A New Visual Cryptography-Based QR Code System for Medication Administration
Abstract
In health care, medication errors can result in serious health risks to patients, and hospitals require a secure medication administration system to prevent such errors. This paper therefore proposes a secure medication administration method based on threshold sharing technology. When a patient visits a doctor and the doctor prescribes n medications, a photo and the personal information of the patient are encoded into n QR code transparencies that can be decoded by common QR code scanners available for smartphones. The prescription and n QR code transparencies are then stored in a hospital’s medication administration system. When the patient receives their medicine, they can scan these n QR code transparencies using a smartphone to ensure that they have all the medicines prescribed by the doctor; this function is accessible even if the patient’s phone does not have Internet access. The main purpose of the proposed system is to prevent hospitals from giving medicine to the wrong patient, or giving less than the prescribed dosage of medicine to the patient. The focus is not on the internal medicine packaging process in hospitals but on reducing the probability of counter staff giving medicine to the wrong patient. This function is of considerable importance to non-English-speaking people who are not used to reading medicine names in English.
1. Introduction
The National Coordinating Council for Medication Error Reporting and Prevention defines a medication error as any preventable event that may lead to inappropriate medication use or patient harm when the medication is in the control of a healthcare professional, patient, or consumer [1]. Since the publication of an Institute of Medicine report on medication errors in 1999, patient advocates have focused on improving the safety of medical care in hospitals [2]. Medication errors cause health damage to at least 1.5 million people every year, and the extra cost of treating drug injuries in hospitals is $3.5 billion per year [3]. The aim of medication administration technologies is to improve patient safety by streamlining care and identifying, preventing, and mitigating medication administration incidents and adverse drug events [4]. One recent recommendation for enhancing the accuracy of inpatient medication administration is the use of bar code verification technology within an electronic medication administration system. Large-scale research results have shown that increasing the use of bar codes in a hospital’s medication administration system can greatly reduce the chance of medication errors [5]. In particular, a second check during the process of delivering drugs through bar codes or other identification devices has been applied in hospitals in Australia, and the results of a previous study have confirmed that it is indeed possible to minimize the number of medical errors [6]. In academia and industry, systems installed on smartphones to check medicines and ensure the safe use of medicine have also been developed [7–9]. Many hospitals are willing to install a bar code system to allow different personnel to repeatedly check the correctness of the drugs given by the pharmacy [10, 11]. Patients also hope to use their smartphones to help them use drugs correctly [12, 13]. The use of an integrated automated system to facilitate prescription review has been widely adopted by inpatients in major hospitals. Automated inpatient medication systems with RFID technologies have thus been implemented in many hospitals to assist professionals in double-checking drug use by inpatients [14]. However, a substantial amount of money is required to install an RFID system, and RFID systems are not easy to apply to nonhospitalized patients. For nonhospitalized patients, most hospitals rely on over-the-counter medicine dispensers to manually confirm the medicines, which is the main cause of medication errors. This paper proposes a considerably cheaper solution than RFID systems for avoiding medication errors. Today, almost everyone in many countries has at least one or more smartphones. The proposed method uses smartphones to prevent patients from making medication errors. Moreover, when a patient uses their smartphone to confirm whether the medicine received is correct and complete, since the proposed method only needs to stack received images, Internet access is not required, reducing patient’s mobile Internet access fees and ensuring that patients are able to check their prescriptions at all times.
In recent years, image processing technologies have become popular in information system applications. Many studies have focused on image representation and rendering techniques [15–21]. Using newly developed technology, photos of patients can be used to enhance their medication safety without the requirement of any additional hardware. In the proposed method, when a patient visits a doctor and is prescribed n medications, threshold sharing technology is used to encode a photo of the patient into n QR code transparencies. The prescription and n QR code transparencies are then sent to the hospital’s medication administration system. These n QR code transparencies will be, respectively, printed on the patient’s n medicine packages. A QR code transparency provides the smallest amount of information required to reveal the smallest part of the original photo. As the number of QR transparencies received increases, more parts of the patient’s photo are revealed. When all n QR code transparencies are received, an image that is sufficient to identify the patient is revealed. Each QR code transparency of the photo is associated with only one prescribed medication. When patients scan the QR code transparency of a medicine package, the smartphone obtains the QR code transparency associated with a medicine. When these QR code transparencies are stacked, an image that is sufficient to recognize the patient can be viewed on the smartphone screen, and the QR code on the image can be used to confirm the patient’s personal information. Patients need only to download a QR scanner for their smartphone to use these QR code transparencies to confirm that the medications they have received are correct. Even if a patient has no Internet access, the smartphone will still be able to display their images and personal information by scanning the QR codes. Thus, patients can scan the QR codes with their smartphone to ensure that they have all the medicines prescribed by their doctor. Hence, the probability that hospitals will give the wrong medicine to the wrong patient is reduced and patients can ensure that they received all the prescribed medicine. This function is particularly important for non-English speaking people who are not used to reading medicine names in English. Thus, although the prescription gives the medicines prescribed by the doctor in English, they are often reluctant or unable to check the medicines carefully.
Although medication safety has attracted widespread attention, most related research results from the past focused on avoiding pharmacy staff from making mistakes when packaging medicine. Regarding preventive measures to prevent medical staff from giving medicines to the wrong patients, as hospitals use RFID or QR codes [22], only inpatients are protected from being given the wrong medicine. Regarding outpatients who are not hospitalized, there is almost no way to prevent the counter staff at the pharmacy from giving medicines to the wrong patients. Among the many factors that cause medical errors, one of the factors that cannot be ignored is pharmacy staff giving medicines to the wrong patients. Sometimes, although they have not mistaken the patient [6, 23, 24], the pharmacy staff may omit some of the patient’s medicine. It is not uncommon for medical staff to mistake patients. Between 2006 and 2007, the United Kingdom National Patient Safety Agency (NPSA) received 24,382 reports of wrong patients. While there are many measures to prevent medicine packaging errors in hospitals, there are very few mechanisms in the hospital to prevent wrong patients [25]. In addition, the data collected by two Finnish hospitals from 2013 to 2014 showed that 10% of the incidents related to medicine administration were related to medicine given to the wrong patients. Of these incidents where medicines were given to the wrong patients, 77% were due to pharmacy staff not confirming the identity of the patients [26]. The reason that the medicine is given to the wrong patient is that the medical staff in the pharmacy or hospital may be familiar with the medicine, but they may not recognize the patient. Although the process of taking the medicine from the pharmacy and sending it to the counter is repeatedly checked for errors and can even be automatically completed by a machine, it may still be handed over to the wrong patient [27]. In fact, according to one survey, it was found that as many as 66.8% of the pharmacy staff in a university hospital in Finland handed over medicine without confirming the identity of the patient [28]. Recent research also confirms the need to add mechanisms to help identify patients in the current process of handing over medicines to patients, in order to ensure that medicines are not given to the wrong patients [26]. Furthermore, according to National Health Service (NHS) data, of the 5,437,999 medical incidents that occurred between 2005 and 2010, 15.6% were related to missed drugs or delayed medication [24]. Hence, it is very important for the patient or the patient’s family to confirm that they have received their own medicine and there is no missing medicine [25].
This study proposes an economical and effective way for patients to confirm whether the dispensed medicine is their own and whether the medicine has all been received. This system allows hospitals to reduce the probability of the pharmacy counter staff giving medicine to the wrong patient without being noticed by the patient. In summary, compared to the methods used in hospitals today, the proposed method can greatly improve the safety of patients using prescribed medicines, prevent patients taking medicines they have not been prescribed, and do not require hospitals to spend their budgets on new hardware devices.
The remainder of this paper is arranged as follows. Section 2 discusses related work. Section 3 describes the basic QR code concept. Section 4 describes the proposed method. Experiment results are provided in Section 5. Finally, conclusions are given in Section 6.
2. Related Work
Ensuring patient safety has always been an important issue of medicine management systems. Many large hospitals have used radio frequency identification (RFID) technology to manage the distribution of medicines. Jin et al. used Elliptic Curve Cryptography (ECC) to develop an RFID authentication scheme that could meet security requirements [29]. Yen et al. proposed two RFID technologies to prevent human errors in inpatient medicine management that can be used in online and offline environments and can prevent proof attacks. These technologies can provide auditable evidence of medication records, which can be used for medication disputes or routine medication safety audits [14]. These research results mainly rely on RFID to maintain medication safety. However, not only is RFID expensive, but it also requires additional hardware equipment in the hospital [22], and it is not suitable for outpatients who are not hospitalized. Our method can be applied to outpatients, and it does not require the hospital to add additional hardware equipment. This method only needs to print a transparency on the medicine bag when it is used, which does not increase the operating costs of the hospital.
The method proposed in this study is based on image sharing technology and uses visual cryptography to ensure that the images used cannot be viewed by patients until all the correct medicines are scanned. Visual cryptography is an image sharing technique that was first introduced by Naor and Shamir in 1994 [30]. A secret image can be encoded into n transparencies and can be revealed if at least r transparencies are stacked together. This process is called (r, n)-threshold visual cryptography. The proposed method does not require a computer or another computing equivalent for image evaluation. The secret image can be revealed by only stacking the qualified transparencies together.
However, in most studies focusing on visual cryptography, secret images are encrypted into noisy transparencies with size expansion. Chang and Hwang [31] proposed a method for generating two meaningful transparencies to easily manage transparencies or defend against malicious attack. Similarly, Ateniese et al. [32] generated meaningful transparencies through steganography. Furthermore, Hou and Wu [33] adopted the halftone and color composition/decomposition techniques to generate meaningful transparencies for gray or color images. In 2009, Chen [34] proposed a generalized random grid method for generating n distinct meaningful transparencies without size expansion. Fang [35] proposed a progressive visual cryptography method that produces meaningful transparencies.
A QR code is a two-dimensional bar code that can be easily obtained [36], for example, on leaflets or posters, often to record website addresses, and has been the focus of an increasing number of recent researches. The data embedded in a QR code can be extracted by scanning the QR code using a QR code scanner on a smartphone. A QR code can be regarded as a visible watermark that causes the degradation of image quality. Huang et al. [37] introduced a reversible data hiding method for the lossless recovery of an original image without a QR code from an image with a QR code as a visible watermark.
Unlike previous research on visual cryptography, the proposed method combines visual cryptography with QR codes so that each transparency is unable to see the original image, but the QR code can be read. Thus, the original image cannot be restored without a sufficient number of transparencies, but the QR code scanner can read the message recorded by QR code. The proposed method provides management convenience, especially for images that are not subject to QR code interference, and it allows users to carry nonsensitive information using a QR code.
3. Basic Concept of the QR Code
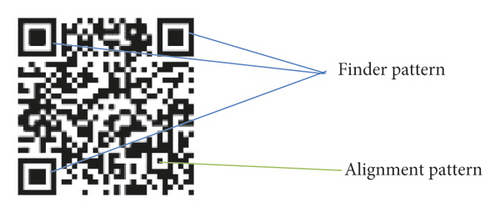
A standard QR code consists of a series of black and white blocks that form a square, as shown in Figure 1.

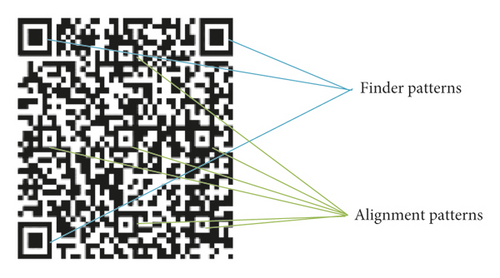
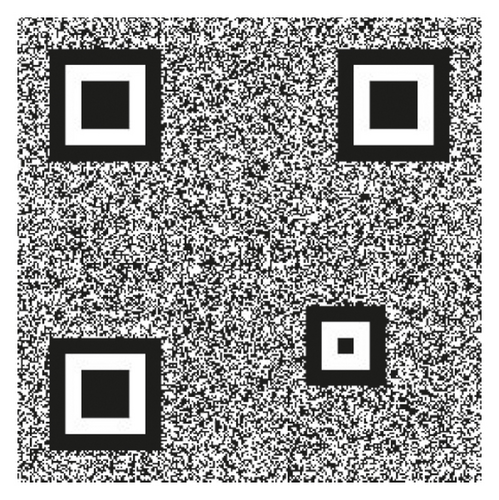
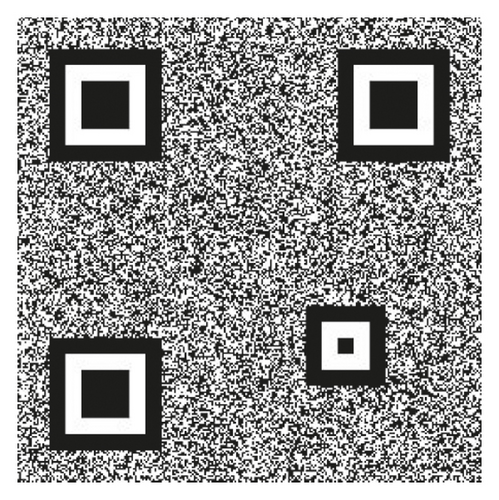
To correctly and fault-tolerantly extract data from a QR code, the decoder requires a finder and alignment patterns for locating the QR code. The finder patterns shown in Figures 2 and 3 are located at three corners of each symbol, and the alignment patterns are at fixed locations depending on the size of the QR code.
Unlike previous visual cryptography methods, the proposed method generates neither meaningful nor completely noisy transparencies. The generated transparencies also have the ability to decode QR codes. These transparencies are stacked together to reveal the secret image. Users can thus store more information, with improved management convenience using the proposed method.
If transparencies are completely noise, it is impossible to determine if they have contained errors incurred during archiving before enough transparencies have been obtained to restore the original image. Using a QR code scanner, which are now available everywhere, the proposed method has no such problems. It is especially useful for images that are not interfered with by QR code.
In this study, the (r, n)-threshold visual cryptography technique is extended to an (r, n)-threshold image sharing method, where r ≤ n. In the extended method, n QR code transparencies are generated from a patient’s photo. Parts of the initial photo are hierarchically revealed according to the number of QR code transparencies scanned. When fewer than r QR code transparencies are scanned, nothing is revealed. When between r and n QR code transparencies are scanned, a part of the initial photo is revealed. The higher the number of photo portions received, the larger is the revealed section of the patient’s photo. When n QR code transparencies are scanned, an image that is sufficient to recognize the patient and a QR code that records the patient’s personal information are revealed.
4. Proposed Method
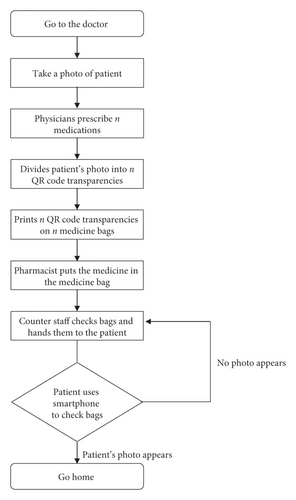
The proposed approach not only has the same properties as traditional visual cryptography but also has the ability to retrieve QR codes. With the proposed technique, when a patient goes to the doctor, the hospital staff can use a webcam connected to the computer to take a picture of the patient and store the photo in the patient’s computer file. For the proposed method, the size and source of the data are not restricted; however, to fit the QR code, the shape of the image data should be square. Assuming that a doctor prescribes n medicines to a patient, the computer automatically divides the patient’s photo into n QR code transparencies and prints them on n medicine bags separately. In order to add the QR code to the photo, the significant part of the image (the patient’s face area) should shy away from the three finder pattern blocks. In this way, when patients get their medicine, they can use the QR code scanning app on their smartphones to check whether the medicine is correct and nothing is missing. Only when the patient’s smartphone scans all n QR code transparencies will the patient’s photo appear on the phone. This action lets the patient know that these are the correct medicines and that all medicines have been received. Figure 4 shows the process of outpatient care. Due to the characteristics of visual cryptography, the decoding process does not require computing equipment. Therefore, the time needed to decode information, including the QR code decoding, is in seconds, making it effective for every patient-medicine combination, and failure seldom occurs.
In order to ensure that patients can only see their images and the QR code recording their personal information on their smartphones once all the correct medicines are scanned, a new visual cryptography method for generating meaningful QR code transparencies is proposed in this study. The aim is to ensure that patients are not shown their full patient image and the QR code recording their personal information unless they have obtained all the necessary QR codes transparencies. Let the patient’s photo be a secret image. Consider a p × q binary secret image S and a t × t QR code image Q. When using the proposed (r, n)-threshold visual cryptography method with QR code transparencies, the outputs are p × q binary stego images (G1, G2, …, Gn). In the proposed method, these stego images are printed on n medicine packages, respectively, so that users can use a smartphone to scan these images. However, the patient is not able to see any identifiable images until they scan all necessary stego images.
| Sij | [T1]ij | [T2]ij | Probability | |
|---|---|---|---|---|
| White | ■□ | ■□ | ■□ | ½ |
| ■□ | ■□ | ■□ | ½ | |
| Black | ■□ | □■ | ■■ | ½ |
| □■ | ■□ | ■■ | ½ |
Two pixels are generated in every transparency (T1 and T2) to encode each pixel of the secret image S. Therefore, the size of each transparency is twice that of the secret image. There are two encoding rules for the transparent pixels of the secret image, each with a probability of 1/2. There are also two encoding rules for the opaque pixels of the secret image, each with a probability of 1/2. However, irrespective of the two pixels in any share, the corresponding pixel of the secret image has the same probability of being black or white. In Table 1, ⊗ represents the stacking operator, and □ ⊗ □ = □, □ ⊗ ■ = ■, ■ ⊗ □ = ■, and ■ ⊗ ■ = ■ are the basic operators. The difference in the occurrence probability of the white and black pixels of the secret image can be used to obtain the stacking result. Thus, when stacking any two pixel pairs together, the result of one transparent pixel and one opaque pixel (□■ or ■□) will correspond to a white pixel in the secret image. The result of two opaque pixels (■■) corresponds to a black pixel in the secret image. The difference in the ratio of opaque pixels for every two pixels (called contrast) allows the observation of the content of the secret image. In the (2, 2)-threshold visual cryptography method, the contrast is 1/2 when two transparencies are stacked together. Moreover, to generate nonexpansible transparency, the transparent pixel is randomly selected from the two generated pixels for each encoding result.
In the second part of the proposed method, the (2, 2)-threshold nonexpansible visual cryptography method with QR code transparencies is stated. When a transparency is generated, a QR code transparency can be produced by the following process. First, the proposed method generates the QR code from the patient’s social security number or other personal information using a QR code encoder. Then, the QR code is resized to fit the size of the nonexpansible transparency. The finder and alignment patterns of the resized QR code are then retained. Next, pixels of the resized QR code are shortened, with the exception of the finder and alignment patterns. An example is illustrated in Figure 5. Finally, the transparencies are modified by filling the alignment patterns and shortened pixels of the resized QR code into the finder patterns. Through the above method, after the patient sees a doctor, if the doctor prescribes n medicines, then n QR code transparencies are generated and printed on n medicine packages, respectively. Patients thus do not need to go online and can simply scan the n QR code transparencies with a smartphone to confirm that they have received all the medicines prescribed by the doctor.


In addition to using visual cryptography to allow patients to confirm whether the medicines they received are correct and not missing any doses, the proposed method can also display QR codes. According to the EU and Indian regulations, all medicine packages must be printed with a QR code to record drug information [38, 39]. The Food and Drug Administration (FDA) also stipulates that detailed information about the medicine should be attached to the package of the medicine. Therefore, with the increasing popularity of smartphones, QR codes have been widely used to record drug information, and studies have found that users have responded well [40]. The use of QR codes on the packaging of medicines can also be applied to inpatients. Nurses sometimes need to read information about medicines to understand how to administer them. While RFID was commonly used in the past, the cost was 100 times more expensive than QR codes; therefore, the use of QR codes on the packaging of drugs to record drug information is both efficient and low-cost [22]. However, when the hospital delivers the medicine to the patient, the patient may not need the whole box of medicine, but only a few pills; thus, patients often do not receive the original medicine packaging. Therefore, in order to inform the patient about the medicine, it is very important to print the QR code on the medicine bag given to the patient by the hospital. Patients only need to install an app that scans the QR code on their mobile phones to easily read the drug information recorded therein.
In addition to recording the QR code that contains information about the medicine, it can contain the patient’s information; thus, patients can confirm whether it is their medicine bag. In Zimbabwe, the hospital records the patient’s simple case data in the QR code and prints it as a card for the patient; thus, if a patient is referred to another hospital, the receiving hospital can easily understand the patient’s condition [41]. Printing this QR code on the medicine bag eliminates the need to print a QR code card for the patient.
Based on the above, our method combines the technique of visual cryptography and QR code. In addition to allowing patients to check whether they have received all their medicine, they can also read the various information recorded in the QR code, thus reducing the risk of patients receiving the wrong medicine. While this mechanism is currently lacking in hospitals, it is much needed. Integrating patient photos and QR codes into one transparency also allows hospitals to print the information on the medicine bags faster, which is very helpful for large hospitals in Asia with a large number of patients. In addition, according to the hospital research, drug packaging has become a visual communication tool, and the color and artistic design of the appearance of the medicine bag will affect the patient’s perception of the medicine [42]. The scheme proposed herein can integrate patient photos and QR codes into a transparency, which can reduce interference with the artistic design of medicine packaging and improve the safety of patient medication.
5. Experimental Results
The results achieved using the proposed method in the experiments conducted in this study are displayed in Figures 6 and 7. Figure 6(a) depicts the original patient photo, and Figures 6(b) and 6(c) display the generated transparencies. Figure 6(d) illustrates the results of stacking the two transparencies from Figures 6(b) and 6(c). Figure 6(e) shows the QR code with the string ASZ192384563 embedded. The proposed method can use a variety of personal information, such as a social security number or identity card number to generate a QR code. And it is impossible to duplicate QR code of other patients. Figures 6(f) and 6(g) illustrate the generated QR code transparencies. Figure 6(h) displays the results of receiving the two transparencies from Figures 6(f) and 6(g).





In this experiment, the computational environment adopted a i7-9750h 2.6 GHz CPU and 16 GB RAM. The encoding process can be completed in seconds and is divided into to two subprocesses. The first process is picture sharing. In our example, this subprocess required 1.46 seconds to generate the transparencies, as shown in Figures 6(b) and 6(c). The second process is embedding a QR code into the transparencies. In our example, this subprocess required 0.77 seconds to generate the QR code for the transparencies, as shown in Figures 6(f) and 6(g). In addition, the generation of the QR code shown in Figure 6(e) required 0.32 seconds. Therefore, in our example, the total process required only about 2.55 seconds to generate the QR code transparencies.
Figure 7 shows the actual results on the smartphone after scanning Figure 6. Although the QR code is displayed on the smartphone and cannot be scanned by the phone’s own camera, many QR code decoders available now have the function of scanning the smartphone’s own screen. There is a benefit to displaying personal information by scanning the QR code. Although the name of the patient will be printed on the medicine package, sometimes there will be cases where different patients have the same name. The patient will need additional information to confirm that the package belongs to them specifically. However, if a large amount of personal information is printed on the medicine package, it may be seen by other patients collecting medicine at the counter. Compared with printing personal information on the medicine package, if patients can only see their personal information by scanning the QR code transparencies, the patient’s personal privacy will be more secure. The proposed method is not lossless after the inclusion of the QR codes. However, if the patient’s smartphone can be used as a scanner, the stacking result of transparencies can be scanned; through the computation, the original image except finder patterns of the QR code can be recovered without loss.
There are four levels for assigning the QR code error correction ratio: level L (low), level M (medium), level Q (quartile), and level H (high). Level L (low) can correct at most 7% of the codewords; level M (medium) can correct at most 15% of the codewords; level Q (quartile) can correct at most 25% of the codewords; and level H (high) can correct at most 30% of the codewords. The higher the error correction ratio level of the QR code is, the more accurate it will be in use, but it may cause the area of the QR code to become larger. When combined with the patient’s photo, it will cause greater interference to the degree of image restoration. For example, in Figure 6, the QR code encoding uses level H for error correction. Figure 6(e) contains one alignment pattern; however, if it uses other levels, there will be no alignment pattern in the generated QR code. The QR codes by assigning the four error correction levels are shown in Figure 8.




The corresponding QR transparency stacking results are shown in Figure 9. It can be seen that, in error correction levels L, M, and Q, there is no alignment pattern and the face of the patient is completely shown. At error correction level H, the face of patient is partially shaded with an alignment pattern; however, its error correction ability is better than other levels.




Table 2 shows the comparison of the execution times for the QR code transparencies among error correction levels L, M, Q, and H. It can be seen that when level H is assigned, the execution time is obviously longer than when other levels are assigned.
| Level L | Level M | Level Q | Level H | |
|---|---|---|---|---|
| QR code generation | 0.25 | 0.26 | 0.26 | 0.31 |
| Picture sharing | 1.34 | 1.35 | 1.35 | 1.46 |
| Embedding QR code into transparencies | 0.57 | 0.57 | 0.57 | 0.79 |
| Total | 2.16 | 2.18 | 2.18 | 2.56 |
6. Conclusions
In this study, an image sharing-based solution is presented for securing medication administration to patients. Patients can use a smartphone to scan QR code transparencies printed on each medicine to ensure that they receive all the medicines prescribed by the doctor. The proposed method can help prevent patients from taking the wrong medicine, thereby ensuring patient safety. The method can be used with existing hardware in hospitals and smartphones, which are very popular today. The proposed method is therefore practical and competitive with other schemes. In order to accommodate the computing power of low-cost smartphones, we propose a visual cryptography solution that only requires stacking operations; however, this will inevitably cause image distortion, since our system has not yet been certified by the competent authority. At present, the proposed scheme has not been implemented in a hospital; therefore, in our future work, we intend to cooperate with hospitals to implement the proposed scheme after obtaining the certification of the competent authority, evaluate the patient’s acceptance of proposed scheme, and examine the effectiveness of the proposed scheme for improving medication safety.
Conflicts of Interest
The authors declare that they have no conflicts of interest.
Open Research
Data Availability
The image data used to support the findings of this study are included within the article.




