Precision Poverty Alleviation Methods in the Agricultural Field Based upon Wireless Communication Networks and Blockchain
Abstract
Poverty in the agricultural sector has always existed and needs to be urgently solved. How to achieve precise poverty alleviation and poverty alleviation in the agricultural sector has become a top priority now. In this regard, this study combines blockchain technology and wireless network technology to build a blockchain platform. The platform is responsible for assisting the development of agricultural poverty alleviation projects, integrating project data into a public area according to the characteristics of the blockchain. The data cannot be tampered with during storage and transmission, ensuring the authenticity of the data. As the core of blockchain technology, the algorithm of the consensus mechanism plays a crucial role in alleviating poverty in agriculture, using the RBFT consensus mechanism to achieve “precise identification” of the poor. The pilot has shown that the RBFT algorithm will achieve a throughput of 2,980 strokes/second. In addition, the time from node failure to recovery is diminished by 60% compared to the time consumed by the PBFT algorithm. It can be clearly seen that the blockchain platform using the RBFT algorithm is more robust.
1. Introduction
As a basic and key industry, agriculture has always played a “cornerstone” role. However, due to the industrial structure, agriculture has the problem of low industrial efficiency. Blockchain technology has a very good role in promoting the high-quality development of agriculture. Moreover, the current agricultural industry and social structure have obvious characteristics of weak centralization and decentralization. This fits well with the characteristics of the blockchain, and it also has application integration points. Therefore, the blockchain will be used as a crucial factor to lead the reform and development of agriculture [1].
Poverty alleviation work is imperative, but there are still a series of problems that need to be resolved before poverty alleviation is truly achieved. How to “accurately identify“ the impoverished population, avoid poverty alleviation that varies from person to person, how to trace the flow of poverty alleviation funds, how to build data sharing, and a unified poverty alleviation management system are all the issues that need to be solved urgently. In the end, we discovered in research and practice that blockchain technology occupies the advantages of real-time data processing and monitoring, and decentralization in the process of precise poverty alleviation. The emergence of blockchain technology will provide new ideas for global technological innovation. Regarding wireless communication networks, blockchain, and agricultural poverty alleviation, there have been many related studies at home and abroad. Lee et al. proposed a novel framework for computing using wireless mobile miners (MMs) in blockchain systems. Emulation results validate the analysis and derivation and show that using a larger number of MMs can reduce energy expenditure by up to 95% compared to a blockchain system with a single MM [2]. Wei H analyzed the key factors that affect the efficiency of the blockchain. Wei H considers this problem from a communication perspective. In particular, Wei et al. proposed a coordinated satellite ground network to create an efficient blockchain [3]. Guo et al. proposed a blockchain-based mobile edge computing (B-MEC) framework for adaptive resource allocation and computing offloading in future wireless networks. Among them, the blockchain serves as an overlay system to provide management and control functions [4]. Lee J H discusses how blockchain will revolutionize the consumer electronic market. Lee and Pilkington analyzed the current winds of change in the booming global consumer electronic (CE) industry worth billions of dollars. Lee J H finally pointed out that blockchain technology has the ability to make the CE industry a more transparent, safer, and more honest place [5]. Yeoh aims to study the major regulatory challenges affecting blockchain and innovative distributed technologies in the European Union (EU) and the United States. The survey results (intelligent regulatory noninterference methods adopted by the European Union and the United States) to a large extent predict the future innovative contribution of blockchain in financial services and related fields and the enhancement of financial inclusion [6]. Khaqqi et al. proposed a new ETS model customized for Industry 4.0 integration. The case study shows the internal workings of a reputation-based trading system, where reputation represents the performance of participants and their commitment to emission reduction [7]. The data of these studies are not perfect, and the experimental conclusions are not applicable to some basic and important fields such as agriculture and the internet of things, so they cannot be accepted and adopted by the public.
The innovation of this study is that the technical characteristics of the blockchain are very compatible with the needs of poverty alleviation and alleviation in the agricultural field. Blockchain not only provides a good technical support platform for the development of the agricultural field but also solves many problems that exist in agricultural poverty alleviation today, such as “precise identification” of the poor, fund traceability, data security, and other issues. The agricultural platform formed by combining blockchain technology and wireless network technology can not only promote the improvement of agricultural industry efficiency but also achieve effective and accurate poverty alleviation. It provides a series of guarantees for people who are out of poverty and truly achieves “precise poverty alleviation.”
2. Wireless Communication Network and Blockchain
This study involves blockchain and wireless communication networks. The specific overall model of the blockchain-based precision poverty alleviation innovation mechanism is shown in Figure 1. The next experimental process will be carried out according to the model, mainly analyzing the core of blockchain technology, such as technical framework, asymmetric encryption, and consensus mechanism. [8–10].
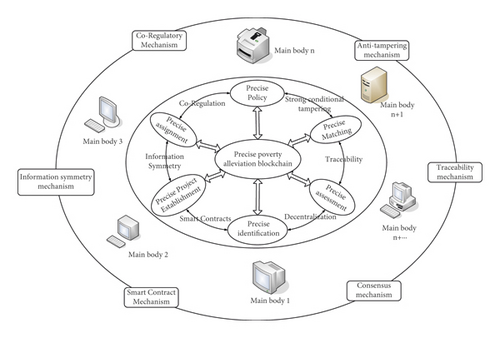
2.1. Blockchain
Blockchain technology cannot be separated from algorithms, and the more important algorithms are symmetric encryption and asymmetric encryption, and this study applies to elliptic curve cryptography (ECC) in asymmetric encryption. What follows is an introduction to asymmetric encryption and digital signatures.
2.1.1. Asymmetric Encryption and Digital Signature
Asymmetric encryption means that the key used by the sender to encrypt the data does not need to be kept secret, while the key used by the receiver to decrypt the data cannot be disclosed, i.e., both parties use two different keys. If asymmetric encryption is used to encrypt the key of symmetric encryption, the key of symmetric encryption can achieve secure transmission.
- (1)
An integer i from 1 to n – 1 is randomly selected.
- (2)
According to the elliptic curve multiplication rule, the following is calculated
(8) - (3)
Calculation
(9) - (4)
Computing the hash of the information M, H.
(10) -
HASH is a cryptographic hash function, such as SHA-2 [16].
- (5)
The left-most Ln bits of H are taken and marked as h, where Ln is the binary bit length of the sequence n [17].
- (6)
Calculation
(11) -
(n is the order), if s = = 0, go back to step 1.
- (7)
S = (r, s) is the signature.
- (8)
Private key signature:
- (1)
Whether the r and s of the signature are both in the interval [1, n − 1] must be verified.
- (2)
Similarly, the original message must be calculated.
(13) - (3)
Order
(14) - (4)
Order
(15) -
And,
(16) - (5)
A point on the curve is calculated.
(17) - (6)
If
It means that the signature is valid; otherwise, it is invalid.
Let it be compared with tG, if they are equal, and the signature verification is successful [18].
2.1.2. Blockchain Technology Architecture
- (1)
Distributed Bookkeeping. Multiple participants collectively check and maintain the data.
- (2)
Traceability. The data recorded using blockchain technology can be effectively accessed and traced for a long time.
- (3)
Untamperable. The data cannot be tampered with during the process of transmission and storage to ensure the permanent preservation of data.
- (4)
Consensus Mechanism. The consistency of data interaction and process makes it a consensus mechanism.
According to the degree of openness, blockchain can be divided into three types: public chain, consortium chain, and private chain [23, 24]. The comparison table of the three blockchains is shown in Table 1.
| Public chain | Private chain | Alliance chain | |
|---|---|---|---|
| Participants | Any user | Inside the organization | Alliance member |
| Incentives | Need | Unnecessary | Dispensable |
| Degree of centralization | Completely decentralized | (Multi) centralization | Polycentricity |
| Consensus mechanism | PoW/PoS/DPoS | Distributed consistency algorithm | Distributed consistency algorithm |
| Bookkeeper | All participants | Customization | Affiliate members consult to determine |
| Computing power | 3–20 strokes/sec | 1000–100000 strokes/sec | 1000–10000 strokes/sec |
| Outstanding features | Credit since establishment | Transparent and traceable | Scalable and efficient |
| Typical scenarios | Digital currency of public trust, the transaction processing | Internal audit, issuance | Distributed with permissions ledger processing |
The public chain establishes a trust mechanism through cryptography, such as bitcoin. Only the chain with the largest workload and that is longest will be recognized and linked to the previous chain [25]. In the shared blockchain system, anyone can freely enter and exit, and there are corresponding incentive mechanisms to encourage people to participate, such as bitcoin. When people mine, there will be bitcoin rewards.
Consortium chain is a new model extended from public blockchain [26, 27]. The alliance chain is multicentralized, that is, each node participating in the alliance is the center of the alliance chain. Compared with the public chain, it has the advantages of high efficiency, cost optimization, and strong adaptability, such as the R3 Banking Union formed by many internationally renowned banks [28].
The private chain is a fully private blockchain where write access is controlled by only one single entity. This is because an institution does not need to exchange information with other institutions and is only based on the blockchain system that it needs to establish, such as the Deloitte audit blockchain. Compared with other chains, the private chain has the characteristics of self-endorsement and complete centralization. It guarantees the transparency and traceability of institutional data, and the operation of the private chain does not require an incentive mechanism [29].
The blockchain technology system framework is composed of the data layer, network layer, consensus layer, incentive layer, contract layer, and application layer from bottom to top, as shown in Figure 2:
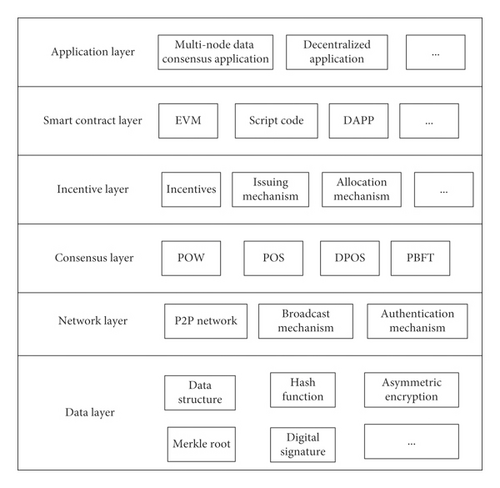
Block is the core unit of blockchain [30]. Blockchain is formed by interconnecting blocks. The nodes participating in the system generate and record the transaction data of the system over a period of time into blocks by cryptographic methods. Each data block contains not only the data but also a block header that records the block meta-information, which contains information such as the block hash and the previous block hash, thus linking the blocks together. The schematic diagram of the blockchain data structure is shown in Figure 3:
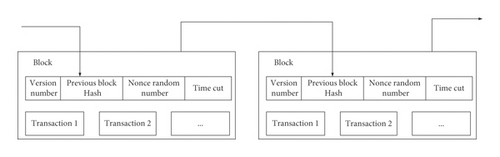
Figure 4 shows a schematic of storing data in chunk leaders in the form of Merkle roots.
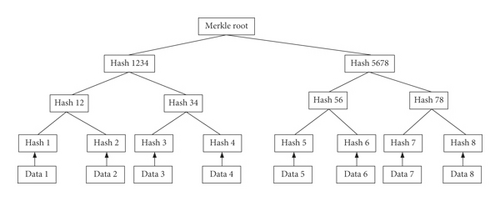
Merkle tree is also known as the hash tree, which is a tree constructed based on hash data. Merkle tree is represented as a binary tree in the blockchain. First, the hash value of each transaction is calculated to get Hash1, Hash2, Hash3, and Hash4, and then, Hash1, Hash2, Hash3, and Hash4 are combined into one string, respectively. To get the subhash, Hash12 and Hash34 are calculated, then Hash12 and Hash34 are combined to calculate the hash, and it is pushed up to get the Merkle Root. To verify whether the two pieces of data are consistent, it only needs to compare whether the Merkle roots of the two pieces of data are consistent. If they are the same, it means that the two pieces of data are the same; otherwise, it can look down from the root of the tree where the data have changed. Using the Merkle tree in the blockchain can record all transaction information. This transaction information is related to each other, and any modification of transaction information will affect the change of Merkle root, thereby effectively preventing information tampering. The performance comparison table of the SHA family algorithm in the hash algorithm is shown in Table 2.
| Algorithm name | SHA-1 | SHA-244 | SHA-256 | SHA-346 | SHA-512 |
|---|---|---|---|---|---|
| Information summary length | 160 | 244 | 256 | 384 | 512 |
| Packet length | 512 | 512 | 512 | 512 | 512 |
| Word length | 32 | 32 | 32 | 64 | 64 |
| Number of steps | 80 | 64 | 64 | 80 | 80 |
2.1.3. P2P Network
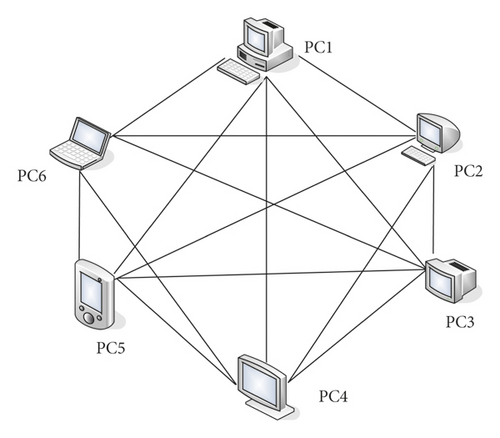
P2P network is also one of the key technologies in the blockchain. Each node in the P2P network mainly uses sockets for network communication programming. P2P network models are mainly divided into the following types, centralized, purely distributed, hybrid, and structured P2P networks. The centralized structure is simple and easy to implement. The purely distributed structure, as the name implies, removes the central node and randomly establishes a network between nodes in the P2P network. In this way, there will be no problems such as poor scalability and a single point of failure in a centralized network. However, it also has problems such as flooding circulation and response to storms in the process of message dissemination. A hybrid network is actually a hybrid of a collective network and a purely distributed network. The bitcoin network also currently uses a hybrid network. The random distribution of nodes in a structured network is different from a pure distributed network. It is distributed according to a certain structure, such as forming a tree network or a mesh network. At present, structured networks are basically constructed based on the idea of distributed hash tables. It was mentioned that the bitcoin network is composed of hybrid P2P. Each node in it contains the function of routing. However, not every node includes functions such as wallet, mining, and storage of blockchain data. Among them, the node containing the complete transaction data of the blockchain is called the master node. In addition, nodes that store part of the data in the blockchain database become light nodes. A schematic diagram of the P2P network architecture is shown in Figure 5. P2P networks can provide higher security than the traditional client-server model. A large number of distributed nodes on the blockchain makes them virtually immune to denial-of-service (DoS) attacks.
2.1.4. Consensus Mechanism
At present, there are mainly the following types of consensus mechanisms: PoW, PoS, DPoS, and PBFT. The existing consensus mechanism will be introduced in detail.
The proof-of-work (PoW) mechanism is the main mechanism, and the computing power of the system is provided by each node. Through the competition mechanism, nodes with strong computing power are more likely to be rewarded by the system. In bitcoin, miners calculate the SHA-256 hash value twice in the block header to find a random value that matches the target. If successfully found, the miner releases the block it packs, retrieves, verifies other nodes, and sends it to another block account. The advantage of PoW is that nodes can freely enter and exit, allowing more users to participate in mining and improving system stability. The downside is that it consumes more energy and more electricity. As the cost of mining increases, more miners leave the system, and the lack of computing power directly affects the security of the system.
The essence of PoW is that other nodes coordinate the content of the chain by calculating the hash value to match its attributes to obtain account permissions and add transmission information to the blockchain. Although POW can align the nodes in the bitcoin system, this method wastes a lot of energy and computing power and is inefficient. To support the continuous operation of the chain, the potential “51% attack” risk is that some nodes may obtain more than 51% of the computing power. It is more likely to obtain accounting rights than other nodes, thus threatening the normal process of bitcoin transactions.
Proof-of-stake (POS) mechanism does not require computing power to mine. The PoS mechanism introduced the concept of “coin age” for the first time. Whoever owns the older the currency, the greater the probability of who gets the right to bookkeeping. By keeping the blockchain product client online, users will be able to obtain additional currency. The PoS mechanism is relatively energy efficient and does not need to spend a lot of electricity and energy.
Proof of stake is a voting mechanism. Compared with the excessive waste of computing resources in the PoW consensus mechanism, the PoS consensus algorithm only needs to perform a small amount of calculations to ensure the normal operation of the blockchain. Its advantage is energy saving, and it is more decentralized than the PoW consensus mechanism, saving a lot of computing resources. But at the same time, because of its nature, it is still mining, which cannot be commercially used. The comparison between PoW and PoS consensus mechanism is shown in Table 3.
| Indicators | PoW | PoS |
|---|---|---|
| Throughput | < = 6 | 5–10 |
| Time delay | Minute level | Minute level |
| Energy consumption | Very high | General |
| Transaction confirmation time | 10 min | 10 min |
| Transaction cannot be changed at any time | 60 min | 60 min |
A raft cluster typically contains five server nodes, which allow two nodes to simultaneously crash. Server nodes have three states: leader, follower, and candidate. There is only one leader in a term, and the leader is responsible for handling all customer requests.
DPoS first appeared in BitShares. Shareholders vote for a certain number of trusted accounts based on the percentage of the number of cryptocurrencies they own, and the trusted accounts generate blocks in order. If the block cannot be generated within a given time, then the accounting right will be transferred to the next person. Shareholders can vote to replace these trusted accounts at any time. If these accounts gain illegal benefits or have unstable computing power, they will be kicked out of the system and other representatives will replace them. The DPoS mechanism makes transaction confirmation and verification faster. However, blockchain products based on the DPoS mechanism will have the problem that shareholders are not motivated to vote.
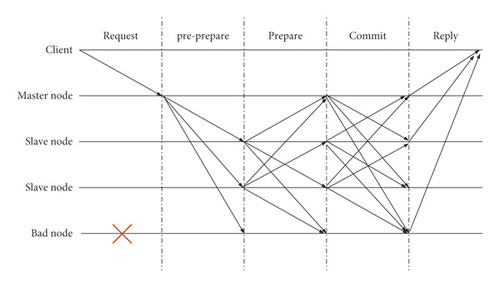
PBFT is suitable for application scenarios where consensus needs to be reached when there are byzantine nodes (faulty nodes) in a distributed system. Assuming that there are at most f byzantine nodes, when the total number of nodes N is greater than or equal to 3f + 1, PBFT can still maintain the consistency of information. PBFT is used in alliance chains or private chains where byzantine nodes exist. The byzantine problem mainly involves consistency and correctness, and each node of the blockchain is not able to globally obtain unique data from that centralized object, and to ensure the consistency of data across the network; then, the whole system must have a unified protocol and mechanism, i.e., consensus mechanism.
The consensus algorithm is compared in the following aspects, and the results are shown in Table 4.
| Feature | Paxos | Raft | DPoS | PoS | PoW | PBFT |
|---|---|---|---|---|---|---|
| Byzantine fault tolerance | × | × | √ | √ | √ | √ |
| Centralization | × | √ | × | √ | √ | × |
| Carry more transaction volume | √ | √ | × | × | × | √ |
| Faster confirmation speed | √ | √ | × | × | × | √ |
| Energy efficient | √ | √ | × | × | × | √ |
| Encourage development | √ | √ | √ | √ | × | √ |
The schematic diagram of the consensus protocol of the PBFT algorithm is shown in Figure 6.
2.1.5. Introduction to Mainstream Blockchain Platforms
There are many ways to implement blockchain. The two mainstream blockchain platforms are Hyperledger and Ethereum.
(1) Hyperledger. Hyperledger (Hyperledger) does not allow unknown identities, and participating members must be registered through MSP (Membership Service Provider). The certainty of membership lays a foundation for the network environment of mutual trust for the cooperation of all parties involved and the credibility of data. Hyperledger provides a flexible and extensible framework based on modularization and supports pluggable components. Users can replace and upgrade components according to actual application scenarios and project requirements. The unique “channel” concept of Hyperledger allows some participants to create separate chains. The data between the chains are isolated from each other, and the data can be stored in different chains according to the rules. Maintained by the corresponding participants, the “channel” takes into account the sharing and confidentiality of data. Because of the advantages of Hyperledger's alliance chain attributes and user authentication mechanism, channel design, and modular architecture, it can provide better data security and system flexibility.
(2) Ethereum. Ethereum (Ethereum) is a resonance network composed of member computers worldwide. Its ultimate goal is to allow the world to use this as a carrier to more quickly realize the establishment of a blockchain platform. For this, it created “Ether” (also known as “Bitcoin 2.0”) as an incentive currency to support the operation of the application. Ether is a technology that sends cryptocurrency to anyone by paying a small fee. Based on it, you can also create various applications that are never down and available to everyone. It is a programmable blockchain that belongs to the whole world. Ether builds on the innovations brought by bitcoin while making many improvements. While both allow you to use the digital currency without the support of a payment service provider or bank, Ether is programmable, so you can build other different digital assets—even bitcoin—based on it. The Ethereum architecture diagram is shown in Figure 7.
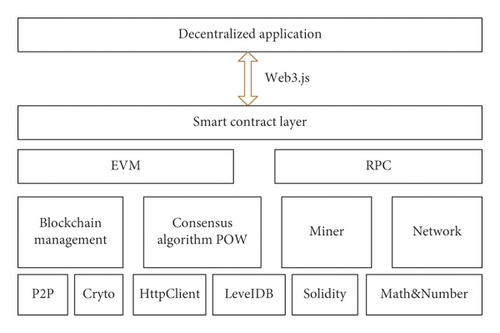
The blockchain platform used for this study is the Hyperledger Fabric, which is a licensed member and supports rich queries to immutable distributed ledgers, modular architecture with support for plug-in components, and protection of digital keys and sensitive data.
2.2. Wireless Communication Network
As one of the mainstream communication methods nowadays, the wireless communication network can not only save a lot of hardware equipment but also can transmit over long distances, which brings great convenience to people. Moreover, in the construction of this blockchain system platform, it is indispensable to use the wireless communication network, and the transmission of data and the interaction of information also play an important role in the platform. Therefore, the wireless communication network determines whether the data can be transmitted, displayed, and interacted in real time. When selecting a wireless communication network, a safe, reliable, and efficient wireless communication network should be deployed according to the characteristics and design requirements of the system.
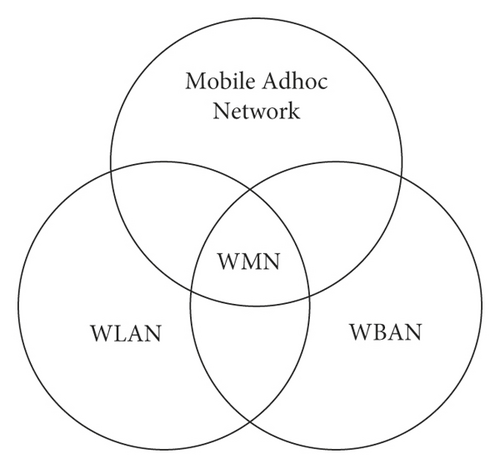
The wireless communication network used this time is a wireless mesh network. Generally, wireless mesh networks can be divided into the following three network structures: flat network structure, multilevel network structure, and hybrid network structure. Among them, the planar network structure is mainly composed of interconnections between various terminal nodes. The multilevel network structure is mainly composed of routing nodes directly interconnected with terminal nodes. The hybrid network structure has not only the interconnection between terminal nodes but also the interconnection between routing nodes and terminal nodes. The relationship diagram between wireless network and wireless local area network, ad hoc network, and WBAN is shown in Figure 8.
The nodes in the wireless mesh network are interconnected with high broadband and high utilization, the APs are self-configuring and self-healing, and the mesh is compatible with wireless client terminals. The network is easy to install, non-line-of-sight transmission, and robust network.
3. Targeted Poverty Alleviation Methods in the Agricultural Sector
In the process of precise poverty alleviation, there are still problems of poor population identification accuracy, insufficient data authenticity, nontransparent use of poverty alleviation funds, and imprecise poverty alleviation assessment. In response to these problems, this study gives some methods of precise poverty alleviation and poverty eradication.
3.1. Methods of Precision Poverty Alleviation in the Agricultural Sector
In any case, the primary task for the agricultural sector to achieve targeted poverty alleviation and alleviation is to resolve the identification and identification of the poor. For this purpose, the blockchain system will combine various information for analysis and evaluation, such as the causes of poverty and bank information. It achieves the accuracy and truthfulness of poor household data collection. The real realization of the accurate identification of the poor needs to rely on the consensus mechanism of blockchain technology. The information on the poor is not static after entering the database. Since the poor always have the opportunity to get rid of poverty, the storage information of the poor must be adjusted while ensuring that the poor can maintain their living conditions after getting out of poverty. Moreover, after the poor people enter the treasury, regular audits and rechecks must be performed so as to accurately identify the poor. After the poor have been lifted out of poverty, “Internet + Education” programs should be established while maintaining the status quo. Through online distance education and training, life skills can be improved and poverty alleviation can be made more effective. To overcome poverty, we should support wisdom and ambition and use education to stop the intergenerational transmission of poverty.
In terms of food safety, embedding the entire agricultural product supply chain into a blockchain-driven system can combine farms with intelligent agricultural systems to collect and save first-line data on agricultural production. Each product has its own unique traceable source code. The quality management and protection of agricultural products involve a wide range of areas, including the production, storage, transportation, and use of agricultural products. At present, there are quality management and safety systems for all types of agricultural products at home and abroad. However, because these systems and the actual process of organic product production, storage, transportation, and use are discrepant the response of supervisors is very weak. The full implementation of a reliable blockchain in workflow and farm management can avoid this discrepancy problem. This is particularly useful for work sharing and collaboration between producers and customers. First, the blockchain-based agricultural quality management system is the “natural” result of the widespread application of block chain in the agricultural production process and management. Second, because production factors such as land, capital, and human resources involve all aspects of labor and agricultural management, they are all registered in the “chain,” and the various links in the production, storage, circulation, and use of the internet-of-things supply chain. The “chain” storage is inconspicuous, ensuring the traceability of agricultural product information in all links. Automatic quality control of agricultural products must be implemented, early warning must be given, and problems must be solved in advance.
3.2. Experimental Test Results
We use throughput as a measurement index and use two block generation time intervals of 10 s and 20 s to evaluate the performance of the PBFT and raft algorithms, respectively. By using the Java implementation of these two algorithms in this project, running 20 times, the results obtained are shown in Figures 9 and 10.
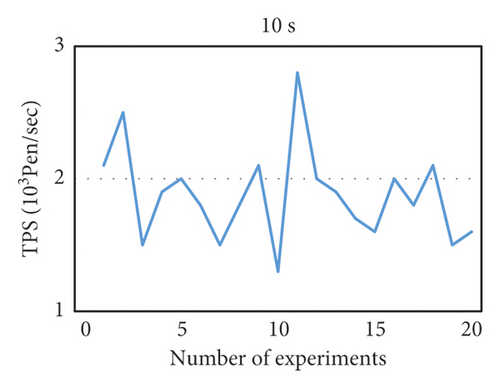
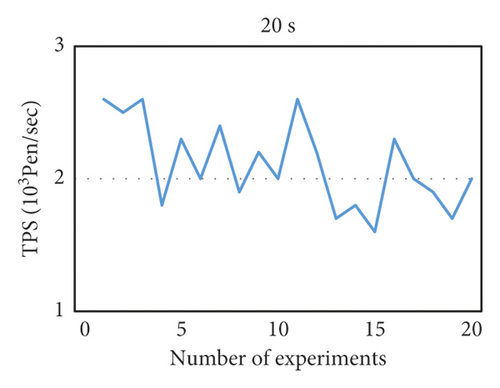
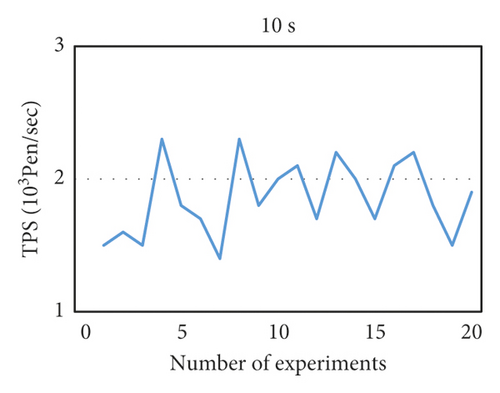
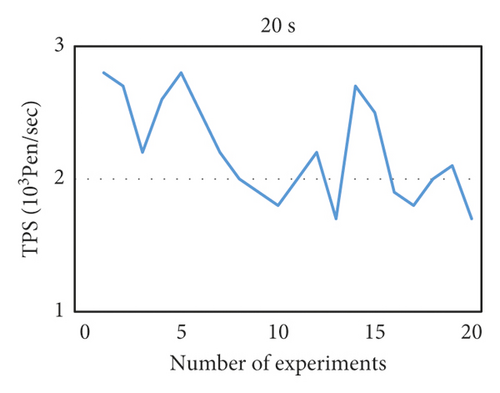
- (1)
Each message is written to the log in node. PBFT and raft are consensus algorithms for databases (logs). The blockchain application system is mainly transaction oriented, which is a lower-level technology of the blockchain.
- (2)
PBFT and raft do not consider the byzantine problem, and they are based on the trust mechanism for all nodes. If the leader maliciously tampered with the transaction information, the entire cluster will store the wrong information, which is intolerable to the transaction system.
This study uses the RBFT consensus algorithm, which is a combination of the raft algorithm and the PBFT algorithm, which is only applicable to permissioned systems (private chains) and can only accommodate faulty nodes (CFT), not evil nodes. In the case of a single node, when the system nodes are normally operating, the TPS comparison results of various blockchains when using different consensus algorithms are shown in Figure 11(a). Figure 11(b) shows the CPU usage of running POW, PBFT, and the improved RBFT consensus algorithms in the case of a single node.
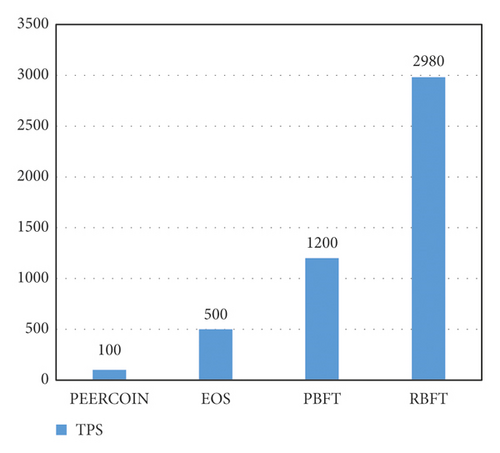
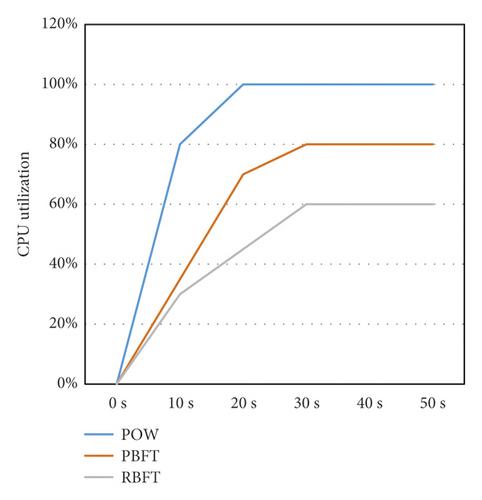
It can be seen from Figure 11(a) that the RBFT algorithm's time to reach is reduced, so the TPS of the algorithm is greatly improved compared to the PBFT algorithm. It can be seen from Figure 11(b) that the CPU usage rate of the POW algorithm quickly reached 100%, that is, the CPU is running at full capacity, while the RBFT algorithm uses the master node to generate blocks. Therefore, there is no need for computing power competition, and the CPU usage rate is significantly reduced.
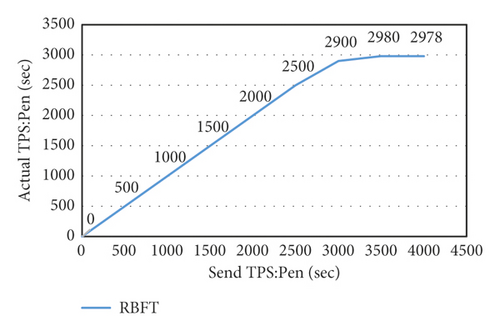
The client uses the testing tool Agile to send simulated transactions to the consensus node with different throughputs: it is sent in multiple rounds, and each round uses a sending rate to send the simulated transaction to the consensus node for 1 minute and records the response data of the formula node. The sending rate between multiple rounds is increased to obtain the data of the system under different transaction volumes and obtain the performance inflection point. The test tool Agile will record the number of confirmed transactions he has received, and the time is 60 s to calculate the RBFT throughput, as shown in Figure 12(a).
- (1)
Start the Platform
- (2)
Disconnect one of the nodes.
- (3)
Send messages to the surviving nodes to generate n blocks.
- (4)
Restart the disconnected node and calculate the recovery time based on the log timestamp.
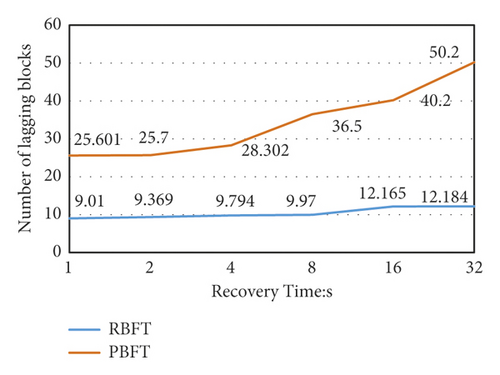
We tested the blockchain platforms equipped with RBFT and PBFT consensus algorithms, respectively, and the test results are shown in Figure 12(b).
It can be seen that RBFT has a greater advantage than PBFT in the recovery of failed nodes. For the data recovery of the same size node, taking the data recovery of a block as an example, PBFT takes about 25 seconds and RBFT only takes about 9 seconds, which is a time reduction of more than 60%. Moreover, as the number of blocks to be recovered increases, the recovery time more slowly increases than PBFT. When restoring 32 blocks of data, PBFT already takes about 50 seconds, while RBFT only takes about 12 seconds. The time consumed is only 25% of the original algorithm, which reflects higher recovery efficiency.
4. Discussion
This study is based on blockchain technology and wireless communication network technology to achieve precision poverty alleviation and poverty alleviation methods in the agricultural field. Through the understanding of wireless communication network technology and blockchain technology, this study has discovered the advantages of blockchain applications in the agricultural field. Next, this study proposes a series of solutions combining blockchain technology to solve the problems in precision poverty alleviation, food safety, and management in the agricultural field, so as to truly realize “precise poverty alleviation and poverty alleviation.”
This study has developed the traditional distributed consensus algorithm and the PBFT algorithm with polynomial execution time. On this basis, the PBFT algorithm was improved to address the shortcomings of the PBFT algorithm, and the RPBFT algorithm in the blockchain application field was formed. After experimental testing, the algorithm has the advantages of high throughput, low latency, and strong fault tolerance, which is very suitable for blockchain applications in the agricultural field.
5. Conclusions
The application of blockchain in agricultural modernization covers many aspects such as agricultural product trade and precision agriculture. In today's agricultural modernization, there are still many poor groups, and the blockchain can better integrate all the links involved in the agricultural field based on its own advantages. In this way, it is not only conducive to the circulation of agricultural products but also can save a lot of manpower and material resources and bring a huge improvement to the efficiency and economic benefits of the entire agricultural field. The core of blockchain technology lies in the consensus mechanism, and nowadays, the consensus mechanism algorithm is relatively complete. Therefore, the use of one or more consensus mechanism algorithms during research is worthy of serious consideration, and new algorithms can even be innovated according to the needs of design research. This can also provide a good idea for future blockchain technology research. However, the adoption of blockchain technology to achieve poverty eradication faces many challenges in terms of concept, technology, and law.
Conflicts of Interest
The authors declare that they have no conflicts of interest.
Acknowledgments
This work was supported by the Excellent Youth Project of Department of Education of Hunan Province of China (grant no. 20B394) and the Natural Science Foundation of Hunan Province of China (grant no. 2018JJ2277). It was also supported by the Key Project of Department of Education of Hunan Province of China (grant nos. 20A334 and 18A367).
Open Research
Data Availability
No data were used to support this study.




