Reliability and validity of the Chinese version of the Information Security Attitude Questionnaire for nurses
No Patient or Public Contribution.
Abstract
Aim
Nurses play a crucial role within medical institutions, maintaining direct interaction with patient data. Despite this, there is a scarcity of tools for evaluating nurses' perspectives on patient information security. This study aimed to translate the Information Security Attitude Questionnaire into Chinese and validate its reliability and validity among clinical nurses.
Design
A cross-sectional design.
Methods
A total of 728 clinical nurses from three hospitals in China participated in this study. The Information Security Attitude Questionnaire (ISA-Q) was translated into Chinese utilizing the Brislin two-way translation method. The reliability was assessed through internal consistency coefficient and test–retest reliability. The validity was determined through the Delphi expert consultation method and factor analysis.
Results
The Chinese version of ISA-Q consists of 30 items. Cronbach's α coefficient of the questionnaire was 0.930, and Cronbach's α coefficient of the six dimensions ranged from 0.781 to 0.938. The split-half reliability and test–retest reliability were 0.797 and 0.848, respectively. The content validity index (S-CVI) was 0.962. Exploratory factor analysis revealed a 6-factor structure supported by eigenvalues, total variance interpretation, and scree plots, accounting for a cumulative variance contribution rate of 69.436%. Confirmatory factor analysis further validated the 6-factor structure, demonstrating an appropriate model fit.
Conclusion
The robust reliability and validity exhibited by the Chinese version of ISA-Q establish it as a dependable tool for evaluating the information security attitudes of clinical nurses.
Implications for Nursing Practice
The Chinese iteration of the ISA-Q questionnaire offers a profound insight into the information security attitudes held by clinical nurses. This understanding serves as a foundation for nursing managers to develop targeted intervention strategies aimed at fortifying nurses' information security attitudes, thereby enhancing patient safety.
1 INTRODUCTION
Patient safety has emerged as a critical global priority. It encompasses the concept that patients should be safeguarded from harm resulting from medical interventions, distinct from harm stemming from the natural progression of their illnesses (Bani Issa et al., 2020). Within this framework, patient information security stands as a crucial component of ensuring patient safety. As information technology and management methodologies advance, big data assume an increasingly statistically significant role in the medical domain. While propelling the progress of healthcare, it concurrently introduces risks and challenges, foremost among them being patient information security concerns (Price 2nd & Cohen, 2019).
Information security encompasses processes and methodologies aimed at safeguarding confidential, personal, and sensitive data from unauthorized access, misuse, alteration, or destruction (Institute, 2021). Attitude is an important predictor of behaviour and an important variable to support (Kang & Seomun, 2021; Rajeh, 2022). Clinical nurses, as integral members of medical institutions, regularly handle patient information in their daily duties and bear the responsibility of ensuring its security (Kang et al., 2022). If nurses' commitment to safeguarding patient information weakens or if they fail to grasp their obligation in this regard, it can lead to breaches of patient information. Research indicates that in the United States alone, 12.55% of patients' medical records were compromised in 2019, with the average cost of such breaches soaring to $6.45 million, and this rate of data breaches is escalating annually (Coble, 2020). Patient information breaches not only disrupt the management and advancement of hospital information resources but also result in substantial financial losses and cause damage to patients' health information (Kang et al., 2022). Therefore, it is imperative for nurses to recognize the critical importance of information security in managing patient information. Hospitals must intensify nurse training programs and enhance their attitudes toward safeguarding patient information security.
However, the majority of existing studies focus on the impact of nurses' information management skills on patient information security, with limited exploration into the current status of nurses' attitudes toward information security and the factors influencing them. Additionally, China has yet to develop a tool for assessing the information security attitudes of clinical nurses (Hartigan et al., 2018; Kleib et al., 2021). At present, there are questionnaires available from overseas sources used to evaluate nurses' attitudes toward information security (Bulgurcu et al., 2010; Parsons et al., 2017; Velki et al., 2014). However, these questionnaires predominantly focus on assessing administrative and physical aspects, lacking in-depth technical content and comprehensive evaluation dimensions. Korean scholar GyeongAe Seomun et al. recently developed and validated the Information Security Attitude Questionnaire (ISA-Q) specifically tailored for nurses (Kang & Seomun, 2023), which was validated among the clinical nurses. The questionnaire offers a comprehensive evaluation of nurses' attitudes toward information security across three dimensions: physical, technical, and administrative. This addresses the limitations found in existing assessment scales. However, the questionnaire has not undergone validation in other languages. Therefore, this study sought to translate the ISA-Q into Chinese and assess its reliability and validity among Chinese nurses. The objective was to furnish a measurement tool for appraising nurses' attitudes toward information security.
2 METHODS
2.1 Design and participants
This multicentre cross-sectional study was conducted in three hospitals in China from April 2023 to May 2023. A total of 728 nurses were enrolled from the Second Affiliated Hospital of Nanchang University in Jiangxi Province, the First Affiliated Hospital of Zhejiang University in Zhejiang Province, and the First Affiliated Hospital of Sun Yat-sen University in Guangdong Province by utilizing a convenience sampling method. According to the sample size requirements of quantitative research, each project should have at least 10 participants (Wolf et al., 2013). To ensure the credibility and reliability of the research findings, it was determined that at least 20 nurses should participate in each item of the questionnaire. Given that the questionnaire comprised 30 items, the initial target sample size was set at 600 nurses. However, to account for potential non-response or invalid questionnaire data, a larger sample size was deemed necessary, resulting in the recruitment of 728 nurses for this study (Zhang et al., 2022). The inclusion criteria for nurses involved registered nurses with at least 1 year of experience in hospital nursing who volunteered to take part in the study. Exclusion criteria encompassed nursing trainees and nurses lacking labour contracts.
2.2 Instruments
2.2.1 General information questionnaire
The questionnaire consisted of seven questions, including age, gender, marital status, education level, position, department, and total clinical work experience.
2.2.2 Information Security Attitude Questionnaire (ISA-Q)
The ISA-Q was developed by GyeongAe Seomun et al. (Kang & Seomun, 2023) in 2023 and consists of a total of 30 items that explore three dimensions of security. The first dimension, administrative, encompasses three sub-dimensions: work systematicity, promotion of professional responsibility, and engagement in continuous education. The second dimension, physical, includes two sub-dimensions: maintenance of facility stability and environmental control. The third dimension, technical, involves a sub-dimension related to restricting access to information. Each item of the questionnaire was evaluated using a 4-point Likert scale, and each item's score ranged from 1 to 4 points (1 = never, 2 = almost never, 3 = occasionally, 4 = almost every time). Overall questionnaire scores varied from 30 to 120, with higher scores indicating more positive information security attitudes. Cronbach's α value of the questionnaire was 0.94, and Cronbach's α value of the six dimensions ranged from 0.64 to 0.89.
2.3 Procedures
2.3.1 Translation and cultural adaptation
After obtaining permission from Professor Seomun via email, we proceeded to translate the questionnaire into Chinese following the Brislin two-way translation method (Khalaila, 2013). Initially, the ISA-Q was translated into Chinese by two Chinese professors majoring in English. Subsequently, two Chinese professors proficient in English, as native speakers, conducted the back translation. Finally, the translated questionnaire underwent assessment and refinement by two nursing experts and two psychology experts. To ensure clarity and comprehensibility, the translated questionnaire was piloted on a sample of 10 nurses through a pre-survey to evaluate whether the language of the questionnaire was concise and easy to understand.
2.3.2 Data collection procedure
After appropriate training, the researchers visited each of the three hospitals to collect the questionnaires. An online questionnaire had been pre-designed. With the assistance of the nursing department director at each hospital, the hospital nurses were convened, and the researchers provided a detailed explanation of the study's purpose and significance. Nurses who volunteered to participate were asked to sign an informed consent form, after which the questionnaires were distributed online and collected on-site. Each questionnaire was submitted anonymously. A total of 750 questionnaires were distributed, and after excluding invalid submissions, 728 valid questionnaires were obtained, resulting in an effective recovery rate of 97.07%.
2.3.3 Data analysis
In this study, SPSS 25.0 and AMOS 24.0 software were used for statistical analysis. The count data have been presented as frequencies and percentages. Statistical significance was considered when p < 0.05.
2.3.4 Items analysis
The total score of each questionnaire was calculated and ranked from low to high, and the top 27% (low group) and the bottom 27% (high group) with the top 27% (low group) and bottom 27% (high group) selected. Two independent samples t-tests were conducted to assess whether the questionnaire exhibited appropriate discrimination. It is generally believed that when the critical ratio of each item is ≥3 and p < 0.05, it indicates that the item has appropriate discrimination (Raykov & Marcoulides, 2016). The Pearson correlation test was employed to examine the correlation between each item score and the total score to assess item homogeneity. It is generally believed that when the correlation coefficient between the score of each item and the total score of the questionnaire is ≥0.4, the item demonstrates appropriate homogeneity (Raykov & Marcoulides, 2016). Additionally, Cronbach's α coefficient analysis was conducted after deleting each item. If the deletion of an item leads to an increase in Cronbach's α coefficient of the questionnaire, it suggests that the item should be considered for removal.
2.3.5 Reliability analysis
Reliability refers to the consistency and stability of questionnaire test results (Holgate, 2000). In this study, Cronbach's α coefficient was used to evaluate the internal consistency of the questionnaire. Additionally, the items were divided into two sets based on odd and even order, and the correlation between the results of both sets was calculated to evaluate the split-half reliability of the translated questionnaire. Test–retest reliability was employed to evaluate the temporal stability of the questionnaire, with twenty nurses pre-selected for numbering, and test–retest reliability was assessed 2 weeks later (Lu et al., 2022). Generally, it is considered acceptable when the values of Cronbach's α coefficient, split-half reliability, and test–retest reliability are all ≥0.70 (Frost et al., 2007; Marques et al., 2021).
2.3.6 Validity analysis
The validity analysis of the questionnaire comprises content validity analysis and construct validity analysis. Content validity was assessed using the Delphi method, where seven nursing experts evaluated the questionnaire. Responses were collected using a 4-point Likert scale, with ratings ranging from 4 (highly relevant) to 1 (irrelevant). Item-level content validity (I-CVI) and scale-level content validity (S-CVI) were calculated based on expert ratings. I-CVI was determined as the number of experts rating the item as 3 or higher divided by the total number of experts, with values ideally exceeding 0.78 (Wolf & McNeish, 2023). S-CVI is calculated as the average of I-CVI of 30 items, and S-CVI ≥ 0.90 indicates that the content validity of the translated questionnaire is appropriate (Wolf & McNeish, 2023).
Exploratory factor analysis (EFA) and confirmatory factor analysis (CFA) were used to evaluate the construct validity of the translated questionnaire. A total of 728 nurses were randomly split into two groups of 364 for EFA and CFA, respectively. EFA was used to discover the underlying factor structure of the questionnaire, and CFA was used to validate the corresponding factor structure. In EFA, the Kaiser-Meyer-Olkin (KMO) and Bartlett's sphericity tests were computed to evaluate the factor structure's reliability. A KMO value exceeding 0.60 and a statistically significant Bartlett's test (p < 0.05) indicate suitability for factor analysis (Tobias & Carlson, 1969). Amos 24.0 software was utilized for model fitting in CFA. A good fit is indicated by Tucker-Lewis index (TLI), comparative fit index (CFI), and incremental fit index (IFI) values all exceeding 0.9 (Gao et al., 2023; Wolf & McNeish, 2023). In addition, CMIN/DF should not exceed 3.0 and RMSEA should be below 0.08.
2.3.7 Research Ethics Committee approval
All participating nurses volunteered for inclusion in this study and provided signed informed consent forms. Anonymity was strictly maintained throughout the completion of all questionnaires. Furthermore, this study received approval from the Ethics Committee of the institution (REDACTED).
3 RESULTS
3.1 General information on the sample
This study recruited a total of 728 nurses, comprising 78 males (10.7%) and 650 females (89.3%). Among them, 51.1% fell within the age range of 25–34 years, 77.6% were married, and 60.7% held a bachelor's degree. Additionally, 38.6% of the nurses were currently serving as primary nurses, with 54.5% originating from the ward. Moreover, 51.4% of the nurses reported having a cumulative clinical work experience spanning between 5 and 15 years. The remaining sociodemographic information is shown in Table 1.
| Factors | Group | n | % |
|---|---|---|---|
| Age | 18–24 | 75 | 10.3 |
| 25–34 | 372 | 51.1 | |
| 35–44 | 215 | 29.5 | |
| ≥45 | 66 | 9.1 | |
| Sex | Male | 78 | 10.7 |
| Female | 650 | 89.3 | |
| Marital status | Unmarried | 150 | 20.6 |
| Married | 565 | 77.6 | |
| Divorced/Widowed | 13 | 1.8 | |
| Education level | Technical secondary school | 42 | 5.8 |
| Junior college education | 241 | 33.1 | |
| Undergraduate education | 442 | 60.7 | |
| Postgraduate education | 3 | 0.4 | |
| Position | Nurse | 109 | 14.9 |
| Primary nurse | 281 | 38.6 | |
| Nurse-in-charge | 277 | 38.1 | |
| Associate chief nurse and above | 61 | 8.4 | |
| Department | Ward | 397 | 54.5 |
| Outpatient | 63 | 8.7 | |
| Special | 268 | 36.8 | |
| Total clinical work experience (year) | <5 | 144 | 19.8 |
| 5–15 | 374 | 51.4 | |
| >15 | 210 | 28.8 |
3.2 Item analysis
The item analysis revealed a statistically significant difference (p < 0.001) between the high and low groups across all items, with critical ratio values ranging from 5.676 to 13.773, indicating strong differentiation among items. The correlation coefficient between each item of the translation questionnaire and the total score ranged from 0.492 to 0.710 (p < 0.001), indicating a moderate correlation between each item and the questionnaire. Successive deletion of Items 1–30 and comparison of scale reliability with the total scale after each deletion showed that Cronbach's α coefficient ranged from 0.926 and 0.930, when single items were deleted, failing to surpass the reliability of the total questionnaire. Therefore, it was concluded that retaining all 30 items in the translated questionnaire was appropriate (Table 2).
| Item | Critical ratio | Correlation coefficient between item and total score | Cronbach's alpha if item deleted |
|---|---|---|---|
| Work Systematicity-1 | 7.661 | 0.569 | 0.928 |
| Work Systematicity-2 | 5.676 | 0.555 | 0.928 |
| Work Systematicity-3 | 7.011 | 0.605 | 0.927 |
| Work Systematicity-4 | 7.375 | 0.639 | 0.927 |
| Work Systematicity-5 | 6.171 | 0.710 | 0.927 |
| Work Systematicity-6 | 5.793 | 0.710 | 0.927 |
| Work Systematicity-7 | 7.418 | 0.686 | 0.927 |
| Work Systematicity-8 | 7.898 | 0.628 | 0.927 |
| Work Systematicity-9 | 7.699 | 0.649 | 0.927 |
| Promoting professional responsibility-1 | 10.901 | 0.563 | 0.928 |
| Promoting professional responsibility-2 | 12.062 | 0.560 | 0.928 |
| Promoting professional responsibility-3 | 13.022 | 0.546 | 0.930 |
| Promoting professional responsibility-4 | 11.436 | 0.566 | 0.928 |
| Promoting professional responsibility-5 | 11.526 | 0.572 | 0.928 |
| Continuous education participation-1 | 11.050 | 0.633 | 0.927 |
| Continuous education participation-2 | 12.039 | 0.560 | 0.928 |
| Continuous education participation-3 | 10.726 | 0.640 | 0.927 |
| Continuous education participation-4 | 10.408 | 0.646 | 0.927 |
| Continuous education participation-5 | 10.959 | 0.630 | 0.927 |
| Maintaining facility stability-1 | 10.413 | 0.633 | 0.927 |
| Maintaining facility stability-2 | 11.315 | 0.607 | 0.927 |
| Maintaining facility stability-3 | 8.500 | 0.613 | 0.927 |
| Maintaining facility stability-4 | 8.439 | 0.622 | 0.927 |
| Restricting access to information-1 | 11.414 | 0.600 | 0.927 |
| Restricting access to information-2 | 10.977 | 0.566 | 0.928 |
| Restricting access to information-3 | 10.299 | 0.562 | 0.928 |
| Restricting access to information-4 | 13.773 | 0.492 | 0.929 |
| Environmental control-1 | 9.804 | 0.670 | 0.926 |
| Environmental control-2 | 10.654 | 0.495 | 0.929 |
| Environmental control-3 | 9.717 | 0.617 | 0.927 |
3.3 Reliability analysis
Cronbach's α value of the Chinese version of the Information Security Attitude Questionnaire was 0.930. Cronbach's α value of the six dimensions of the questionnaire ranged from 0.781 to 0.938. The split-half reliability of the translated questionnaire was found to be 0.797. Two weeks later, a retest was conducted with 20 nurses, yielding a test–retest reliability coefficient of 0.848 (Table 3).
| The scale and its dimension | Cronbach's alpha | Split-half reliability | Test–retest reliability |
|---|---|---|---|
| The ISA-Q | 0.930 | 0.797 | 0.848 |
| Work systematicity | 0.938 | ||
| Promoting professional responsibility | 0.861 | ||
| Continuous education participation | 0.895 | ||
| Maintaining facility stability | 0.876 | ||
| Restricting access to information | 0.837 | ||
| Environmental control | 0.781 |
3.4 Validity analysis
3.4.1 Content validity analysis
I-CVI and S-CVI were calculated according to the scores of seven different experts. The results showed that the range of I-CVI was 0.857–1.000, and the value of S-CVI was 0.962 (Table 4).
| Item | Expert1 | Expert2 | Expert3 | Expert4 | Expert5 | Expert6 | Expert7 | I-CVI | S-CVI |
|---|---|---|---|---|---|---|---|---|---|
| 1 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 1.000 | 0.962 |
| 2 | 4 | 4 | 4 | 4 | 3 | 3 | 3 | 1.000 | |
| 3 | 3 | 3 | 3 | 3 | 3 | 3 | 2 | 0.857 | |
| 4 | 3 | 3 | 3 | 3 | 3 | 4 | 4 | 1.000 | |
| 5 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 1.000 | |
| 6 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 1.000 | |
| 7 | 4 | 4 | 4 | 3 | 4 | 4 | 4 | 1.000 | |
| 8 | 4 | 4 | 3 | 3 | 3 | 2 | 3 | 0.857 | |
| 9 | 3 | 3 | 3 | 3 | 3 | 3 | 3 | 1.000 | |
| 10 | 3 | 3 | 3 | 3 | 4 | 4 | 4 | 1.000 | |
| 11 | 4 | 4 | 4 | 4 | 4 | 3 | 3 | 1.000 | |
| 12 | 4 | 4 | 4 | 4 | 4 | 3 | 3 | 1.000 | |
| 13 | 2 | 3 | 3 | 3 | 3 | 3 | 4 | 0.857 | |
| 14 | 3 | 3 | 3 | 3 | 4 | 4 | 4 | 1.000 | |
| 15 | 3 | 3 | 3 | 4 | 3 | 4 | 3 | 1.000 | |
| 16 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 1.000 | |
| 17 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 1.000 | |
| 18 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 1.000 | |
| 19 | 3 | 2 | 3 | 3 | 3 | 3 | 3 | 0.857 | |
| 20 | 4 | 4 | 3 | 2 | 3 | 3 | 4 | 0.857 | |
| 21 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 1.000 | |
| 22 | 3 | 4 | 4 | 4 | 2 | 4 | 4 | 0.857 | |
| 23 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 1.000 | |
| 24 | 3 | 3 | 3 | 3 | 4 | 2 | 4 | 0.857 | |
| 25 | 4 | 4 | 4 | 4 | 4 | 3 | 3 | 1.000 | |
| 26 | 3 | 3 | 3 | 3 | 3 | 3 | 2 | 0.857 | |
| 27 | 3 | 3 | 4 | 4 | 4 | 4 | 4 | 1.000 | |
| 28 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 1.000 | |
| 29 | 4 | 4 | 4 | 4 | 3 | 4 | 4 | 1.000 | |
| 30 | 4 | 3 | 4 | 3 | 4 | 4 | 4 | 1.000 |
3.4.2 Exploratory factor analysis
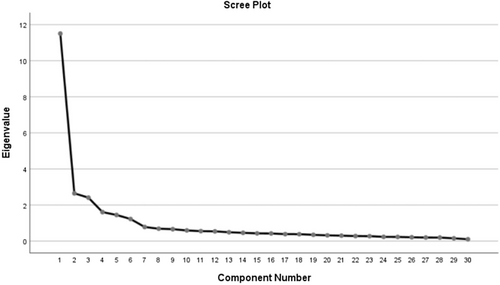
The EFA results revealed that KMO = 0.922 and Bartlett's spherical test was statistically significant (χ2 = 7255,929; p < 0.001), thus indicating that factor analysis was appropriate. Six factors with eigenvalues >1 were extracted by principal component analysis, which explained 69.436% of the total variance. The scree plot (Figure 1), provides additional support for the existence of the 6-factor model, as the downward trend of the curve diminishes after the sixth point. Moreover, each item exhibited a factor loading greater than 0.4, and there was no occurrence of double-factor loading (Table 5).
| Item | Factor 1 | Factor 2 | Factor 3 | Factor 4 | Factor 5 | Factor 6 |
|---|---|---|---|---|---|---|
| Work Systematicity-1 | 0.756 | — | — | — | — | — |
| Work Systematicity-2 | 0.713 | — | — | — | — | — |
| Work Systematicity-3 | 0.765 | — | — | — | — | — |
| Work Systematicity-4 | 0.837 | — | — | — | — | — |
| Work Systematicity-5 | 0.817 | — | — | — | — | — |
| Work Systematicity-6 | 0.697 | — | — | — | — | — |
| Work Systematicity-7 | 0.716 | — | — | — | — | — |
| Work Systematicity-8 | 0.778 | — | — | — | — | — |
| Work Systematicity-9 | 0.819 | — | — | — | — | — |
| Promoting professional responsibility-1 | — | — | 0.694 | — | — | — |
| Promoting professional responsibility-2 | — | — | 0.676 | — | — | — |
| Promoting professional responsibility-3 | — | — | 0.820 | — | — | — |
| Promoting professional responsibility-4 | — | — | 0.725 | — | — | — |
| Promoting professional responsibility-5 | — | — | 0.761 | — | — | — |
| Continuous education participation-1 | — | 0.750 | — | — | — | — |
| Continuous education participation-2 | — | 0.773 | — | — | — | — |
| Continuous education participation-3 | — | 0.769 | — | — | — | — |
| Continuous education participation-4 | — | 0.687 | — | — | — | — |
| Continuous education participation-5 | — | 0.759 | — | — | — | — |
| Maintaining facility stability-1 | — | — | — | 0.690 | — | — |
| Maintaining facility stability-2 | — | — | — | 0.774 | — | — |
| Maintaining facility stability-3 | — | — | — | 0.762 | — | — |
| Maintaining facility stability-4 | — | — | — | 0.789 | — | — |
| Restricting access to information-1 | — | — | — | — | 0.721 | — |
| Restricting access to information-2 | — | — | — | — | 0.751 | — |
| Restricting access to information-3 | — | — | — | — | 0.783 | — |
| Restricting access to information-4 | — | — | — | — | 0.738 | — |
| Environmental control-1 | — | — | — | — | — | 0.694 |
| Environmental control-2 | — | — | — | — | — | 0.772 |
| Environmental control-3 | — | — | — | — | — | 0.739 |
3.4.3 Confirmatory factor analysis
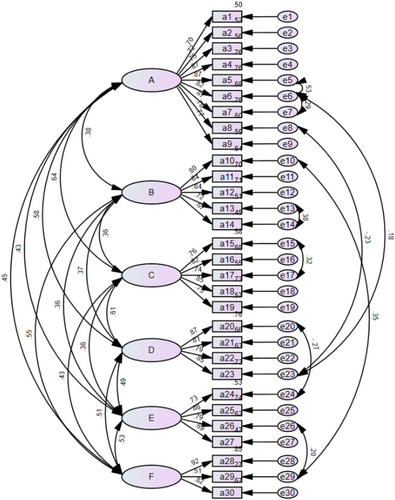
CFA validated the 6-factor model, with results displayed in Figure 2. Based on the correction index, nine corrections were made to the initial model, namely e5 and e6, e6 and e7, e6 and e23, e8 and e23, e10 and e29, e13 and e14, e15 and e17, e20 and e24, e26 and e29. The final model fitting results were CMIN/DF = 2.030, RMSEA = 0.053, TLI = 0.941, CFI = 0.949, and IFI = 0.949. These results suggested that the translated questionnaire exhibited an appropriate level of fit to the data.
4 DISCUSSION
We conducted our translation work using the Brislin two-way translation method (Khalaila, 2013). The translated questionnaire was culturally adjusted to align more closely with Chinese cultural norms. Seven different nursing experts were invited to translate and adapt the original questionnaire in accordance with Chinese guidelines and common expressions, resulting in the final Chinese version of ISA-Q. This Chinese version demonstrates strong equivalence with the original scale while better reflecting Chinese language expression and logical thinking patterns, thereby reducing ambiguity and enhancing comprehension. A total of three items were adjusted: Item 3 was revised from “I am aware of natural disasters and emergency measures/procedures” to “I am aware of natural disasters and can take emergency measures according to the process.” Item 21 was modified from “I make sure the screen saver is active when I leave” to “When I leave the computer that stores patient information, I make sure the screen saver is active.” Furthermore, item 27 in the original questionnaire was altered from “I change my password for business use regularly” to “I regularly change my system password to prevent disclosure of patient information,” reflecting the influence of Chinese culture. Ten nurses participated in a pre-survey, indicating that the translated questionnaire was concise and easy to comprehend, with completion taking approximately 4–5 min. Additionally, the critical ratio of items exceeded the standard value, suggesting strong discrimination between questionnaire items and effective evaluation of information security attitudes among different nurses (Raykov & Marcoulides, 2016). The correlation between the item scores and the total score of the questionnaire was found to be moderate. Interestingly, even when individual items were deleted, Cronbach's α coefficient did not exceed the reliability of the total questionnaire, so all 30 items could be retained.
Reliability analysis can aid to evaluate whether the translated questionnaire accurately represents its intended structure (Koo & Li, 2016). In this study, Cronbach's α coefficient, split-half reliability, and test–retest reliability were employed to measure the reliability of the translated questionnaire. Cronbach's α coefficient of the translated questionnaire was 0.930, which was slightly lower than that of the original questionnaire (Kang & Seomun, 2023). However, the split-half reliability and test–retest reliability were 0.797 and 0.848, respectively, indicating strong temporal stability of the translated questionnaire. Consequently, the Chinese version of ISA-Q demonstrates good reliability. Validity refers to the exact correspondence between the measurement tool and the real world (Yang et al., 2021). Content and construct validity were utilized to evaluate the validity of the translated questionnaire. The content validity of the translated questionnaire was evaluated by seven different experts using Delphi expert consultation method. The S-CVI of the translated questionnaire was 0.962, higher than the standard value, thereby indicating that the content validity of the translated questionnaire was good (Wolf & McNeish, 2023). EFA and CFA were used to evaluate the construct validity of the translated questionnaire. EFA revealed extraction of 6 factors with eigenvalues greater than 1, explaining 69.436% of the total variance, exceeding the standard value by 40% (Yang et al., 2022). Additionally, satisfactory results were obtained for factor loadings. The results of CFA indicated a good fit index for the equation model of the translated questionnaire, with correlations between all latent variables ranging from 0.36 to 0.64, below the standard value of 0.7. Thus, the Chinese version of ISA-Q demonstrates robust validity.
4.1 Limitations
Several limitations are evident in this study. Firstly, the research was limited to a cross-sectional study conducted solely in three hospitals across three provinces in China. It remains uncertain whether the Chinese version of ISA-Q is applicable to hospitals in other regions of the country, necessitating further verification. Secondly, the questionnaire utilized in this study relied on self-reporting, introducing the possibility of reporting bias. Lastly, the study did not delve into the factors influencing the information security attitudes of clinical nurses, which will be addressed in future research endeavours.
5 CONCLUSIONS
The Chinese version of ISA-Q comprises 30 items that are characterized by their conciseness, clarity, and ease of understanding. The findings of this study demonstrated that the Chinese version of ISA-Q exhibited commendable reliability and validity, rendering it a dependable tool for evaluating the information security attitude of clinical nurses. Moreover, the questionnaire results offer valuable insights for nursing managers and educators, aiding in the formulation of intervention measures aimed at enhancing information security practices among nurses.
AUTHOR CONTRIBUTIONS
Study design: WX, CZ. Data collection: XL, YS, JL. Data analysis: XY. Study supervision: YD, CZ. Manuscript writing: WX. Critical revisions for important intellectual content: JL, YS. All authors contributed to the article and approved the submitted version.
ACKNOWLEDGEMENTS
Thank you to all clinical nurses who volunteered to participate in this study and also to the Director of Nursing for their great support in data collection. In addition, we would like to thank Professor Seomun for providing the English version of ISA-Q for this study. At the same time, we are grateful for the hard work of the editors and the valuable suggestions of the reviewers.
FUNDING INFORMATION
This research received no specific grant from any funding agency in the public, commercial, or not-for-profit sectors.
CONFLICT OF INTEREST STATEMENT
The authors claim that there is no conflict of interest in this study.
ETHICS STATEMENT
The study involving human subjects was reviewed and approved by the Second Affiliated Hospital of Nanchang University. All nurses participating in this study were informed of the purpose and significance of this study and signed an informed consent form.
Open Research
DATA AVAILABILITY STATEMENT
All data related to this study are available from the corresponding author upon reasonable request.




