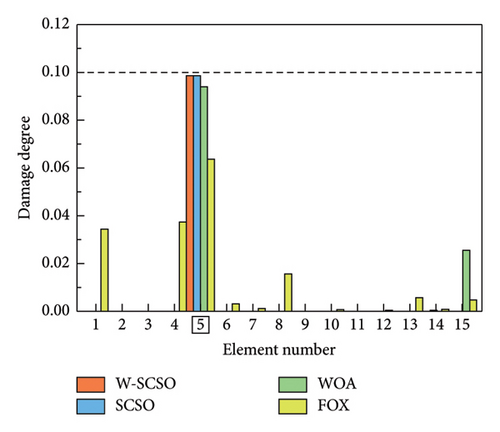
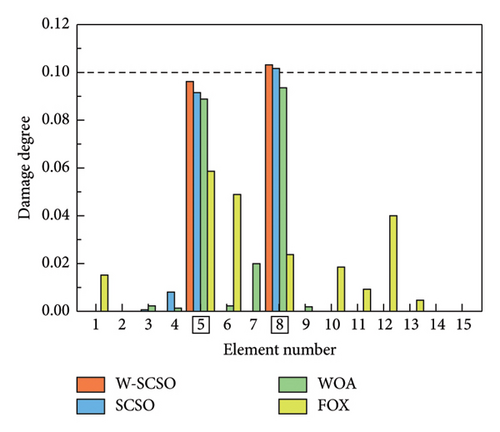
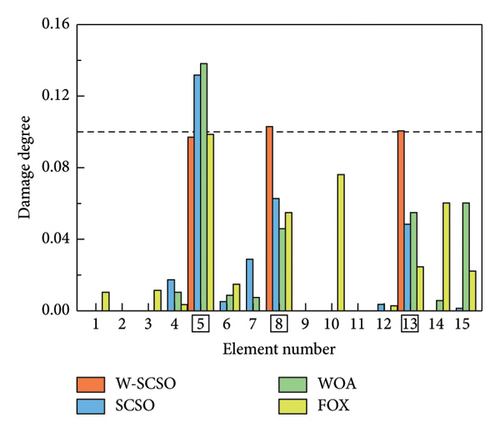
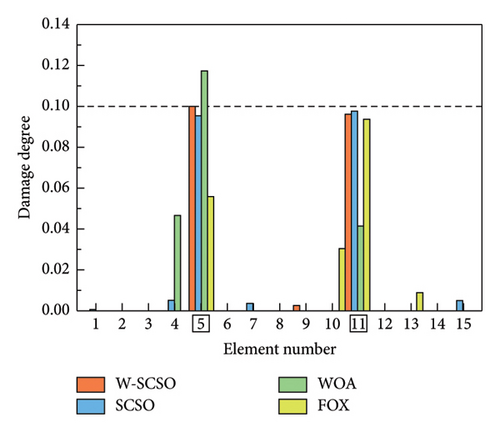
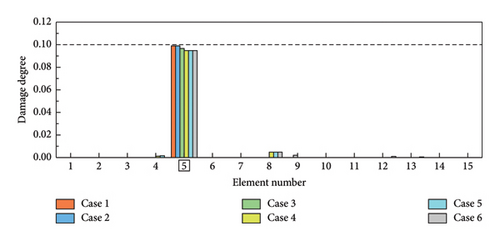
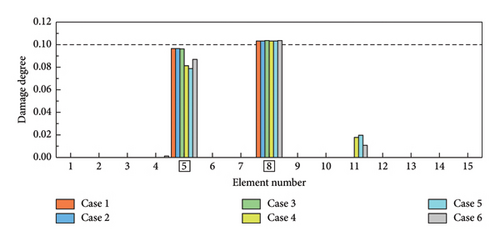
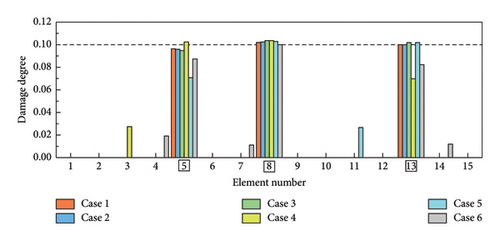
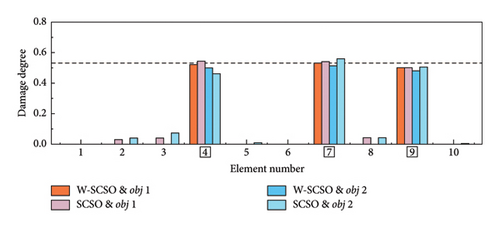
As shown in Table 5, six distinct cases are applied for the simulations of single, double, triple, and symmetrical damages. In cases 1–3, obj 1 is used for SDI, while obj 2 is employed in cases 4–6. The SDI results are shown in Figures 8 and 9. The labels of the actual damaged elements are framed, and the actual degree of damage is marked with a dashed line. On the one hand, the proposed W-SCSO algorithm produces higher precision and less degree of misidentifications compared to the other algorithms in these simulations. On the other hand, compared to obj 2, the proposed obj 1 can more accurately locate and quantify structural damages, which exhibits stronger noise robustness. Especially in triple damage cases, obj 2 struggles to accurately quantify the damage degree of multiple damaged elements, while obj 1 is sensitive to multiple damages, even under high level noise interference. The accuracy of the identification using obj 2 in symmetrical damage cases is reduced because the natural frequency, or circular frequency, sensitivities between symmetric parameters are always equal when damages occur in a symmetric structure with symmetrical form and degree [59]. On the contrary, obj 1 can effectively restrict the adverse effect of natural frequency sensitivities in symmetrical damage identification. Based on the W-SCSO algorithm and the improved objective function, the proposed method has been successfully validated for accurately identifying structural damage in both single and multiple damages using incomplete modal data, even with strong noise interference.
| Case | Measured DOFs | Objective function | Noise level | Damage degree |
|---|---|---|---|---|
| 1 | 14 | obj 1 (MSC & FCR & L1/2 sparse regularization) | 0.15%&5% | 10% |
| 2 | 14 | 0.15%&10% | ||
| 3 | 7 | 0.15%&10% | ||
| 4 | 14 | obj 2 (MAC & FCR & L1/2 sparse regularization) | 0.15%&5% | |
| 5 | 14 | 0.15%&10% | ||
| 6 | 7 | 0.15%&10% |
5. Experimental Verification
5.1. Experimental Setup and Finite Element Model Updating
A simply supported beam model made of aluminum alloy was constructed in the laboratory to evaluate the effectiveness of the proposed method. The geometric parameters and boundary conditions of the beam model are shown in Figure 10, and the experimental model and instruments applied in the experiment are shown in Figure 11. The acceleration responses are collected using the DH5922 dynamic signal test system. The data collection method is preset to continuous sampling, and the signal sampling frequency, the number of time domain points, and the sampling time of each case are 1000 Hz, 2048, and 60 s, respectively. The length and moment of sectional inertia of the beam are defined as 2.46 m and 1.00 × 10−7 m4, respectively. The initial sectional area, density, and Young’s modulus of the beam are 3.00 × 10−3 m2, 2750 kg/m3, and 70 GPa, respectively.
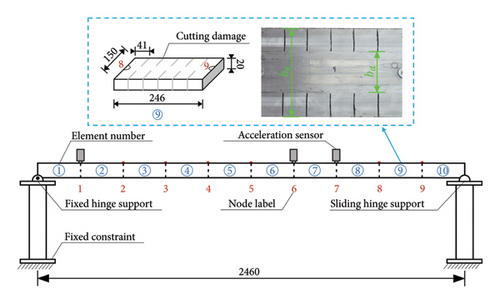
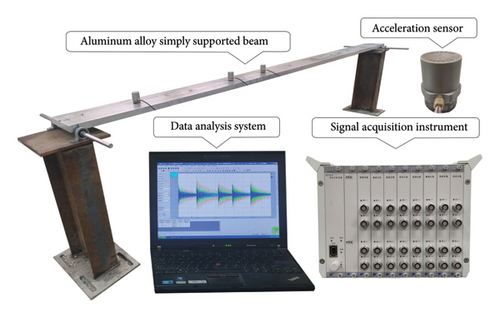
The modal information of the beam is obtained by hammer impact testing for FE model updating and SDI. Three piezoelectric acceleration sensors with the INV9828 specification and a voltage sensitivity of 50.047 mV/ms−2 are placed at nodes to measure the vertical acceleration responses. The sensor located at the first node is fixed, and the remaining sensors are moved in turn from the second node to the ninth node to measure the response data. Subsequently, acceleration responses of the beam are obtained by conducting normalization and the Fast Fourier Transform method is utilized to precondition the responses [60]. Then, the data analysis system is used to obtain the mode shapes and natural frequencies of the experimental beam.
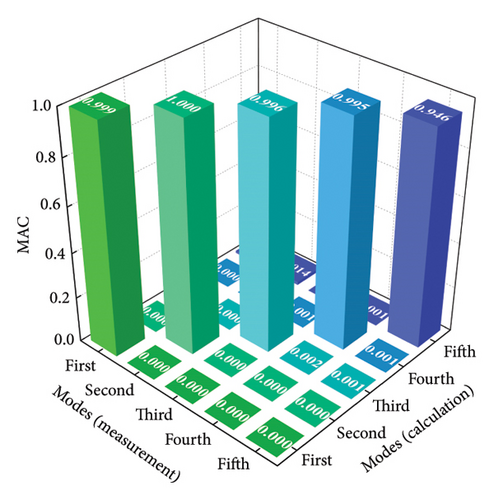
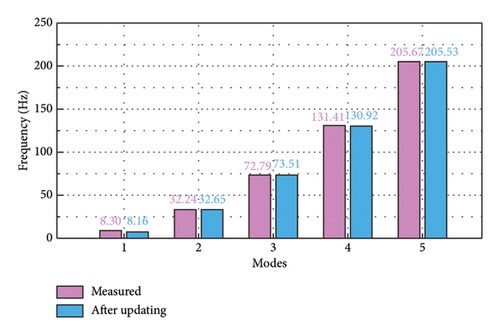
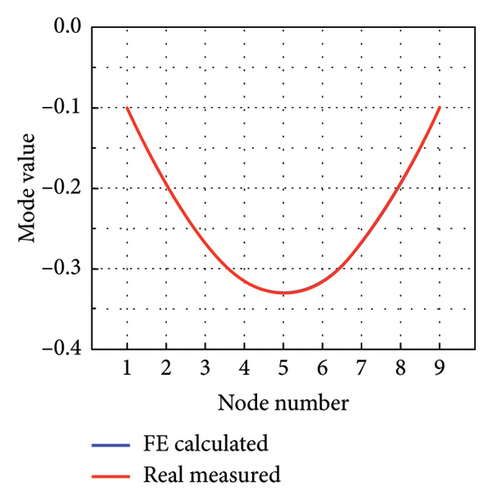
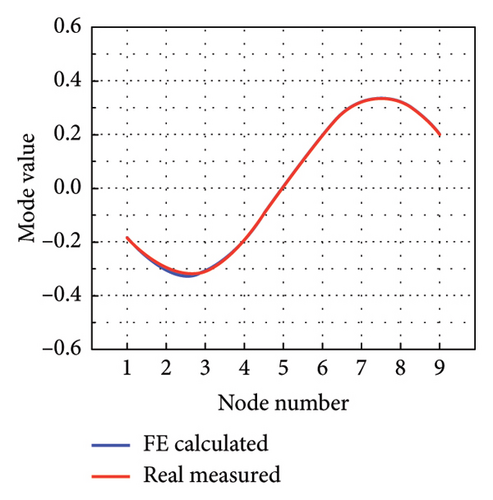
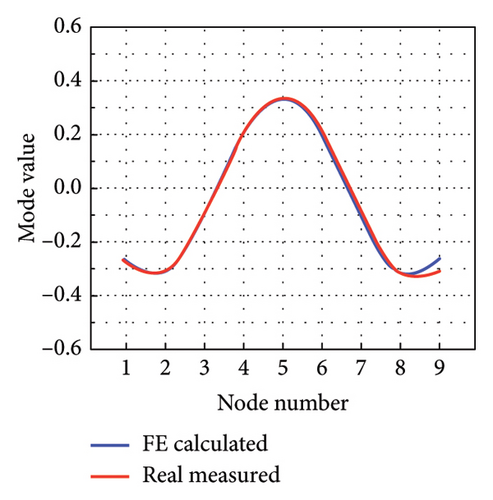
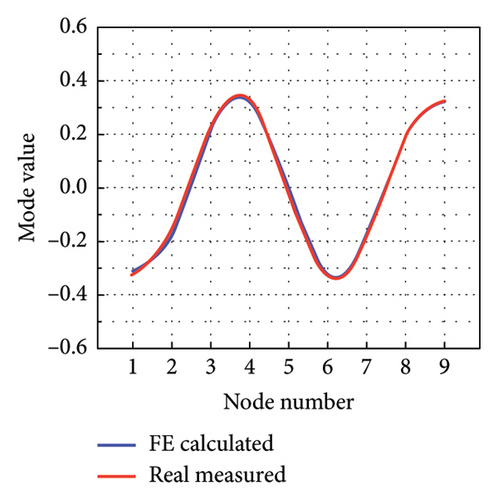
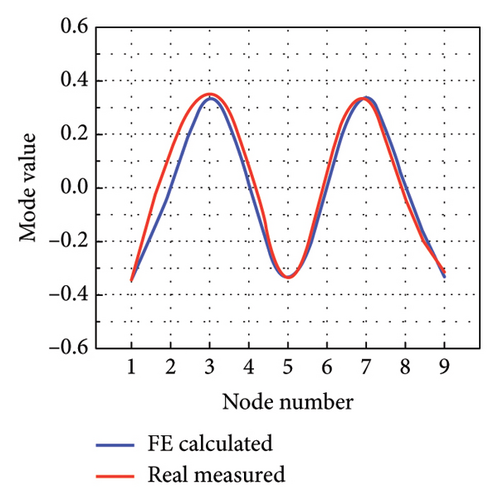
The intact experimental beam is measured five times, and the average of the measured data serves as the measured response for model updating. The limited number of sensors causes the issue of structural modal incompleteness; thereby, Guyan reduction scheme is utilized to acquire low-order modes of the FE model. The W-SCSO algorithm and the improved objective function are utilized for model updating. The updated sectional area, density, moment of sectional inertia, and Young’s modulus of the beam are 2.81 × 10−3 m2, 2683 kg/m3, 1.002 × 10−7 m4, and 7.32 × 1010 N/m2, respectively. The accuracy of the updated FE model can be verified by comparing the measured and calculated MAC, natural frequencies, and mode shapes from the first one to the five orders [20], as shown in Figures 12 and 13. It is obvious that, after model updating, the correlation values of the same orders along the diagonal line in the MAC tend to be 1 and the other values tend to be 0, indicating a strong correlation between modes of the same order in the measured and calculated data. Furthermore, the measured and calculated natural frequencies and mode shapes exhibit similarities. Hence, the calculated results of the updated model have been validated to be consistent with the experimental measurements.
5.2. Experimental Process and Damage Identification
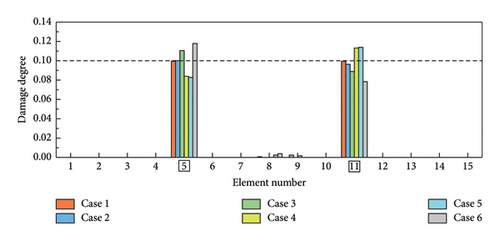
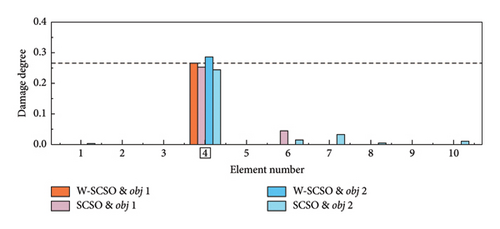
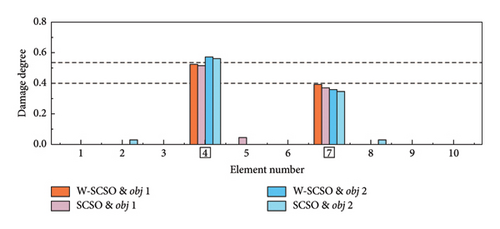
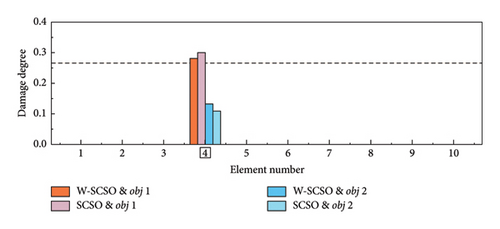
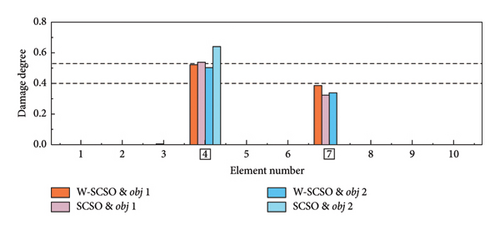
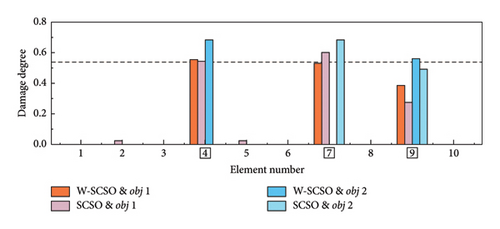
In the experiment, three damage cases are set up, as detailed in Table 6. SDI is performed based on the first four orders of modal information. Each damage case was measured five times, and the average of the measured data was calculated to serve as the reference results. It is worth noting that the measurement data were inevitably interfered with noise, which can lead to uncertain measurement errors and impact the accuracy of the SDI. The reference results are inputted into the W-SCSO and SCSO algorithms to independently calculate the consequence based on obj 1 and obj 2 separately. In this section, the number of individuals for both algorithms is set as 30, with a maximum of 100 iterations.
| Case | Damage element | Depth of cut (cm) | Damage degree (%) |
|---|---|---|---|
| 1 | 4 | 4 | 26.67 |
| 2 | 4 | 8 | 53.33 |
| 7 | 6 | 40.00 | |
| 3 | 4 | 8 | 53.33 |
| 7 | 8 | 53.33 | |
| 9 | 8 | 53.33 | |
To select an appropriate regularization parameter ϵ and compare the numerical and experimental results, SDI is conducted using the updated FE model of the experimental beam, with damage cases consistent with those presented in Table 6. Table 7 shows the SDI results for case 3 under different regularization parameters, where the W-SCSO algorithm with obj 1 is applied for computation. The results indicate that when ϵ = 0.05, the SDI results achieve the highest accuracy compared to other parameter values. Thus, the regularization parameter ϵ is set as 0.05 for obj 1 and obj 2 in the subsequent numerical simulations and experiments.
| ϵ | Noise level | Identified damage | Misidentification |
|---|---|---|---|
| 0 | 0.15%&5% | [email protected]%, [email protected]%, [email protected]% | [email protected]%, [email protected]% |
| 0.005 | [email protected]%, [email protected]%, [email protected]% | [email protected]% | |
| 0.01 | [email protected]%, [email protected]%, [email protected]% | [email protected]% | |
| 0.05 | [email protected]%, [email protected]%, [email protected]% | None | |
| 0.1 | [email protected]%, [email protected]%, [email protected]% | None | |
| 0.5 | [email protected]%, [email protected]%, [email protected]% | None | |
| 1 | [email protected]%, [email protected]%, [email protected]% | None |
In both the numerical model and experimental beam, the W-SCSO and SCSO algorithms are, respectively, applied to compute each damage case 20 times, with the SDI results corresponding to the lowest fitness values shown in Figures 14 and 15. Specially, in the numerical simulation, a noise level of ±0.15% in natural frequencies and ±5% in mode shape data are added. The simulation results demonstrate that the use of obj 1 enables accurate damage identification of the updated FE model, exhibiting stronger robustness compared to obj 2. Furthermore, the proposed W-SCSO algorithm outperforms the SCSO algorithm, achieving fewer misidentifications and higher accuracy in SDI. When using the experimental beam model for damage identification, both algorithms struggle to accurately identify the actual triple damage when employing obj 2. Nevertheless, the proposed obj 1 can be used to identify single and multiple damages. The W-SCSO algorithm can effectively optimize the objective function for locating and quantifying actual damages, whereas the SCSO algorithm tends to produce more errors and misidentifications. The reasons for the imprecise SDI results lie in the random noise disturbance, measurement and model errors, and modal incompleteness. Comparative outcomes indicate that the proposed method possesses strong robustness and satisfactory sensitivity to damage. Experimental results proved that the proposed SDI method, which combines the W-SCSO algorithm and the improved objective function, effectively use the first four orders of incomplete modal information to identify single and multiple damages in the experimental beam. Therefore, the developed approach can be considered to have good applicability in addressing damage identification in bridge structures.
6. Conclusions
- 1.
Better optimization ability and stability of the W-SCSO algorithm are demonstrated compared with the other four algorithms through the CEC2017 benchmark function test. Results indicate that the W-SCSO algorithm exhibits both computational stability and high accuracy.
- 2.
Numerical simulations are performed to verify the effect of the proposed SDI method based on the W-SCSO algorithm and the improved objective function. The simulation results demonstrate that this method can effectively address the SDI problem using incomplete modal data, which represents stronger robustness in the presence of high noise interference.
- 3.
Damage identification results from both numerical and experimental studies show that the proposed method exhibits excellent accuracy and effectiveness in locating and quantifying damages within bridge structures, even with modal incompleteness and strong noise interference.
Conflicts of Interest
The authors declare no conflicts of interest.
Funding
This work was jointly supported by the National Natural Science Foundation of China (Grant Number U2004184), China Scholarship Council Fund as a Senior Research Fellow (Grant Number 202308410481), Training Plan for Young Key Teachers in Colleges and Universities in Henan Province, China (Grant Number 2021GGJS078), CRSRI Open Research Program (Grant Number CKWV20241182/KY), Key Scientific and Technological Research Projects of Henan Province, China (242102241015), and Henan Provincial Natural Science Foundation Project (Grant Number 252300420048).
Open Research
Data Availability Statement
The data that support the findings of this study are available from the corresponding author upon reasonable request.




