Investigation into the Reliability and Encryption Performance of Wireless Signal Transmission by Network Coding Combined with Blockchain in Natural Disaster Scenarios
Abstract
To enhance the reliability and encryption of unmanned aerial vehicle (UAV) wireless signals in natural disaster scenarios, firstly, the present work analyzes the current wireless signal transmission mode of UAV. In addition, it discusses the efficient network coding of wireless signal transmission model and blockchain with strong encryption ability. Secondly, the signal transmission model of network coding is explored. Finally, the network coding wireless signal transmission model is combined with the blockchain wireless signal transmission model to realize efficient and encrypted data transmission. The research results show that the network coding wireless signal transmission model combined with blockchain technology realizes the maximum difference of network coding wireless signal transmission rate of 1.5 Mb/s. The model also encrypts the data in the simulation scenario of natural disasters through blockchain technology. After encryption, the data protection effect of the transmission model is significantly improved and meets the requirements of standard data transmission. Meanwhile, the wireless signal transmission model can reduce the resource occupation rate in the process of data transmission and improve the success rate and universality of data transmission in natural disaster scenarios. The probability of data being successfully protected in disaster is more than 90%. The results provide technical support for the stable transmission of wireless signals in natural disaster scenarios and provide a reference for improving the reliability and encryption of wireless signal transmission.
1. Introduction
With the development of network technology, wireless signal transmission has become a primary data transmission mode. Wireless signal transmission can strengthen the communication between users and provide a good platform for resource sharing between users, significantly facilitating modern human beings’ lives [1]. Wireless signal transmission needs to be efficient satisfying people’s protection of information to adapt to the fast-paced life of humans. Therefore, unmanned aerial vehicles (UAVs) have become the primary communication tool under natural disasters. The wireless signal transmission of UAV can provide significant advantages for disaster analysis and personnel rescue under natural disasters [2]. Although wireless signal transmission is not ideal in practical applications, many studies have provided technical support for its development.
Marques et al. (2019) [3] pointed out that network coding has been a prominent breakthrough in communication in recent years. Its basic idea is that the network node participates in data forwarding and processing, significantly improving network performance. Huang et al. (2019) [4] reported that the proposal of network coding was a breakthrough in the theoretical research in network communication, which allowed network nodes to encode the transmitted information appropriately before forwarding information. The authors believed that the application of network coding had the advantages of improving network throughput, balancing network load, reducing node energy consumption, and enhancing network robustness and security. Andoni et al. (2019) [5] observed that the application research of blockchain technology as a distributed shared database technology in various fields was in the ascendant; the decentralization, transparency, fairness, and openness of blockchain technology were consistent with the concept of energy Internet, and its application in energy Internet would further promote the construction of energy Internet. Saberi et al. (2019) [6] pointed out that the application and implementation of cloud storage technology furnished users with a new data processing mode. Its convenient and efficient characteristics attracted many individuals and groups to store data in the cloud storage system. They noticed that cloud storage technology had problems such as an open environment and a centralized processing process, which posed a significant threat to data and user security. Therefore, they utilized the booming blockchain technology to solve the security problems existing in cloud storage technology. Min (2019) [7] reported that with the rapid development of Internet technology, the amount of data in cyberspace was gradually increasing. The authors constructed the information protection program based on blockchain, which had high security and realized the robust protection of information, ensuring the privacy and security of data in practice. The analysis of the current research suggests that the current data transmission research is not mature, and the designed data model transmission mode still cannot meet the needs of users, and the transmission stability rate is not ideal. Most importantly, the current data transmission model cannot be realized simultaneously with many factors such as transmission rate, stability, and encryption. Therefore, more research is needed to provide technology for this work.
In short, the present work first explores the application of network coding and blockchain technology in UAV wireless communication and designs the network coding algorithm. Second, combined with network coding and blockchain technology, a new wireless signal transmission technology is proposed. Finally, taking the rainstorm in Henan Province in July 2021 as the experimental scene, the designed model combining network coding and blockchain technology is compared with the original wireless signal transmission model to verify the performance of wireless signal transmission technology. The present work adds encryption function to a large number of data transmission models, which innovates the situation of poor stability of traditional data transmission. This research can provide technical support for efficient and reliable wireless signal transmission and makes an important contribution to information security transmission in natural disaster scenarios.
2. Exploration of the Wireless Signal Transmission Model
2.1. Network Transmission under a Rainstorm in Henan Province
On the afternoon of July 20, 2021, a video of the Henan subway flooded due to a rainstorm spread all over the network. Suddenly, the Internet and traditional media have spoken out, and the Henan local flood affected netizens’ hearts all over the country. News of Henan’s torrential rain quickly spread across the Internet. Figure 1 displays the major accident scenes caused by the rainstorm in Henan.

As shown in Figure 1, due to the rainstorm, people in Henan are affected to varying degrees in all aspects, among which road traffic and network operation are the most serious. Contemporary network operation is exceptionally vital, and network operation needs to rely on essential network equipment and network base stations. When natural disasters occur, unpredictable damage will be caused to network equipment and base stations. Therefore, it is a considerable problem to restore the network operator when the network equipment and base station are damaged. How to overcome and improve this problem has become epoch-making research. The rescue work under natural disasters and disaster investigation requiring signal communication must be improved. Therefore, the communication mode of small equipment such as UAV has become the leading technical means of communication under natural disasters.
2.2. Wireless Signal Transmission Model via Network Coding
The remote communication of UVA network is the inevitable development trend. Effective and reliable real-time communication between UAVs is the premise and foundation of realizing their cooperative operation. Because the information transmission technology via blockchain has the advantages of good security and timeliness, low system complexity, and low power consumption, it is an excellent choice to apply it to UAV communication links [8]. Network coding and intermediate coding node can realize the efficient transmission of information data through the received data’s nonlinear or linear coding operation. Network coding technology was first used in a wired ne, specifically used to optimize the network layer to improve the running speed of wired networks [9]. Nowadays, this technology has matured, but wireless network coding technology still faces many problems, including the issues of wireless network coding itself and the difficulties in customer use [10]. From the analysis of the factors of network coding, network coding significantly improves the network data transmission performance and network throughput, saves network bandwidth resources, balances the network load, and has many defects. From an internal point of view, network coding significantly improves network data transmission performance and network throughput, saves network bandwidth resources, balances network load, and has many defects. Compared with traditional network data transmission, nodes in a network coding system need to operate coding and decoding programs frequently, which will produce a series of problems. For example, complex programs will increase the delay of network data transmission and consume excessive network computing resources [11]. Therefore, in the process of network coding optimization, the network coding program needs to be optimized first.
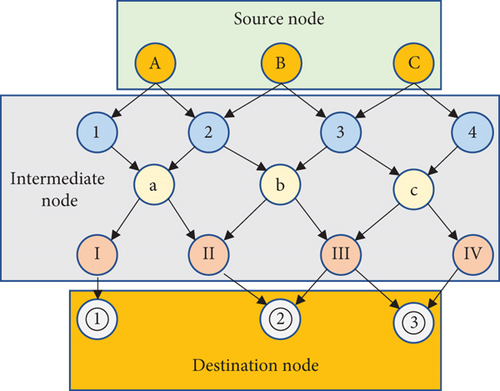
Principally, network coding transmission information is realized by defining network nodes, determining the relationship between output points and input points, and then, encoding the required data based on the intermediate nodes with coding conditions. The network coding system includes many intermediate nodes encoding in turn. After the previous node completes the required coding content, it will transmit the data to the next node. When all intermediate nodes complete coding the data they need, the network coding system will dispatch the coded output to the destination node to complete the data transmission [12]. When the destination node receives the data sent by the original source node, it will decode the data to obtain the original information [13]. Figure 2 reveals the basic flow of data transmission through network coding.

As shown in Figure 2, data transmission between users is implemented after determining the transmitted data’s source node and destination node. The user only needs to upload and view the corresponding data during data transmission. The encoding and decoding programs are completed at the wireless network end, significantly saving the user’s resources [14]. During data transmission, the number of intermediate nodes is at least 2. The coding function of nodes is obtained under certain conditions, indicating that not all nodes can be coded. Theoretically, when the generation domain of the network coding system is infinite, applying network coding can also realize the multidial theoretical capacity. At present, the limited generation domain is still used in practical applications [15]. Network coding can carry out nonlinear and linear processing in the process of data processing. In theory, linear network coding can implement the maximum capacity of network information transmission. In the encoding process, the coefficients used for encoding are selected according to the size of the generation domain. The selection of encoding coefficients needs to meet the encoding task of each intermediate node to ensure that the destination node that finally receives the data can decode smoothly [16].
2.3. Blockchain Technology
As network technology advances, the network should meet the high-speed data transmission and the security guarantee in the process of network transmission [17]. Therefore, the role of blockchain technology is self-evident. Blockchain is composed of nodes. Its task is to store, encrypt, and package data to generate a new block. Then, a representative node in the block is selected and connected with other blocks to form a blockchain chain [18]. Blockchain is a database consisting of decentralized, centralized structures and encrypts data. Its primary function is to ensure that data is not stolen or modified. Compared with traditional databases, blockchain databases have the advantages of decentralization, tamper-proof, anonymization, time sequence, centralized maintenance, and programmability [19]. Decentralization of blockchain means that the blockchain nodes have the same functions and powers in a multinode network structure. Tamper-proof means that in the blockchain, except for creating blocks, other blocks have the unique hash value of the previous block’s data, and all blocks are connected through the hash value. If the block’s data is modified, the hash value in the block will change accordingly. At this time, when the hash value of the previous block disappears, the blockchain connection will be forced to be disconnected, so other blocks will organize the block’s data to be modified [20]. Anonymization means that the blockchain system will hide the user’s information during data transmission between users for user security. When users conduct data transactions, they contact each other through addresses [21]. Time sequence means that each blockchain has a time tag. The blockchain will store the data in order according to the time tag of the node. It can also quickly find the data according to the time tag of the data in practice [22]. Centralized maintenance indicates that the blockchain solves the problems in the blockchain system through various algorithms to maintain the system’s regular operation [23]. Programmability demonstrates that the blockchain can calculate the data through the code with contractual nature and save the results in the public database to realize the transformation of multiple data [24]. Figure 3 displays the basic structure of the blockchain.
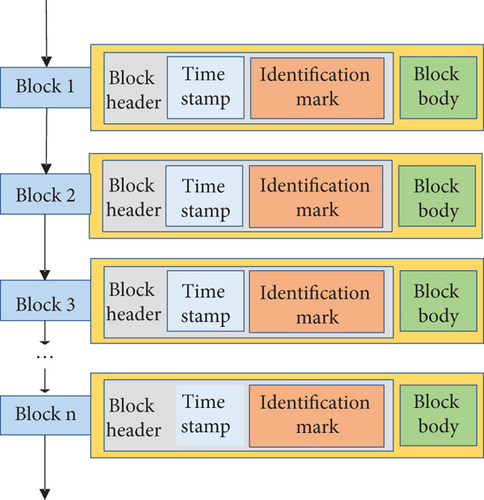
In Figure 3, the blockchain is composed of multiple blocks. The block is mainly constituted of a block header and a block body. The primary function of the block body is to identify and authenticate users in the transaction process, and the block header is responsible for storing data and including the identification and time tag of the data. The blockchain depends on the parameters in the block header to search for data.
2.4. Data Transmission Algorithm Based on Network Coding
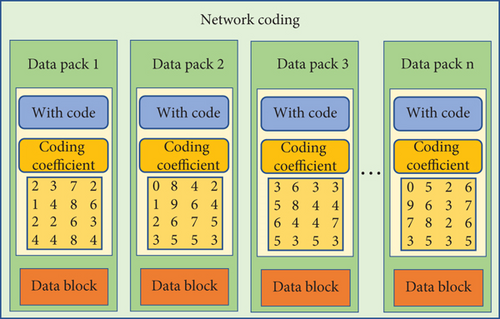
The data transmission based on network coding is carried out through coding and decoding. When the transmitted data is large, the network coding system divides the data into many transmission groups. A group of information is divided into many blocks for coding and transmission in the coding process. Each data coding area contains a data block and other identification areas, covering the storage area of coding coefficients for easy decoding and identification marks, such as generation coding [25]. Figure 4 illustrates the specific structure of network coding for data transmission.
2.5. Model Design Based on Network Coding and Blockchain Technology
Network coding technology is data grouping and block coding transmission of grouped data. Users upload data through wireless networks using mobile devices. After data uploading, the network coding system first groups the data, divides the data randomly, completes the grouped data, and divides the data blocks according to the random principle. Then, the data is encoded and transmitted. The required data is encoded according to different nodes in the transmission process. The encoded data is distinguished by substitute coding and coding coefficients. After all the data are encoded, they are combined with substitute coding as the identification. The combined output coding needs to decode the data. The data is decrypted according to the decoding process’s generation coding and coding coefficients. The generation coding identifies the data; the coding coefficient helps the encoded data recover to the source data [27]. Figure 5 illustrates the flow of data encoding, transmission, and decoding.
As shown in Figure 5, the encoding and decoding process also includes data transactions. The transaction area is in the coding body of the coding block. In other words, the user carries out specific transaction transmission of the data through the coding body. The encoded content of the data is included in the coding terminal. In this way, the actual content of the data is hidden to a certain extent to protect the data. However, its protection mechanism is still imperfect. Therefore, this paper combines network coding with blockchain technology to protect the safe transaction of data in data transmission. Specifically, an efficient and secure wireless signal transmission technology is obtained through network coding technology’s efficient data transmission function and the high-intensity data protection function of blockchain technology. This technology can encrypt data, enhancing the efficiency and reliability of data transmission. Figure 6 shows the specific data transmission through network coding and blockchain technology.
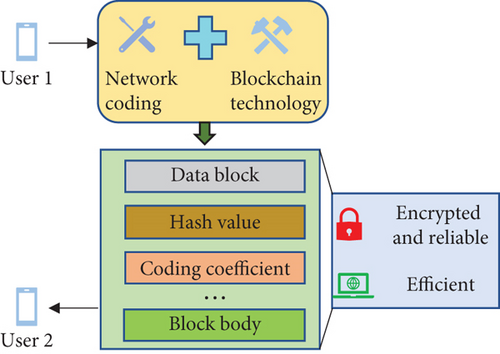
As shown in Figure 6, network coding technology is the fastest form of data transmission at present, but it belongs to a mechanism without data encryption protection. Therefore, in the event of a natural disaster, the network fluctuates, which will result in data loss. Moreover, the data without encryption protection will become transparent data after losing, which is incredibly dangerous for transmitting data. In short, while efficiently transmitting data, it is essential to avoid data loss and data theft under the influence of natural disasters. Here, network coding and blockchain are integrated into data transmission to realize the encryption protection of wireless signals and improve the reliability of wireless signal transmission. Figure 7 provides data transmission after combining network coding and blockchain technology.
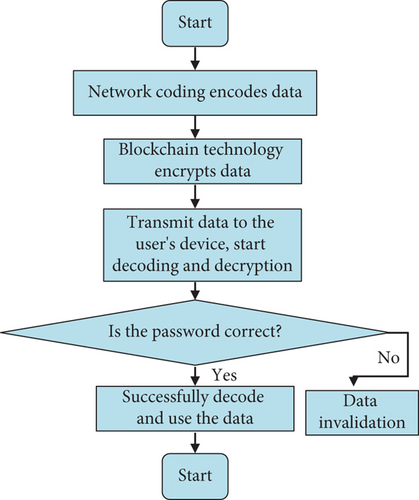
According to Figure 7, the user first encodes and transmits the data. Finally, password authentication is essential for data decoding due to the encryption nature of the blockchain to encrypt the data while improving the efficient transmission of data. The studied specific scenario aims to simulate the data transmission effect under the natural disaster scenario. The specific experimental content includes the comparison of the data transmission effect. The total amount of data transmission is 10 G, and the same equipment is used for comparison under different methods.
3. Research on the Performance of Network Coding and Blockchain Technology
3.1. Basic Performance Study
Under the same network environment and external flow conditions, the actual data transmission rate of traditional network coding technology, blockchain technology, and the combination of network coding and blockchain technology is compared with the ideal wireless data transmission rate. Figure 8 displays the comparison results of data transmission rates.
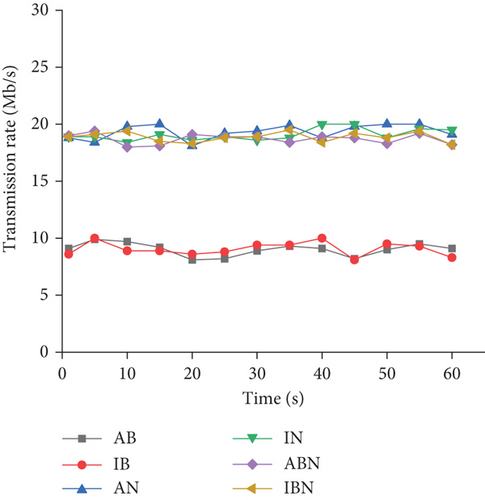
In Figure 8, AB represents the actual result of blockchain, IB refers to the ideal result of blockchain, AN means the actual result of network coding, IN stands for the perfect result of network coding, ABN signifies the actual result of network coding combined with blockchain, and IBN represents the ideal result of network coding combined with blockchain. The difference between the perfect and actual results is insignificant in the overall transmission rate comparison, and the maximum difference is 2. The wireless data transmission results of blockchain and network coding differ significantly, with a maximum difference of about 10. However, the wireless data transmission rate difference between the ideal result and actual result of the combination of network coding and blockchain reported here is small, with a maximum difference of about 1.5. Therefore, the wireless data transmission model combining network coding and blockchain can fully meet the o wireless data transmission rate. It is also necessary to make statistics on the specific network resources occupied during the operation of the model. In the current process of wireless data transmission, in addition to the wireless data transmission rate, users pay more attention to the resource occupancy rate. The smaller the resource occupancy rate, the simpler the equipment users need to use. Therefore, reducing the resource occupancy rate in wireless data transmission is necessary.
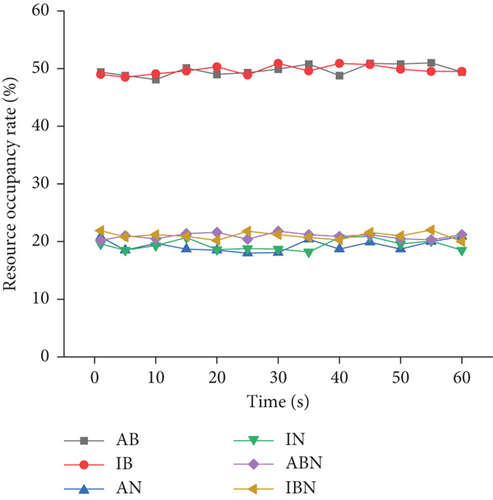
According to Figure 9, the gap between the overall ideal resource occupancy rate and the actual resource occupancy rate is slight, with a maximum difference of about 2.5%. The resource occupancy rate of network coding is much lower than that of blockchain, with a maximum difference of about 30%. However, there is little difference in the resource occupancy rate in the wireless data transmission process of the combination of network coding and blockchain. The wireless data transmission resource occupancy rate of the combination of network coding and blockchain is about 3% higher than that of network coding. This proves that the resource occupancy rate of the actual model constructed here is in an ideal state.
3.2. Wireless Data Transmission under Natural Disasters
Natural disasters are inevitable. Small natural disasters are bearable for any wireless data transmission without damaging the wireless network base station because they do not cause severe data damage or loss. However, terrible natural disasters have a crippling impact on wireless data transmission. Therefore, a reliable data protection mechanism is needed to avoid significant data loss and data theft after natural disasters in wireless data transmission. Figure 10 summarizes each model’s successful data transmission rate in the process of wireless data transmission under the condition of irregular network fluctuation.
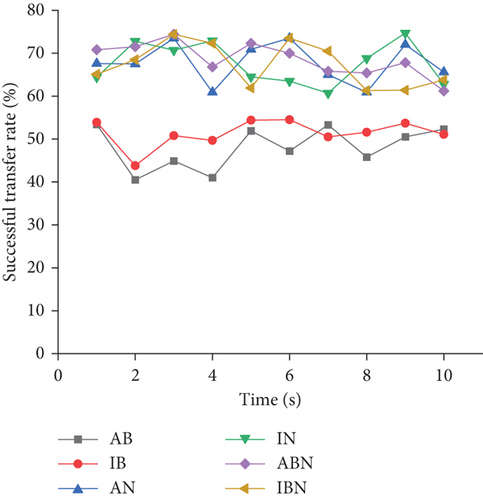
As shown in Figure 10, under the condition of network fluctuation, the successful data transmission rate of the three models is relatively low, up to about 70%. Nevertheless, there is little change in the successful data transmission rate of the model combining network coding and blockchain, all about 70%. Thus, the wireless data transmission model combining network coding and blockchain in natural disasters still shows an ideal data transmission effect. Furthermore, the security of data transmission is investigated. Figure 11 provides the data failure caused by the irregular fluctuation of network data transmission in the case of natural disaster simulation.
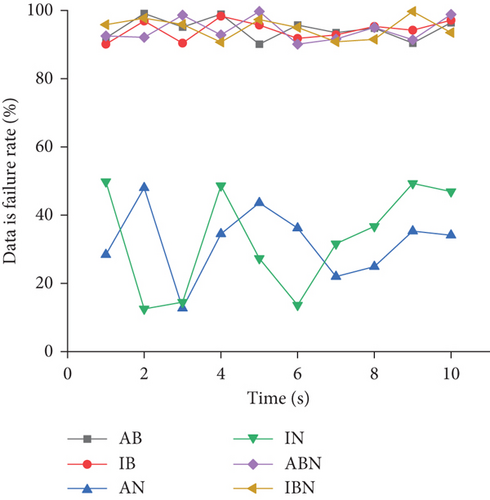
Figure 11 presents the data failure rate after tampering or embezzlement of data under the simulated natural disaster. This test simulates ten data transmissions and conducts manual tampering and embezzlement after the data transmission is completed to check the data failure rate after the experiment. The higher the failure rate, the greater the protection degree of the data transmission model to the transmitted data. The results suggest that the failure rate of the network encoded data transmission model after data is tampered with is the lowest, with the maximal rate of about 50%. It can be concluded that the protection degree of the network encoded data transmission model for data is too low to meet the general data transmission needs of users. However, after the data is medicated by blockchain technology, the failure rate of data generally reaches more than 90%. In contrast, the wireless data transmission model based on network coding technology and blockchain generally has a data failure rate of more than 90% after tampering and embezzlement after data transmission. Hence, this model can meet the security needs of users for data transmission.
4. Discussion
Firstly, the present work introduces the basic situation of disasters in Henan Province and comprehensively analyzes the current situation of data transmission through disaster scenes. Secondly, it analyzes the network coding technology and blockchain technology and designs the network coding data transmission model based on blockchain according to the two technologies. Finally, the disaster scene is simulated, and the designed model is comprehensively studied and analyzed. It is found that in the comparison of overall transmission rate, the transmission rate difference between the predicted results and the actual results of the combination of network coding and blockchain designed here is very small, and the maximum difference is about 1.5. Therefore, the wireless data transmission model combined with network coding and blockchain can fully meet the requirements of wireless data transmission rate. There is little difference between the overall predicted resource occupancy rate and the actual resource occupancy rate, and the maximum difference is about 2.5%. The resource occupancy rate of network coding is much lower than that of blockchain, with a maximum difference of about 30%. However, there is little difference in resource occupancy in the wireless data transmission process of the combination of network coding and blockchain. The resource occupancy rate of wireless data transmission combined with network coding and blockchain is about 3% higher than that of network coding. It shows that the model combining network coding and blockchain has ideal resource occupancy. Finally, through the disaster simulation test, it is found that the data transmission success rate of the three models is relatively low, up to about 70%. Nevertheless, the data transmission success rate of the combined model of network coding and blockchain has little change, which is about 70%. Therefore, the wireless data transmission model combining network coding and blockchain still shows ideal data transmission effect in natural disasters. This test simulates ten times of data transmission. After the data transmission is completed, manual tampering and embezzlement are carried out to check the data failure rate after the experiment. The higher the failure rate, the greater the protection degree of the data transmission model to the transmitted data. The results show that the network coding data transmission model has the lowest failure rate after the data is tampered, and the maximum value is about 50%. It can be concluded that the degree of data protection of network coded data transmission model is too low to meet the general data transmission needs of users. However, after the data is optimized by blockchain technology, it can effectively protect the data transmission process.
5. Conclusion
The present work combines network coding technology with blockchain technology to simulate the network situation under natural disasters and then studies the performance of the model in data transmission. The research results show that the wireless data transmission model combined with network coding and blockchain technology can meet efficient data transmission and significantly reduce the relative resource occupation in data transmission. Additionally, this experiment simulates a series of data transmission accidents caused by the violent fluctuation of wireless network signals under natural disasters. Practice has proved that the designed data transmission model can complete the task of data transmission with the highest success rate and protect the tampering and embezzlement in data transmission to a great extent. The failure rate after data tampering and embezzlement is more than 90%, which can ensure that the data will not be embezzled and tampered while efficiently transmitting the data. To sum up, the data transmission model based on network coding combined with blockchain can take into account various needs in current data transmission and meet the multiple needs of user data transmission under the condition of natural disasters. It provides important technical support for the transmission of a large number of data and contributes to the development of communication technology. Although the exploration can provide sufficient technical support for user data transmission in model design, the practical application design in natural disasters is still not perfect. Future research will strengthen the data transmission application of the model combining network coding and blockchain in the case of natural disasters.
Conflicts of Interest
The authors declare that they have no conflicts of interest.
Open Research
Data Availability
The data used to support the findings of this study are included within the article.




