Relay Node-Based Routing Algorithm for Reducing Latency in Industrial Mobile Communication Network
Abstract
Mobile network nodes perform time transfer during data packet performance in an asynchronous manner. Network nodes get packets for transmission from node sensors that reject the demands of node attackers. When packet loss occurs unexpectedly due to a network removal, it is exceedingly difficult to detect assaults and time forwarding. Attack detection accuracy deteriorates, and packet loss rates rise. A strategy for node mobile intermediate that gets over attacks that identify the forward choosing is provided for improved data forwarding. Network performance is completely damaged by specific attacks, such as communication processes that degrade or lose packets. The algorithm’s architecture ensures that the best nodes are chosen for relaying and that transmission packets that do not drop are declined. To enable the node and create an effective path routing, a process is executed. Decreasing the amount of packet loss and increasing attack efficiency are being identified.
1. Introduction
The mobile network accepts the user in its environment such as the performance of the protected monitor network, irregular behaviour to evade the worry protection, and lack of middle coherence in the middle. As a result, distinct layers of intruders may alter in a mobile environment. In a mobile network, there are many layers for available intrusions [1]. While nodes are malfunctioning due to intrusions at the layer linking the data, denial of communication is misbehaving at the application layer. Intruders use a variety of techniques, such as dropping poles, withholding connections, black holes, spoofing connections, and Sybil, to determine where they are in the network and how to get in [2].
When an intruder drops data, the mobile environment network is under attack. When an intrusion packet was dropped, nodes that were relaying traffic were identified in order to focus on abnormal nodes [3]. As a result, communication is via terminal means intruder, and the entire piece of information is lost [4]. Node specification from packet data is the broadcast node sender. A node that should be malicious from the packet loss technique is created by the mobile environmental network problem. They argue that the count sequence objective is larger to contain the intruder issue performance [5]. According to node intruder resources, with a higher load, communication should be disrupted because of resource overload, which causes packet traffic to transmit from the initiate’s node sender. The issue of malicious behaviour that could reject the selected issue of an invader grey hole or target network-specific packet data, that is, the part picked at random, was removed from all packet sharing [6]. To prevent various intruders from being identified by lost packets, intruders for a group could be considered an intruder’s characteristic [7].
To break the oath that is used and contains independent loops, a multiple data routing strategy is available. The method is to employ the reliable communication route that provides an intrusion loss packet [8]. According to the means record, the ambient mobile network, which was the layer of the network layer known to identify the intrusion that caused a packet loss attack, was avoided. The drop packets were used to avoid opportunities from node intruders with paths that were fully recognised by the node network during the communication period [9].
Regular topological network changes could cause the best possible routing path to become ineffective immediately [10]. The strong network should be designed with a built-in mobile routing network. Even though the environmental network was based on information for global requirements, there is no middle structure in the network because there are no adjacent operations that can be included in this design [11]. As we have already indicated, the needs of distinct groups merged with the way the nodes functioned. It is simple to control the node entity through packet organisation with a maximum range that classified the complete ant colony. To fully realise one’s potential, nodes of resources were present throughout the entire communication process [12].
The remaining sections of the paper are as follows. Section 2 provided related works. Section 3 provides enhanced improved data forwarding scheme that contains information about a method that assists in node target from the sender in which concentrates the attack on specific forwarding nodes. Section 4 mentioned simulations of performance analysis and result analysis with various parameters. The research’s conclusion and the research’s future work are discussed in Section 5.
2. Related Work
Node terminals developed by Wu et al. [13] were based on social network characteristics that specifically take into account mobile social network delay tolerance. Assume that the mobile ad hoc protocol routing is complete for node target and node source among the path communication. It adapted with amazing skill to the way that logical dynamic MSN were dealt with using an optimization colony based on algorithm routing. The MSN trait of being a social network is present. Data forwarding and updating strategies were used in the ACOMSN methodological design.
According to Quang and Kim [14], the wireless sensor network in industries for information was improved with real-time performances of real-time gradient routing. The suggested algorithm for routing is based on the two-hop information, which is determined by the number of hops with a certain distance to the sink, and routing velocity of two-hop that has been adopted. Additionally, computing complexity and energy consumption result in a reduction in the scheme’s control acknowledgment.
Zhang et al. [15] found a solution to the energy balancing issue, and WSNs are highly essential routing algorithms that ensure the quality of service while being energy-efficient. Data categories and defined priorities were used to categorise the industrial training. Consumption energy has the equilibrium that set node forwarding candidate that establishes and the purpose of effective communication cannot be with common data and timely reliable with sink node that sent data sensing was crucial in industries. When the data was high in exhibiting simulation results, the data kinds were more trustworthy in real-time transmission.
According to Chourasia and Boghey [16], many nodes were created as a group with the creation of the MANET. While interacting with all those who have minimal resources, the current node in MANET is malevolent, degrading the network performance in a dynamic way, and this affects routing performance. Continually hostile nodes cause the neighbouring response node to redirect all requests. The routing method, which is in charge of node intermediates, continues movement. Attacks against the security of the suggested method were made in the network node by malicious packet dropping. The information or data that linked the sender and the receiver together to discover an idea was done by an attacker who would then suggest a viable scheme. Receivers from the sender were not available with enough activity to spot a malicious node neighbor’s intermediate. It reduces dropped and received data to enhance intended routing security in network data.
According to Sangaiah et al. [17], a boost in productivity and duty was focused on the work of supervising factories with a lot of activity. With node sensors’ limited energy supply, these networks are essential to ensuring optimal energy utilisation. The goal of coverage and tracking is to consume energy efficiently. Sensors were notified by cluster head nodes, and their weights were calculated. The predefined weight has a maximum connection to the cluster head route that sends signals in the network.
According to Fang et al. [18], the WSN industries are based on computer fog and use unique wireless network sensors which provide reduced latency transfer of information, quick resource scheduling, and real-time control. Internal attacks present a significant security challenge for the network distribution. The typical security measures used in different attacks involve trade-offs between security and information convergence, which is necessary to fulfill energy consumption and transmission requirements. Energy consumption and performance transmission were balanced in order to introduce the concept of making grey decisions. Secure routing based on management confidence, reliable nodes, and the trade was suggested for effective selection.
According to Khudayer et al. [19], emergency operations and environmental protection are two areas where humans support MANET, which has set the way for swiftly advancing wireless industrial communication. The topology of the network changes as a result of a MANET source routing problem, and the discovery of request routing increases the frequency of broken links. Researchers suggested ZRDM and LFPM as two techniques for source routing that improve on-demand. In order to avoid the route that is intended for LFPM, node mobility that generates breakage forces the route request flooding to aim for ZRDM. Performances of the processes for which we suggested the experiment, such as the dynamic source routing protocol, are well known.
According to Luo et al. [20], the routing protocol which is based on WSN concerns a significant portion of energy-saving optimization; the availability of sensor nodes with the most factual battery power is limited. Network queue relay one-dimensional data that minimises energy usage and maximises network lifetime. To enable the most energy-saving opportunistic routing, energy residual must be minimal in comparison to the node’s cost and power.
3. Overview of the Proposed Scheme
The unsequenced node of mobile has the period of communication as its intrinsic property. The network environment in the node receives the packet data from the node sender in order to reject the node attacker’s intention. The packet data that transmits node instance for each time is of higher quality than the packet data that are lost. Environmental network mobile cannot easily handle the intruder kind, as the node among the communication that initiates while packet data drops erratically. When using this technique, the rate of packet drop and the effectiveness of attacks were decreased.
The method we suggested in this paper, known as enhanced improved data forwarding, is employed for environmental node relaying to the forward selective through categorization. Intruders may refuse the transmission of packets in the node operation when a network characteristic is completely damaged, such as when a packet is dropped. As long as there will be no packet data loss and communication is not refused, the built-in enhanced efficient relaying node algorithm selections were permitted. The efficient routing path was designed, and packet transmission was carried out to authorise the node. Rate drop packets were reduced, and the efficiency of the detection was improved.
The suggested enhanced improved data forwarding method is shown in Figure 1. Every data had to be measured by the range for the transmission packet node, and the packet transmission time was limited to packets that could be received or sent with a particular quantity. Selective forwarding in a network environment in which node destinations were sent to node sources for packet sharing is refused in advance with node attacker. The standard and intruder forwarding selection that categorise the employed method of enhanced improved data forwarding were presented in the environmental network in relaying node. The enhanced effective relaying node selection algorithm’s optimal node is selected for the routing. The efficiency of detection has increased while the rate of packet drops has decreased.
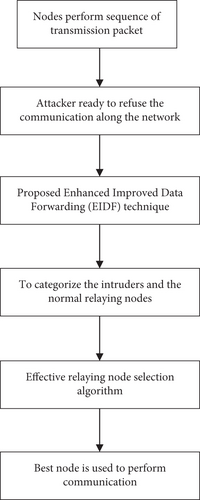
3.1. Sequence of Packet Transmission by Node
The table routing maintained the details and packet requests for the value of the count node. They are similar to the count sequence, which is equal, and they are also similar to the range of the hop count and the routing table that does not modify the relaying node. It altered the path recently due to the weather, path routing has good intentions with it, and sharing packet data is to guide speed. In the network, the node sender in the direction with packet reply transmits and produced the node target that agreed while it occurs in the same condition. The details and packet request value of the count node are recorded in the table routing. The hop-count range and count sequence, as well as the routing table that does not change the relaying node, are likewise identical. The recently changed path is good with sharing packet data speed to the point. The network’s node sender consented to broadcast packet replies in the direction of the created node target while the situation persisted.
3.2. Enhanced Improved Data Forwarding (EIDF) Technique
Count series verification from the table path, count node forwarding data, count node attacker forwarding selective, and count packet reply or request that verifies the node relay. Value forwarding data is focused on the node relaying, and table routing is to preserve the value that counts series to equate the count of series. Value forwarding data is the least amount of data with a table based on the value forwarding data packet, rate forwarding data comparable to an access route backward, or an access route forwarding data modifier to the relaying node following. However, node target and node sender among the identified recent routes are equivalent to a packet replay or request. The maximum rate forwarding data table is similar, and the most recent packet requests that lose data typically go towards the target node. When a packet requests retransmission and a node is replaying it, the network’s routing database does not establish that path access. The node quality and count series in table routing are comparable to the current route. Rate the least forwarding data with a packet reply that offers valuable forwarding data to confirm the node’s answering. Data packet sharing is the method utilised in this, and the path was well-organized [21–34].
-
Algorithm 1: Algorithm for enhanced improved data forwarding (EIDF) technique.
-
Step 1: in the path different relay node analysis
-
Step 2: relay node which is chosen
-
Step 3: packet transmission with initial sequence
-
Step 4: trusted node is verified
-
Step 5: if {node == trust}
-
Step 6: communication allocation
-
Step 7: else
-
Step 8: if {node == Attacked}
-
Step 9: communication decline
-
Step 10: data packet loss
-
Step 11: for routing different node search
-
Step 12: end if
-
Step 13: end for
3.3. Enhanced Efficient Relaying Node Selection Algorithm
Upon accepting a specific transmit packet awareness, the position of the broadcast was previously with the weather and on the focused node source that we observed. Data packets are retransmitted with the node in order to list single hop packet awareness locations of location node sources that we added with each node, as well as to determine whether one count with hop packet awareness locations of source node addresses that add with each node. With a dual list and a two-hop count, packet awareness locates addresses of node sources that are added with other nodes which accept packets. With the sender node, a single hop was not previously planned. The sum for the record of the source node’s two hops includes the data packets that were shared with their single node’s neighbour but should have been shared with the single node itself. During the communication period, packet data will not be dropped thanks to the routing’s efficient node relaying.
-
Algorithm 2: Algorithm for enhanced efficient relaying node selection.
-
Step 1: rate of forwarding data is monitored
-
Step 2: selection node is efficient for each one
-
Step 3: if {relaying node == efficient}
-
Step 4: node efficient was selected
-
Step 5: path is constructed
-
Step 6: else
-
Step 7: if {relaying node!= efficient}
-
Step 8: they do not choose the node efficient
-
Step 9: end if
-
Step 10: efficient detection increases, and the rate of loss reduces the packet
-
Step 11: end for
Path routing in communication nodes relaying allows for the building of an improved efficient node selection technique. Due to the attacker’s ability to forward the avoid option, there was a significant loss of data packets during the conversation interval. Minimum packet drop rate and effective detection are improved.
3.3.1. Packet ID
Information about the mobile node contains each packet ID. The table of every node in the routing is stored, and the performances of mobile node are communicable, as we observed.
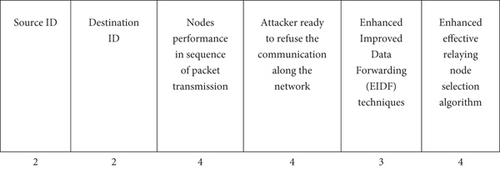
Figure 2 depicts the enhanced improved data forwarding (EIDF) method that we suggested and illustrated to format the packets. Each field of the ID node’s destination and source carried 2 bytes. The transmission packet carrying the third performance node’s sequence was 4 bytes long. Four bytes were taken from the fourth one’s field. The network along with communication was equipped to prevent attackers, and the communication along with packet transfer prevents the attack with selective data forwarding. Three bytes were occupied in the fifth place, and the enhanced imposed data forwarding (EIDF) technique, route communication, offers the free attack. In the last field, four bytes were taken with the algorithm of enhanced efficiency relying on node selection.
4. Performance Evaluation
4.1. Simulation Model and Parameters
Network simulator tool (NS 2.34) with simulated scheme enhanced improved data forwarding (EIDF). Simulation is based on a simulation time of 40 milliseconds for the region of 1160 meter × 920 meter square which has been placed with mobile ad hoc nodes 100. Network at various speeds among random manner with the mobile node. During this time, communication overloads the packet with a constant speed that provides constrain bit rate (CBR). Path routing is a free attack selectively obtained using the protocol demand on distance vector routing. Table 1 represents the estimation of the simulation setup.
| No. of nodes | 100 |
|---|---|
| Area size | 1160 × 920 |
| Mac | 802.11 g |
| Radio range | 250 m |
| Simulation time | 40 ms |
| Traffic source | CBR |
| Packet size | 512 bytes |
| Mobile model | Random waypoint |
| Protocol | AODV |
4.1.1. Simulation Result
Figure 3 represents the scheme proposed for enhanced improved data forwarding (EIDF). It is compared with the attack forwarding data section to remove and detect the use of methods that exist in RA [13] and NIDS [16].
Node destination from the source node was a path-free routing to attack which provided the emission of attack that was used for the identification of EIDF in it. Node source from the packet reply has been provided as a free node of attack. The node behavior is observed to construct the algorithm of enhanced effective relaying node selection and node best selection. Rate of packet drop is minimized and efficient detection is increased.
4.2. Performance Analysis
In NS 2.34, graph X is used as performance metrics that follow the analysis of the simulation.
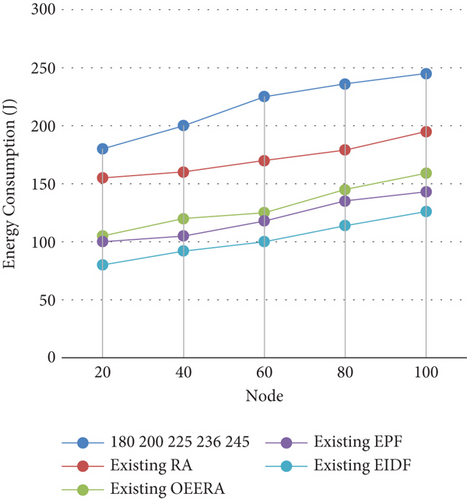
4.2.1. Energy Consumption
4.2.2. Packet Delivery Ratio
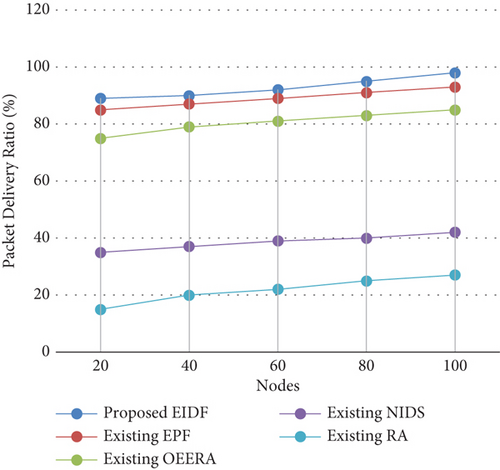
4.2.3. End-to-End Delay
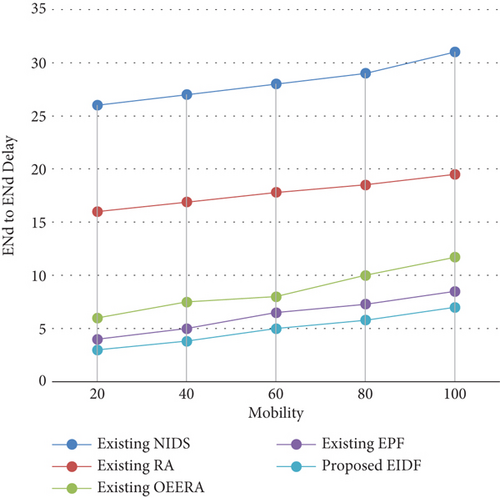
4.2.4. Network Lifetime
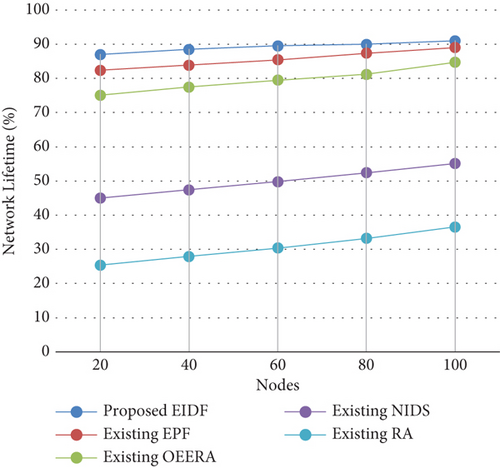
4.2.5. Packet Drop Rate
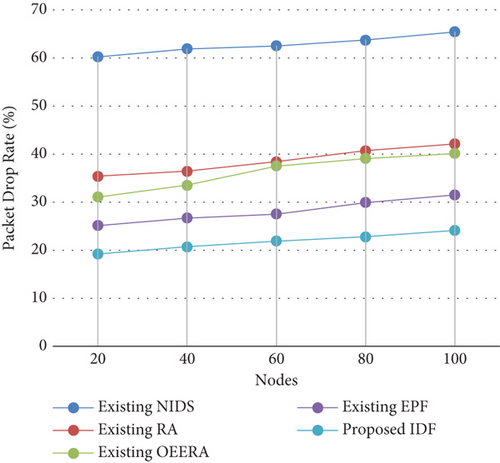
4.2.6. Detection Efficiency
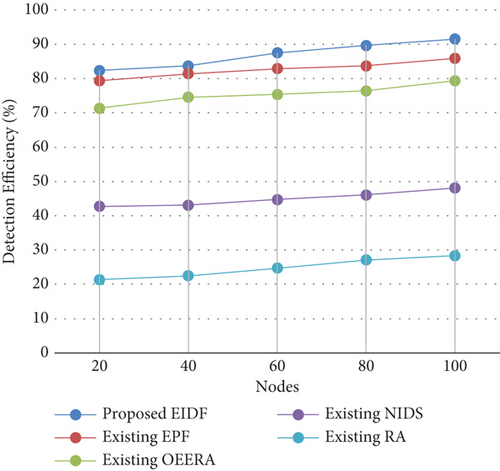
5. Conclusion
The mobile node acts as an intermediary in the mobile network by communicating and rejecting node intrusions. The malicious node operations cause packets to be sent with higher-quality data loss. It was difficult to reject and identify the detrimental communication which should be spread farther with maximum packet loss rate and minimised attack detection efficiency. The approach suggested that enhanced improved data forwarding protects against intrusions that previously discovered the selective forwarding on mobile nodes. In order to hurt invaders, a routing network that reduces or drops packet sharing is necessary. To offer a hint to the constructed scheme that is effective, enhanced relay node that is efficient does not lose packets and rejects the process. Construction route is effective, and communication is a procedure that is performed to carry out the node’s authorization. Rate packet loss is reduced, and detection attack efficiency is raised. The work focused on various parameter analyses of the MIMO-based fuzzy approach.
Conflicts of Interest
The authors declare that they have no conflicts of interest.
Open Research
Data Availability
The datasets used and/or analyzed during the current study are available from the corresponding author on reasonable request.




