Null Field and Interior Field Methods for Laplace’s Equation in Actually Punctured Disks
Abstract
For solving Laplace’s equation in circular domains with circular holes, the null field method (NFM) was developed by Chen and his research group (see Chen and Shen (2009)). In Li et al. (2012) the explicit algebraic equations of the NFM were provided, where some stability analysis was made. For the NFM, the conservative schemes were proposed in Lee et al. (2013), and the algorithm singularity was fully investigated in Lee et al., submitted to Engineering Analysis with Boundary Elements, (2013). To target the same problems, a new interior field method (IFM) is also proposed. Besides the NFM and the IFM, the collocation Trefftz method (CTM) and the boundary integral equation method (BIE) are two effective boundary methods. This paper is devoted to a further study on NFM and IFM for three goals. The first goal is to explore their intrinsic relations. Since there exists no error analysis for the NFM, the second goal is to drive error bounds of the numerical solutions. The third goal is to apply those methods to Laplace’s equation in the domains with extremely small holes, which are called actually punctured disks. By NFM, IFM, BIE, and CTM, numerical experiments are carried out, and comparisons are provided. This paper provides an in-depth overview of four methods, the error analysis of the NFM, and the intriguing computation, which are essential for the boundary methods.
1. Introduction
For circular domains with circular holes, there exist a number of papers of boundary methods. In Barone and Caulk [1, 2] and Caulk [3], the Fourier functions are used for the circular holes for boundary integral equations. In Bird and Steele [4], the simple algorithms as the collocation Trefftz method (CTM) in [5, 6] are used. In Ang and Kang [7], complex boundary elements are studied. Recently, Chen and his research group have developed the null filed method (NFM), in which the field nodes Q are located outside of the solution domain S. The fundamental solutions (FS) can be expanded as the convergent series, and the Fourier functions are also used to approximate the Dirichlet and Neumann boundary conditions. Numerous papers have been published for different physical problems. Since error analysis and numerical experiments for four boundary methods are our main concern, we only cite [8–14]. More references of NFM are also given in [10–12, 14–17].
In [17], explicit algebraic equations of the NFM are derived, stability analysis is first made for the simple annular domain with concentric circular boundaries, and numerical experiments are performed to find the optimal field nodes. The field nodes can be located on the domain boundary: Q ∈ ∂S, if the solutions are smooth enough to satisfy u ∈ H2(∂S) and uν ∈ H1(∂S), where uν is the normal derivative and Hk(∂S) (k = 1,2) are the Sobolev spaces; see the proof in [17]. It is discovered numerically that when the field nodes Q ∈ ∂S, the NFM provides small errors and the smallest condition numbers, compared with all Q ∈ Sc. Moreover for the NFM, the conservative schemes are proposed in [15], and the algorithm singularity is fully investigated in [16]. In fact, the explicit algebraic equations can also be derived from the Green representation formula with the field nodes inside the solution domain. This method is called the interior field method (IFM).
In addition to the NFM and IFM, the collocation Trefftz method (CTM) and the boundary integral equation method (BIE) are effective boundary methods too. Three goals are motivated in this paper. The first goal is to explore the intrinsic relations of NFM, IFM, CTM, and BIE with an in-depth overview. So far, there exists no error analysis for the NFM. The second goal is to derive error bounds of the numerical solutions by the NFM. The optimal convergence (or exponential) rates can be achieved. The third goal is to solve a challenging problem: Laplace′s equation in the circular domains with extremely small holes, which are called the actually punctured disks in this paper. Four boundary methods, NFM, IFM, CTM, and BIE, are employed. Numerical experiments are carried out, and comparisons are provided. It is observed that the CTM is more advantageous in the applications than the others.
Besides, the method of fundamental solutions (MFS) is also popular in boundary methods, which originated from Kupradze and Aleksidze [18] in 1964. For the MFS, numerous computations are reviewed in Fairweather and Karageorghis [19] and Chen et al. [20], but the error and stability analysis is developed by Li et al. in [21, 22]. Both the CTM and the MFS can be applied to arbitrary solution domains. However, the MFS incurs a severe numerical instability for very elongated domains [22]. Since the performance of the CTM is better than that of the MFS, reported elsewhere, we do not carry out the numerical computation of the MFS in this paper. Moreover, the null-field method with discrete source (NFM-DS) is effective and popular in light scattering (see Wriedt [23]), where the transition (T) matrix is provided in Doicu and Wriedt [24]. In fact, the null field equation (NFE) of the Green representation formula in (9) can be employed on a source outside the solution domain S, without a need of the FS expansions, called the T matrix method [24]. Hence, the T matrix method is valid for arbitrary solution domains. There also occurs a severe numerical instability for very elongated holes (i.e., particles). To improve the stability for this case, different sources (i.e., discrete sources) may be utilized in the NFM-DS, by means of the idea of the MFS. The techniques for improving the stability by the NFM-DS are reported in many papers; we only cite [23, 25].
This paper is organized as follows. In the next section, the explicit discrete equations of NFM, IFM, CTM, and BIE are given, and their relations and overviews are explored. In Section 3, for the NFM some analysis is studied for circular domains with concentric circular boundaries. In Section 4, error bounds are provided without proof for the NFM with eccentric circular boundaries of simple annular domains. In Section 5, numerical experiments are carried out for Laplace′s equation in the actually punctured disks. The results are reported with comparisons. In the last section, a few concluding remarks are addressed.
2. The Null Field Method and Other Algorithms
2.1. The Null Field Method
2.2. Conservative Schemes
2.3. The Interior Field Method
In [17], we prove that when u ∈ H2(∂S) and uν ∈ H1(∂S), the NFM remains valid for the field nodes Q ∈ ∂S; that is, ρ = R on ∂SR and on and (23) and (24) hold. In fact, we may use (24) only, because (23) is obtained directly from the Dirichlet conditions on ∂SR and , respectively. Interestingly, (24) is obtained from the interior (i.e., the first) Green formula in (6) only. For this reason, the interior field method (IFM) is named. Evidently, the IFM is equivalent to the special NFM. Based on this linkage, the new error analysis in Section 4 is explored.
2.4. The First Kind Boundary Integral Equations
2.5. The Collocation Trefftz Method
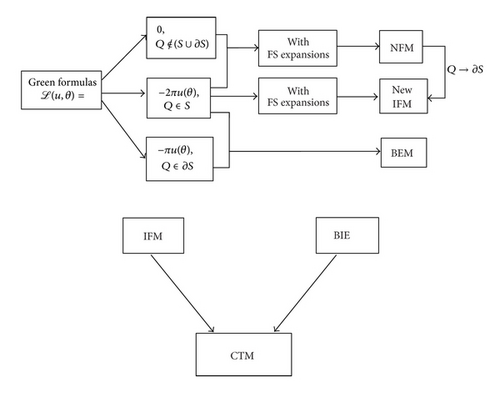
Therefore, we may classify the IFM and the first kind BIE into the TM family, and their analysis may follow the framework in [6]. However, the particular solutions (32) can be applied to arbitrary shaped domains, for example, simply or multiple-connected domains, but the functions (19) and (31) are confined themselves to the circular domains with circular holes only. The four boundary methods, NFM, IFM, BIE, and CTM, are described together, with their explicit algebraic equations. The relations of their expansion coefficients are discovered at the first time. Moreover, Figure 1 shows clear relations among NFM, IFM, BIE, and CTM. The intrinsic relations have been provided to fulfill the first goal of this paper.
3. Preliminary Analysis of the NFM
Proposition 1. For the concentric circular domains, when ρ = R + ϵ ≠ 1, the leading coefficients are exact by the NFM, and the solution errors result only from the truncations of their Fourier expansions.
4. Error Bounds of the NFM with
The NFM with the field nodes Q ∈ ∂S (i.e., ) located on the domain boundary is the most important application for Chen′s publications (see [8–14]). We will provide the errors bounds under the Sobolev norms of this special NFM for circular domains with eccentric circular boundaries without proof. Based on the equivalence of the special NFM and the CTM, we may follow the framework of analysis of Treffez method in [6]. The Sobolev norms for Fourier functions are provided in Kreiss and Oliger [31], Pasciak [32], and Canuto and Quarteroni [33].
Lemma 2. Let (64) be given, for ∂SR = ℓR; there exist the bounds of the remainders of (69)
We can prove the following lemma similarly.
Lemma 3. Let (64) be given, for ; there exist the bounds of the remainders of (72)
We have the following theorem.
Theorem 4. Let (64) and R ≠ 1 hold. For the solution uN,M from the TM in (36), there exists the error bound
5. Numerical Experiments
5.1. IFM and Its Conservative Schemes
Consider the model problem with R = 2.5 and R1 = 1 and then shrink the interior hole by decreasing radius R1 from 1 down to 10−4. This reflects that Laplace′s equation may occur in an actually punctured disk, where there may be a very small hole but not as a solitary point. For the conservative schemes of the IFM, the errors, condition numbers, and the leading coefficients are listed in Tables 1 and 2, where δ = u − uM−N. For R1 = 0.1,0.01,0.001,0.0001, the optimal results are marked in bold. We also note that when R1 decreases, the errors decrease and the condition numbers increase. Table 2 lists the leading coefficients, p0, p1, and . All tables are computed by MATLAB with double precision.
| R1 | (M, N) | ∥δ∥∞,∂S | ∥δ∥0,∂S | Cond | Cond_eff |
|---|---|---|---|---|---|
| 1 | (24, 12) | 1.52 (−8) | 1.54 (−8) | 8.48 (1) | 2.70 (1) |
| 0.5 | (24, 12) | 4.90 (−11) | 4.70 (−11) | 2.64 (2) | 1.30 (2) |
| 0.1 | (24, 8) | 6.81 (−12) | 6.67 (−12) | 1.62 (3) | 9.21 (2) |
| 0.1 | (24, 7) | 6.81 (−12) | 6.67 (−12) | 1.39 (3) | 7.89 (2) |
| 0.1 | (24, 6) | 6.81 (−12) | 6.83 (−12) | 1.16 (3) | 6.58 (2) |
| 0.1 | (24, 5) | 2.40 (−10) | 9.34 (−11) | 9.34 (2) | 5.26 (2) |
| 0.1 | (24, 4) | 1.58 (−8) | 6.10 (−9) | 7.05 (2) | 3.95 (2) |
| 10−2 | (24, 6) | 3.69 (−12) | 3.62 (−12) | 1.97 (4) | 1.16 (4) |
| 10−2 | (24, 5) | 6.69 (−12) | 3.62 (−12) | 1.57 (4) | 9.26 (3) |
| 10−2 | (24, 4) | 3.69 (−12) | 3.62 (−12) | 1.18 (4) | 6.94 (3) |
| 10−2 | (24, 3) | 6.10 (−10) | 7.63 (−11) | 7.91 (3) | 4.63 (3) |
| 10−2 | (24, 2) | 4.80 (−7) | 6.00 (−8) | 3.98 (3) | 2.31 (3) |
| 10−3 | (24, 5) | 2.58 (−12) | 2.53 (−12) | 2.22 (5) | 1.32 (5) |
| 10−3 | (24, 4) | 2.58 (−12) | 2.53 (−12) | 1.67 (5) | 9.93 (4) |
| 10−3 | (24, 3) | 2.58 (−12) | 2.53 (−12) | 1.11 (5) | 6.62 (4) |
| 10−3 | (24, 2) | 3.35 (−9) | 1.33 (−10) | 5.58 (4) | 3.31 (4) |
| 10−3 | (24, 1) | 3.52 (−5) | 1.39 (−6) | 1.09 (2) | 7.90 (1) |
| 10−4 | (24, 5) | 1.98 (−12) | 1.94 (−12) | 2.87 (6) | 1.72 (6) |
| 10−4 | (24, 4) | 1.98 (−12) | 1.94 (−12) | 2.15 (6) | 1.29 (6) |
| 10−4 | (24, 3) | 1.98 (−12) | 1.95 (−12) | 1.44 (6) | 8.62 (5) |
| 10−4 | (24, 2) | 2.57 (−11) | 1.97 (−12) | 7.20 (5) | 4.31 (5) |
| 10−4 | (24, 1) | 2.70 (−6) | 3.38 (−8) | 1.40 (2) | 1.03 (2) |
| R1 | (M, N) | p0 | p1 | |
|---|---|---|---|---|
| 1 | (24, 12) | 5.770780163555825 (−1) | −5.770780163555787 (−1) | 7.213475204444549 (−1) |
| 0.5 | (24, 12) | 2.806196474263354 (−1) | −2.358350543983467 (−1) | 2.834834114319612 (−1) |
| 0.1 | (24, 8) | 1.313991926276972 (−1) | −1.053200366713576 (−1) | 1.254266057498590 (−1) |
| 0.1 | (24, 7) | 1.313991926276972 (−1) | −1.053200366713574 (−1) | 1.254266057498546 (−1) |
| 0.1 | (24, 6) | 1.313991926276971 (−1) | −1.053200366713574 (−1) | 1.254266057498543 (−1) |
| 0.1 | (24, 5) | 1.313991926276971 (−1) | −1.053200366713575 (−1) | 1.254266057498583 (−1) |
| 0.1 | (24, 4) | 1.313991926276965 (−1) | −1.053200366713555 (−1) | 1.254266057489581 (−1) |
| 10−2 | (24, 6) | 7.480685008050482 (−2) | −5.984662000415889 (−2) | 7.124623469104319 (−2) |
| 10−2 | (24, 5) | 7.480685008050478 (−2) | −5.984662000415886 (−2) | 7.124623469102030 (−2) |
| 10−2 | (24, 4) | 7.480685008050478 (−2) | −5.984662000415891 (−2) | 7.124623469102347 (−2) |
| 10−2 | (24, 3) | 7.480685008050478 (−2) | −5.984662000415888 (−2) | 7.124623469085235 (−2) |
| 10−2 | (24, 2) | 7.480685008030524 (−2) | −5.984662000262044 (−2) | 7.124614851570256 (−2) |
| 10−3 | (24, 5) | 5.228968294193471 (−2) | −4.183175432150129 (−2) | 4.979970933244982 (−2) |
| 10−3 | (24, 4) | 5.228968294193472 (−2) | −4.183175432150129 (−2) | 4.979970933242725 (−2) |
| 10−3 | (24, 3) | 5.228968294193472 (−2) | −4.183175432150130 (−2) | 4.979970933271582 (−2) |
| 10−3 | (24, 2) | 5.228968294193472 (−2) | −4.183175432150118 (−2) | 4.979970873003448 (−2) |
| 10−3 | (24, 1) | 5.228968256993316 (−2) | −4.183174605594654 (−2) | |
| 10−4 | (24, 5) | 4.019180446935835 (−2) | −3.215344363673135 (−2) | 3.827790910656165 (−2) |
| 10−4 | (24, 4) | 4.019180446935836 (−2) | −3.215344363673130 (−2) | 3.827790910851808 (−2) |
| 10−4 | (24, 3) | 4.019180446935834 (−2) | −3.215344363673132 (−2) | 3.827790910677455 (−2) |
| 10−4 | (24, 2) | 4.019180446935835 (−2) | −3.215344363673135 (−2) | 3.827790909840129 (−2) |
| 10−4 | (24, 1) | 4.019180446716058 (−2) | −3.215344357372844 (−2) | |
As for the computations by the original IFM, the errors, condition numbers, and the leading coefficients are listed in Tables 3 and 4, where only the optimal results are listed. Comparing Table 3 with Table 1, the differences in terms of errors and condition number are insignificant, but the effective condition numbers are much smaller by the original IFM. Strictly speaking, the conservative schemes satisfy the flux conservative law exactly, but the original IFM does not.
| R1 | (M, N) | ∥δ∥∞,∂S | ∥δ∥0,∂S | Cond | Cond_eff |
|---|---|---|---|---|---|
| 1 | (24, 12) | 8.94 (−9) | 8.87 (−9) | 1.38 (2) | 1.85 (1) |
| 0.5 | (24, 12) | 4.90 (−11) | 4.70 (−11) | 2.67 (2) | 4.61 (1) |
| 0.1 | (24, 6) | 6.81 (−12) | 6.67 (−12) | 8.32 (2) | 5.19 (1) |
| 10−2 | (24, 3) | 3.69 (−12) | 3.63 (−12) | 5.20 (3) | 4.54 (1) |
| 10−4 | (24, 2) | 1.98 (−12) | 1.94 (−12) | 3.88 (5) | 5.57 (1) |
| R1 | (M, N) | p0 | p1 | ||
|---|---|---|---|---|---|
| 1 | (24, 12) | 5.770780163555844 (−1) | −5.770780163555829 (−1) | −1.442695040888961 (0) | 7.213475204444735 (−1) |
| 0.5 | (24, 12) | 2.806196474263354 (−1) | −2.358350543983468 (−1) | −1.403098237131676 (0) | 2.834834114319622 (−1) |
| 0.1 | (24, 6) | 1.313991926276971 (−1) | −1.053200366713573 (−1) | −3.284979815692429 (0) | 1.254266057498605 (−1) |
| 10−2 | (24, 3) | 7.480685008050476 (−2) | −5.984662000415886 (−2) | −1.870171252012620 (1) | 7.124623469101694 (−2) |
| 10−4 | (24, 2) | 4.019180446935834 (−2) | −3.215344363673133 (−2) | −1.004795111733959 (3) | 3.827790910389037 (−2) |
5.2. The CTM and the BIE
| R1 | (M, N) | ∥δ∥∞,∂S | ∥δ∥0,∂S | Cond | Cond_eff |
|---|---|---|---|---|---|
| 1 | (24, 12) | 1.58 (−9) | 1.57 (−9) | 7.62 | 3.03 |
| 0.5 | (24, 12) | 8.68 (−12) | 8.32 (−12) | 4.59 | 3.93 |
| 0.1 | (24, 5) | 1.21 (−12) | 1.19 (−12) | 1.31 (1) | 1.21 (1) |
| 10−2 | (24, 3) | 6.54 (−13) | 6.41 (−13) | 5.17 (1) | 4.39 (1) |
| 10−3 | (24, 2) | 4.57 (−13) | 4.48 (−13) | 1.93 (2) | 1.57 (2) |
| 10−4 | (24, 1) | 3.51 (−13) | 3.44 (−13) | 6.44 (2) | 5.11 (2) |
| R1 | (M, N) | a0 | a1 | ||
|---|---|---|---|---|---|
| 1 | (24, 12) | −3.219280948873607 (−1) | −7.213475204444795 (−1) | 1.442695040888962 (0) | 3.606737602222373 (−1) |
| 0.5 | (24, 12) | 3.571770447036389 (−1) | −2.947938179979336 (−1) | 7.015491185658381 (−1) | 7.087085285799036 (−2) |
| 0.1 | (24, 5) | 6.990003440487363 (−1) | −1.316500458391969 (−1) | 3.284979815692430 (−1) | 6.271330287492891 (−3) |
| 10−2 | (24, 3) | 8.286379414763349 (−1) | −7.480827500519865 (−2) | 1.870171252012619 (−1) | 3.562311734550295 (−4) |
| 10−3 | (24, 2) | 8.802186203691674 (−1) | −5.228969290187686 (−2) | 1.307242073548369 (−1) | 2.489985466613060 (−5) |
| 10−4 | (24, 1) | 9.079315551685712 (−1) | −4.019180454591526 (−2) | 1.004795111733959 (−1) | 1.913895455111127 (−6) |
| R1 | (M, N) | ∥δ∥∞,∂S | ∥δ∥0,∂S | Cond | Cond_eff |
|---|---|---|---|---|---|
| 1 | (24, 12) | 8.94 (−9) | 8.87 (−9) | 1.38 (2) | 2.66 (1) |
| 0.5 | (24, 12) | 4.90 (−11) | 4.70 (−11) | 2.67 (2) | 6.41 (1) |
| 0.1 | (24, 5) | 7.27 (−12) | 7.00 (−12) | 7.36 (2) | 8.71 (1) |
| 10−2 | (24, 3) | 3.69 (−12) | 3.63 (−12) | 5.20 (3) | 1.12 (2) |
| 10−3 | (24, 2) | 2.58 (−12) | 2.53 (−12) | 3.88 (4) | 1.22 (2) |
| 10−4 | (24, 2) | 1.98 (−12) | 1.94 (−12) | 3.88 (5) | 1.59 (2) |
| R1 | (M, N) | ||||
|---|---|---|---|---|---|
| 1 | (24, 12) | 1.405353491806680 (−1) | −5.770780163555832 (−1) | −1.442695040888961 (0) | 7.213475204444746 (−1) |
| 0.5 | (24, 12) | −1.559230197485811 (−1) | −2.358350543983469 (−1) | −1.403098237131677 (0) | 2.834834114319625 (−1) |
| 0.1 | (24, 5) | −3.051434745472195 (−1) | −1.053200366713573 (−1) | −3.284979815692429 (0) | 1.254266057498587 (−1) |
| 10−2 | (24, 3) | −3.617358170944118 (−1) | −5.984662000415891 (−2) | −1.870171252012620 (1) | 7.124623469100554 (−2) |
| 10−3 | (24, 2) | −3.842529842329820 (−1) | −4.183175432150123 (−2) | −1.307242073548368 (2) | 4.979970933294560 (−2) |
| 10−4 | (24, 2) | −3.963508627055583 (−1) | −3.215344363673110 (−2) | −1.004795111733959 (3) | 3.827790910431746 (−2) |
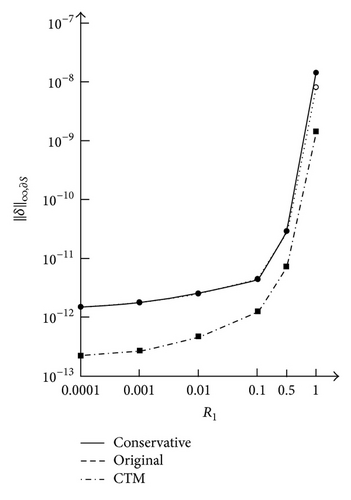
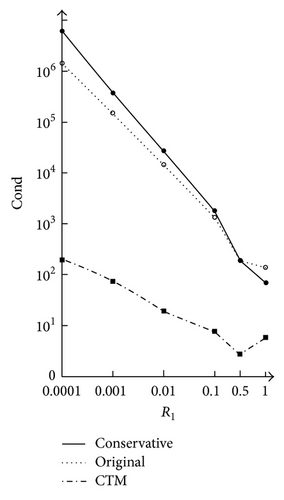
6. Concluding Remarks
To close this paper, let us make a few concluding remarks.
(1) By following [17] for the NFM, we propose the interior field method (IFM). Since all boundary methods can be applied to any annular domains, they may be used for circular domains with circular holes; in this paper, we employ the first kind boundary integral equation (BIE) in [30] and the collocation Trefftz method (CTM) in [6]. The relations of expansion coefficients among NFM, IFM, BIE, and CTM are found. The intrinsic relations among them are discovered, to show that the IFM and the BIE are special cases of CTM. Section 2 yields an in-depth overview of four methods for circular domains with circular holes.
(2) For the NFM, some stability analysis in [17] was made for concentric circular boundaries. The error analysis of the NFM is challenging. Sections 3 and 4 are devoted to the error analysis of the NFM. In Section 3, a preliminary analysis is provided. In Section 4, for the special NFM with , the error bounds are provided without proof. The optimal convergence rates can be achieved. The error analysis is important and valid in wide applications, because the special NFM offers the best numerical performance in convergence and stability; see [17].
(3) Numerical experiments are carried out for a challenging problem of the actually punctured disks. We choose NFM, IFM, CTM, and BIE and their conservative schemes. Numerical results are reported from R1 = 1 down to R1 = 10−4. Note that the popular methods, such as the finite element method (FEM), the finite difference method (FDM), and the boundary element method (BEM), may fail to handle this problem. The actually punctured disks may be regarded as a kind of singularity problems, and the local mesh refinements and other innovations of FEM, FDM, and BEM are indispensable. However, their algorithms are complicated and troublesome; see [5]. Consequently, the computation of this paper enriches the boundary methods [6].
(4) Numerical comparisons of different methods are imperative in real application. Though their numerical performances are basically the same, the CTM is best in accuracy, stability, and simplicity of algorithms. Moreover, the CTM can always circumvent the degenerate scale problems encountered in NFM, IFM, and BIE. More importantly, the CTM can be applied to any shape domains and singularity problems (see [5, 6]). In summary, three goals motivated have been fulfilled.
Acknowledgments
The authors are grateful to T. Wriedt and J. T. Chen for their valuable comments and suggestions and indebted to I. S. Lin for the computation in this paper.




