Using camouflaging mobility to protect privacy in mobile ad hoc networks†
Part of this paper was presented in the IEEE WoWMoM 08, Workshop on Security, Privacy, and Authentication in Wireless Networks, Newport Beach, CA, 23–27 June 2008.
Abstract
The open nature of wireless medium has left wireless communications vulnerable to various privacy attacks. Much research work has been proposed to protect the identity anonymity of communicating parties, the anonymity of network routes and the location privacy of the message source and destination. However, with the advent of new radio identification and localization techniques, more advanced privacy attacks are possible. We describe a new privacy attack in which the adversary tries to infer the itineraries of the nodes in the network. To protect itinerary privacy, we design an algorithm, called 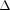 -camouflaging mobility algorithm, which changes the original motion segments of a node into
-camouflaging mobility algorithm, which changes the original motion segments of a node into 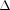 -shaped camouflaging paths. Itinerary privacy, correspondent privacy, and route privacy are closely related so we propose a comprehensive anonymous routing scheme, called MARS, to protect these privacy goals. MARS exploits camouflaging mobility to protect itinerary privacy and uses motion pseudonyms generated from the camouflaging mobility to protect correspondent privacy and route privacy without using cryptography. Our analysis results show that
-shaped camouflaging paths. Itinerary privacy, correspondent privacy, and route privacy are closely related so we propose a comprehensive anonymous routing scheme, called MARS, to protect these privacy goals. MARS exploits camouflaging mobility to protect itinerary privacy and uses motion pseudonyms generated from the camouflaging mobility to protect correspondent privacy and route privacy without using cryptography. Our analysis results show that 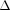 -camouflaging mobility algorithm is cost-effective, which can significantly reduce the itinerary exposure probability at a small cost of extra travel distance. Moreover, our network simulation results illustrated that MARS anonymous routing scheme and
-camouflaging mobility algorithm is cost-effective, which can significantly reduce the itinerary exposure probability at a small cost of extra travel distance. Moreover, our network simulation results illustrated that MARS anonymous routing scheme and 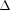 -camouflaging mobility algorithm did not reduce network layer performance. Copyright © 2009 John Wiley & Sons, Ltd.
-camouflaging mobility algorithm did not reduce network layer performance. Copyright © 2009 John Wiley & Sons, Ltd.




