Multidomain Secure Communication and Intelligent Traffic Detection Model in VANETs
Abstract
Vehicular ad-hoc network (VANET) plays a vital role in the intelligent transportation system. It is crucial to ensure secure communication among entities in the VANET for realizing an efficient transportation system. In this scenario, the current communication scheme is vulnerable to the leakage of private information from entities. The research primarily centers on single-domain vehicular networks, with only a limited number of researchers exploring cross-domain authentication among vehicle entities. Cross-domain communication schemes have received little attention from scholars. Furthermore, there are issues, including the susceptibility of in-vehicle conversations to eavesdropping, the vulnerability of long-distance transmissions to interruptions, and the exposure of wireless networks to traffic attacks. To address these issues, a multidomain secure communication and intelligent traffic detection model in VANET is proposed. This model offers several notable advantages as follows: (1) It employs a key self-verification algorithm for local computation and authentication of entity keys. This approach mitigates the risks of identity impersonation attacks and key leakage results from third-party key escrow. (2) A multidomain communication scheme is devised to categorize vehicle-to-vehicle (V2V) scenarios into intradomain and interdomain, which correspond to situations where the communicating parties are within the same domain and across different domains, respectively. (3) We propose the implementation of new session message encryption algorithms for V2V communication. This involves generating dynamic random keys to ensure secure data sharing and facilitates long-distance cross-domain communication among vehicles. (4) An intelligent two-layer traffic detection paradigm is proposed to improve the efficiency of detecting attack traffic in vehicular networks. This paper provides security proofs and performance analysis of the proposed scheme. The experimental results demonstrate that within the communication module, the comparative scheme exhibits high computational demands and significant delays, whereas our approach provides superior security and better computational performance. Compared to the traditional detection model, our two-layer detection paradigm reduces model training time by 69–4477 ms and testing time by 9–1469 ms.
1. Introduction
One of the application scenarios of intelligent transportation systems (ITSs) is vehicular ad-hoc network (VANET) [1]. VANET is a vehicle communication network that facilitates traffic warnings, automated driving, enhanced driving comfort, and road traffic information retrieval. It is a self-organizing, cost-effective, and open network structure built on the road [2].
1.1. Research Motivation
- •
Due to the majority of data transmission occurring over wireless networks, VANETs are susceptible to identity spoofing attacks. To combat such attacks, authentication technology serves as a powerful tool [9]. It is worthwhile for researchers to consider how to use this technology to make terminal privacy information more secure.
- •
Intercepting messages transmitted in the public channel is easy for hackers [10], and it is urgent to protect communication security in resource-constrained VANET environments.
- •
While large-scale VANETs can offer drivers a wealth of detailed and diverse information, they also become more attractive targets for hacking attacks [11]. While exploring solutions for attack traffic detection, researchers are confronted with the challenge of balancing detection performance and detection efficiency. This conflict has become a prominent topic of the study.
Consequently, the identification of vehicles, ensuring secure communication between them, and detecting attacks within the network have emerged as difficult and pressing issues in the ongoing research on secure communication in vehicle self-organized networks. Failing to address these three problems adequately can result in significant property damage and even pose threats to human lives [12].
1.2. Our Contribution
- •
A multidomain secure communication and traffic detection model in VANET is proposed. An authentication module, a secure communication module, and a detection module are included in the model. The authentication module provides authentication functions for both vehicle-to-roadside unit (V2R) and vehicle-to-vehicle (V2V) communications within the same domain. The communication module facilitates V2V communication. Lastly, the detection module works to improve the efficiency of flow detection.
- •
Decentralized key generation is implemented in the proposed scheme, eliminating the need for key assignment by a central authority. Instead, a key self-verification algorithm is employed to validate the public and private keys of entities, including roadside units (RSUs) and vehicles. This approach significantly mitigates the security risks of large-scale key leakage due to attacks on the key generation center and impersonation attacks due to key interception during key distribution.
- •
Cross-domain secure channels are established. Communication schemes are distinguished as intradomain and interdomain. The intradomain scheme caters to communicating parties within the same domain, while the interdomain scheme accommodates communication between communicating parties in different domains. To enhance communication security, dynamic random keys are utilized. The scheme demonstrates excellent scalability and high security, making it suitable for diverse application scenarios.
- •
A two-layer traffic detection paradigm is employed to more efficiently detect attacks in VANETs. The traffic detection process is divided into two steps, and four machine learning algorithms are tested and evaluated. The results demonstrate that the proposed scheme yields a significant reduction in time requirements, including both training and detection time, while slightly enhancing the overall detection performance compared to the original algorithm with only one step.
1.3. Organization
The remainder of the paper is structured as follows. Section 2 discusses the related research work, and Section 3 presents the fundamentals used in this paper. Section 4 outlines the system model and initializes the system. Sections 5 and 6 are the authentication module and secure communication module, respectively. Section 7 is the detection module. The performance analysis of the three modules is shown in Section 8. Finally, the conclusion is presented in Section 9.
2. Related Work
Three key directions relevant to this paper are summarized as follows: the authentication scheme, communication scheme, and traffic detection scheme. This section provides an overall review of the schemes proposed by other researchers.
2.1. Authentication
In the literature [3], a software-defined networking (SDN)–based comprehensive framework is proposed to address the challenge of providing ubiquitous and reliable connectivity among high-speed vehicles in the context of 5G. The framework incorporates an authentication protocol based on elliptic curve ciphers (ECCs) to ensure end-to-end privacy protection. Considering the inherent high mobility of vehicles, the authors of literature [13] introduce a combined proof and certification scheme for verifying the electronic control unit (ECU) firmware installed in vehicles. This scheme enables the RSU’s edge server (ES) to verify the integrity of the ECU firmware as a vehicle passes through an RSU. To mitigate the risk of unauthorized visitors exploiting legitimate authentication, the authors of literature [14] present a dual authentication scheme for the internet of vehicles (IoV). This scheme incorporates trust assessment in the authentication protocol, evaluating a vehicle’s reputation based on its historical interaction behavior. The authors in literature [15] shift the authentication computation to registration, eliminating most of the computational tasks at the terminal. The protocol is shown to be secure under the decision bilinear Diffie–Hellman (DBDH) problem assumption and performs very well in performance analysis. A hash-based lightweight and anonymous authentication scheme is designed in literature [16]. It can address the aforementioned restrictions and enhance the effectiveness of authentication in vehicle-to-infrastructure (V2I) architecture. This scheme effectively combines identity, password, and biometric to enhance resistance against impersonation, denial of service (DoS), and privileged insider attacks. The authors of literature [17] introduce a lightweight, conditional privacy-preserving authentication and key agreement model. This model utilizes symmetric keys to minimize computation and communication overhead during the process. It also addresses the issue of a single point of failure by employing a multitrusted authority (TA) approach. In addition, the model supports the revocation of identities for illegal vehicles. By combining the advantages of attribute encryption and authentication, the authors of literature [18] propose an authenticated asymmetric group key agreement (AGKA) based on attribute encryption. Attribute encryption and authentication techniques ensure the security of the group key protocol and protect individual privacy. In addition, the protocol transfers the computation and communication loads to powerful servers to reduce the workload of smart terminals under unbalanced mobile networks. To provide a secure and efficient transmission mechanism for data over public channels, the authors of literature [19] propose a privacy-preserving intervehicular authentication protocol for VANETS using physical unclonable function (PUF). It is more reliable, convenient, and practical for secure data transmission in VANETs.
However, the majority of these schemes rely on traditional authoritative centers or trusted authorities for authentication, which may limit the robustness of VANET. Moreover, the utilization of traditional key escrow technology in these schemes poses risks such as key leakage, key interception, and counterfeit attacks.
2.2. Communication
In the context of secure communication within smart cities, the authors of literature [6] present a two-level authentication key exchange scheme utilizing ECC technology. The first level involves authenticating the cluster heads (CHs), while the second level requires the verified CHs from the first level to authenticate vehicles and facilitate message exchange between the CHs and vehicles. The authors of literature [20] establish a lightweight and efficient group communication channel between sensor nodes. Taking the CHs as a bridge node, it realizes that the sensor nodes in different clusters have the same group key information and negotiate a pair of asymmetric group keys to realize cross-cluster secure communication. The cluster communication adopts an asymmetric encryption mechanism. It realizes the group-secure communication mechanism in which the message sender is not constrained. The authors of literature [21] propose a protocol that establishes a session key between vehicles and RSUs using lightweight cryptographic primitives. It employs a pseudonym mechanism to maintain the anonymity of legitimate vehicles while allowing malicious vehicles to be tracked. Moreover, it does not require a TA to verify the identities between vehicles and RSUs. The authors of literature [22] propose an AGKA protocol between intelligent information system terminals for mobile edge computing networks. AGKA is used to realize the group-secure communication mechanism in which message senders are not constrained in this protocol. In the literature [23], a group key agreement (GKA) protocol is suggested to establish a secure communication channel for intelligent terminals. The protocol offers scalability and dynamic configurability by allowing users to adjust the privacy level based on their preferences. The authors of literature [24] introduce a computationally efficient privacy-preserving identity-based recognition model. Identity-based cryptography (IDC) and ECC are employed to ensure message origin, message integrity, nonrepudiation, and vehicle identity anonymity in V2V communication.
Some schemes, including the aforementioned communication schemes, aim to enhance security but often come with drawbacks such as increased computational complexity, costs, and time consumption. However, in the VANET scenario, where vehicles move swiftly, long delay solutions are not viable. Furthermore, existing communication schemes treat all vehicle terminals in the network equally, resulting in similar communication consumption for both nearby and distant vehicles.
2.3. Detection
Literature [25] develops a lightweight security protocol for radio frequency identification (RFID)–based vehicular cloud computing (VCC) using hash functions and Henon mapping. This protocol can resist physical attacks on RFID tags, and its security against various attacks is verified using the Scyther simulation tool. The authors of literature [26] employ the Bat algorithm with group division and binary difference mutation to select typical features. A weighted voting mechanism based on the random forest (RF) algorithm is established, allowing for adaptive weight changes of samples during stream classification. This approach demonstrates effective feature selection and achieves accurate classification. To improve detection performance, the authors of literature [27] introduce a cognitive memory–guided autoencoder constructed using a deep neural network. The model capitalizes on the advantages of an autoencoder and enhances the storage capability of normal feature patterns through a memory module. The memory module is constrained by feature reconstruction loss and feature sparsity loss, resulting in improved discriminative power and superior detection performance. Addressing different attack types, the authors of literature [28] propose an adaptive approach to generate the optimal number of hidden layers and neurons per layer through multiple iterations of the genetic algorithm. The detection model achieves a high detection rate by adapting to the specific attack characteristics. Using the SDN controller as a foundation, the authors of literature [29] detect intrusions by analyzing host logs and network traffic, employing signature-based, anomaly-based, and machine learning–based detection methods. The approach successfully combines different detection techniques to enhance intrusion detection effectiveness. In the literature [30], the authors construct a real testbed to simulate network attacks and design intrusion detection systems (IDSs). Attacks targeting backdoors, command injections, and structured query language vulnerabilities are injected into the system. A machine learning–based anomaly detection system is employed to analyze the detection of the aforementioned attacks. The authors of literature [31] propose a gradient hybrid leader–based optimization (HLBO) algorithm based on the HLBO algorithm to identify distributed DoS (DDoS) attack detection easily in an optimized manner. In the literature [32], flows are categorized into “easy flows,” which are detected in the first stage, and “hard flows,” which are detected in the second stage. The objective is to minimize the time required for classifying encrypted streams while maintaining a high level of accuracy in stream classification.
As summarized above, researchers have made progress in the field of VANETs traffic detection. However, their schemes often focus on optimizing the internal structure of algorithms while overlooking the importance of adjusting the detection processes.
2.4. Our Scheme
To address the aforementioned issues, we present a multidomain secure communication and traffic detection model in VANETs. In this model, we replace traditional key certification authorities with a key self-verification algorithm, mitigating the risks associated with key leakage and interception. Two communication schemes are designed to cater to both near-range and long-range V2V communication scenarios, thereby further reducing the communication overhead in near-range interactions. To meet the low-latency requirements of VANET scenarios, we scale down the consumption while ensuring security. In addition, we propose a two-layer traffic detection scheme that significantly reduces the training and detection time of the model.
3. Preliminaries
3.1. Elliptic Curve and Bilinear Pairings
The definition of an elliptic curve E/Fp is given. Let p and q be large prime numbers. An elliptic curve E/Fp is defined by the equation y2 = x3 + a1x + b1(mod p), while a1, b1, x, y ∈ Fp. The set of all the points on the curve together with a “point at infinity” O forms an additive group under the point addition operation. Let G1 be a subgroup of order q, where q ≥ (2k + 1) (k is the safety parameter), and g0 is a generator of G1. Scalar multiplication is defined as ng0 = g0 + g0 + ⋯+g0(n times), where .
-
Property 1: Bilinearity: For any two elements u and v of the group G1, and , there is e(au, bv) = e(u, v)ab.
-
Property 2: Nondegeneracy: There exists a generating element g0 of G1 and a unit element 1 of G2, satisfying e(g0, g0) ≠ 1.
-
Property 3: Computability: For any two elements u and v on the group G1, there exists an efficient algorithm to compute e(u1 + u2, v) = e(u1, v)e(u2, v).
3.2. Bilinear Mapping Complexity Assumptions
- •
Discrete logarithm problem (DLP): Assume that , given and g0, it is difficult to compute an unknown .
- •
Computational Diffie–Hellman problem (CDHP): Given g0 ∈ G1 and elements (ag0, bg0), it is difficult to calculate abg0 when is unknown.
- •
Bilinear CDHP (BCDHP): Given elements g0, ag0, bg0, cg0 ∈ G1, it is difficult to calculate when is unknown.
- •
Inverse CDHP (Inv-CDHP): Given g0, ag0, abg0 ∈ G1, where , it is difficult to calculate (ab/a)g0.
3.3. Multilinear Mapping
-
Property 1: Multilinearity: For g1, g2, …, gk ∈ G1 and , there is .
-
Property 2: Nondegeneracy: There exist g1, g2, …, gk ∈ G1, which satisfy e1(g1, g2, …, gk) ≠ 1.
-
Property 3: Computability: For g1, g2, …, gk ∈ G1, there exists an efficient algorithm to compute e1(g1, g2, …, gk).
3.4. Multilinear Mapping Complexity Assumptions
- •
Multilinear CDHP (MCDHP): Given elements g1, g2, …, gk, gk+1 ∈ G1 and (a1g1, a2g2, …, ak+1gk+1), it is difficult to calculate when are unknown.
- •
Inverse MCDHP (Inv-MCDHP): For g0, aig0, aiajg0 ∈ G1(i, j = 1, 2, …, k, and i ≠ j), known aig0, aiajg0, where , it is difficult to calculate ajg0.
K.Gen is a key generation function K.Gen(1λ)⟶(Cpk, Csk), and λ is a security parameter. Cloud runs this function to obtain the public/private key pair (Cpk, Csk), where , Cpk = Cskg0.
Table 1 offers a description of frequently recurring symbols.
| Symbol | Description |
|---|---|
| G1 | Additive group on elliptic curves E/Fp |
| G2, GT | Multiplicative cyclic groups on elliptic curves E/Fp |
| g0 | The generating element of G1 |
| e | Bilinear mapping |
| e1 | Multilinear mapping |
| H1(·), H2(·), H3(·), H4(·) | Collision-resistant hash functions |
| (Cpk, Csk) | Public/private key pairs of the cloud |
| (PKk, SKk) | Public/private key pairs of RSUk |
| (pkk,m, skk,m) | Public/private key of vehicle m located in domain k of the RSU |
4. System Model and Initialization
4.1. System Model
-
Cloud is a trustworthy cloud platform responsible for generating public parameters and master keys within the system. It plays a crucial role in verifying the identity of both RSU and vehicle entities and authenticating their public and private keys. Furthermore, the cloud assists authenticated RSUs in establishing the communication alliance domain.
-
ES serves as the intermediary link connecting each RSU to the cloud. In comparison to the cloud, ES is in closer proximity to the system terminals, enabling quick responses to terminal requests. Each ES is responsible for managing a cluster of geographically proximate RSUs. It possesses computational capabilities and can locally cache frequently requested resources to ensure rapid responses to terminal demands. Long-distance information forwarding is facilitated by the ESs, and specific transmission channels exist between different ES clusters.
-
RSU has a fixed communication range, called a domain, which is widely distributed in real traffic scenarios. Each domain is managed by a unique RSU, and each RSU is responsible for a single domain. The RSU verifies the identities of vehicles within its domain and forwards communication requests from legitimate vehicles to terminals within the domain or other RSUs. Each RSU is managed by a unique ES.
-
Vehicle, serving as the terminal of the system, is required to authenticate its identity to the RSU within its domain. Depending on the specific communication request, the vehicle can establish communication with other terminals in the same domain or with terminals in other domains by the assistance of the RSU.
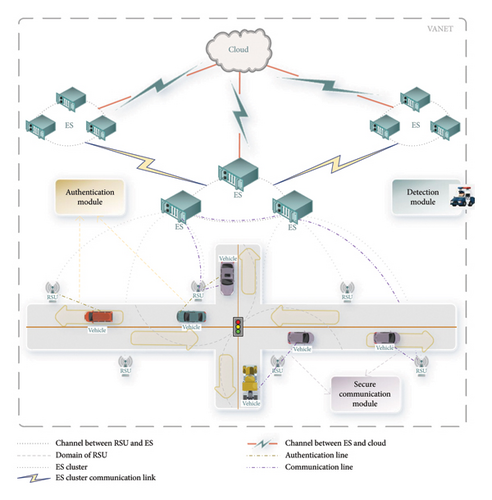
The model is designed with three functional modules: the authentication module, the secure communication module, and the detection module. The authentication module provides authentication functions for vehicle terminals. Specifically, vehicles authenticate themselves to the RSU responsible for managing the domain, and vehicles within the same domain authenticate each other. The communication module facilitates the establishment of secure communications for vehicle terminals. It enables terminals within the same domain and across different domains to establish secure communication channels. These two function modules have strict sequential requirements, and only the RSUs and vehicles that have completed the authentication module can utilize the communication function. The detection module continuously operates from the system’s initiation. It is responsible for detecting traffic within the system, identifying malicious and aggressive traffic, and reporting such incidents to the respective RSU within the domain. The detection module plays a vital role in ensuring the ongoing safe operation of the system.
4.2. Initialization
All entities within the model require initialization, which can be summarized as follows: system parameter generation, terminal key self-verification, and alliance domain establishment. In this paper, it is assumed that there are a total of P vehicles distributed across R domains. The identification (ID) information of both the RSU and the vehicle, which consists of a fixed-length string, is registered with the relevant government department, such as the ministry of transportation. It is assumed that the cloud is aware of the ID for each RSU and vehicle. In addition, , , H3 : GT⟶G1, and are the four collision-resistant hash functions utilized in the model.
Cloud initiates the key generation function, K.Gen(1λ), to generate the public/private key pair (Cpk, Csk) for cloud, where and Cpk = Cskg0. The system parameters {Cpk, q, G1, G2, GT, g0, e, e1, H1, H2, H3, H4} are also generated by the cloud.
4.2.1. Terminal Key Self-Verification
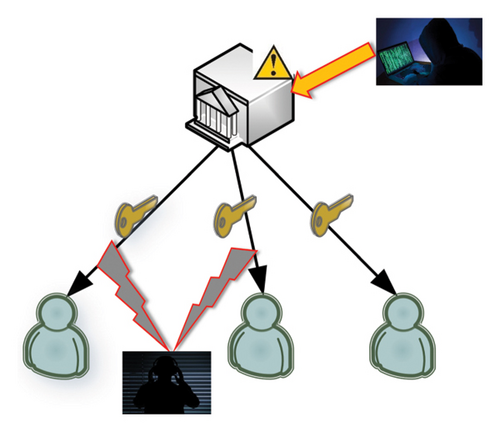
In traditional schemes, terminal keys are usually generated by a trusted third party and transmitted to the terminals through a dedicated channel. Nonetheless, these channels are susceptible to the presence of numerous stealthy adversaries that attempt to eavesdrop on the key transfer process. Once an attacker gains access to a terminal’s key, the potential damage is evident. Moreover, third parties holding a significant number of terminal keys become vulnerable to coordinated attacks by malicious actors. Any compromise in this context can lead to the breach of confidentiality for a substantial number of endpoint keys within the system, as depicted in Figure 2(a).
- 1.
The terminal Lk selects a random positive integer and computes SKk = H1(IDk)τk, PKk = SKkg0, and tk = τkCpk, where SKk is the private key and PKk is the public key. The message {PKk, tk} is sent to the cloud by terminal Lk.
- 2.
After receiving the message {PKk, tk}, the cloud calculates and ϑC,k = H1(IDk)g0 according to the sender’s identifier. Equations and are verified by the cloud. If it holds, the PKk is secretly saved by the cloud as the public key of terminal Lk, and the PKk is associated with the identification information IDk.
At this point, the key of terminal Lk is certified by the cloud. For the convenience of readers, in the following, (PKk, SKk) is used to denote the public/private key of the RSUk, and (pkk,m, skk,m) is used to represent the public/private key of the mth vehicle in domain k. The process is described in Algorithm 1.
4.2.2. Alliance Domain Establishment
- 1.
The cloud calculates the parameter yPKk = e1(PK1, PK2, …, PKk−1, PKk+1, …, PKR) and generates the signature . The message {yPKk, sigCk} is then delivered to RSUk by the cloud.
It should be noted that the parameter yPKk is exclusively used by RSUk to calculate the federated domain key in subsequent steps, and each RSU is assigned different parameters. For RSUi in domain i, the cloud computes the parameter yPKi = e1(PK1, PK2, …, PKi−1, PKi+1, …, PKR) and generates the signature , and the message {yPKi, sigCi} is sent to RSUi. Similarly, the cloud computes the required information for each authenticated RSU in turn and sends the information accordingly.
-
Algorithm 1: Key self-verification algorithm.
-
for k in {1, 2, …, R + P}
-
1. Lk ⟶ Cloud
-
select
-
compute SKk = H1(IDk)τk, PKk = SKkg0 and tk = τkCpk
-
send {PKk, tk}
-
2. Cloud
-
compute ϑC,k = H1(IDk)g0 and
-
verify and
-
storage PKk
-
end
- 2.
Once the message arrives at its destination, its authenticity and correctness must be checked first by the receiver. Equation is verified by RSUk. If it holds, the verification passes. Then, with its private key SKk, RSUk calculates the session key of the alliance domain as
()
The above steps are summarized in Algorithm 2. By following these steps, each RSU can compute the same alliance domain session key, denoted as s1 = s2 = ⋯ = sR (the proof is described in Theorem 3 in Section 8.1.1). In the subsequent discussion, s0 will be used to represent the session key of the alliance domain.
-
Algorithm 2: Establishment of communication alliance domain.
-
for k in {1, 2, …, R}
-
1. Cloud ⟶ RSU
-
compute yPKk = e1(PK1, PK2, …, PKk−1, PKk+1, …, PKR) and
-
send {yPKk, sigCk}
-
2. RSU
-
verify
-
compute
-
end
5. Authentication Module
In the VANET scenario, attackers are skilled at exploiting weak points, particularly the identities of legitimate entities that are exposed in the open network. Legitimate entities are cautious and do not readily trust entities other than themselves. Before exchanging information, any two entities must verify each other’s identities. Hence, this authentication module provides two functions: first, the authentication of the vehicle with the RSU of the domain it is in, which needs to be performed by every vehicle participating in the VANET; second, the authentication of the vehicle with other vehicles in the same domain, which is required when the vehicles in the same domain establish communication. All vehicles must adhere to the logical rule of “authentication before communication.” Only authenticated vehicle terminals can obtain the parameters for subsequent communication functions.
5.1. Authentication Between Vehicle and Local Domain RSU
Each RSU is responsible for verifying the legitimacy of the vehicle identities within its domain. Vehicles need to identify themselves to the RSU where they are located. This authentication process is not limited to unidirectional identity verification from the RSU to the vehicle. The vehicle also needs to verify the authenticity of the RSU to ensure that it is indeed the legitimate RSU managing the domain.
- 1.
RSUi randomly selects and calculates f = 1/(s0 + SKi), Fi = fiβig0 and ρi,m = βipki,m(1 ≤ m ≤ γ). The message {PKi, Fi, ρi,m} is sent by RSUi to Ui,m(1 ≤ m ≤ γ) located in the domain i.
-
Note: Each vehicle terminal in domain i receives the same parameters PKi and Fi, except for the last parameter, which differs, and the vehicle terminal Ui,n receives ρi,n = βipki,n.
- 2.
After receiving the message {PKi, Fi, ρi,m}, Ui,m calculates and verifies . If the equation holds, then Ui,m computes sigi,m = (1/(ski,m))ηi,m and sends the message {pki,m, sigi,m} to RSUi.
- 3.
After vehicle RSUi receives the message, it first checks equation . If this equation holds, RSUi considers Ui,m as a member of this domain, and two-way authentication is completed. Subsequently, RSUi will process legitimate requests from this member.
In the above step, bidirectional authentication between RSU and vehicle is achieved through the equations and . This approach effectively prevents hackers from impersonating RSUs to deceive the trust of vehicles. Compared to traditional unidirectional authentication schemes, our scheme greatly enhances authentication security.
5.2. Authentication Between Vehicles in the Same Domain
- 1.
Ui,m calculates sigm,l = ski,mpki,l and Mi,m = H2(sigm,l) ⊕ ηi,m. The message {sigm,l, Mi,m, pki,m} is sent by vehicle Ui,m to vehicle Ui,l. Here, ηi,m is the parameter obtained by Ui,m in Section 5.1.
- 2.
After receiving the information {sigm,l, Mi,m, pki,m}, Ui,l calculates Mi,l = H2(ski,lpki,m) and checks the equation according to the parameter ηi,l obtained by Ui,l in Section 5.1 (note: ηi,l = ηi,m). If the equation holds, the Ui,m is an authenticated vehicle by RSUi and Ui,l can consider negotiating the session key with it later. If Mi,l ⊕ Mi,m ≠ ηi,l, subsequent communication requests of Ui,m will be rejected by Ui,l.
6. Secure Communication Module
The registered and authenticated vehicles within the system can securely share data, exchange information, and collaborate on calculations by establishing a secure channel between them. The communication between vehicles can be categorized into two types: communication between vehicles within the same RSU domain and communication between vehicles distributed across different RSU domains. In this paper, the secure communication technology between vehicles involves establishing secure communication by encrypting session information through online negotiation of a common session key between vehicles. The establishment of session keys between vehicles can further be divided into two scenarios: establishing session keys between vehicles within the same RSU domain and establishing session keys between vehicles distributed across different RSU domains. The following sections describe these two types of secure communication schemes in detail.
6.1. Intradomain Vehicle Terminal Communication
6.1.1. Session Key Establishment Between Vehicles in a Common RSU Domain
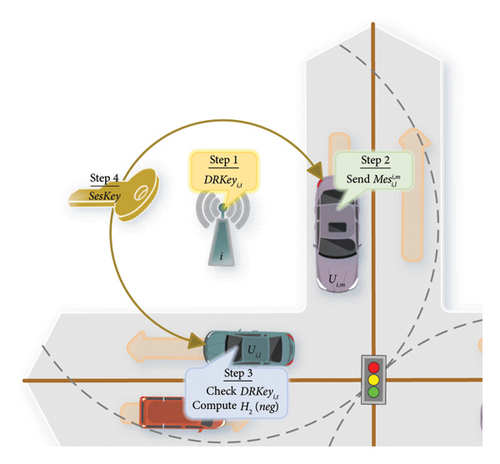
- 1.
At moment t, RSUi chooses a random number and generates the current timestamp timei,t. RSUi calculates DRKeyi,t = H1(H2(PKi)||ui,t||timei,t). Among them, a random number can make the key random, making it impossible for external attackers to infer the key through the regulation; a timestamp is used to ensure the dynamic nature of the key, which can effectively prevent attackers from brute-force cracking. The RSUi transmits DRKeyi,t, which is the component of the session key for the future [t, t + t0) time period of the domain, to the authenticated vehicle terminals within the same domain.
-
DRKeyi,t is a component of the session key for vehicles in domain i, which is valid for a fixed interval period t0 (i.e., for time [t, t + t0)). At the moment (t + t0), RSUi will regenerate a new random number and calculate a new according to the above process, where is the timestamp of moment (t + t0). is valid for time [t + t0, t + 2t0).
- 2.
Vehicle Ui,m send message to vehicle Ui,l. This message indicates that Ui,m requests to establish a session key with Ui,l.
- 3.
After receiving the message , vehicle Ui,l checks whether the DRKeyi,t in the message is the same as it received from RSUi. If it is the same, the parameter ηi,l obtained in the authentication phase is used as the negotiation part, i.e., negi,l = ηi,l. Ui,l calculates the session key SesKeyi,m,l = H1(H4(DRKeyi,t‖H2(negi,l))) and sends the ready status to Ui,m.
- 4.
After vehicle Ui,m completes Step (2), it calculates the session key SesKeyi,m,l = H1(H4(DRKeyi,t‖H2(negi,m))). Once Ui,m receives the ready state from vehicle Ui,l, they are ready to start communication using the session key SesKeyi,m,l.
By combining dynamic random key parameters issued by the RSU and the negotiation process between vehicles, the confidentiality and integrity of intradomain communication are enhanced. The intradomain session key negotiation process is shown in Figure 3.
6.1.2. Secure Communication Between Vehicles in a Common RSU Domain
Suppose that the vehicle terminal Ui,m sends a message mi,m,l to Ui,l. The process of establishing secure communication between vehicle terminal Ui,m and Ui,l is as follows.
Session message encryption: The message sender Ui,m encrypts the message using the session key SesKeyi,m,l negotiated in Section 6.1.1, that is, calculates MESi,m,l = mi,m,l ⊕ SesKeyi,m,l. The message {MESi,m,l, pki,m} is then sent to vehicle Ui,l.
Session message decryption: After receiving the message {MESi,m,l, pki,m}, vehicle Ui,l determines that the other party is the vehicle Ui,m according to pki,m and decrypts the message using the session key SesKeyi,m,l negotiated with Ui,m. Ui,l calculates mi,m,l = MESi,m,l ⊕ SesKeyi,m,l and obtains the decrypted message mi,m,l.
6.2. Interdomain Vehicle Terminal Communication
6.2.1. Session Key Establishment Between Vehicles in Different RSU Domains
The communication key for interdomain vehicles is composed of two parts: “dynamic + attribute.” “Dynamic” refers to the time stamp time when the communication is established. Adding a timestamp prevents the key from being brute-force cracked by an attacker effectively. “Attributes” refers to the attributes Attr owned by the vehicle terminal. Attributes include those that come with the vehicle terminal itself and those created by the vehicle’s user. A vehicle belonging to the same manufacturer has the same Attr attribute, for example, {Benz, Toyota, and Volkswagen, …}. Each vehicle can customize its relational network, for example, {fammily, friends, colleagues, …}, and the vehicles in the same relational network have the same attribute.
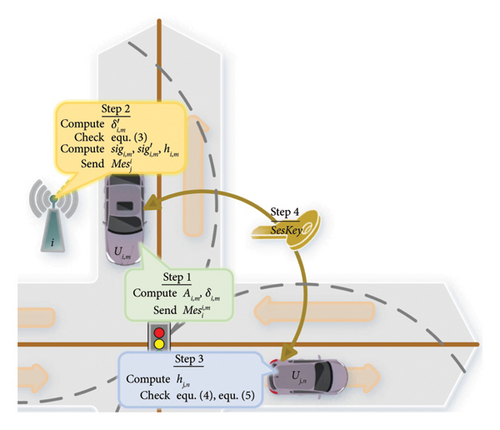
- 1.
Vehicle Ui,m calculates Ai,m = H1(friends) and . Ui,m sends the message to the RSUi.
- 2.
After RSUi receives the message , it calculates and verifies the following equation:
() -
If equation (3) holds, RSUi confirms that Ui,m is the member of this domain. Then, RSUi signs the message of member Ui,m with the session key of the alliance domain. RSUi computes , and and sends the message to RSUj. If equation (3) does not hold, RSUi rejects to sign, and it will not be forwarded to RSUj either. Finally, the information is forwarded by RSUj to the vehicle terminal Uj,n.
- 3.
Upon receiving the message , Uj,n initially computes and verifies whether the following equation:
() -
holds, thereby ensuring the integrity of the message. After the verification passes, Uj,n verifies the following equation:
() -
using the session public key pk0 of the federated domain and the public key pki,m of Ui,m. If the equation is verified, it indicates that Ui,m is a vehicle terminal authenticated by the RSUi, and Ai,m is a ciphertext attribute that has been verified and signed by the RSUi. According to Ai,m, vehicle Uj,n can determine the attribute used by Ui,m as friends. Uj,n sends the readiness status to Ui,m and calculates the session key SesKeyi,m,j,n = H1(time‖friends) based on the current timestamp and explicit attribute.
- 4.
After vehicle Ui,m receives the ready state from Uj,n, it calculates the session key SesKeyi,m,j,n = H1(time‖friends) using the same method. SesKeyi,m,j,n is subsequently utilized as the key for the session between vehicle terminals Ui,m and Uj,n, which belong to different domains.
Vehicles with the same attributes can communicate using their exclusive keys. Therefore, the scheme is highly scalable as well as highly secure and can be adapted to a variety of application scenarios. The interdomain session key negotiation process is shown in Figure 4.
6.2.2. Secure Communication Between Vehicles in Different RSU Domains
We suppose that the vehicle terminal Ui,m sends a message mi,m,j,n to Uj,n. The process of establishing secures communication between vehicle terminal Ui,m and Uj,n is as follows.
Session message encryption: the message sender Ui,m encrypts the message using the session key SesKeyi,m,j,n negotiated in Section 6.2.1, that is, calculates MESi,m,j,n = mi,m,j,n ⊕ SesKeyi,m,j,n. The message {MESi,m,j,n, pki,m} is then sent to vehicle Uj,n.
Session message decryption: After receiving the message {MESi,m,j,n, pki,m}, vehicle Uj,n determines that the other party is the vehicle Ui,m according to pki,m and decrypts the message using the session key SesKeyi,m,j,n negotiated with Ui,m. Uj,n calculates mi,m,j,n = MESi,m,j,n ⊕ SesKeyi,m,j,n and obtains the decrypted message mi,m,j,n.
7. Detection Module
The rise of VANET has attracted significant attention from attackers. Hackers are likely to launch various malicious attacks. For instance, they can manipulate data and send false information to unsuspecting vehicles, resulting in intentional accidents. In addition, hackers can launch flooding attacks on RSUs, overwhelming them with excessive requests and impeding their ability to handle legitimate requests from other vehicles. Moreover, hackers may infiltrate the network and stealthily extract substantial amounts of sensitive information. Undoubtedly, these actions pose a severe threat to the security of VANET.
Considering that VANET scenarios are more vulnerable to attacks, our secure communication model contains the detection module compared to traditional communication schemes. The primary function of this module is to discern between malicious and normal traffic, promptly intercepting and reporting any malicious activity. The detection of network anomalies constitutes a pivotal area of research [35], emphasizing the significance of effectively detecting and preventing attacks. Fortunately, the hackers’ attack differs from the honest terminals’ behavior. If an attack is launched, it will leave a corresponding trace. There are many current schemes for classifying and detecting DoS traffic. However, what we propose is a detection paradigm that can be applied to other scholars’ research models. In this section, the data preprocessing is first described and then the proposed traffic detection mechanism is presented.
7.1. Data Preprocessing and Dataset Description
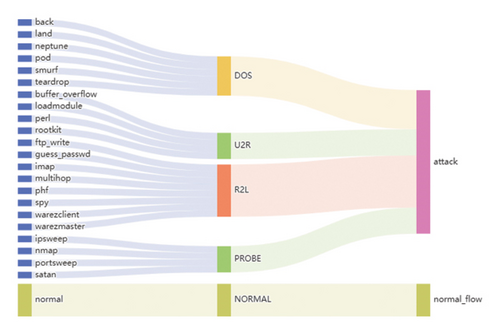
- •
Probe: This category includes activities related to surveillance and probing. These activities involve attempting to gather information about the target system or network.
- •
DoS: Attacks falling under this category aim to disrupt or disable the target host or network by overwhelming its resources or services, rendering them unavailable to legitimate users.
- •
U2R: Attacks classified as U2R involve unauthorized users attempting to gain elevated privileges, such as superuser or root access, on the local system.
- •
R2L: Attacks falling under this category involve unauthorized access to a target system from remote machines. The objective is to gain unauthorized access to the local system or network.
Excessive data dimensionality hampers effective detection capabilities. Hence, there is a need to distinguish the feature variables that have a greater impact on the classification effect. In contrast to other machine learning algorithms, RF not only distinguishes traffic classes but also enables the measurement of feature importance [41, 42].
The significance of each variable was assessed, and the variables were subsequently ranked in descending order based on their ratings. The model was trained by progressively incorporating the second, third, and subsequent important variables alongside the first one until the training was optimal.
7.2. Two-Layer Flow Detection
DoS attacks are a prevalent form of cyberattack. The DoS attack aims to overwhelm a target host by inundating it with a large volume of malicious packets, thereby consuming its available resources. Consequently, the targeted host must allocate resources to handle these pointless and anomalous packets. As a result, legitimate packets may not receive timely responses from the host, leading to increased network delays or even packet drops [43]. SYN flood and teardrop attacks are among the commonly observed types of DoS attacks.
In the present network landscape, DoS attacks stand out as the most common and constitute a significant portion of the overall number of attacks [44–46]. Unlike other forms of cyberattacks that aim to enable unauthorized access or escalate existing privileges, DoS attacks have a distinct objective of disrupting the targeted service’s functionality. Hackers employ DoS attacks to create vulnerabilities for subsequent real attacks, as the system is likely to become inaccessible following a DoS attack. It is very effective and necessary to identify DoS attacks.
-
Level 1: When confronted with unknown traffic, the detection system initially assesses whether the traffic constitutes a DoS attack. If the traffic is classified as a DoS attack, the detection system intercepts it and reports it to the RSU responsible for the domain. The RSU will then deny the request associated with the malicious traffic. On the other hand, if the traffic is not identified as a DoS attack, it proceeds to the next level of detection.
-
Level 2: After the Level 1 detection phase, the remaining traffic includes normal traffic and other types of attack traffic. These attack types may include U2R attacks, DNS spoofing attacks, man-in-the-middle (MITM) attacks, and others. In Level 2, the detection system further analyzes the retained traffic and classifies it into different categories, such as normal traffic, URLs, DNS requests, and various types of attack traffic.
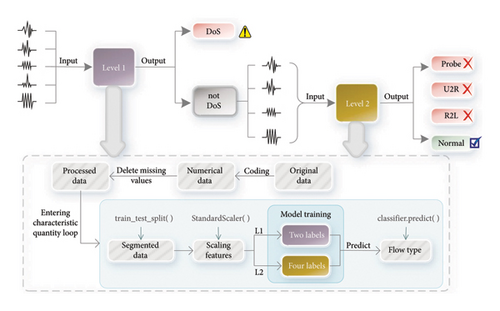
This two-layer detection paradigm aims to increase the efficiency of detecting malicious traffic. Identifying the illegal traffic in the shortest possible time is crucial in the VANET scenario.
8. Performance Evaluation
Evaluating secure communication models for VANETs involves considering multiple aspects. In this paper, the evaluation focuses on several key factors: the correctness and security of vehicle authentication and communication, computational complexity and consumption time compared to other schemes, and the efficiency of the proposed two-layer traffic detection scheme.
8.1. Correctness and Security Analysis
8.1.1. Correctness Analysis
Theorem 1. Legitimate terminals, including RSUs and vehicles, can authenticate their identities with the cloud. Terminal Lk(1 ≤ k ≤ R + P) transmit authentication information to the cloud. Cloud verifies that the equation holds, and if it does, there is a correspondence between the public and private keys of the terminal. The public key of the terminal is legitimized.
Proof 1. Since the public key PKk = SKkg0 and parameters tk = τkCpk of terminal Lk are sent to the cloud, the cloud can calculate ϑC,k = H1(IDk)g0 and based on the Lk′s IDk. According to the properties of the bilinear map, it can be concluded that
Therefore, the cloud verifies that the above equation is equivalent to verifying the correspondence between the public and private keys of the terminal. For unregistered terminals, the cloud cannot verify their identity.
Theorem 2. During the establishment process of the alliance domain, RSUk(1 ≤ k ≤ R) has the capability to authenticate the identity of the cloud. The cloud generates exclusive parameters for each RSU within the alliance domain and subsequently signs these parameters. RSU then verifies equation . If the equation is valid, the verification process is deemed successful.
Proof 2. The calculation results of yPKk = e1(PK1, PK2, …, PKk−1, PKk+1, …, PKR) and are sent to RSUk by cloud. Cloud’s public key Cpk is public in the system, and RSUk uses Cpk to verify the received messages. From the properties of bilinear mappings, we have
Therefore, RSU validation of the above equation is equivalent to verifying the identity of the “cloud.” A passed verification would indicate that the received parameters and signature are legitimate.
Theorem 3. Based on Theorem 1 and Theorem 2, RSUi(1 ≤ i ≤ R) can further negotiate the private key si of the alliance domain, and each of the RSU computes the same alliance domain session key, that is, s1 = s2 = ⋯ = si = ⋯ = sR.
Proof 3. Let us take the key negotiation process of RSUi as an example. Cloud sends parameter yPKi = e1(PK1, PK2, …, PKi−1, PKi+1, …, PKR) to the RSUi that match Theorem 1. After checking the information by Theorem 2, RSUi uses its own private key SKi to compute the private key of the federated domain. By the properties of multilinear mappings, we have
For RSUk, the received message is yPKk = e1(PK1, PK2, …, PKk−1, PKk+1, …, PKR), and the private key SKk is used to calculate the private key of the federated domain as
Similarly, we can get .
Therefore, RSUs belonging to the same federated domain can compute the same federated domain private key.
Theorem 4. The RSU and the vehicle terminals in this domain can achieve two-way authentication. Vehicle Ui,m(1 ≤ m ≤ γ) can verify the identity of RSUi(1 ≤ i ≤ R) by equation , and RSUi verifies the identity of vehicle Ui,m by equation .
Proof 4.
- 1.
The vehicle Ui,m verifies the identity of RSUi. RSUi computes ρi,m = βipki,m by using the public key of the vehicle and sends a message {PKi, Fi, ρi,m} to Ui,m. After receiving the information, the vehicle Ui,m calculates . By the nature of the bilinear mapping, the vehicle Ui,m can verify that
() - 2.
RSUi verifies the identity of vehicle Ui,m. After Ui,m verifies the identity of RSUi, it computes sigi,m = (1/(ski,m))ηi,m and sends the message {pki,m, sigi,m} to RSUi. By the nature of the bilinear mapping, RSUi can verify that
()
Therefore, the two-way authentication between the RSU and the vehicle terminal in this domain can be achieved by equations and .
Theorem 5. When a vehicle in this domain needs to send messages to a vehicle outside the domain, the RSU can verify the legitimacy of the identity of the vehicle in this domain.
Proof 5. The vehicle terminal Ui,m sends the message {RSUj, pki,m, pkj,n, Ai,m, δi,m} to RSUi, indicating that it wants to communicate with the vehicle Uj,n of the domain j. RSUi computes and verifies by the properties of bilinear mappings that
Therefore, when the local domain vehicle needs to send information to the extradomain vehicle, the RSU can verify the legitimacy of the local domain vehicle’s identity by the above equation.
Theorem 6. The vehicle terminal receives information from other domain members that can verify the authenticity of the information. The information of Ui,m is forwarded to the vehicle Uj,n, which can verify the information by the equation .
Proof 6. After Uj,n receives the message , it first verifies the integrity of the message using hash operations. Then, Uj,n verify the equation by the session public key of the federation domain and the public key of the message sender. According to the property of bilinear mapping, we get
Therefore, equation is proved. The recipient can verify the legitimacy and authenticity of the message by this equation.
8.1.2. Security Analysis
Theorem 7. RSUs not verified to cloud cannot become members in the federation domain, and vehicle terminals need to be verified to RSUs, so that they can communicate with other terminals.
Proof 7.
- 1.
The cloud system stores the PK of an authenticated RSU. Once RSUs are successfully authenticated, the cloud system calculates the parameters required and sends them to each respective RSU. Importantly, the cloud system does not record or transmit the public keys of unauthenticated RSUs. According to Theorem 3, unauthenticated RSUs cannot calculate the federated domain key using their own private keys, even if they obtain the public keys of other domains. This ensures that the security of the federated domain is maintained. If a malicious node attempts to compute the session key of the federation domain, it would be equivalent to solving the DLP, which is a computationally challenging task.
- 2.
In the process of authentication from the vehicle terminal to the RSU in this domain, the RSU and the vehicle verify each other’s identity. The verification process involves parameters η = βg0, which is used to establish secure communication. Vehicles without certification cannot obtain parameter η. The RSU can choose a new random number instead of β, when the parameter β is used for a long time or is at the risk of leakage. For intradomain communication, the parameter η is used as a component of the session key and is not available to vehicles that are not authenticated to the RSU. For interdomain communication, the information sent by the vehicle to the terminals in other domains needs to be forwarded by the RSU to reach the receiver. If the vehicle is not authenticated, the RSU does not forward the communication request message of that vehicle and does not waste resources by uploading false information to the channel.
Theorem 8. Resistant to MITM attacks. In a MITM attack, an attacker intercepts the original message and alters its content before forwarding it to the intended recipient. However, the proposed model has mechanisms in place to detect and identify maliciously tampered messages. These mechanisms help ensure the integrity and authenticity of the messages, making it difficult for attackers to successfully carry out MITM attacks.
Proof 8. Take the example of establishing communication between two vehicles Ui,m and Uj,n of different domains. Suppose an attacker launches an attack on the process of establishing communication between Ui,m and Uj,n.
- 1.
Suppose a hacker intercepts a message {RSUj, pki,m, pkj,n, Ai,m, δi,m} sent from Ui,m to RSUi on the channel, tampers the original message Ai,m with Ai,m , and sends the tampered message {RSUj, pki,m, pkj,n, MAi,m, δi,m} to RSUi. After receiving the message, RSUi calculates and verifies . From Theorem 5, it follows that
() -
As a result, RSUi can correctly identify false information and achieve resistance to MITM attacks.
- 2.
Suppose the hacker intercepts the message sent by RSU to RSUj on the channel and tampers the original message pki,m to Mpki,m. The message is sent by the hacker to RSUj, and RSUj forwards the message to Uj,n.
Uj,n implements the MITM attack according to two ways: (a) using hash operations to verify the integrity of the information. Uj,n computes and confirms that hj,n ≠ hi,m. Uj,n refuses to establish communication. (b) Using the reverse computational difficulty assumption. From Theorem 6, Uj,n verifies the following equation:
Authentication fails and Uj,n refuses to establish communication.
Therefore, the receiver Uj,n can correctly identify false information and achieve resistance to MITM attacks.
8.2. Communication Performance Evaluation
8.2.1. Computational Complexity Analysis
Certain contemporary communication schemes rely on simplistic operations such as exclusive OR (XOR) or hash, which may offer relatively better performance. However, cryptographic schemes built upon bilinear and multilinear mappings offer the potential for more advanced security attributes and capabilities. The advantage of bilinear mappings lies in their foundation on mathematically complex problems that have undergone extensive scrutiny within both computer science and cryptography disciplines. Consequently, they are regarded as significantly resilient to attacks and possess robust mathematical security. Furthermore, bilinear mappings enable the implementation of more sophisticated cryptographic functions, including attribute-based encryption and digital signatures, which cannot be achieved using XOR and hashing operations.
Let MtP be the map-to-point hash operation, GeZ be the group G elements to the power of the domain Z elements, bm be the bilinear map operation, paecc be the addition operation on elliptic curves, ZeZ be the domain Z elements to the power of the domain Z elements, mul be the scalar multiplication operation, and hash be the ordinary hash operation.
Tables 2 and 3 analyze in detail the computational aspects of this paper and literature [14, 47] in the resource-constrained environment. Table 2 focuses on the computations performed on the sender side, while Table 3 outlines the computations required on the receiver side. It is important to note that operations consuming less time, such as heterogeneous and addition operations, are not included in the statistics since their time consumption is considered negligible.
| Authentication | Communication | Total | ||
|---|---|---|---|---|
| Literature [47] | — | 1 paecc + 1 mul + 1 hash | 1 paecc + 1 mul + 1 hash | |
| Literature [14] | 1 MtP + 1 GeZ + 1 bm + 1 paecc + 1 hash | 1 MtP + 2 bm + 3 ZeZ + 1 hash | 2 MtP + 1 GeZ + 3 bm + 3 ZeZ + 1 paecc + 2 hash | |
| Our | Intra | 1 paecc + 1 hash | 3 hash | 1 paecc + 4 hash |
| Inter | — | 1 paecc + 2 mul + 3 hash | 1 paecc + 2 mul + 3 hash | |
| Authentication | Communication | Total | ||
|---|---|---|---|---|
| Literature [47] | — | 2 paecc + 1 hash | 2 paecc + 1 hash | |
| Literature [14] | 1 MtP + 1 GeZ + 1 bm + 1 paecc + 1 hash | 1 MtP + 2 bm + 3 ZeZ + 1 hash | 2 MtP + 1 GeZ + 3 bm + 3 ZeZ + paecc + 2 hash | |
| Our | Intra | 1 paecc + 1 hash | 3 hash | paecc + 4 hash |
| Inter | — | 2 bm + paecc + 4 hash | 2 bm + paecc + 4 hash | |
In contrast to the communication schemes proposed in the literature [14, 47], which are the same for any two vehicles, this paper distinguishes vehicle communication based on two cases. In the first case, vehicle terminals within the same domain utilize an intradomain communication scheme, while in the second case, terminals from different domains employ an interdomain communication scheme. It is worth mentioning that communication vehicles in close proximity generate fewer computational requirements compared to long-range communication scenarios.
Observing Table 2, the authors of literature [47] do not design the authentication process. Instead, after obtaining the public and private keys, the sender sends the message to the receiver, who verifies the message. In literature [47], the sender uses 1 paecc, 1 mul, and 1 hash operations. Compare to the intradomain scheme in this paper, the authors of literature [47] use 2 hash and 1 mul. Compared to the interdomain scheme in this paper, the authors of literature [47] use 3 hash and 1 mul. In our intradomain scheme, the computation on the sender side is mainly spent on the authentication process, which is the consumption incurred to verify the sender’s identity. In our interdomain scheme, the authentication process is shown in the authentication and communication process to the RSU, where the sender needs only 1 paecc, 2 mul, and 3 hash operations to make a secure communication with another terminal. The sender in the literature [14] uses a variety of operations, in addition to the paecc, mul, and hash operations mentioned above, and in addition, uses the MtP, GeZ, bm, and ZeZ operations, which are not used by the sender in either this paper or the scheme in the literature [47].
Let us observe Table 3. In the literature [14], the computation on the receiver side is the same as on the sender side, because the negotiation of the key between the two sides requires the receiver side to send the information to the RSU in the same way. After the RSU verifies the vehicle’s identity to the trusted agency, the parameters used to calculate the communication key are sent to the sender and the receiver. In the scheme proposed in [47], the receiver uses 2 paecc and 1 hash operations to authenticate the sender and calculate the communication key. The receiver uses 1 more paecc operation and no mul operation than the sender. In our intradomain scheme, the computation of the receiver is equal to the sender; in our interdomain scheme, the receiver uses 2 bm and 1 hash operations and 2 mul operations than the sender.
8.2.2. Time Analysis of Calculation Consumption
The time consumption of the operations used in Tables 2 and 3 was tested with the JPBC cryptographic library (JPBC-2.0.0 Version) in the Java programming language on Windows 10 operating system using an Intel(R) Core(TM) i5-8500 CPU @ 3.00 GHz processor. The JPBC is a pairing-based cryptography library with high flexibility and functionality. It is used in the experimental part of many cryptography papers [48–50]. This paper employs the Type A curves from the JPBC library. Type A curves are commonly utilized in constructing cryptographic schemes related to bilinear maps, which involve the finite field Zq and the group G. Generally, the larger the bit-length r bit of the order in Zq, the larger the element space in Zq, and the larger the bit-length q bit of the order in the group G, the more difficult it is to attack the cryptographic algorithms based on the group G. However, this also entails higher computational costs and storage requirements. Due to the limitations of the experimental conditions, we set r = 128 and q = 512. Therefore, such values enable research under the existing experimental conditions while ensuring the security and operability of the cryptographic algorithms to a certain extent.
Let TMMtP be the time consumed of MtP operation, TMGeZ be the time consumed of GeZ operation, TMbm be the time consumed of bm operation, TMpaecc be the time consumed of paecc operation, TMZeZ be the time consumed of ZeZ operation, TMmul be the time consumed of mul operation, and TMhash be the time consumed of hash operation. The single consumption times of the above operations are shown in Table 4.
| Operation | Consumption time (ms) |
|---|---|
| TMMtP | 19.9310 |
| TMGeZ | 6.3454 |
| TMbm | 3.7263 |
| TMpaecc | 0.0345 |
| TMZeZ | 0.0109 |
| TMmul | 0.0003 |
| TMhash | 0.0002 |
Table 5 compares the computational time consumed by the schemes during the communication process. The literature [14] takes the longest time, and it is because one MtP operation and one GeZ operation are used. The MtP operation requires mapping a message to a point of an elliptic curve, which means substituting the message as an x-coordinate into the elliptic curve equation and calculating the corresponding y-coordinate. This computation process is much slower than the traditional hash operation, and therefore takes longer. GeZ operation is the second most time-consuming after MtP operations. The consumption time of the literature [47] is 0.0338 ms less than our intradomain scheme, 7.4194 ms less than our interdomain scheme, and 114.8036 ms less than the literature [14]. However, in the scheme of [47], there is no process of mutual authentication of each other’s identity between the sender and the receiver, as it is vulnerable to impersonation attacks.
The intradomain communication scheme in this paper mainly uses paecc and hash operations, and a total computation time of 0.0704 ms is consumed by the receiver and the sender. It is not necessary to use bilinear mapping operations to authenticate messages, because there is a mutual authentication process between the communicating parties. The DRKey is added to the key, which makes the communication key dynamic and random. Therefore, the security of our scheme is guaranteed. Our interdomain communication scheme consumes a total of 7.5236 ms and uses 2 bm, 2 paecc, 2 mul, and 7 hash operations, where 2 bm are used to verify that the sender is a verified terminal by RSU. We use hash operations to verify that the information has not been maliciously tampered with by the attacker. The scheme proposed in this paper does not use time-consuming operations taking full account of security.
8.3. Performance Analysis of Flow Detection
8.3.1. Experimental Setup
This part of the experiment was conducted using Jupyter (Python Version 3.9.12) on a Windows operating system, utilizing a Core i7-8565U CPU with 16 GB of RAM and a clock speed of 1.99 GHz.
Neural networks and deep learning have gradually evolved on the basis of machine learning. Therefore, it is of great significance to study machine learning algorithms. Furthermore, compared to the various techniques derived later, the analytical features and analysis process of machine learning are clear and explainable [51]. We consider testing the proposed method on four machine learning algorithms: support vector machines (SVMs), RF, logistic regression (LR), and decision tree (DT). SVM, which demonstrates excellent performance in high-dimensional spaces, is particularly well-adapted to handling complex datasets. RF exhibits remarkable accuracy and typically provides highly precise prediction results for large- scale datasets. LR, characterized by low computational complexity, is fast and consumes minimal storage resources during the classification process. The structure of the DT model is intuitive, rendering it easy to understand and interpret.
In this paper, the hyperparameters are tuned and optimized using the grid search (GridSearchCV) of the scikit-learn library. A 5-fold cross-validation (i.e., cv = 5) with scoring method “accuracy” is used to perform the task in parallel using all available CPU cores on the computer (i.e., n_jobs = −1). It divides the range of hyperparameter values into grid points and then performs an exhaustive search for all combinations of hyperparameters at these grid points. The test ranges are chosen after several experiments, and the test ranges and results are displayed in Table 6. In the SVM, the penalty coefficient C is 50 in the first stage and 150 in the second stage. RF uses “entropy” to measure dataset’s purity in both stages, with the maximum depth of trees being 30. The number of DTs in the forest is 50 in the first stage and 75 in the second stage. In the LR model, the penalty parameters are 1 and 100, respectively, and the regularization parameter is of the “l2” type. In the DT model, the maximum depth of trees is 30 and none, respectively; the minimum number of samples required for each leaf node is 1 and 5, respectively; and the minimum number of samples required for node splitting is 2. The hyperparameters not mentioned above are set to default values.
| Parameter name | L1 | L2 | |||
|---|---|---|---|---|---|
| Test range | Result | Test range | Result | ||
| SVM | C | [0.1, 1, 10, 50, 100] | 50 | [10, 50, 100, 150, 200] | 150 |
| RF | Criterion | [“Gini,” “entropy”] | Entropy | [“Gini,” “entropy”] | Entropy |
| max_depth | [None, 10, 30, 50] | 30 | [None, 10, 30, 50] | 30 | |
| n_estimators | [25, 50, 75, 100, 125] | 50 | [10, 25, 50, 75, 100] | 75 | |
| LR | C | [0.01, 0.1, 1.0, 5] | 1 | [1, 10, 100, 500] | 100 |
| Penalty | [“l1,” “l2”] | l2 | [“l1,” “l2”] | l2 | |
| DT | max_depth | [None, 10, 30, 50] | 30 | [None, 10, 30, 50] | None |
| min_samples_leaf | [1, 5, 8, 10] | 1 | [1, 5, 8, 10] | 5 | |
| min_samples_split | [2, 5, 8, 10] | 2 | [2, 5, 8, 10] | 2 | |
A training set of 60,000 items and a test set of 30,000 items were randomly selected from the dataset. The data distribution is shown in Table 7.
| Class | Training dataset | Testing dataset | ||
|---|---|---|---|---|
| Num | Percentage (%) | Num | Percentage (%) | |
| Normal | 21,715 | 36.19 | 10,434 | 34.78 |
| Probe | 4107 | 6.84 | 2377 | 7.92 |
| DoS | 33,000 | 55.00 | 15,650 | 52.17 |
| U2R | 52 | 0.09 | 39 | 0.13 |
| R2L | 1126 | 1.88 | 1500 | 5.00 |
8.3.2. Analysis of Detection Performance
The importance of variables is determined by using the RF algorithm. The features are ranked based on their weights, with higher weights indicating a higher importance. Based on this ranking, the optimal number of features needed to achieve the best classification performance is determined, and the results are presented in Table 8. To evaluate the performance, the classification results of the original machine learning algorithms (e.g., SVMs, RF, LR, and DT) are compared with the proposed two-layer traffic detection scheme. The original machine learning algorithms are referred to as “ORIGINAL,” while the proposed two-layer traffic detection scheme is referred to as “OUR.” Table 9 illustrates the effectiveness comparison of the ORIGINAL and OUR methods in detecting the five types of traffic.
| Algorithm | Features’ number | ||
|---|---|---|---|
| ORIGINAL | OUR | ||
| SVM | 5 | L1 | 36 |
| L2 | 5 | ||
| RF | 20 | L1 | 17 |
| L2 | 39 | ||
| LR | 33 | L1 | 33 |
| L2 | 31 | ||
| DT | 22 | L1 | 28 |
| L2 | 4 | ||
| Algorithm | DoS | Normal | Probe | U2R | R2L | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ORIGINAL | OUR | Change | ORIGINAL | OUR | Change | ORIGINAL | OUR | Change | ORIGINAL | OUR | Change | ORIGINAL | OUR | Change | |
| SVM | 15,546 | 15,625 | +79 | 10,293 | 10,298 | +5 | 2215 | 2353 | +138 | 0 | 0 | / | 0 | 157 | +157 |
| RF | 15,551 | 15,632 | +81 | 10,246 | 10,280 | +34 | 2373 | 2374 | +1 | 0 | 0 | / | 20 | 178 | +158 |
| LR | 15,623 | 15,629 | +6 | 10,224 | 10,178 | −46 | 2331 | 2355 | +24 | 14 | 17 | +3 | 225 | 393 | +168 |
| DT | 15,496 | 15,642 | +146 | 9577 | 10,348 | +771 | 2353 | 1901 | −452 | 0 | 0 | / | 140 | 0 | −140 |
In the proposed scheme, the detection of DoS attack traffic is carried out in the first phase. Table 9 illustrates that all OUR algorithms show improved performance in detecting DoS attacks compared to the ORIGINAL approach. Among them, OUR DT algorithm shows the most significant enhancement. Compared to the ORIGINAL, OUR DT algorithm correctly identified 146 DoS flows, and only 8 DoS flows were not identified. Followed by the fact that our RF algorithm and SVM algorithm detected 81 and 79 more data streams, respectively, which means that the difficulty of the enemy’s attack is increased. As for the ORIGINAL LR algorithm, it has already achieved a high level of accuracy with 15,623 correct classifications, which could explain the relatively limited improvement observed in OUR LR algorithm.
The second phase of the proposed scheme focuses on detecting normal, probe, U2R, and R2L traffic. Regarding the detection of normal traffic, OUR DT algorithm exhibits a significant improvement. Specifically, OUR DT correctly identifies 10,348 instances of normal traffic, making it the algorithm with the highest number of correctly classified normal traffic instances. However, OUR LR algorithm shows a small degradation in detecting normal traffic compared to the ORIGINAL approach, as it misclassifies a small number of normal instances as attack vectors. OUR SVM and RF algorithms demonstrate a slightly improved detection performance for normal traffic. In terms of detecting probe traffic, there is a minor improvement observed in OUR LR and RF algorithms, while OUR DT algorithm experiences a remarkable decrease in performance. SVM improved the most, detecting 138 more probe flows. As for the detection of U2R traffic, OUR algorithm shows a slight improvement in LR, and no change in SVM, RF, and DT algorithms. In the case of R2L traffic, both OUR SVM, RF, and LR algorithms exhibit improved detection performance. However, it is worth noting that OUR DT algorithm is not as effective as the original DT in the second detection stage.
8.3.3. Analysis of Detection Time Consumption
In the VANET application scenario, which has great potential, the requirements for detection efficiency are demanding. When the terminal is communicating, the detection module’s efficiency needs to match the speed of message delivery. The detection system must intervene before the receiver receives the hazard information. Therefore, it is necessary to analyze the detection consumption time of the proposed model.
The models need to be trained before they can be tested. In this paper, we compare the time overhead in two aspects: training time and testing time. Since the proposed scheme is divided into two phases, the elapsed time should be the sum of the time required for both phases. Table 10 provides a detailed description of the training time and testing time for this scheme (data with “0” in the table do not really take no time but take so little time that they are almost negligible.)
| Algorithm | Phase | Training time (ms) | Testing time (ms) | Total training time (ms) | Total testing time (ms) |
|---|---|---|---|---|---|
| SVM | L1 | 907 | 353 | 2210 | 748 |
| L2 | 1303 | 395 | |||
| RF | L1 | 656 | 51 | 1455 | 140 |
| L2 | 799 | 89 | |||
| LR | L1 | 1139 | 3 | 1422 | 5 |
| L2 | 283 | 2 | |||
| DT | L1 | 126 | 0 | 132 | 0 |
| L2 | 6 | 0 | |||
We still compare the training time and testing time of the ORIGINAL algorithm with the proposed two-layer traffic detection scheme. Figure 7 presents the comparison of training time consumption. Our four algorithms in the proposed scheme significantly reduce training time compared to the original. The DT algorithm reduces it by 69 ms, the RF algorithm by 107 ms, the SVM algorithm by approximately one-third, and the LR algorithm by 75.89% of the original.
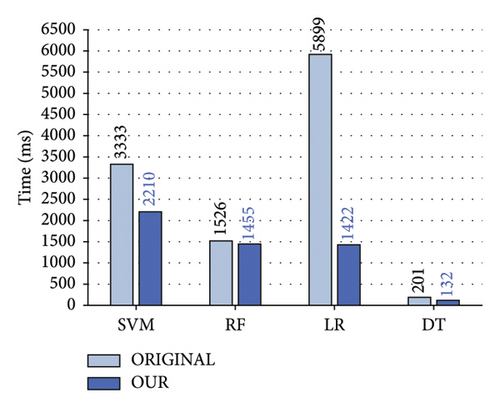
Figure 8 illustrates the comparison of testing time. The proposed two-layer detection scheme significantly reduces testing time for the four original machine learning algorithms. The most notable improvement is observed in our SVM algorithm, reducing test time from 2217 to 748 ms. Our RF algorithm’s testing time is reduced to 43.09% of the original. For the LR algorithm, our scheme saves 11 ms, and for the DT algorithm, its detection time is almost negligible.
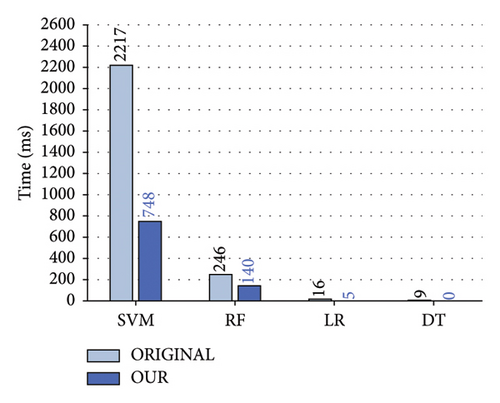
8.3.4. Summary of Detection Function
The proposed two-layer traffic detection scheme shows a significant reduction in elapsed time, including model training and traffic detection, while also slightly improving detection performance. The number of correct classifications for each algorithm is summarized in Table 11. In the first stage, all algorithms demonstrated improved detection performance, with the DT algorithm achieving the highest detection rate of 99.95% among the four. In addition, the DT algorithm showed favorable results in the detection time analysis, requiring only 126 ms for training and negligible testing time. Therefore, the DT algorithm can be used in the first phase to detect DoS attacks in the VANET scenario.
| Algorithm | ORIGINAL | OUR | Change |
|---|---|---|---|
| SVM | 28,054 | 28,433 | +379 |
| RF | 28,190 | 28,464 | +274 |
| LR | 28,417 | 28,572 | +155 |
| DT | 27,566 | 27,891 | +325 |
In the second detection phase, the DT algorithm performs significantly worse than the other algorithms and is therefore not recommended in the second phase of detection. The SVM, RF, and LR algorithms have different detection performances for different traffic. However, an overall analysis reveals that the detection performance is on the rise. The LR algorithm, as the algorithm with the highest number of correct classifications, takes 283 ms to train the model and only 2 ms for testing. Therefore, the LR model can be considered in the second stage of detection to distinguish the attack types other than DoS attacks.
9. Conclusion
Aiming at the security problems in the VANET scenario, a multidomain secure communication and traffic detection model is proposed. This model uses a key self-verification algorithm to replace the authoritative central distribution of keys in traditional schemes. In addition, two types of communication, intradomain and interdomain, are designed to minimize communication overhead. Furthermore, a two-layer traffic detection approach is introduced, testing four machine learning algorithms that effectively reduce training and testing time for the model. In the future, our team will continue to improve the existing models, optimize them for specific machine learning algorithms, and implement the proposed models in real VANET scenarios. We are committed to coming up with new proposals for VANETs.
Conflicts of Interest
The authors declare no conflicts of interest.
Funding
This work was supported by the National Natural Science Foundation of China (Grant no. 61971380), the Key Technologies R&D Program of Henan Province (Grant nos. 242102211078, 252102211089, 252102211112, 242102211098, and 242102210135), the Science and Technology Research Program of the Chongqing Municipal Education Commission (Grant no. KJQN202300617), and the research funding of the Key Laboratory of Big Data Intelligent Computing (Grant no. BDIC-2023-B-006).
Open Research
Data Availability Statement
The JPBC open-source library is used. It has been labeled in the paper. The experimental environment and the experimental data used are all provided in the paper. The experimental results of the paper can be reproduced through the already labeled code sources and the experimental environment and data provided in the paper.




