You cannot spell risk without “I-S”: The disclosure of information systems risks by Fortune 1000 firms
Abstract
Cybersecurity events can cause business disruptions, health and safety repercussions, financial costs, and negative publicity for large firms, and executives rank cybersecurity as a top operational concern. Although cybersecurity may be the most publicized information systems (IS) risk, large firms face a range of IS risks. Over the past three decades, researchers developed frameworks to categorize and evaluate IS risks. However, there have been few updates to these frameworks despite numerous technological advances, and we are not aware of any research that uses empirical data to map actual IS risks cited by large firms to these frameworks. To address this gap, we coded and analyzed text data from Item 1A (Risk Factors) of the fiscal year 2020 Securities and Exchange Commission Forms 10-K for all Fortune 1000 firms. We build on prior research to develop a framework that places 25 IS risks into four quadrants and 10 categories, and we record the number and type of IS risks cited by each firm. The risk of cyberattack is cited by virtually all Fortune 1000 firms, and the risk of software/hardware failure is cited by 90% of Fortune 1000 firms. Risks associated with data privacy law compliance are cited by 70% of Fortune 1000 firms, and risks associated with internet/telecommunications/power outage, human error, and natural disasters/terrorism are cited by 60% of Fortune 1000 firms. We perform additional analysis to identify differences in risk citation based on industry and financial measures.
1 INTRODUCTION
Cybersecurity events result in high financial costs and negative publicity for large firms (World Economic Forum, 2024). The 2019 Capital One cybersecurity breach involving 106 million records resulted in a $190 million settlement, and the 2017 Equifax cybersecurity breach involving 147 million records resulted in a $425 million settlement. The 2013 Target cybersecurity breach has resulted in cumulative costs of almost $300 million (Plachkinova & Maurer, 2018). It should be no surprise that executives of large firms rank cybersecurity as a top operational concern (Kim et al., 2018), and there is growing interest in the cybersecurity risk assessment and management practices of large firms (Marsh, 2023).
Although cybersecurity may be the most publicized information systems (IS) risk, it is only one of multiple IS risks faced by large firms (World Economic Forum, 2022). During the 1990s and 2000s, academic researchers proposed frameworks to categorize and evaluate a range of IS risks, including and beyond cybersecurity (Birch & McEvoy, 1992; Rainer et al., 1991; Smith & McKeen, 2001). However, there have been few updates to these academic frameworks over the past two decades, despite technological advances such as cloud computing and artificial intelligence (Song et al., 2021), the advent of management practices such as offshoring (Mithas & Whitaker, 2007), and societal factors such as climate change (Melville, 2010). Although multiple industry standards have been issued (ISO, 2004, 2005, 2018, 2022) and there has been some academic research to consider the perspective of individual users, Board of Directors, and financial audits and accounting (Coles & Hodgkinson, 2008; Kim et al., 2018; Parent & Reich, 2009), we are not aware of any research that uses empirical data to identify how actual risks faced by large firms map to IS risk frameworks.
To address this gap in the literature, we coded and analyzed the fiscal year 2020 Securities and Exchange Commission (SEC) Forms 10-K for Fortune 1000 firms, which are the largest firms (measured by annual revenue) publicly traded in the United States. We build on prior research to develop a framework that places 25 IS risks into four quadrants and 10 categories, and we record the number and type of risks cited by each Fortune 1000 firm. We classify the frequency of citation into five categories: very high citation (cited by 86%–99% of firms), high (66%–85%), medium (36%–65%), low (16%–35%), and very low (1%–15%). Two of the 25 risks are very highly cited by Fortune 1000 firms, one risk is highly cited, six risks are cited at a medium rate, six risks are cited at a low rate, and the remaining 10 risks are cited at a very low rate. After identifying the number and type of risks cited by firms, we perform analysis to identify differences in risk citation based on industry and financial measures.
The rest of this article is organized as follows. First, we perform a literature review to summarize industry standards and prior academic research from the risk, IS, and accounting disciplines. We provide our categorization of 25 IS risks in 10 categories across four quadrants, and we describe the process we used to code risks from 10-K reports filed by Fortune 1000 firms. We profile the Fortune 1000 firms, identify the extent to which each risk is cited, correlate financial measures with IS risks, evaluate IS risks by industry, and identify the underlying empirical factors for IS risks. We conclude by discussing implications and contributions of this research and identifying areas for future research.
2 LITERATURE REVIEW
We identified four sets of literature to study the disclosure of IS risk by publicly traded firms, including professional industry standards and academic research from the disciplines of risk, IS, and accounting. We provide a brief overview of these four sets of literature below.
2.1 Industry standards
Over the past three decades, at least four ISO (International Organization for Standardization) industry standards have been developed that play a significant role in the way that organizations conceptualize IS risks. Table 1 provides details for these four ISO standards. For example, ISO 13335 (“Information Technology – Security Techniques – Management of Information and Communications Technology Security”) was first published in 1996 (ISO, 2004). ISO 13335 presents concepts and models that can help organizations achieve a basic understanding of IS security and discusses general management issues to help organizations plan and implement IS security. During the early 1990s, the British Standard Institute (BSI) developed standard 7799 (“Code of Practice for Information Security Management”), which then became the basis for ISO 17799 (“Information Technology – Security Techniques – Code of Practice for Information Security Management”) first published in 2000 (ISO, 2005). ISO 17799 moves beyond the discussion of general management issues in ISO 13335 to present 10 security controls that would form the basis for an organization to conduct a security risk assessment. ISO 31000 (“Risk Management – Guidelines”) provides a five-part framework and five-part process for organizations to manage their IS and other risks (ISO, 2018). ISO 27002 (“Information Security, Cybersecurity and Cyber Protection – Information Security Controls”) replaced ISO 17799 and was first published in 2005 (ISO, 2022). ISO built on ISO 17799 by recategorizing and adding categories, resulting in a total of 14 security controls for organizations to use as the basis of a security risk assessment.
| ISO standard | 13335 | 17799 | 31000 | 27002 |
| Name | Information Technology ‒ Security Techniques ‒ Management of Information and Communications Technology (ICT) Security | Information Technology ‒ Security Techniques ‒ Code of Practice for Information Security Management | Risk Management ‒ Guidelines | Information Security, Cybersecurity and Privacy Protection ‒ Information Security Controls |
| Publication date(s) |
|
|
|
|
| Current status |
|
|
|
|
| Summary | Presents a set of general management issues related to ICT security, including
|
Consists of 10 security controls for information as an asset. These controls would form the basis of a security risk assessment:
|
Presents 11 principles, a five-part framework, and a five-part process to manage risk. The five part-process to manage risk is as follows:
|
Renames some ISO 13335 controls, separates a category into two categories, and adds three categories, resulting in a set of 14 security controls:
|
| Relationship with this article | This standard provides basic definitions and models. It does not articulate specific risks or standardized risk assessment and management regimes | Although this standard defines a set of controls, it does not articulate the risks intended to be managed by each control | Although this standard defines a framework and process to manage risk (not limited to cybersecurity), it does not articulate the actual risks | Although this expanded standard does allow a reader to infer some risks, it still does not articulate the primary IS risks for large organizations or specific industries |
These industry standards provide a set of best practices and discusscurrent concerns and issues related to cybersecurity risk. In general, the standards appear to be evolving toward empowering organizations to develop more sound risk analysis and management regimes. For example, the earlier ISO 13335 standard provided general definitions and basic guidance for risk assessment and management. The more recent ISO 27002 standard provides refined cybersecurity considerations related to supplier relationships and incident management. ISO 27002 also promotes a higher maturity in risk assessment and management strategies, which in turn calls for more standardization in how risk is understood and managed.
Although the standards described in Table 1 demonstrate advances in risk assessment and management, they do not articulate the specific IS risks faced by organizations. Recognizing that the ISO standards are meant to be generalizable across industries, there remains ambiguity about specific IS risks that may have higher priority or more relevance for specific industries and firms. Similarly, the standards do not supply the knowledge needed to identify whether a specific risk issue is adequately prioritized or addressed by a specific firm or industry. This article aims to complement industry standards by providing a knowledge basis for relevant risk issues across various industries and firms. This knowledge would eventually enable firms to benchmark their specific controls and the basic features of risk characterization, as discussed in Section 3.
2.2 Risk academic research
We characterize risk as (C′,Q,K) and (A′,C′,Q,K). The term A′ represents a set of specified events, C′ some specified consequences, Q a measurement or description of uncertainties, and K the knowledge that supports Q and (A′,C′) (Aven & Thekdi, 2021). A key tenet of risk assessment and risk management is the recognition that each firm is different. Each firm will have a unique set of vulnerabilities, events of concern, measured consequences, uncertainties, and knowledge (MacKenzie, 2014). These detailed risk aspects are largely assumed to be privately held and managed, outside the purview of other firms and regulators.
Although detailed information about risk aspects is often private, there are opportunities to understand high-level risk concerns that firms consider when implementing risk characterization and risk management (Lathrop & Ezell, 2017). Regulatory filings for these firms offer a comprehensive view of risk-related concerns and risk management priorities. The themes present in a firm's regulatory filings also present signals about the firm's risk-related activities. Analysis can investigate why a given firm includes some risk topic areas and not others. The presence of a particular topic area suggests a firm's publicly communicated intent to understand and manage risk related to that topic area. The absence of a particular topic area may suggest that the firm does not consider that topic area to be a material or a high-priority risk issue to be addressed, chooses to publicly downplay the risk, maintains a relatively immature risk program, or has some other motivation to not include the topic area. The language in these regulatory filings is also important, as language, tone, and other descriptors can impact investor sentiment (Tan et al., 2014).
There is need for a holistic perspective on risk-related priorities within and across firms. Due to firm-specific factors in risk characterizations combined with privacy measures, there remains little guidance on how to benchmark and generalize risk-related focus areas in high-level planning, decision-making, and resource allocation. Although individual risk characterizations may vary drastically among firms, the general landscape of high-level concerns may be more consistent within and across various sectors. However, given the qualitative nature of these filings, it remains a substantial task to derive themes from these filings across a large set of firms.
Information about the high-level risk-related priorities, including vulnerabilities, of firms allows for broader evaluation of trust among firms. For example, the information technology (IT) infrastructures of firms rely on conditional trust, which allows firms to use available information to identify risks associated with alliances (Daellenbach & Davenport, 2004), whether that alliance is pre-negotiated or created through a third party (Martínez & Durán, 2021). In addition, a broad understanding of risk-related priorities across firms is critical for investors and other stakeholders with a vested interest to understand the general landscape of IS-related risk factors. However, existing frameworks to evaluate IS largely refer to compliance with standards in firm-specific settings (Ross, 2007) or require extensive sources of firm-specific data (Tang et al., 2017).
We focus on IS as a cornerstone for firm functionality, safety, and reputation. The implications for an IS risk event can cause serious repercussions for health and safety. For example, an IS disruption for a healthcare organization can have physical safety implications for patients (Neprash et al., 2022). Disruptions within any node of a firm's network can propagate in complex ways, leading to a cascade of failures (Buldyrev et al., 2010). We believe that this article provides a useful first step in a comprehensive analysis of risk topic areas across firms.
2.3 Information systems academic research
Birch and McEvoy (1992) were among the first IS researchers to note that IS must be made subject to appropriate risk analysis and risk management. They described the purpose of risk analysis as being to assist managers in making informed decisions about IS investments, with the need to direct expenditures to reduce corporate exposure to IS risks in the context of overall business risks. Rainer et al. (1991) articulated a framework for IS risks, with the main three categories of IS risks being physical threats, unauthorized physical or electronic access, and authorized physical or electronic access, with numerous subcategories under these three main categories. Smith and McKeen (2001) proposed a more extensive framework of eight IS risk categories, including financial risk, technology risk, security risk, information risk, people risk, business process risk, management risk, external risk, and risk of success. However, there are limited details for this framework, and no data collection or analysis to demonstrate the framework. Parent and Reich (2009) extend the thinking to the role of IS governance in the firm, where IS governance objectives are to deliver value to the business and either prevent IS-based catastrophes from occurring or minimize the business consequences if an IS-based catastrophe does occur, and they articulate the related risk categories as information risk, internal and external infrastructure risk, IS project risk and IS competence risk. In the decades since this early IS research, there have been few updates to these frameworks despite technological advances such as cloud computing and artificial intelligence (Song et al., 2021), the advent of management practices such as offshoring (Mithas & Whitaker, 2007), and societal factors such as climate change (Melville, 2010), and we are not aware of any research that uses empirical data to identify how actual risks faced by large firms map to IS risk frameworks.
2.4 Accounting academic research
Richardson, Watson, and coauthors (Li et al., 2012; Masli et al., 2016) study IT material weaknesses from internal control reports required by Sarbanes–Oxley legislation. Their 2012 study provides three main categories of data processing integrity, system access and security, and system structure and usage, and their 2016 study provides five main categories of internal IT control oversight, IT capability, software development, IT architecture, and external IT control oversight, with multiple subcategories under each main category. These categories generally follow accounting industry frameworks such as COBIT (Control Objectives for Information and Related Technology), COSO (Committee of Sponsoring Organization's Internal Control Integrated Framework), and ISACA (IS Audit and Control Association). Boritz et al. (2013) developed a more extensive set of categories for IT material weaknesses based on a content analysis of auditor reports, and these categories included access, monitoring, design issues, change and development, end-user computing, segregation of incompatible functions, policies, documentation, master files, staffing sufficiency and competency, backup, operations, security (other than access), and outsourcing. Although this accounting research is worthwhile and contributes to our learning, it is important to note that an IT material weakness refers to a significant deficiency or combination of deficiencies in a company's internal control over financial reporting that could result in a material misstatement in the financial statements (Raghunandan & Rama, 2006). An IT material weakness does not mean that the firm's financial statements are misstated; it simply means that there is an increased risk of material misstatement in the firm's financial reporting.
This article builds on prior research with a grounding in formal frameworks from the risk discipline and goes beyond the impact of IS risks on financial reporting to develop a more comprehensive view for the impact of IS risks on a firm's business operations. Moreover, this article includes data from all Fortune 1000 firms, rather than a subset of firms whose auditors reported IT material weaknesses.
3 IS RISK FRAMEWORK
We now describe a framework of IS risks for Fortune 1000 firms, based on professional industry standards and academic research in the risk, IS, and accounting disciplines.
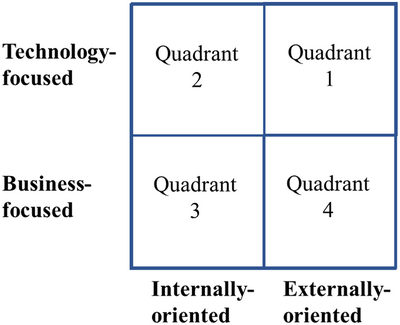
Table 2 provides a summary of our approach including references. We conceptualize IS risks in quadrants on a 2 × 2 matrix as shown in Figure 1 , where one dimension is technical versus business (Banker et al., 2022) and the second dimension is internal versus external (Nan & Tanriverdi, 2017). Of course, the dimensions are not entirely distinct, and some risks can fit across dimensions. Nonetheless, this conceptual model is a helpful start to define our 10 main IS risk categories. We now describe the quadrants in our 2 × 2 matrix, 10 main categories of IS risks in the four quadrants, and 25 IS risks. For parsimony, our narrative in this section does not duplicate the references included in Table 2.
| Quadrant | Category | Risks | Sample reference(s) |
|---|---|---|---|
| 1. Technology-external | 1A. Cybersecurity and data protection |
1A1. Cyberattack/cybersecurity breach 1A2. United States/foreign data protection laws 1A3. User error, negligence or malfeasance |
|
| 1B. Natural disasters and terrorism | 1B1. Natural disasters/terrorism |
|
|
| 1C. Emerging and advanced technologies | 1C1. Emerging/advanced technologies |
|
|
| 2. Technology-internal | 2A. Infrastructure and architecture |
2A1. Software/hardware failure 2A2. Internet/telecom/power outage 2A3. Payments 2A4. Algorithms/models |
|
| 2B. Implementation |
2B1. ERP implementation/upgrade 2B2. Integrate acquisitions |
||
| 2C. Asset protection |
2C1. Intellectual property 2C2. Insufficient insurance 2C3. Inability to detect risk |
||
| 3. Business-internal | 3A. Human capital |
3A1. IT human capital 3A2. Offshoring/geographic dispersion |
|
| 4. Business-external | 4A. Industry |
4A1. New IT-based competitors 4A2. IT industry dynamics |
|
| 4B. Licensing and vendors |
4B1. Software license/hardware purchase 4B2. Open-source software 4B3. IT/BPO providers 4B4. Data providers 4B5. Dominant platform providers |
||
| 4C. Marketing and consumer |
4C1. Electronic commerce/omni-channel 4C2. Changing consumer use of technology |
- Note: The IS risks noted in this study are mentioned repeatedly in prior research. References in this table constitute one sample reference for each IS risk and are not intended to be a complete or exhaustive list of references.
- Abbreviations: ERP, enterprise resource planning; IT, information technology; BPO business process outsourcing.
3.1 Quadrant 1: technical-external
3.1.1 Category 1A: cybersecurity and data protection/transfer
We identify four risks in this category. The risk of cyberattack or cybersecurity breach is the most well-known IS risk and the lead risk in this category. A second risk in this category is that firms may be unable to fully comply with United States or foreign laws related to data privacy and transfer, such as the General Data Protection Regulation (GDPR) in the European Union. A third risk is that an error, negligence, or malfeasance by an external user or firm employee may result in an adverse event for the firm.
3.1.2 Category 1B: natural disasters and terrorism
This category includes the risk of impact from natural disasters and terrorism on the firm's IS. It has become critically important for firms to account for extreme events such as geopolitical events and climate change as they develop and implement financial and operational strategies (Zhuang & Bier, 2007).
3.1.3 Category 1C: emerging and advanced technologies
This category includes risk related to emerging and advanced technologies such as artificial intelligence, autonomous vehicles, blockchain, drones, and machine learning, including the firm's ability to incorporate and/or adapt to these technologies.
3.2 Quadrant 2: technical-internal
3.2.1 Category 2A: infrastructure and architecture
We identify four risks in this category. One risk is related to hardware failures or errors and software failures or defects. The second risk in this category is related to the impact of an internet outage, telecommunications outage, and/or power outage on the firm's business continuity. The third risk is that the firm may not be able to accept or make electronic payment(s) due to an error or outage of the payment infrastructure. The fourth risk is the risk that IT-based algorithms or models may not work as desired, causing an adverse impact to the firm's operations or financial results.
3.2.2 Category 2B: implementation
We identify two risks in this category. One risk relates to implementing, enhancing, updating, or upgrading the firm's enterprise resource planning (ERP) system, and the other risk relates to integrating the IT systems of an acquired firm.
3.2.3 Category 2C: asset protection
We identify three risks in this category. One risk is based on the firm's ability to protect intellectual property associated with proprietary software or technology. Another risk is that the firm may not maintain sufficient insurance coverage to cover adverse IS risk events. The third risk is that the firm may not be able to detect an adverse risk event, such as an intrusion into their network.
3.3 Quadrant 3: business-internal
3.3.1 Category 3A: human capital
We identify two risks in this category. One risk is associated with the firm's ability to hire and retain the necessary IT human resources. The second risk relates to the firm's ability to coordinate its workforce across geographies, including the relatively broader scope of offshoring and the relatively narrower scope of coordinating employees working remotely during the COVID-19 pandemic.
3.4 Quadrant 4: business-external
3.4.1 Category 4A: industry
We identify two risks in this category. One risk relates to new IT-based competitors entering an industry, as IS provides the ability for new firms to rapidly scale up their business processes and achieve cost efficiencies early in their lifecycle. The second risk in this category arises from rapid changes and developments in industry dynamics due to new technologies, as IT industry developments can impact firms in other industries.
3.4.2 Category 4B: licensing and vendors
We identify five risks in this category. One risk is related to a firm's procurement for software licenses, hardware purchases, and hosting service agreements. This risk entails the risk of suboptimal contracting by the firm and suboptimal performance by the vendor. The second risk is related to open-source software which firms may use alongside or in place of commercial software. The third risk relates to IT or business process outsourcing providers (including offshore providers), as these providers must integrate their systems and processes with the client firm which could introduce performance risk or unauthorized access risk. The fourth risk relates to data providers, who supply data to the client firm through electronic interfaces, and any errors or omissions in the data can impact process outcomes for the firm. The fifth risk relates to dominant platform providers such as Amazon Web Services or Google, whose policies or processes may adversely affect firm processes and/or performance.
3.4.3 Category 4C: marketing and consumer
We identify two risks in this category. One risk is related to electronic commerce or omni-channel marketing, in which the firm may need to manage or coordinate multiple channels in addition to traditional brick-and-mortar channels. The second risk relates to the manner in which changing consumer use of personal technology (including smart phones) could adversely impact the firm.
4 DATA AND CODING PROCESS
4.1 Securities and Exchange Commission 10-K filing
This subsection provides a primer on the SEC Form 10-K filing requirements, objectives and process. All publicly traded firms headquartered in the United States are required to file a Form 10-K (“Annual report”), generally within 90 days of the end of the fiscal year (SEC, 2006). A Form 10-K provides a comprehensive summary of the firm's financial performance over the past year, including income statements, balance sheets, cash flow statements, and notes to the financial statements. In addition to financial information, the Form 10-K also provides detailed information about a firm's operations and management in sections or subsections (referred to as “items”) such as description of the business (Item 1), discussion of results of operations (Item 8), and information on corporate governance and executive compensation (Items 11 and 12). The primary purpose of a Form 10-K is to enable investors to make informed decisions about buying, selling, or holding a firm's stock or bonds.
‘Risk Factors’ includes information about the most significant risks that apply to the company or to its securities. Companies generally list the risk factors in order of their importance. In practice, this section focuses on the risks themselves, not how the company addresses those risks. Some risks may be true for the entire economy, some may apply only to the company's industry sector or geographic region, and some may be unique to the company (SEC Office of Investor Education and Advocacy, 2013, Page 2).
Firms include cautionary language to alert investors to inherent uncertainties and update their risk disclosures in subsequent years if there are material changes to risks facing the business. To facilitate readability and comprehension, many firms organize Item 1A into subsections, such as industry-specific risks, market risks, regulatory risks, operational risks, financial risks, and risks related to the firm's products or services.
There are limitations to the “Risk Factors” text data. These data are not intended to communicate detailed risk factors, perform a detailed analysis of those risks, audit whether the risk program adheres to other external standards or regulations, or understand in detail how the firm addresses those risks. Instead, these filings serve as a communication tool primarily to investors and regulators. Because firms decide which risk topic areas are material, there are grounds for scrutiny related to which risk topic areas are included and excluded. Moreover, text (in the absence of audio and video) conveys only partial information on tone and sentiment.
The data represent firm-specific views of the risk landscape, illustrating topics the firm chooses to disclose while adhering to legal/regulatory requirements. The cited risk areas may or may not be those of highest priority within the firm, and may or may not be the largest risk issues on the horizon, but are the risk issues that rise to the surface for public awareness. Thus, the data do not represent or substitute the need for a risk characterization. Instead, these data serve as a communication of risk issues. Some may view the risk issues cited in regulatory filings as those that stakeholders expect to be addressed in coming years, through risk analysis and risk management regimes.
Although misleading regulators in SEC filings can be damaging for the firm, there are gray areas in how to interpret and discuss risk issues due to uncertainties, perception-related factors, and individual contexts. Two firms with the exact same exposure to a particular risk issue could potentially have widely different interpretations, stances, and communication priorities for that risk issue, as they are illustrated in regulatory findings. Thus, language in the filings should not be seen as a direct reflection on individual risk programs within the firm.
4.2 Data process and validity
Figure 2 summarizes our research process for this article. In this subsection, we provide detail for the two highlighted subprocesses of collecting and filtering the data while maintaining data validity.
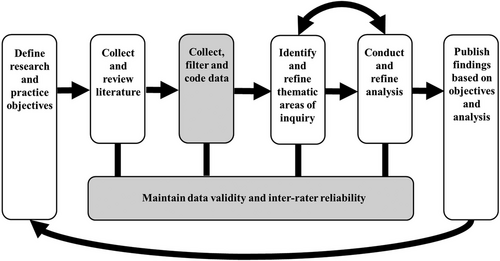
To achieve data completeness and recency, we collected data (see upper highlighted box in Figure 2) from Item 1A “Risk Factors” for all 965 of the Fortune 1000 firms that filed an SEC Form 10-K for the 2020 fiscal year. Thirty-five firms did not file a 10-K during 2020 for various reasons, such as if the firm was acquired during 2020 and was not required to file a 10-K after the acquisition. One coauthor with a Certified Public Accounting (CPA) certificate, who worked as a manager for a Big Four Accounting Firm prior to becoming a university faculty, carefully reviewed Item 1A for every firm to filter the IS-related content. In this review, the coauthor went through each subsection, paragraph, and bullet-point of Item 1A for every firm. If a subsection, paragraph and/or bullet-point contained risks related to any aspect of IS as defined in the case study scope (promoting construct validity), the coauthor filtered that subsection, paragraph, or bullet-point into a separate document without deleting the content from the original Item 1A. This careful review was designed to place all IS risk content into a dedicated repository for coding by the coauthors.
The SEC filings across firms are widely variable in length, context, structure, and level of detail. This variability could potentially contribute to issues with integrity of the data and coding process (see lower highlighted box in Figure 2). To address this issue and to maintain a consistent reasoning and rigor, the Item 1A was filtered to contain only IS-relevant material. Although this filtering reduced the amount of text requiring manual coding and ensured that the coded text was relevant to the IS-related research scope, one risk to data validity is that the data filtering was performed by one coauthor with a CPA certificate. Although we did use both coauthors to perform the coding process (see statistics on inter-rater reliability below), we do not have similar inter-rater reliability statistics for the data filtering process.
Once the IS-related content was filtered from each Item 1A, the two coauthors evenly divided the firms for subsequent coding, with about 500 firms for each coauthor including an intentional overlap of about 100 firms (about 10% of the data) to compute inter-rater reliability, which represents the degree of consistency across coders when coding the same data. Each author coded the data for their assigned firms, recording a “1” if the Item 1A IS-related content cited a risk in our framework or a “0” if the firm did not cite that risk. The coauthors communicated before and during the coding process to develop and follow a consistent coding approach.
We measure inter-rater reliability using two statistics, proportional agreement and Cohen's Kappa. Proportional agreement refers to the degree of agreement between raters based on the proportion of cases they agree upon relative to the total number of cases being assessed. The two coauthors observed proportional agreement of 0.9101 for the firms of overlap. Cohen's Kappa is a more formal measure of inter-rater reliability, which adjusts the observed proportion of agreement between raters by taking into account the proportion of agreement that could be expected by chance (Cohen, 1960). For the firms of overlap, the two coauthors achieved a Cohen's Kappa of 0.8146, which exceeds the threshold for “near perfect” agreement (McHugh, 2012). In situations where the observed proportional agreement for specific risk categories was relatively lower, the authors incorporated learning from their communication and review to recode specific risk categories for the overlap firms and remaining firms (about 450 firms per author) where necessary to ensure a consistent coding approach.
4.3 Firm profile
As discussed above, 965 of the Fortune 1000 firms filed a fiscal year 2020 Form 10-K. We collected financial data on the Fortune 1000 firms through Compustat. According to the financial data, the average revenue of Fortune 1000 firms in our data is $15.3 billion (standard deviation $36.6 billion), the average profit is $0.9 billion (standard deviation $4.3 billion), average assets are $54.4 billion (standard deviation $246.1 billion), average number of employees is 37,650 (standard deviation 104,650), and average market capitalization is $34.9 billion (standard deviation $117.2 billion). On average, each Fortune 1000 firm cited 9.5 IS risks in their Item 1A (standard deviation 4.5), with an average of 1361 words related to IS risks (standard deviation 1464). When computed by firm, the average word per risk is 196 (standard deviation 303). Table 3 shows the number of firms by industry, according to the 2-digit North American Industry Classification System (NAICS) code.
| NAICS 2-digit code | Industry description | Number of firms |
|---|---|---|
| 11 | Agriculture, forestry, fishing and hunting | 1 |
| 21 | Mining | 27 |
| 22 | Utilities | 40 |
| 23 | Construction | 48 |
| 31 | Manufacturing (nondurable goods) | 47 |
| 32 | Manufacturing (natural resource-based goods) | 97 |
| 33 | Manufacturing (durable goods) | 208 |
| 42 | Wholesale trade | 49 |
| 44 | Retail trade (e.g., grocery) | 49 |
| 45 | Retail trade (e.g., general merchandise) | 31 |
| 48 | Transportation | 37 |
| 49 | Warehousing | 2 |
| 51 | Information | 75 |
| 52 | Finance and insurance | 123 |
| 53 | Real estate rental and leasing | 34 |
| 54 | Professional, scientific, and technical services | 34 |
| 55 | Management of companies and enterprises | 1 |
| 56 | Administrative and support and waste services | 26 |
| 61 | Educational services | 2 |
| 62 | Health care and social assistance | 21 |
| 71 | Arts, entertainment, and recreation | 5 |
| 72 | Accommodation and food services | 22 |
| 81 | Other services | 2 |
| 99 | Other | 4 |
| Total | 985 |
- Note: Compustat does not list the 2-digit NAICS code for 15 of the Fortune 1000 firms.
- Abbreviation: NAICS, North American Industry Classification System.
5 MEANS ANALYSIS
Our first step is to record the percentage of firms that cite each IS risk in our framework. We categorize the citation rate based on the percentage of firms as follows: very high (86%–99%), high (66%–85%), medium (36%–65%), low (16%–35%), and very low (1%–15%). Table 4 provides a summary, with narrative on each category below.
| Quadrant | Risk | Percentage of firms (%) | Standard deviation (%) | Very high | High | Med | Low | Very low |
|---|---|---|---|---|---|---|---|---|
| 1. Technology-external | 1A1. Cyberattack/cybersecurity breach | 98.9 | 10.1 | X | ||||
| 1A2. United States/foreign data protection laws | 69.9 | 45.8 | X | |||||
| 1A3. User error, negligence or malfeasance | 61.3 | 48.7 | X | |||||
| 1B1. Natural disasters/terrorism | 56.8 | 49.6 | X | |||||
| 1C1. Emerging/advanced technologies | 9.0 | 28.7 | X | |||||
| 2. Technology-internal | 2A1. Software/hardware failure | 86.2 | 34.5 | X | ||||
| 2A2. Internet/telecom/power outage | 61.5 | 48.7 | X | |||||
| 2A3. Payments | 7.7 | 26.6 | X | |||||
| 2A4. Algorithms/models | 12.0 | 32.5 | X | |||||
| 2B1. ERP implementation/upgrade | 49.4 | 50.0 | X | |||||
| 2B2. Integrate acquisitions | 14.6 | 35.3 | X | |||||
| 2C1. Intellectual property | 23.8 | 43.2 | X | |||||
| 2C2. Insufficient insurance | 35.1 | 47.8 | X | |||||
| 2C3. Inability to detect risk events | 39.2 | 48.8 | X | |||||
| 3. Business-internal | 3A1. IT human capital | 12.6 | 33.2 | X | ||||
| 3A2. Offshoring/geographic dispersion | 27.7 | 44.8 | X | |||||
| 4. Business-external | 4A1. New IT-based competitors | 14.1 | 34.8 | X | ||||
| 4A2. IT industry dynamics | 27.5 | 44.7 | X | |||||
| 4B1. Software license/hardware purchase | 31.6 | 46.5 | X | |||||
| 4B2. Open-source software | 6.9 | 25.4 | X | |||||
| 4B3. IT/BPO providers | 54.4 | 49.8 | X | |||||
| 4B4. Data providers | 7.9 | 26.9 | X | |||||
| 4B5. Dominant platform providers | 7.2 | 25.8 | X | |||||
| 4C1. Electronic commerce/omni-channel | 14.4 | 35.1 | X | |||||
| 4C2. Changing consumer use of technology | 17.7 | 38.2 | X |
- Abbreviations: ERP, enterprise resource planning; IT, information technology.
5.1 Very highly cited IS risks
Consistent with the examples cited earlier, the risk of cyberattack or breach is acknowledged by virtually all (99%) Fortune 1000 firms. The other risk in our framework cited at a very high level (86%) by Fortune 1000 firms is hardware/software failure.
5.2 Highly cited IS risks
The only risk cited at a high level (70%) by Fortune 1000 firms is the risk of noncompliance with United States or foreign data protection laws. Consistent with the reputation risk above, this risk may also follow from the objective of SEC filings to inform investors.
5.3 Medium cited IS risks
About a quarter (six out of 25) of the risks in our framework are cited at a medium level by Fortune 1000 firms. The risk of internet/telecommunications/power outage is cited by 61% of Fortune 1000 firms. We find it interesting that the citation rate for internet/telecommunications/power outage is lower than the citation rate for hardware/software failure (86%). We wonder if this is because public infrastructure is viewed as being more reliable than hardware/software within the firm, or because public infrastructure is out of the control of the firm which may then reduce the firm's legal liability. If so, this could be one explanation for the growth of cloud computing which moves hardware/software outside the firm into a global network. The risk of human error is cited by 61% of Fortune 1000 firms. The wording used most often to cite this risk suggests that firms consider unintentional/intentional actions and employee/customer actions as part of this risk.
Fifty-seven percent of Fortune 1000 firms cite the IS risk of natural disasters or terrorism, consistent with an increasing prevalence of climate-related natural disasters and terrorism events. Fifty-four percent of Fortune 1000 firms cite IS risks posed by IT or business process outsourcing vendors, who frequently integrate their systems with the client firm's IS. Forty-nine percent of Fortune 1000 firms cite IS risks attributable to implementation, enhancement, upgrade or update of the ERP system, and 39% of firms cite the inability to detect IS risk events in a timely manner as a risk.
5.4 Low-cited IS risks
About a quarter (six out of 25) of the risks in our framework are cited at a low level by Fortune 1000 firms. The risk of insufficient insurance to cover for adverse IS events is cited by 35% of firms. This risk, along with the inability to detect IS risks noted above, relates with potential shortcomings of the firm that would not be known until the risks manifest. Risks associated with software license/hardware purchase are cited by 32% of Fortune 1000 firms, and IS risks associated with offshoring or geographic dispersion are cited by 28% of Fortune 1000 firms. Although offshoring has become a more established business practice over the last 15 years, several mentions in this area for the 2020 fiscal year relate to remote work arrangements due to COVID. Risks attributable to IT industry dynamics are cited by 27% of Fortune 1000 firms, consistent with the phenomenon that dynamics of the IT industry can impact all industries. Twenty-five percent of Fortune 1000 firms cite risks related to the protection of IT-based intellectual property, as firms use IT to develop intellectual property that is valuable to the firm. IS risks attributable to changing customer use of personal technology are cited by 18% of Fortune 1000 firms. Arranging the risks from most cited to least cited, this is the first mention of customer-related IS risks as the customer portion of human error risks cited by 61% of Fortune 1000 firms.
5.5 Very low-cited IS risks
About 40% (10 out of 25) of IS risks in our framework are cited by 15% or fewer of Fortune 1000 firms, though we believe that the low citation of these risks may be partly attributable to the tendency of Fortune 1000 firms to mimic each other in their disclosures rather than to salience of the risks. Fifteen percent of Fortune 1000 firms cite IS risks related to the integration of IT systems for acquired or merged companies. Fourteen percent of Fortune 1000 firms cite IS risks related to electronic commerce or omni-channel operations. We were surprised that this percentage was so low, though it is possible that this low percentage indicates that electronic commerce is a well-established managerial practice no longer worthy of specific mention. Fourteen percent of Fortune 1000 firms cite IS risks associated with new IT-based competitors entering their industry, consistent with the phenomenon that IT is enabling new business models and allowing new entrants to achieve some operational advantages previously only possible through scale.
IS risks related to regulations other than United States/foreign privacy laws were cited by 13% of Fortune 1000 firms, far below the 70% level citing United States/foreign privacy laws, indicating that the risk associated with privacy regulations is felt much more widely than the risk associated with other regulations. Risks associated with the ability to hire and retain IT human resources are cited by 13% of Fortune 1000 firms. The year 2020 represented a high-water mark for employment and compensation of IT professionals, and we wonder if this risk will continue to be as prominent in future years as the employment market eases. Risks associated with algorithms and models are cited by 12% of Fortune 1000 firms. Just as firms use IS to create intellectual property (cited by 25% of Fortune 1000 firms), firms also use IS to create and run algorithms and models to manage their business.
Risks associated with the ability to make or receive electronic payments were cited by 8% of Fortune 1000 firms. We are surprised that this risk was cited at such a low rate because the ability to receive payments is directly tied to revenue, though perhaps similar to internet/telecommunications/power infrastructure noted above, the electronic payment infrastructure may be viewed as reliable which could reduce firms’ inclination to cite this risk. Risks associated with data providers are cited by 8% of Fortune 1000 firms, and risks associated with dominant platform providers are cited by 7% of Fortune 1000 firms. Many large firms use data providers for parts of their business, and dominant platform providers are another emerging phenomenon (similar to new IT-based competitors) where the use of IT has a significant impact across industries. Finally, risks associated with the use of open-source software are cited by 7% of Fortune 1000 firms. We are unsure whether the relatively low rate of citations for this risk is attributable to the fact that open-source software is now a well-established business practice (similar to electronic commerce discussed above), or because large firms may be limiting their use of open-source software to specific applications because of security concerns.
6 OTHER ANALYSES
In addition to our main analysis, we performed four additional analyses to generate further insights. These additional analyses are correlation of IS risk factors with financial measures, separate analysis of means by industry, factor analysis of IS risks, and word count analysis.
6.1 Correlation of IS risk factors with financial measures
We performed a pairwise correlation of financial measures from Compustat (revenue, profit, assets, market capitalization) with each of the 25 IS risks. We were surprised that there was relatively little correlation of financial variables with IS risk factors, though this may be because there is relatively little variation in financial variables among the firms in our study, because all of the firms in our study are large publicly traded firms.
We did find some correlations worth mention, though we are careful not to attribute causality. In this subsection, the first number in each set of parentheses is the correlation coefficient, which represents the direction of a linear relationship between two variables, where a positive coefficient means that the two numbers are positively related and a negative coefficient means that the two numbers are negatively related. The second number in each set of parentheses is the p value, which represents the probability of obtaining a given coefficient if there was no relationship between the two variables. We use the generally accepted convention that a p value less than 0.05 means that the correlation is statistically significant (unlikely to occur by chance).
Firm revenue is negatively correlated with the IS risk of attracting and maintaining IT human capital (−0.07106, p < 0.0273), suggesting that firms with higher revenue may invest the financial resources to attract and maintain the appropriate IT human resources. Firm assets are negatively correlated with human error, negligence and malfeasance (−0.08265, p < 0.0102), and hardware/software failure (−0.10297, p < 0.0014), suggesting that firms with larger assets may invest more resources and effort to protect these assets. Market capitalization is positively correlated with IS risks related to payments (0.10706, p < 0.0009) and software licenses/hardware procurement (0.06884, p < 0.0325), suggesting that firms with larger market values may be more attuned to risks directly associated with the revenue (payments) and expenses (software/hardware procurement) that sustain market value.
Although not the main focus of this article, we also recorded whether each Fortune 1000 firm cited an actual cyberattack. In most cases when firms in our data cite a cyberattack, they indicate a view that the cyberattack was not material to the firm's operations or financial reporting. Although we recognize that citation of a cyberattack is not perfectly correlated with whether the firm actually experienced a cyberattack, we find it interesting that firm revenue (−0.07017, p < 0.0293) and number of employees (−0.06687, p < 0.0378) are both negatively correlated with citation of an actual cyberattack. Because we do not know the strength of correlation between cyberattack citation and actual cyberattack (though we assume that the correlation is positive), and we also do not know the willingness of firms to report actual cyberattacks (see discussion below), we are not able to know whether these negative correlations result from the fact that firms with larger revenue are better able to assemble the resources to protect against actual cyberattacks, or whether firms with larger revenues may be more reluctant to disclose actual cyberattacks (regardless of whether the cyberattack is material) because they are more concerned that an adverse public reaction could risk a loss in future revenue.
6.2 Analysis by industry
We performed a separate means analysis of IS risks by industry. Similar to our correlation analysis above, there was not a substantial difference in means across industries. In no case was the difference in means for any risk factor between two industries above the standard deviation for all firms. As mentioned above, this may be because there is relatively little variability across the large publicly traded firms in our study. However, we still wanted to look for innovative ways to explore potential differences across industries. We computed in average citation number of risk factors cited by each industry for all industries that had more than 20 firms in our data, and we ranked the industries from 1 (highest citation) to 17 (lowest citation) for IS risk factors. The two industries with the highest citation of IS risks are NAICS 2-digit code 33 (durable goods manufacturing, citing 11.1 risks per firm compared with the overall average of 9.5 risks per firm) and 62 (health care, citing 10.5 risks per firm), which is interesting because these two industries both involve large fixed assets and high-value products.
Two of the three industries with the lowest citation of risk are NAICS 2-digit code 45 (retail such as general merchandise, 8.3 risks per firm) and 72 (accommodation and food services, 8.5 risks per firm), which is interesting because these two industries cater directly to customers in saturated markets with strong price competition. It is possible that in their quest to maintain low costs, these industries are willing to take on more risk, and it is also possible that these industries invest heavily to mitigate and minimize IS risks because these industries cater directly to end consumers where social media and public reputation can have a large impact.
6.3 Factor analysis
We performed an exploratory factor analysis to identify the underlying relationships among the 25 IS risks in our framework, using a varimax rotation to make the factors easier to interpret (Kaiser, 1958). We removed nine risks that load less than 0.50 onto a factor and/or cross-load across factors (meaning that the risk was not tied to one specific factor), and we achieved five factors with an eigenvalue greater than 1.0. An eigenvector indicates a vector that does not change direction when a linear transformation is applied and is a generally accepted criterion to indicate relevant factors (Kaiser, 1960). Together these five factors explain 0.55 of variance in the data. The factors are shown in Table 5 and described below.
| Description | Risk | Factor 1 | Factor 2 | Factor 3 | Factor 4 | Factor 5 |
|---|---|---|---|---|---|---|
| Factors of production | 2C1. Intellectual property | 0.68108 | 0.15043 | 0.27414 | −0.00586 | 0.07514 |
| 4B2. Open-source software | 0.67493 | 0.01246 | 0.14539 | −0.10692 | 0.03094 | |
| 4A2. IT industry dynamics | 0.65904 | 0.22462 | 0.16580 | 0.19962 | 0.17607 | |
| 3A1. IT human capital | 0.65151 | 0.06860 | −0.17233 | 0.14431 | −0.04190 | |
| 4A1. New IT-based competitors | 0.64170 | 0.01911 | 0.13991 | 0.23622 | 0.20670 | |
| 4B1. Software license/hardware purchase | 0.58878 | 0.22819 | 0.08385 | −0.08035 | 0.25014 | |
| Risk of failure | 2A2. Internet/telecom/power outage | 0.09122 | 0.77700 | 0.04620 | 0.14697 | 0.03945 |
| 1B1. Natural disasters/terrorism | 0.03263 | 0.69512 | 0.23750 | 0.10427 | −0.07739 | |
| 2A1. Software/hardware failure | 0.07816 | 0.65858 | −0.08177 | −0.01141 | 0.13991 | |
| 1A4. User error, negligence or malfeasance | 0.25313 | 0.51806 | 0.09715 | −0.03379 | 0.10876 | |
| Use of data | 4B4. Data providers | 0.11178 | 0.09947 | 0.76249 | 0.01328 | 0.35216 |
| 2A4. Algorithms/models | 0.27532 | 0.14003 | 0.72753 | 0.11548 | −0.17772 | |
| Customers | 4C1. Electronic commerce/omni-channel | 0.10249 | 0.13740 | −0.06567 | 0.76636 | 0.00477 |
| 2A3. Payments | 0.03627 | 0.00707 | 0.15236 | 0.72550 | 0.06485 | |
| Disruptive trends | 3A2. Offshoring/geographic dispersion | 0.07997 | 0.18400 | −0.07496 | 0.07988 | 0.70389 |
| 1C1. Emerging technologies | 0.24450 | −0.02482 | 0.18696 | 0.00289 | 0.68019 | |
| Eigenvalue | 4.03431 | 1.53373 | 1.16522 | 1.07130 | 1.01706 | |
| Percent of variance explained | 25.21% | 9.59% | 7.28% | 6.70% | 6.36% |
- Notes: (1) Principal components analysis with varimax rotation. Eigenvalues and percent of variance explained based on unrotated factors. (2) As indicated above, 16 of the 25 risks in our framework loaded above the 0.5 level onto one of 5 factors with an eigenvalue greater than 1.0. (3) Nine risks in our framework did not load above the 0.5 level on to one of five factors with an eigenvalue greater than 1.0. These risks either cross-loaded on factors with an eigenvalue greater than 1.0, and/or loaded onto factors with an eigenvalue less than 1.0. These risks are 1A1. Cyberattack/cybersecurity breach, 1C2. United States/foreign data protection laws, 2B1. ERP implementation/upgrade, 2B2. Integrate acquisitions, 2C2. Insufficient insurance, 2C3. Inability to detect risk events, 4B3. IT/BPO providers, 4B5. Dominant platform providers, 4C2. Changing consumer use of technology.
- Abbreviation: IT, information technology.
The first factor can be described as “factors of production” or the inputs used to produce goods and services, which include capital, labor, and management. In this factor, intellectual property, open-source software and software license/hardware purchase represent IT capital, IT human capital represents labor, and IT industry dynamics and new IT-based competitors represent the backdrop within which firms produce goods and services.
The second factor can be described as “risk of failure,” which includes the external risks of natural disaster/terrorism and internet/telecommunications/power outage and the internal risks of hardware/software failure. As we mentioned above, the risk of user error/negligence/malfeasance includes internal users and external users, which in this case are both consistent with the risk of failure. The third factor can be described as “use of data” to manage the firm, which includes IS risks associated with risks of data providers that are a source of data, application of the data in algorithms and models, and external regulations that may influence the use of data. The fourth factor can be described as “customers,” including the channels to reach customers and electronic payments from customers. The fifth factor can be described as “disruptive trends,” including geographic dispersion due to offshoring and emerging technologies such as artificial intelligence.
6.4 Word count
We collected the number of words per firm and number of words per risk from the IS content we filtered from Item 1A. On average, each Fortune 1000 firm used 1361 words (standard deviation 1464) to describe IS risks with an average of 196 words per risk (standard deviation 303). The four industries with the largest number of words for IS risks are NAICS 2-digit codes 51 (information, average 3788 words on IS risks), 45 (retail, average 2493), 72 (accommodation and food services, average 1889), and 52 (finance and insurance, average 1832). It is not surprising that information industry firms have the longest description of IS risks, because these firms provide IS-based products and services. The next three industries are consumer-facing industries that may feel more responsibility to describe their risks in detail, perhaps due to consumer protection laws or reputation effects.
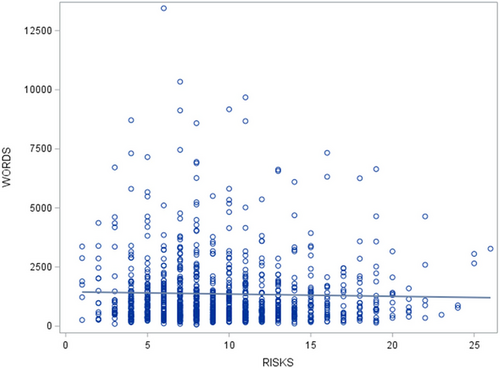
Interestingly, although the top four industries show a relationship of words and words per risk, the correlation between words and risk in our data is not statistically significant (−0.02946, p < 0.3607). Figure 3 provides a scatterplot and regression line to demonstrate the lack of relationship between words and risks in our data. This lack of relationship would lend credence to previous research on the wording of privacy policies. For example, from 2001 to 2003, the readability of privacy policies declined, while the length increased, and nearly half of US individuals do not have education needed to understand about half of privacy policies (Milne et al., 2006). Privacy policies tend to be written in a way that conceals privacy infringements (Pollach, 2007). Firms do not want to reveal whether they adhere to their privacy policies, and instead want to limit the scope of privacy policies to reduce their liabilities (Schwaig et al., 2005). Privacy policies do not provide information users want to know (Earp et al., 2005). Although users are most concerned about the transfer and sharing of information, what information was collected and how it was used, and how organizations store and maintain personal information, privacy policies most frequency contain descriptions of security related to data collection and transfer, how data were collected, and consent about data collection.
7 DISCUSSION
Most existing frameworks on IS risks were developed 20–30 years ago. This article developed an updated framework to account for significant technology, business, and societal developments over the past two decades. Our framework consists of 25 IS risks in 10 categories that fit into four quadrants. We applied this framework to all 965 Fortune 1000 firms that filed an SEC Form 10-K for the 2020 fiscal year. We find that virtually all Fortune 1000 firms cite the risk of a cyberattack, with failure as the other risk that is cited by over 85% of Fortune 1000 firms. United States/foreign privacy laws are the only other IS risk in our framework to be acknowledged by more than two-thirds of Fortune 1000 firms. Beyond these four risks that are the most widely acknowledged, four risks in our framework are cited by 36%–65% of Fortune 1000 firms, six risks are cited by 16%–35% of Fortune 1000 firms, and 10 risks are cited by 15% or fewer of Fortune 1000 firms.
We found relatively little difference in the citation of IS risks across industries and across financial measures, which suggests that large firms may mimic each other in the manner they cite IS risks. Because the intent of SEC Forms 10-K is to report to the investor community, firms may not seek to stand out adversely as they compete with other firms to attract investment in stock and bonds. We perform an exploratory factor analysis which suggests an alternate way to categorize IS risks into factors we describe as factors of production, risk of failure, use of data, customers, and disruptive trends.
Our analysis produces several managerial insights. First, we find that some risk topic areas such as cyberattacks are widely discussed across industries, and other risk topic areas such as IT human capital are not as widely discussed. This brings up the question of why some risk topic areas are more widely discussed than others. Firms may choose not to report on some risk topic areas versus others or may be more exposed to some risk topic areas versus others. However, stark differences in the prevalence of some risk topic areas may signal cases in which firms are more likely to report on popular risk topics emerging in the filings of other companies. There may also be cases of firms reporting on status quo risk issues, possibly viewing this type of reporting as a proxy for standardized risk programs and reporting, or firms using this reporting specifically for areas that involve the highest degree of liabilities. More standardized requirements for SEC filings may further shed light on how firms view those specific risk topic areas.
Second, it is important to note the practice of firms mentioning concerns with insufficient insurance and the inability to detect risk events. Although disclosing this potential issue promotes transparency and may impact liabilities, a focus on those risk topic areas presents an opportunity to further comment on aspects of resilience and continuity of operations, which is not currently required for SEC filings. Third, the findings suggest that there are other important aspects of IS-related risk that were not discussed in the SEC filings. For example, we found minimal discussion about key risk topics such as governance, cyber-physical risk, and maturity of risk programs. There was also minimal discussion of how firms are addressing risk topic areas, or the relative priority of risk topic areas.
Although the SEC filings present a standardized snapshot of risk issues across firms, our results suggest that there is an opportunity to further refine the expectations for those filings. The results show that some risk topic areas are more widely reported compared with others but do not provide a sufficient basis to understand why some firms report some risk topic areas more widely. From a risk perspective, this is problematic. Beyond financial reporting, many stakeholders rely on a firm's ability to understand and manage risk, covering key aspects of safety and security. If there are signals of insufficient consideration, understanding, and/or management of risk, that information could be critical for various stakeholders such as customers, suppliers, shareholders, and community members.
7.1 Limitations and future research
This article involved some limitations that could be addressed by future research. One limitation is that our data based on SEC Forms 10-K considers a view of risk at a single point in time (fiscal year 2020), and future research could address this limitation by tracking risk development and changes for a group of firms over multiple years. A second limitation is that we use a binary indicator for a firm's citation of each risk, when a binary variable may not fully indicate the extent or severity with which the firm views a risk. As we discuss above, the number of words may not be a satisfactory indicator of risk volume or severity. Future research could address this limitation through more sophisticated coding mechanisms, such as sentiment analysis of keywords associated with each risk. Although manual coding has the advantage of depth and context and the two coders in this study have very high inter-rater reliability, the use of manual coding leaves open the possibility that both coders may have missed the same areas that could be relevant for this research. In a related point as mentioned earlier, for this article, we had only one author clean and filter IS risk content from the Item 1A text. Future research could address this potential limitation by using automated coding schema to clean and filter data and identify and categorize risks acknowledged by Fortune 1000 firms. Although the qualitative methods used in this article do not consider tone, sentiment, wording, or sequencing of terms within data, these considerations would be relevant for future research.
Although the text of Forms 10-K Item 1A contains only discussion of risk areas that were deemed to be material by firms, other text-based artifacts such as transcripts of quarterly earnings calls or annual meetings for publicly traded firms also have limitations such as a lack of prescribed format. There are few practical resources that can cover all relevant risk topic areas across various types of organizations. For example, Item IA does not address risk items related to governance, organizational processes (e.g., evidence of a risk program), refined understanding of third-party risk areas, and financial processes for the risk program. However, because Forms 10-K must adhere to strict regulatory requirements, the aggregated high-level findings across industries in this article are based on consistent data validity. There remains an opportunity to aggregate the data used in this article with other data sources to create a more comprehensive view of publicly traded firms.
There are also other areas for future research to build on this article. For example, this article focuses primarily on risk factors cited by firms, with only limited attention to manifestations of risk such as acknowledgement of an actual cyberattack. Future research can focus on the manifestations of IS risks, including potential empirical analysis to study the relationship of risk citation with risk manifestation. Another idea for future research would be to articulate the actions that firms take to mitigate risk, and study whether there is any relationship between mitigation actions, citation of risk, and actual manifestations of risk. Finally, a very interesting and fruitful idea for future research would be to study the relationship of IS risk with physical risk, given the manner in which firms use IS to manage their facilities and operations.
The approach we used in this article to view and benchmark risk concerns across organizations is generalizable. For example, this approach can be applied to understand consistencies and inconsistencies in communication of what are deemed material risk issues across a range of private sector, public sector, and nongovernmental organizations. The approach could be applied using a variety of data resources, such as corporate filings, press releases, analyst reports, and environmental, social, and governance reports. The approach could also be adapted for other uses such as gauging the integrity of risk programs or creating benchmarking standards for risk programs across organizations.
In the long run, the use of a generalizable approach can support a growing need for organizations to further standardize how to communicate about relevant and high priority risk areas, particularly because application findings suggest that there are many inconsistencies in this type of communication. Automation and/or artificial intelligence can be used to aggregate risk communication materials, be adapted to non-written materials, and/or be conducted repeatedly to further understand widespread risk issues and the changes in those risk issues over time.1 The approach could be used to develop tools to provide a more holistic understanding of risk, risk management, and risk governance across a range of organizations, which is important given the public interest and potential economic and societal value.
ACKNOWLEDGMENTS
The authors express gratitude to the Area Editor and two anonymous reviewers for their contributions to strengthen the manuscript.
REFERENCES
- 1 We thank an anonymous reviewer for helping us to identify potential future research opportunities in this area.




