(2n − 1)-Point Ternary Approximating and Interpolating Subdivision Schemes
Abstract
We present an explicit formula which unifies the mask of (2n − 1)-point ternary interpolating as well as approximating subdivision schemes. We observe that the odd point ternary interpolating and approximating schemes introduced by Lian (2009), Siddiqi and Rehan (2010, 2009) and Hassan and Dodgson (2003) are special cases of our proposed masks/schemes. Moreover, schemes introduced by Zheng et al. (2009) can easily be generated by our proposed masks. It is also proved from comparison that (2n − 1)-point schemes are better than 2n-scheme in the sense of computational cost, support and error bounds.
1. Introduction
Subdivision is an algorithmic technique to generate smooth curves and surfaces as a sequence of successively refined control polygons. The schemes involving convex combination of more or less than six points at coarse refinement level to insert a new point at next refinement level is introduced by [1–8]. They introduced odd and even points ternary schemes. Zheng et al. [9] constructed (2n − 1)-point ternary interpolatory subdivision schemes by using variation of constants. They also introduced ternary even symmetric 2n-point subdivision schemes [10]. Mustafa and Khan [11] presented a new 4-point C3 quaternary approximating subdivision scheme. Lian [12] generalized 3-point and 5-point interpolatory schemes into an a-ary subdivision scheme for curve design. Later on, he further generalized his work into 2m-point and (2m + 1)-point interpolating a-ary schemes for curve design [13]. Mustafa and Najma [14] generalized and unified even-point n-ary interpolating and approximating subdivision schemes for any n⩾2. In this paper, we introduce an explicit formula which generalizes and unifies existing odd-point ternary interpolating and approximating subdivision schemes. A general formula which unifies odd-point and even-point n-ary interpolating and approximating schemes is still under investigation.
2. Preliminaries
3. (2n − 1)-Point Ternary Approximating and Interpolating Schemes
Here, first we present some preliminary identities then we will offer masks of (2n − 1)-point ternary approximating and interpolating schemes.
Lemma 3.1. If is Lagrange fundamental polynomial of degree 2n − 2 corresponding to nodes defined by (2.5), then
Proof. Consider
This completes the proof.
Similarly, we can prove the following lemma.
Lemma 3.2. If is Lagrange fundamental polynomial of degree 2n − 3 corresponding to nodes defined by (2.6) then
Lemma 3.3. If and are Lagrange polynomials defined by (2.5) and (3.1), then
Proof. By (3.1), for j = −(n − 1), we get
Remark 3.4. In the setting of primal parametrization, each ternary refinement of coarse polygon of scheme (2.1) replaces the old data by new data and , one to the left, the other to the right, and both at one-third the distance to the neighbours and . In other words, ternary refinement (2.1) defines a scheme whereby replaces the value at the mesh point and and are inserted at the new mesh point and , respectively.
Therefore, we can select the value of x either 1/3 or 2/3 to prove the Lemmas 3.1–3.3. In this paper, x = 1/3 has been selected. One can select x = 2/3 to proof the above lemmas. The results of the above lemmas at x = ± 1/3 are same but the final mask of the scheme obtained in reverse order. Negative values give a proper order of the mask, that have why negative values have been selected to prove the above lemmas.
Now here we present the masks of (2n − 1)-point ternary approximating and interpolating schemes.
Theorem 3.5. An explicit formula for the mask of (2n − 1)-point ternary scheme (2.1) is defined by
3.1. 3-, 5-, 7-Point Ternary Approximating Schemes
3.2. 3-, 5-Point Ternary Interpolating Schemes
- (i)
By setting n = 2 and u = β, we get the following 3-point ternary interpolating scheme:
- (ii)
If n = 3 and u = β, then by (2.1) and (3.10), we get the following 5-point ternary interpolating scheme:
3.3. Comparison with Existing Ternary Schemes
In this section, we will show that the popular existing odd-point ternary schemes are special cases of our proposed family of scheme. Here we will also compare the error bounds between limit curve and control polygon after k-fold subdivision of odd-point and even-point schemes.
3.3.1. Special Cases
- (i)
By letting u = β in (3.10), Zheng et al. (2n − 1)-point interpolating scheme [9] becomes special case of our scheme.
- (ii)
By substituting u = 2/9, and u = −7/243 in (3.15) and (3.16), we get 3-point and 5-point ternary interpolating schemes of Lian [12] respectively.
- (iii)
By substituting u = 35/6561 in (3.13), we get 7-point ternary interpolating scheme of Lian [13]. Similarly, from (3.10), we can generate (2m + 1)-point ternary interpolating schemes of [13].
- (iv)
For n = 2, and parameter u = μ + 25/72 in our proposed mask (3.13), 3-point ternary approximating scheme given in [7] becomes special case of our scheme.
- (v)
For n = 2, and u = 10/27 in (3.11), we get 3-point approximating scheme of Hassan and Dodgson [4].
- (vi)
For n = 2, b = u = 2/9 and a = u − 1/3 in (3.11), we get 3-point interpolating scheme of Hassan and Dodgson [4].
3.3.2. Error Bounds
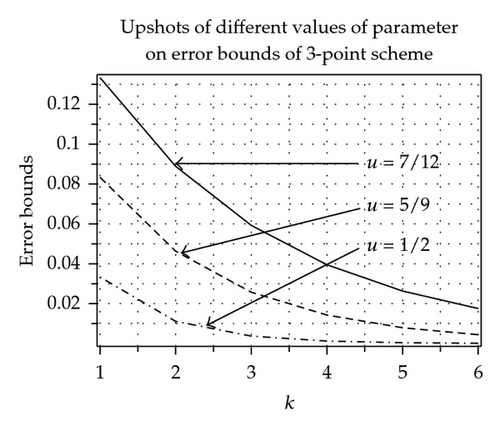
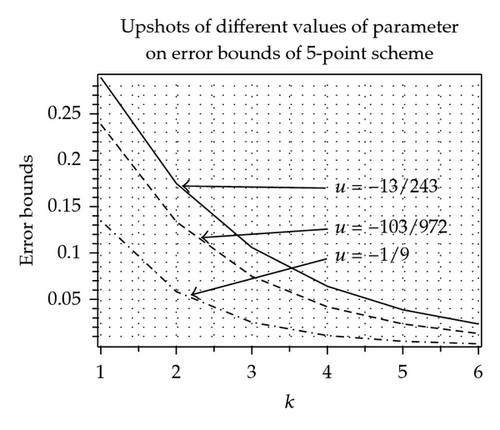
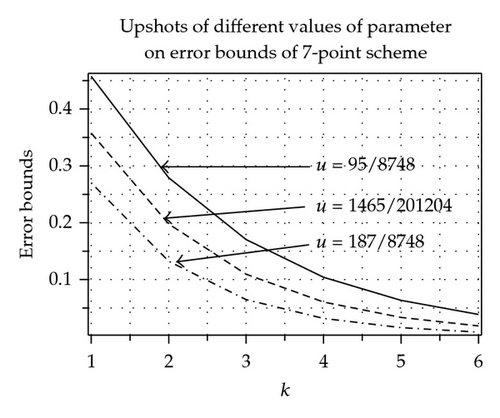
In Tables 1 and 2 by using [15], with χ = 0.1, we have computed error bounds between limit curve and control polygon after k-fold subdivision of odd-point and even-point ternary approximating and interpolating schemes. It is clear from Tables 1 and 2 that error bounds of 3-point ternary schemes (3.11) and (3.15) at each subdivision level k are less than the error bounds of 4-point ternary schemes [3, 10] at each level. Similarly error bounds of 5-point scheme (3.12) and (3.16) are less than the error bounds of 6-point schemes [10, 16]. Similar results can be obtained by comparing other odd-point and even-point schemes. Graphical representation of error bounds is shown in Figure 1.
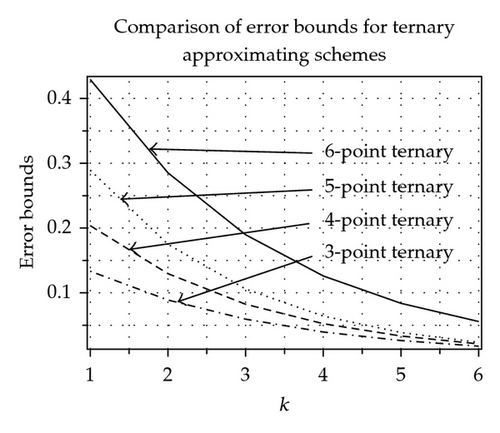

Moreover, support and computational cost of (2n − 1)-point schemes are less than 2n-point schemes. Therefore, we conclude that (2n − 1)-point schemes are better than 2n-point schemes in the sense of support, computational cost, and error bounds.
3.4. Effects of Parameters in Proposed Schemes
We will discuss three major effects/upshots of parameter in schemes (3.11)–(3.16). Effect of parameters in other schemes can be discuss analogously.
3.4.1. Continuity
The effect/upshots of parameter u in schemes (3.11)–(3.16) on order of continuity is shown in Tables 3 and 4. One can easily find the order of continuity over parametric intervals by using approach of [4].
| Scheme | Parameter | Continuity |
|---|---|---|
| 1/6 < u < 2/3 | C0 | |
| 3-point | 2/9 < u < 5/9 | C1 |
| 1/3 < u < 4/9 | C2 | |
| 5-point | −11/81 < u < −7/648 | C0 |
| −103/972 < u < −11/486 | C1 | |
| −2/27 < u < −49/972 | C2 | |
| −1/18 < u < −38/729 | C3 | |
| 7-point | 7/23328 < u < 23/729 | C0 |
| 157/52488 < u < 2501/104976 | C1 | |
| 1043/104976 < u < 67/4374 | C2 | |
| 53/8748 < u < 187/17496 | C3 | |
| Scheme | Parameter | Continuity |
|---|---|---|
| 3-point | 1/6 < u < 2/3 | C0 |
| 2/9 < u < 1/3 | C1 | |
| −11/81 < u < −7/648 | C0 | |
| 5-point | −17/324 < u < −2/81 | C1 |
| −5/108 < u < −7/162 | C2 | |
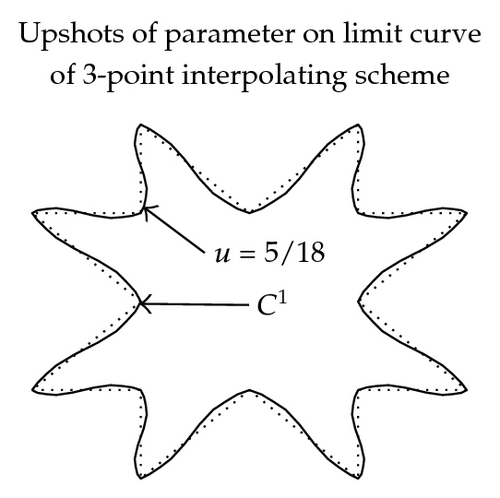
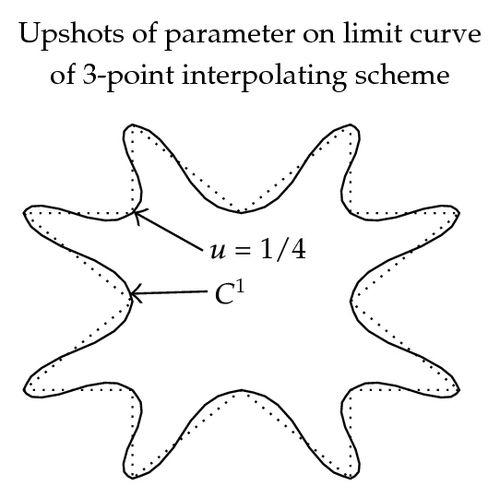
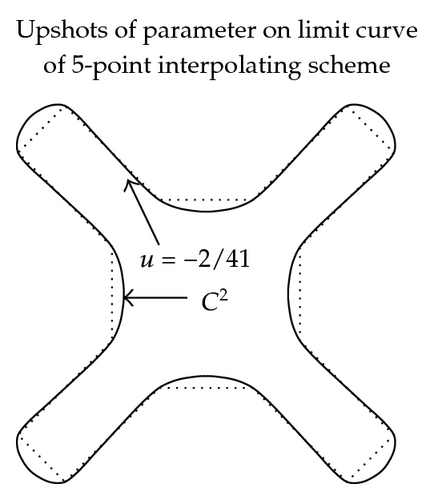
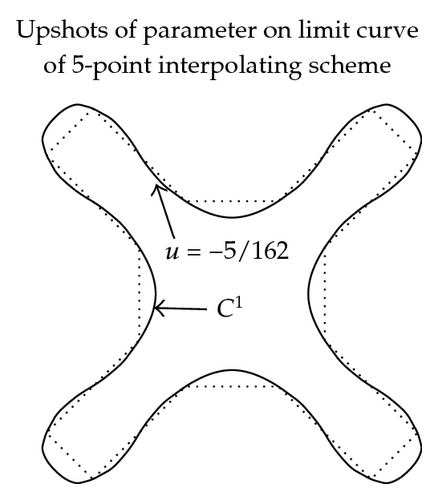
3.4.2. Shapes of Limit Curves
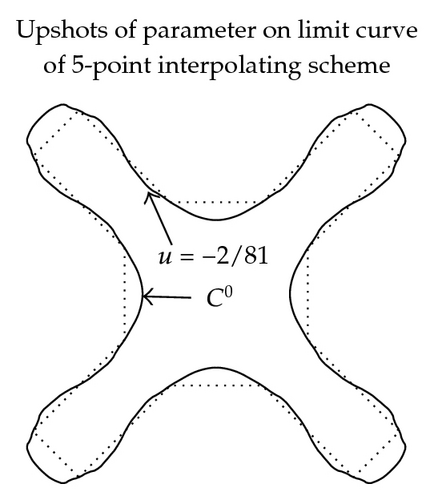
In Figure 2, the effect of parameter in (3.11)–(3.16) on graph and continuity of limit curve is shown. These figures are exposed to show the role of free parameter when 3- and 5-point approximating and interpolating schemes (3.11)–(3.16) applied on discrete data points. From these figures, we see that the behavior of the limiting curve acts as tightness/looseness when the values of free parameter vary.

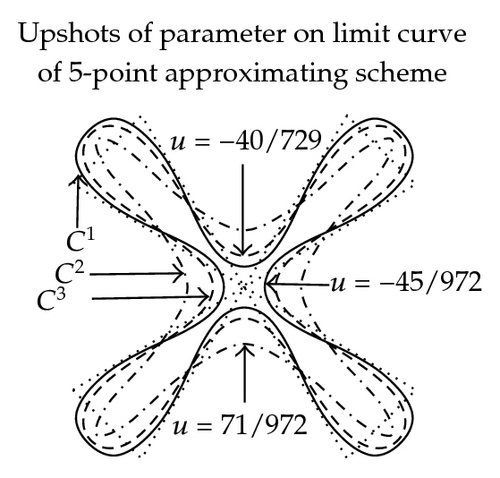
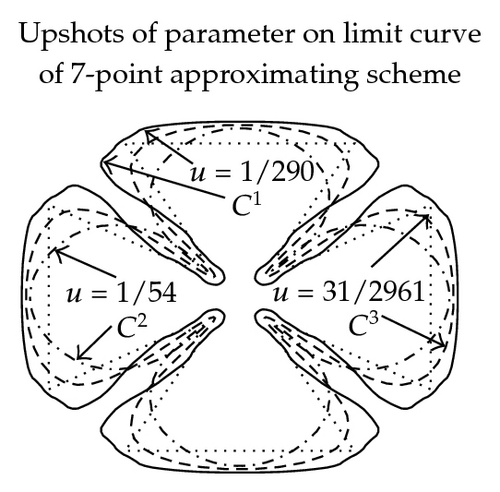
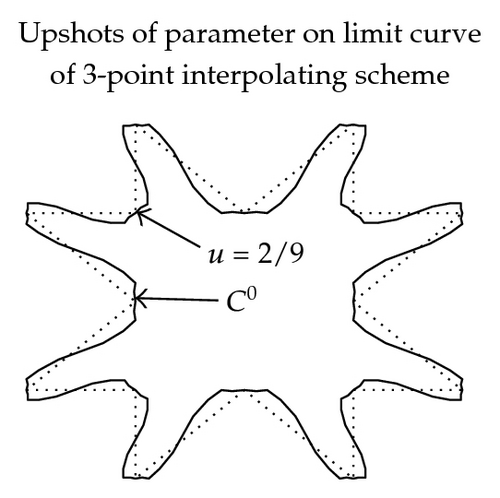
3.4.3. Error Bounds
The effects of parameter on error bounds at each subdivision level between kth level control polygon and limit curves are shown in Figure 3, Tables 5 and 6. From these tables and figures, we conclude that in case of 3-point approximating scheme continuity is maximum over 1/3 < u < 4/9 and error bound is minimum over 1/3 ≤ u ≤ 1/2. On each side of interval 1/3 < u < 4/9 continuity decreases while error bounds increases on each side of interval 1/3 ≤ u ≤ 1/2. In case of 5-, 7-point approximating scheme continuity is maximum over −1/18 < u < −38/729 and 53/8748 < u < 187/17496, while error bound is minimum at u = −13/243 and u = 95/8748, respectively.
| Scheme | Parameter | k = 1 | k = 2 | k = 3 | k = 4 | k = 5 | k = 6 |
|---|---|---|---|---|---|---|---|
| u = 1/2 | 0.033333 | 0.011111 | 0.003703 | 0.001234 | 0.000411 | 0.000137 | |
| 3-point | u = 5/9 | 0.083333 | 0.046296 | 0.025720 | 0.014289 | 0.007938 | 0.004410 |
| u = 7/12 | 0.133333 | 0.088889 | 0.059259 | 0.039506 | 0.026337 | 0.017558 | |
| u = −13/243 | 0.134953 | 0.058313 | 0.025197 | 0.010888 | 0.004704 | 0.002033 | |
| 5-point | u = −103/972 | 0.238775 | 0.133636 | 0.074792 | 0.041859 | 0.023427 | 0.013112 |
| u = −1/9 | 0.289236 | 0.174970 | 0.105846 | 0.064030 | 0.038734 | 0.023432 | |
| u = 95/8748 | 0.270022 | 0.132233 | 0.064756 | 0.031712 | 0.015530 | 0.007605 | |
| 7-point | u = 1465/201204 | 0.357567 | 0.197809 | 0.109430 | 0.060538 | 0.033490 | 0.018527 |
| u = 187/8748 | 0.457353 | 0.279180 | 0.170418 | 0.104028 | 0.063501 | 0.038763 | |
| Scheme | Parameter | k = 1 | k = 2 | k = 3 | k = 4 | k = 5 | k = 6 |
|---|---|---|---|---|---|---|---|
| u = 1/3 | 0.033333 | 0.011111 | 0.003703 | 0.001234 | 0.000411 | 0.000137 | |
| 3-point | u = 7/18 | 0.053333 | 0.023704 | 0.010535 | 0.004682 | 0.002081 | 0.000925 |
| u = 5/18 | 0.097222 | 0.054012 | 0.030007 | 0.016670 | 0.009261 | 0.005145 | |
| u = −2/41 | 0.136205 | 0.058854 | 0.025431 | 0.010989 | 0.004748 | 0.002052 | |
| 5-point | u = −7/162 | 0.169665 | 0.081691 | 0.039332 | 0.018938 | 0.009118 | 0.004390 |
| u = −1/27 | 0.257698 | 0.149528 | 0.086763 | 0.050344 | 0.029212 | 0.016950 | |
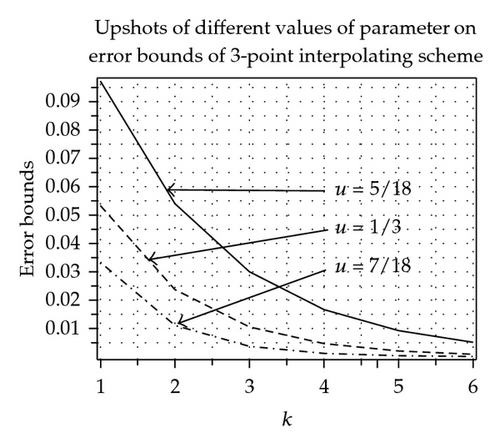
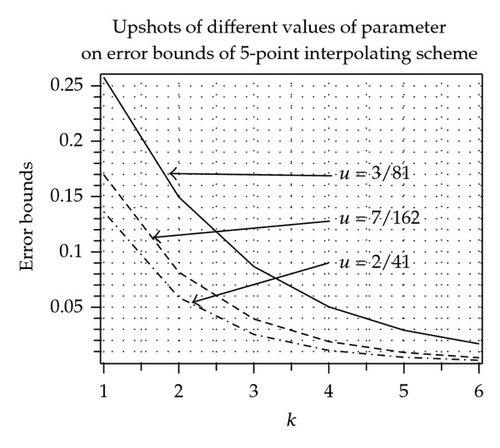
While in case of 3- and 5-point interpolating scheme continuity is maximum over 2/9 < u < 1/3 and −5/108 < u < −7/162, while error bound is minimum at u = 1/3 and u = −2/41, respectively.
3.5. Conclusion
In this paper, we offered an explicit general formula for the generation of mask of (2n − 1)-point ternary interpolating as well as approximating schemes. We have concluded from figures and tables that the (2n − 1)-point schemes are better than 2n-point schemes for n ≥ 2 in the sense of computational cost, support and error bounds. Moreover, odd-point ternary schemes of Hassan and Dodgson [4], Lian [12, 13], Zheng et al. [9], and Siddiqi and Rehan [7, 8] are special cases of our proposed masks.
Acknowledgment
This work is supported by the Indigenous Ph.D. Scholarship Scheme of Higher Education Commission (HEC), Pakistan.




