Research on Contactless Identification and Evaluation of Unarmed Fitness Activity
Abstract
For low accuracy in the recognition and evaluation of unarmed fitness activities, analyzing the impact of the diversity of the execution speed of unarmed fitness activities on the recognition and evaluation results, a contactless recognition and evaluation method of unarmed fitness activities has been proposed by using the normalization to improve dynamic time warping (DTW) algorithm. As can be seen, the proposed method can reduce the influence of activity execution speed change on activity recognition and evaluation, so as to improve the contactless recognition accuracy of unarmed fitness activities. Meanwhile, the overall recognition accuracy can reach 0.91, and the positive rate can be more than 0.84, which has strong robustness.
1. Introduction
Unarmed fitness activities are an important part of national fitness. Because no additional equipment is required and there are no special requirements for fitness venues, unarmed fitness activities are favored by the vast number of people love. However, compared with exercise equipment, most unarmed fitness activities are less difficult. Trainers usually train in the gym or indoor or outdoor by themselves through text description or video. It can be seen that it lacks corresponding movement evaluation and feedback. When the trainer’s movement is not standard and not corrected, the trainer may be injured accidentally. In order to avoid this problem, it is necessary to find an automatic contactless method for identification and evaluation of unarmed fitness activities.
In recent years, the application of radio frequency identification (RFID) technology brings a new opportunity for the identification and evaluation of unarmed fitness activities. Guo Jun et al. proposed a feature fusion method of video and WiFi based on multimode learning, which improved the recognition accuracy of human actions. WiFi channel status information is used as the compensator of video stream. At the same time, convolutional neural network and statistical analysis algorithm are adopted to extract features of video and WiFi, respectively [1]. Xianshan Li et al. proposed a skeleton-based motion recognition method by improving the convolutional block attention module (CBAM). In addition, the improved module is applied to the adaptive network to capture the implicit weighted information of the channel domain and space domain [2]. Xu et al. proposed a dual-flow model of human motion recognition based on human skeleton and scene image, which realized human motion recognition under unstable lighting conditions. Here, the idea of the dual-flow model is used in [3]. Fang Lei and Ning Bai et al. used the self-similar structure of human object color as the basic feature to design adaptive template function to extract human actions, which can accurately and robustly extract human targets in videos [4, 5]. Li and Syed Hassan et al. constructed a three-layer human motion recognition information processing system. And LSTM recursive neural network is introduced to optimize the recognition efficiency of the system, simplify the recognition process, and reduce the data loss rate caused by dimension reduction. Thus, the human motion recognition is realized [6]. Li et al. proposed a method of coherent action recognition in live video with space-time attention and deep learning dictionary, which improved the accuracy and speed of coherent action recognition in live video [7]. Based on the fusion of shape and deep learning features, Muhammad Attique Khan et al. proposed an action recognition method based on entropy controlled geometric mean, which realized the recognition of human actions. Although the above methods have realized the recognition and evaluation of unarmed fitness activities to a certain extent, the accuracy of recognition needs to be further improved [8]. Che et al. proposed a nonnegative matrix factorization which can be used for feature extraction and further improve the motion recognition [9–11]. Moreover, the above methods have certain requirements for the fitness venues. Therefore, in order to solve the above problems and improve the accuracy of the identification and evaluation of unarmed fitness activities, this study adopts the normalized method to improve the angular frequency of activity signals on the basis of the DTW algorithm, which makes the contactless identification and evaluation of unarmed fitness interaction efficient and accurate.
2. Basic Methods
2.1. Introduction to DTW Algorithm
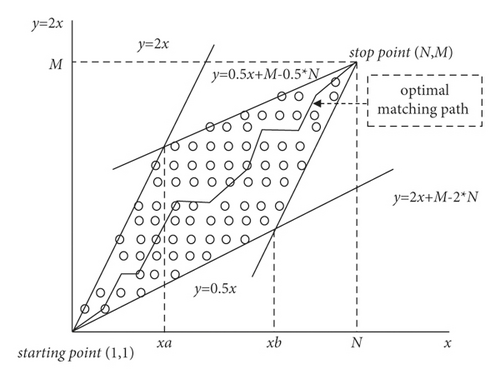
When using DTW algorithm for contactless matching recognition and evaluation of unarmed fitness activities, it is easy to cause wrong recognition and evaluation due to the diversity of movement speed in different activities [14]. Therefore, the algorithm is improved in this study, and the normalization method is considered to eliminate the influence caused by the diversity of movement speed in fitness activities.
2.2. Improvement of DTW Algorithm
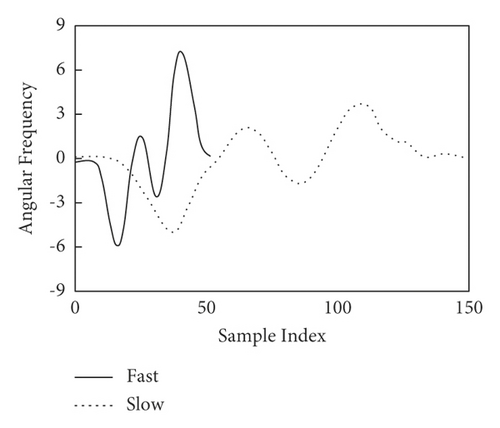
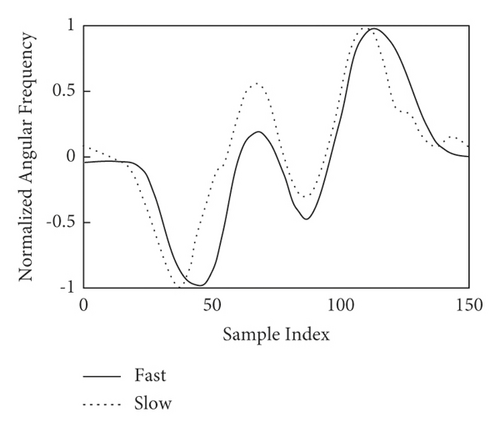
The comparison before and after normalization of the activity sequence by the improved DTW algorithm is shown in Figure 2.
3. Contactless Recognition and Evaluation Method of Unarmed Fitness Activities Based on Improved DTW
3.1. Whole Framework
Based on the above improved DTW algorithm, this study designs the process of contactless recognition and evaluation of unarmed fitness activities as Figure 3. First of all, the existing RFID reader is used to acquire phase information of the unarmed fitness activities, and the phase denoise, angular frequency calculation, and other pretreatment are adopted. Then, obtained phase information is transmitted to the computer through the Internet. After the activity is segmented, DTW (dynamic time warping) algorithm is used to identify activities. Finally, activities are evaluated, and the evaluation results are output.
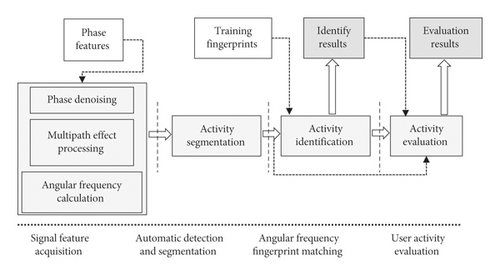
3.2. Signal Feature Acquisition
After N window processing, the signal angular frequency w′ after smoothing can be obtained.
3.3. Activity Segmentation
Movements of unarmed fitness activities are continuous. If the movements are directly recognized and evaluated, it is difficult to achieve ideal results both in recognition efficiency and evaluation accuracy [20]. In order to solve this problem, the activities are segmented. First of all, the coarse-grained segmentation method is adopted to segment the preprocessed long angular frequency sequence of unarmed fitness activity signals. The specific process is as follows.
Compare the variance of each equal length fragment with the preset threshold value Tlarge, and synthesize all fragments larger than the threshold value, as shown in Figure 4(a).
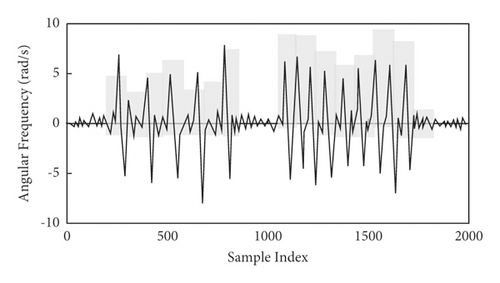
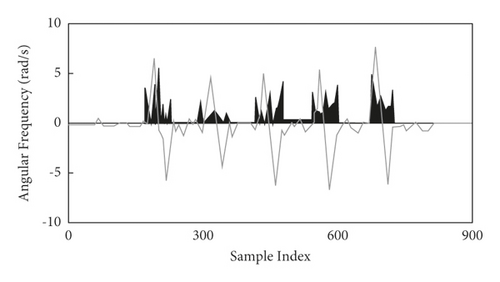
Then, the fine-grained method is used to segment again, and specific operations are as follows.
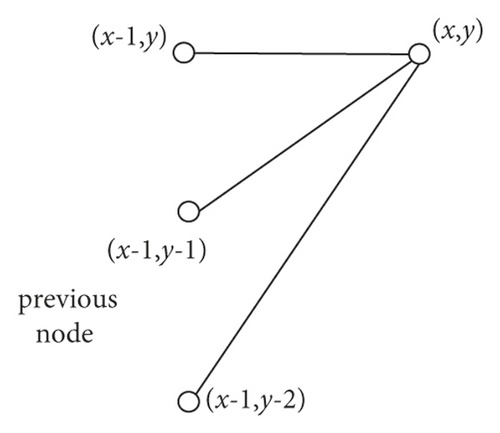
3.4. Activity Identification
The basic idea of improving DTW algorithm for activity recognition is as follows.
- (1)
The first is that w1 = d(1,1)andwK = (I′, J′)
- (2)
When wk = d(i′, j′) and wk+1 = d(x′, y′), x′−i′≤1, y′−j′≤1 and x′−i′≥0, y′−j′≥0
3.5. Activity Evaluation
- (1)
Duration of a group of actions: set the sampling point at the beginning of the action as O and the sampling point at the end of the action as P; then, the duration of the set of actions is [22]
(26) -
where fs represents the sampling rate of RFID reader.
- (2)
The number of a set of actions: set the number of a set of actions as M, which can be counted according to the action segmentation segment, and it can be expressed as
(27) -
where J is the activity of group J.
- (3)
Consistency of movement speed: set the maximum set of activities of group J as and the minimum set as ; then, the equations are as follows:
(28) -
where std stands for standard deviation. If the value of Peek StdJ and Valley StdJ is small, it indicates that the action speed is consistent.
4. Simulation Experiment
4.1. Construction of Experimental Environment
Impinj RFID H47 and Impinj Speedway R420 are used as basic equipment to collect the relative data and information of unarmed fitness movements. Internet technology is used to communicate with computer. The computer is configured with 64 bit Windows10 operating system. The CPU is Intel(R) Core(TM) i5-2040m, 2.5 GHz, and the memory is 4 GB DDR3. Furthermore, the hard disk is 500 GB machine hard disk. The simulation is realized through MATLAB R2017a.
In order to comprehensively evaluate the effectiveness of the proposed method, a 3.2 m∗1.6 m area is selected to build a contactless experiment area of unarmed fitness from three scenarios: fitness room, office, and indoor home. The Impinj RFID H47 passive tag is deployed at the edge of the experimental area. The Impinj Speedway R420 reader is positioned in the experimental area, and the trainer is located in the center of the experimental area. Figure 5 shows the deployment of gym scenario. The deployment of office and indoor home are the same.

4.2. Data Sources and Preprocessing
There are eight kinds of unarmed fitness activities selected as the research objects, such as kneeling back, squat, and fast curl-up, which are common and representative, as shown in Figure 6[23]. In three experimental scenarios, the above eight movements are tracked by ten volunteers for ten times of training, and the experimental dataset for the contactless recognition and evaluation of unarmed fitness movements is obtained. There are a total of 2400 movements. By tracking the above eight movements trained by an excellent fitness trainer at standard speed, the standard fingerprint database for contactless recognition and evaluation of unarmed fitness movements is obtained. There are 24 movements.

4.3. Evaluation Indicators
True positive rate (TPR) and false positive rate (FPR) are selected as indicators to evaluate the recognition effect of the proposed method on unarmed fitness activities [28].
4.4. Experimental Results
4.4.1. Algorithm Verification
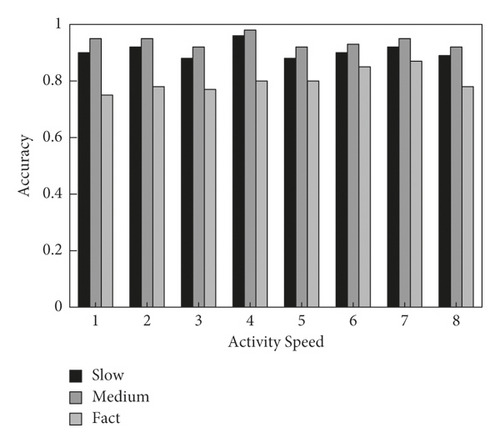
For the effectiveness verification of proposed algorithm normalization, the contactless recognition accuracy [29] of the algorithm for each unarmed fitness activity at different speeds is analyzed. Figure 7 shows the activity recognition accuracy of the algorithm at different speeds without normalization improvement. Figure 8 shows the activity recognition accuracy of the algorithm at different speeds after normalization. Under slow, uniform, and fast execution, the activity recognition accuracy before the algorithm improved is 0.73, 0.90, and 0.51, respectively. While the recognition accuracy after the algorithm improved is 0.89, 0.92, and 0.77, respectively. The accuracy is up 16.4%, 2.2%, and 25.8%, respectively. Thus, the improved algorithm in this study is effective. However, the recognition accuracy of the improved algorithm under fast execution is low. The reason is that the basic RFID equipment [30] has a low sampling rate so that there is a large deformation of the action sequence captured under the fast execution. Considering that normal fitness activities do not involve rapid unarmed movements, it is still effective. Therefore, the algorithm proposed in this study is effective to some extent.
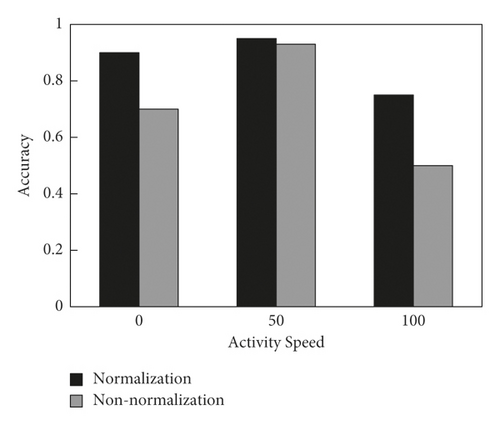
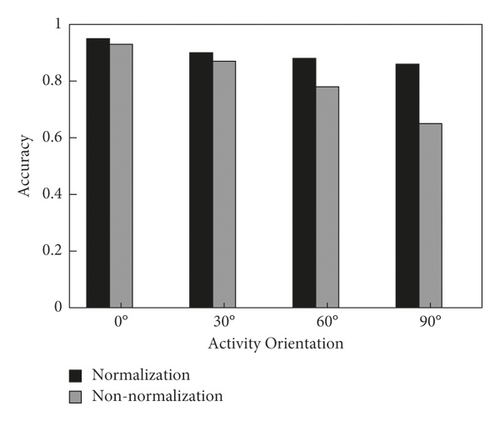
In order to verify the effectiveness of the proposed algorithm in improving the DTW algorithm [31], the 8 movements in the study are repeated 10 times in the directions of 0°, 30°, 60°, and 90°, respectively, and the proposed method is used to identify the results, as shown in Figure 9. As can be seen from the figure, the movement recognition accuracy before the algorithm improved in the directions of 0°, 30°, 60°, and 90° is 0.91, 0.85, 0.72, and 0.61, respectively, while the recognition accuracy after the algorithm improved is 0.93, 0.89, 0.86, and 0.84, respectively. Thus, recognition accuracy of the improved algorithm under different activity directions is improved varying degree. Furthermore, with the increase of the deviation angle, the improvement degree is higher. Therefore, the improvement of DTW algorithm in this study has certain validity.
4.4.2. Verification of Activity Segmentation Results
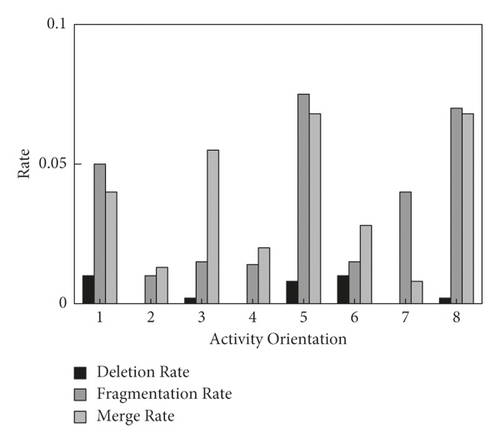
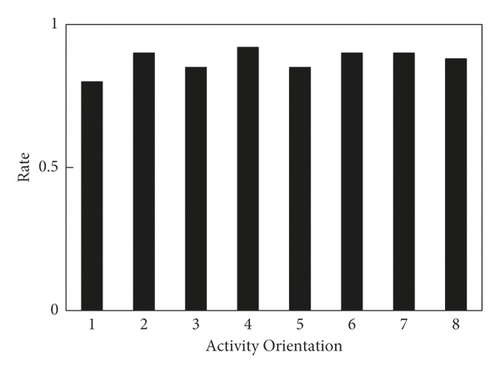
In order to verify the effectiveness of the proposed method in the segmentation of unarmed fitness activities, all activity segments are segmented in three real scenes, and the results are shown in Figures 10 and 11. It can be seen from Figure 10 that all the unarmed fitness activities have low loss ratios [32]. The loss ratio of movement nos. 2, 4, and 7 is 0, and the loss ratios of other movements are less than 0.01, which indicates that the proposed method has strong sensitivity to activities. As for the fragment ratio index, the fragment ratio of nos. 1, 7, 5, and 08 is high, and the fragment ratio of other actions is lower than 0.015, but the fragment ratio of all actions is lower than 0.07, which indicates that the proposed method can segment the movement completely. For the combination ratio index, the combination ratio of nos. 2, 4, and 7 is generally low, and the combination ratio of nos. 3, 5, and 8, which has a short rest between actions, is generally high, but the overall ratio is still lower than 0.065. Thus, the proposed method has a low probability of dividing an activity into multiple movements. It can be seen from Figure 11 that the segmentation accuracy of all actions is high. The segmentation accuracy of nos. 1, 5, and 8 is above 0.85, and the segmentation accuracy of other actions is above 0.9. In conclusion, the proposed method can well segment the unarmed fitness activities and has strong robustness.
4.4.3. Verification of Activity Identification Results
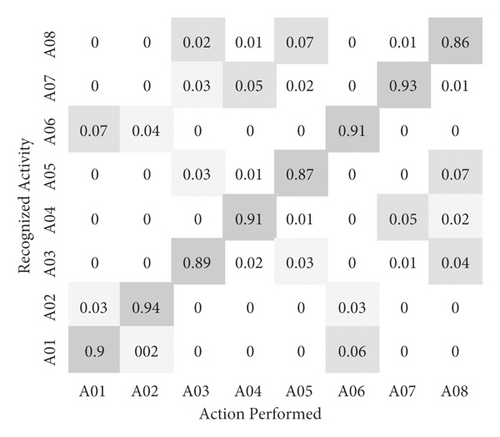
In order to verify the contactless recognition effect of the proposed method on unarmed fitness activities, the proposed method is verified in three real scenarios. Figure 12 is the confusion matrix of all unarmed fitness activities. In the figure, the rows are the interactions matched and identified by the proposed method, and each element represents the probability of each activity identified. Columns are the actions that actually took place, and each element represents the probability that the activity actually took place. As can be seen from the figure, the average recognition rate of the proposed method for activities is 0.91, that is, the proposed method has a high contactless recognition rate for unarmed fitness activities, which can effectively identify unarmed fitness activities in different scenarios.
4.4.4. Robustness Evaluation
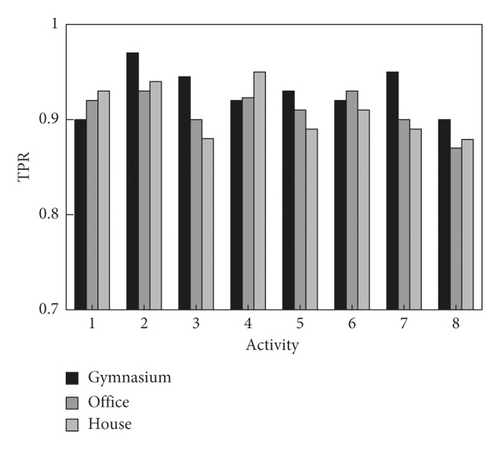
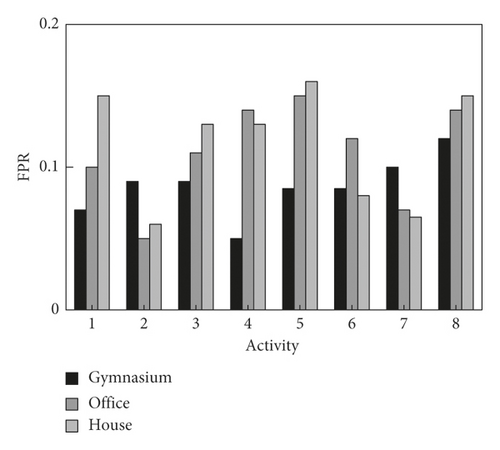
In order to verify the robustness of the proposed method, the contactless recognition of unarmed fitness activities by the proposed method in different scenarios is statistically analyzed. The true positive rate and false positive rate of activity recognition by the proposed method are shown in Figures 13 and 14. As can be seen from Figure 13, the true positive recognition rate of the proposed method for unarmed fitness activities in all scenarios is above 0.84, and the true positive recognition rate in three scenarios is 0.91, 0.90, and 0.89, respectively. As can be seen from Figure 14, the false positive recognition rate of the proposed method for unarmed fitness activities in all scenarios is less than 0.16, and the false positive recognition rate in three scenarios is 0.08, 0.10, and 0.11, respectively. Therefore, the proposed method can accurately identify the unarmed fitness activities in different scenarios and has strong robustness.
5. Conclusion
To sum up, the proposed activity recognition and evaluation method based on improved DTW can improve the contactless recognition accuracy of algorithm for unarmed fitness activities at different speeds and in different directions by normalizing the activity sequence. And the overall recognition accuracy reaches 0.91. The true positive rate of the unarmed fitness activities in all scenarios is more than 0.84, which can effectively identify the unarmed fitness activities in different scenarios with strong robustness. However, there are still some deficiencies. Specifically, the proposed method mainly identifies and evaluates a single activity. If there is more than one trainer at the same time for unarmed fitness activities, the recognition efficiency and evaluation accuracy will be affected. Therefore, how to solve the problem of activity identification and evaluation of multitrainers needs to be further studied, and the next step will be discussed from this aspect.
Conflicts of Interest
The author declares no conflicts of interest regarding this work.
Open Research
Data Availability
The experimental data used to support the findings of this study are available from the corresponding author upon request.




