TabNet-SFO: An Intrusion Detection Model for Smart Water Management in Smart Cities
Abstract
As Smart City (SC) infrastructures evolve rapidly, securing critical systems like smart water management (SWM) becomes paramount to protecting against cyber threats. Enhancing the security, sustainability and execution of conventional schemes is considered significant in developing smart environments. Intrusion detection systems (IDS) can be effectively leveraged to realise this security objective in an Internet of Things (IoT)-based smart environment. This research addresses this need by proposing a novel IDS model called TabNet architecture optimised using Sailfish Optimisation (SFO). The TabNet-SFO model was specifically developed for SWM in SC applications. The proposed IDS model includes data collection, preprocessing, feature selection and classification processes. For training the model, this research used the CIC-DDoS-2019 dataset, and for evaluation, real-time data collected using an IoT-based smart water metre are used. The preprocessing step eliminates unnecessary features, cleans the data, encodes labels and normalises the applied datasets. After preprocessing, the TabNet model selects significant features in the dataset. The TabNet architecture was optimised using the SFO algorithm, which allows hyperparameter tuning and model optimisation. The proposed model demonstrated improved detection accuracy and efficiency on both the simulated and real-time datasets. The model attained a 98.90% accuracy, a 98.85% recall, a 98.80% precision, a 98.82% specificity and a 98.78% f1 score on the CIC-DDoS dataset and a 99.21% accuracy, a 99.02% recall, a 99.05% precision, a 99.10% specificity and a 99.18% f1 score on real-time data. Compared to existing models, the TabNet-SFO model outperformed all existing models in terms of performance metrics and validated its efficiency in detecting attacks.
1. Introduction
Smart cities use the latest technological advances, including cloud computing, big data, IoT and artificial intelligence (AI), to optimise the management of public services [1]. IoT enables the identification and communication of distinct factors related to several city sectors, including healthcare, agriculture, water resource management, transportation, waste disposal and energy. Implementing an SC model enables cities to enhance their administrative and operational procedures, primarily creating sustainable environments for their people [2].
Several cyberattacks can occur in an SC. Water supply: Attackers can alter the concentrations of chemical compounds in water, adversely affecting public health. Power grid collapse: Attackers can cause a power outage within a city. Attackers can manipulate city traffic signal lights, leading to accidents. Wireless networks make traffic signals vulnerable to attack. Smart vehicle attacks involve including fake routes or emulating other cars in the vicinity to create accidents. Attackers hack surveillance cameras to spy on individuals and obtain unauthorised access to their data [3].
The IoT refers to a network of connected devices that enable the continuous transmission of information between physical objects. These devices encompass a range of applications, including SC infrastructures, healthcare and medical devices, industrial robots, automatic cars and smart wearable devices. These devices can be monitored and controlled from a distance [4]. It is estimated that Internet of Things devices will surpass mobile devices in terms of prevalence and possess the capability to access highly sensible information (personal information). This will result in an expansion of attacks, thereby increasing the possibility of attacks. Given that security is crucial for most IoT applications, designing IoT-IDSs is imperative to safeguard the communication facilitated by these IoT technologies [5].
As shown in Figure 1, SC development depends on tactical, strategic and operational factors. These characteristics establish SC management. At the strategic level, it analyses SC pillars: environmental, economic and social. City administrators can develop comprehensive policies to mitigate the damage by measuring the security threats on each pillar.
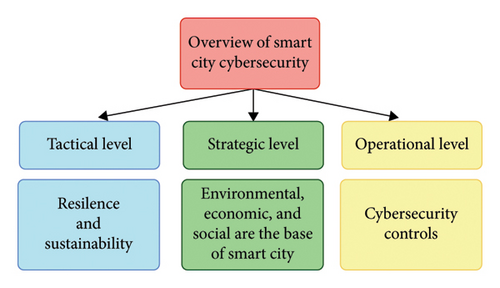
At the tactical level, factors like SC resilience and sustainability are considered. Sustainability means that the city can manage resources for the present and future generations. The city’s resilience is its ability to adapt to adversity. Security-wise, the model measures the SC’s cybersecurity maturity to detect and respond to cyberattacks that could damage resilience and sustainability. Operatically, the maturity model considers vulnerabilities, security policies, the logging effectiveness of the incident response, infrastructure and device access [6]. The IoT is considered a crucial element for the efficient operation of an SC. IoT applications are designed to guarantee the regular functioning of key city services, including water and energy supply, fire alarms and the efficient operation of specialised processing, in addition to other production capacities, to ensure the important connections of SCs [7]. In the SC infrastructure, a denial-of-service (DoS) attack is a highly dangerous form of cyberattack in which attackers deliberately overwhelm the target system by loading it with traffic, keeping it not accessible to legal users. These attacks are typically carried out by flooding the target system with excessive network traffic before the target system becomes unresponsive [8]. The distributed DoS (DDoS) attack, which is a type of DoS attack, is more harmful than DoS attacks [9]. Defending against it becomes increasingly challenging because of the use of several infected devices to overload the target with malicious traffic. These attacks result in significant losses by preventing legal user access by depleting the targeted server. Based on data from Kaspersky Lab, the worldwide economic consequences of DDoS attacks exceed $120,000 for medium- and small-sized enterprises and average over $2 million for corporations per attack. Therefore, effective detection techniques must be employed to secure online services against malicious users [10].
1.1. Smart Water Management in Saudi Arabia
SWM uses IoT sensors to track and enhance water consumption in communal areas and buildings, minimising inefficiency and preserving resources. Institutions, companies and households can use smart water systems to manage and control water consumption. Smart water systems have several advantages that help conserve water, reduce cost and improve water management [11]. SWM enhances the understanding of water systems, including identifying defects, conservation and water administration. Water supply and sanitation in Saudi Arabia are characterised by challenges and successes. The water scarcity is a significant concern in this area. Substantial investments have been made in water desalination, water distribution, sewerage and wastewater treatment to mitigate water scarcity. Currently, desalination constitutes approximately 50% of the nation’s drinkable water supply, groundwater extraction contributes 40% and surface water resources in the southwestern mountain region contribute 10% [12]. Freshwater resources in Saudi Arabia are severely constrained, and the capacity of water desalination facilities needs to be increased to meet the substantial demand. Furthermore, in Saudi Arabia, every household relies on its underground reservoirs to store water until the National Water Company distributes water throughout the local area [13]. One of the primary objectives of this research is to mitigate water scarcity by implementing a comprehensive monitoring system for each tank in an urban area. This system utilises a sensor feedback to effectively direct water flow to specific locations in need.
This research focuses on developing and validating an efficient IDS model called TabNet-SFO, which was specifically designed for SWM within SC applications in Saudi Arabia. Leveraging advanced deep learning (DL) techniques, particularly the TabNet architecture, optimised using the SFO. The primary focus is achieving superior performance in detecting and mitigating cyber threats. This is demonstrated by comprehensively evaluating both the simulated and real-time datasets. Finally, this research aims to contribute to the advancement of intrusion detection technology for SC environments, thereby facilitating the sustainable management of critical water resources in SC.
1.2. Problem Statement and Contributions
- •
Development of TabNet-SFO: The TabNet-SFO intrusion detection framework is explicitly designed for SWM in SC applications. The proposed framework leverages a TabNet architecture optimised using the SFO.
- •
Enhanced threat detection in dynamic environments: The adaptability and effectiveness of the TabNet-SFO model in dynamic environments are highlighted. This is achieved by presenting its performance on real-time data collected by smart water metres, ensuring timely detection and mitigation of cyber threats.
- •
Improved accuracy and reliability: The findings of the proposed model are demonstrably improved in relation to detection accuracy and reliability compared to existing models. This is achieved by leveraging DL techniques and optimisation algorithms. The improvements are validated through a comprehensive evaluation of the simulated and real-time datasets.
- •
Sustainable urban water management: This model contributes to the advancement of sustainable urban water management practices. This is achieved by enhancing the security and resilience of water infrastructure. Ultimately, this will support the goals of SC initiatives toward more efficient and resilient urban environments.
The remaining parts of this work are structured as the following section presents an analysis of the literature review. The third section presents the implementation of the proposed research model TabNet-SFO. This includes the presentation of the dataset, the data preprocessing techniques employed and the TabNet-SFO-based classification approach. The fourth section analyses the performance of the research model. This analysis will be conducted by comparing it with several existing IDS models. Finally, the conclusion of the research will be presented along with suggestions for further research directions.
2. Related Works
An overview of existing research into intrusion detection in the context of SC applications is provided in this literature review. By analysing recent studies, methodologies and findings, this review aims to identify research gaps, challenges and emerging trends in the field and develops a basis for the proposed research on securing SWM in SC environments. Detecting anomalous occurrences automatically in a real-world environment is highly difficult due to their complexity and nature. A previous study [14] introduced a highly effective and resilient framework for identifying abnormalities in video data through the use of AI of things (AIoT). This research proposes a hybrid model that combines a 2D convolutional neural network (CNN) and an echo state network (ESN) for SC surveillance. The CNN was used as a feature extractor from the input, which was then fed into an autocoder to refine the features. The model was designed to be efficient and was implemented on edge devices to ensure that it could be used effectively in AIoT contexts in SC. DL models are applicable for detecting abnormalities discovered in SC applications. A previous study [15] presented a model for detecting anomalies in SC infrastructures using a combination of IoT and DL. The model was used to detect irregularities in the SC environment. In addition, the model used the deep consensus network (DCN) model to identify abnormalities in the data accurately. The arithmetic optimisation algorithm (AOA) was employed to fine-tune the hyperparameters of the DCN model. The Iterative Dichotomiser-3 (ID3) classifier was also used to categorise the discovered items into distinct classes. The results demonstrate the superiority of the model across several measures. DoS and DDoS attacks deplete the resources of the IoT network, resulting in system failure. The TabNet-IDS model was introduced in [16] as an IDS framework that utilises attentive processes to autonomously identify significant characteristics from a dataset for training the IDS model and generating interpretable outcomes. The proposed technique employs automated feature engineering and selection to identify potential risks in an IoT environment. The results indicate that the TabNet architecture effectively analysed tabular information for IoT security and yielded better outcomes.
The authors [17] introduced a Billiards-based optimiser with DL-driven anomaly detection and classification (BBODLADC) for IoT-based sustainable SCs. The model was applied to identify and accurately categorise abnormalities in IoT-enabled SC. The model used binary pigeon optimisation (BPEO) to select features efficiently. In addition, the model employed the Elman recurrent neural network (ERNN) method to identify and categorise abnormalities. The BBO system can be used to optimise the parameters selected by the ERNN algorithm. The simulation exhibited superior results. A DL framework that used a dense random neural network (DRNN) technique was implemented in [18] to accurately differentiate and categorise abnormal actions from regular actions, specifically, identifying different attacks against IoTs. Machine learning (ML) algorithms have a limited capacity to examine performance, especially when compared to DL models. The analysis of the DRNN structures yielded improved computational efficiency and desirable outcomes for categorical attacks. The model’s findings indicated better performance, with significant enhancements observed in most categorical attacks. A previous study [19] introduced an Ebola Optimisation Algorithm (EOA) that used DL for scene categorisation and an IDS approach for IoT-enabled remote sensing images. The model utilised a customised DarkNet-53 to extract features, perform hyperparameter tuning using EOA and perform classification using a graph convolutional network (GCN). The IDS method comprises two operations: variational autocoder (VAE)-based IDS and parameter tuning using skill optimisation. The results of the model demonstrate enhanced performance. Smart systems connected over open networks are at risk of security breaches, including hacker attacks and vulnerability attacks. A solution was developed in [20] to address this problem, which involved using a highly effective IDS model called Tab-AttSRU. The proposed model employs basic recurrent networks to detect anomalous patterns in network traffic effectively. Model-based feature significance and TabNet’s learnable mask for soft selections were applied to achieve accurate interpretation. The decision-making characteristics were selected to ensure essential interpretability using the sequential attention mechanism. The model’s effectiveness and interpretability were demonstrated using experimental data. A previous study [21] presented an improved version of the bacterial foraging optimisation (IBFO) algorithm combined with DL to detect anomalies in an IoT network. The model used the Z-score normalisation strategy for data normalisation. The model utilised IBFO to select the optimum features during the feature selection (FS) phase. The model employs a multiplicative long-short-term memory (MLSTM) model to perform intrusion detection and categorisation. In addition, a Bayesian optimisation method was used to identify the optimal hyperparameters for the MLSTM model. The results demonstrate that the model exhibits enhanced performance with maximum accuracy. An IDS is an effective approach to achieve security in a smart environment. In [22], the authors presented the use of the chaotic poor and rich optimiser (CPRO) along with a DL method for intrusion detection in ubiquitous and smart environments. The Z-score normalisation technique was used to standardise the input. This study employed an FS strategy based on the CPRO algorithm to select subsets of features. The butterfly optimiser with deep sparse AE was employed for intrusion detection. The simulation study revealed that the findings demonstrated superior performance. A previous study [23] focused on the utilisation and assessment of IDS in terms of SCs enabled by the IoT.
Models for anomaly identification, such as RNNs, isolation forests and VAEs, have proven to be highly successful in accurately recognising abnormalities in SC data. These models have demonstrated their capacity to identify atypical electricity usage trends, electrical grid manipulations and cyber risks. This confirms their importance in supervising critical systems in SCs. A previous study [24] presented a model that used IoT to identify cyberattacks in SC applications. The model incorporates ML techniques for this purpose. The ensemble ML model, which incorporates bagging, boosting and stacking ensemble techniques, outperformed the Deep Neural Network Expert System approach. It also offered enhanced reliability and security to power networks (such as Smart Buildings, Smart Grid and Smart Traffic) to defend against cyberattacks through ML. Nature-inspired algorithms have been adopted to address the issues faced by SCs using optimisation and performance-oriented methodologies. Hence, a previous study [25] addressed three specific aspects of SCs: smart living, smart mobility and security provision. This was achieved by creating three solutions inspired by nature. The three solutions were moth flame electric management for smart living, dragon clustering mobility on the Internet of vehicles (IoV) and an ant colony-based IDS for security.
The proposed solutions exhibited superior performance in terms of conventional performance metrics. A previous study [26] used multiple ML classifiers and a DL model for intrusion detection. The initial data balance in the model was achieved by employing the synthetic minority oversampling technique (SMOTE), which mitigates overfitting. To identify normal and abnormal traffic in IoT, random forests, voting classifiers (comprising Gaussian Naive Bayes and logistic regressions ensemble), artificial neural networks and a CNN were used. The model underwent training and testing on seven datasets, achieving an accuracy rate of 99.7% using the voting classifier. The study [27] examined the use of unsupervised IDS for multidimensional time series data in IoT systems. The authors proposed a Gaussian mixture (GM)-VAE scheme based on Gaussian recurrent units (GRUs). GRU cells were used in the study to identify relationships between time series data. In addition, priors of GM were employed in latent spaces to describe multimodal data. Table 1 summarises the comparative analysis of reviewed works.
| Ref | Approach used | Application scenario | Advantages | Disadvantages |
|---|---|---|---|---|
| [14] | Hybrid CNN + ESN | Smart city surveillance | Efficient feature extraction and edge device implementation | Complexity of model training |
| [15] | DCN + AOA + ID3 | SC infrastructure | Superior accuracy and hyperparameter optimisation | Computational overhead |
| [16] | TabNet-IDS | IoT security | Automated feature engineering and interpretable results | Limited to tabular data |
| [17] | BBO + ERNN | IoT-enabled SCs | Efficient feature selection and accurate classification | Parameter optimisation complexity |
| [18] | DRNN | IoT attacks | Improved computational efficiency and improved performance | Model complexity |
| [19] | EOA + DL | IoT-enabled remote sensing | Custom feature extraction and enhanced classification | Computational resources |
| [20] | Tab-AttSRU | Network anomaly detection | Effective interpretability and sequential attention mechanism | Interpretability is dependent on the architecture |
| [21] | IBFO + MLSTM | IoT network | Optimal feature selection and improved performance | Hyperparameter tuning complexity |
| [22] | CPRO + DL | Smart environments | Feature subset selection and effective intrusion detection | Algorithmic complexity |
| [23] | RNNs, isolation forests, VAEs | SCs in the IoT | Versatile anomaly detection and accurate recognition | Model training complexity |
| [24] | Ensemble ML | SC cyber-attacks | Improved reliability and ensemble techniques | Performance variability |
| [25] | Nature-inspired algorithms | SC security | Performance-oriented solutions inspired by nature | Solution-specific applicability |
| [26] | Multiple ML + DL | IoT intrusion detection | High accuracy and model diversity | Data balance requirement |
| [27] | GM-VAE + GRUs | Multidimensional time series | Multimodal data handling and unsupervised learning | Model selection complexity |
During the training phase, a model selection mechanism using the Bayesian Inference Criterion was applied to identify the model that could accurately predict the distribution in the GM latent space. The experimental results on the IoT datasets demonstrate significant improvement.
2.1. Research Gap Analysis
The reviewed existing works show that research into intrusion detection for SC applications has primarily focused on employing various ML and DL techniques. However, despite the diversity of techniques, several research gaps have emerged. First, although many studies have proposed advanced models for IDS, there is a lack of consensus on the most effective techniques for integrating these models into practical SC applications. In addition, most studies have focused on detecting anomalies within the digital domain, such as network traffic or sensor data, neglecting potential physical threats like DoS and DDoS attacks, on SC infrastructure. Furthermore, there is a notable gap in research addressing the scalability and real-time processing requirements of IDSs for large-scale SC deployments. Lastly, there is limited exploration of interdisciplinary approaches, integrating domain-specific water management knowledge with advanced data analytics techniques. Addressing these gaps is crucial for developing a robust and comprehensive IDS model specifically for SWM in an SC environment.
3. Intrusion Detection Model for Smart Water Management in Smart Cities
This section outlines the research methodology used to develop and evaluate the TabNet-SFO intrusion detection framework for SWM in SC applications. A detailed overview of the key components include data collection, preprocessing, model architecture, optimisation techniques and hyperparameter tuning and optimisation. The process of designing, implementing and validating the TabNet-SFO model is discussed by delineating the proposed methodology.
- •
Identifying and isolating dysfunctional parts of water management system.
- •
Deactivate valves and/or functions to mitigate potential malicious activity.
- •
To transmit alerts to system administrators for analysis [28].
- •
Improved leak detection: Real-time data from smart metres can be leveraged to quickly identify leaks, thereby reducing water waste.
- •
Enhanced security: This system helps protect against cyberattacks that could disrupt water supplies or damage infrastructure.
- •
More efficient water use: By monitoring water use patterns, areas where water conservation efforts can be implemented can be identified.
- •
Better decision-making: Valuable insights that can be used to improve water management decisions can be provided by data from the system [30].
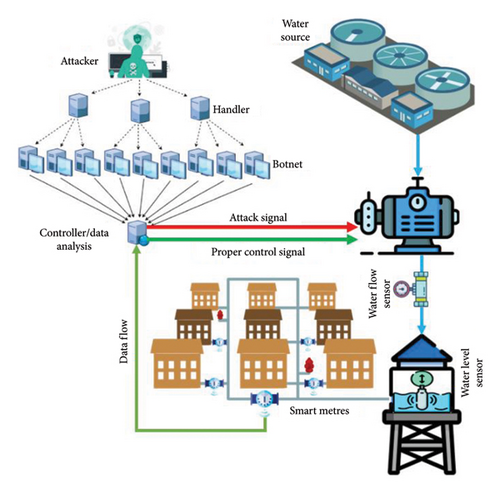
Overall, SWM systems are important for developing sustainable and resilient SCs. Figure 3 shows the workflow of the proposed research model.
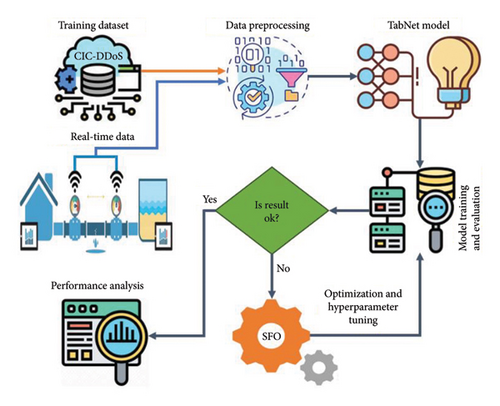
3.1. CIC-DDoS-2019 Dataset
In this study, the CIC-DDoS-2019 dataset was used to train the proposed IDS model. This dataset has been extensively used to detect and classify DDoS attacks. The Canadian Institution for Cybersecurity (CIC) generated this dataset [31]. The dataset comprises benign and up-to-date DDoS attacks that simulate real-world data. The APL has witnessed the implementation of several new attacks using TCP/UDP-based protocols. A novel taxonomy is also presented in Figure 4, which distinguishes between exploitation and reflection-based attacks.
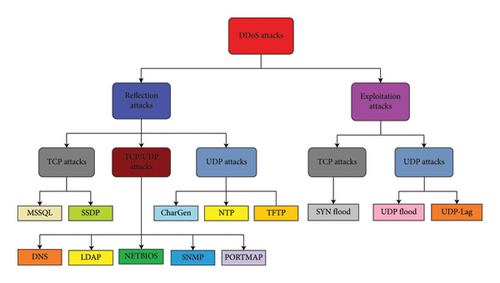
Data were collected on two separate days for training and testing. The training dataset was acquired on January 12, 2019 and included 12 distinct types of DDoS attacks, with each attack type stored in a distinct PCAP file. The features retrieved from the dataset were obtained using the CICFlowMeter tool. Every record in the collection has 88 statistical attributes, such as IP addresses of source and destination, timestamp, port numbers of source and destination, attack protocol and label indicating the type of DDoS attack. The training dataset comprises a comprehensive collection of 12 distinct DDoS attacks: DNS, NTP, NetBIOS, MSSQL, SSDP, SNMP, LDAP, UDP-Lag, UDP, SYN, TFTP and WebDDoS attacks. In contrast, the testing datasets exclusively encompasses seven DDoS attacks: NetBIOS, PortScan, LDAP, UDP, UDP-Lag, MSSQL and SYN. The public can access the dataset on the CIC website in both PCAP files and flow formats. Table 2 shows the distribution of data in the dataset [32].
| Data | Malicious | Benign | Total |
|---|---|---|---|
| Training | 50,006,249 | 56,863 | 50,063,112 |
| Test | 20,307,560 | 56,965 | 20,364,525 |
3.2. Data Preprocessing
This study highlights a binary classification issue for intrusion classification, where all observations are classified as either an attack or normal class. Data preprocessing involves many activities, such as eliminating unnecessary features, data cleaning, label encoding and normalisation. The original dataset contains 88 features. The noncontributing features for detecting DDoS attacks were eliminated. The features in this compilation include unnamed, destination IP, Flow ID, Flow Packets, Destination Port, Source IP, Flow Bytes, Source Port, Timestamp and Similar HTTPs. After removing these 10 attributes, 78 attributes were acquired for this study. Additionally, values that included not a number (NaN) and blanks were eliminated, and values representing infinity were assigned a value of 0. Label encoding utilises one-hot encoding to transform category labels into numerical representations. In addition, binary labels of 1 and 0 were employed to indicate whether the given data indicate a DDoS attack or not [33].
In this context, Xi represents the normalised numeric values within the range of [0-1], while min and max represent the lowest and maximum values derived from all data points, respectively.
3.3. TabNet Architecture
The TabNet model is a singular DL architecture that relies on the sequential multistep processing. This unique DL architecture facilitates FS and enhances the ability to acquire knowledge about features with many dimensions. TabNet outperforms decision trees (DTs) by leveraging its advantages through meticulous design. It achieves this through the following methods: (i) employing sparse instance-wise FS acquired from data; (ii) construct a sequential multistep architecture, where each step influences an aspect of the decisions based on the chosen attributes; (iii) enhance learning capability through nonlinear process of the chosen attributes; and (iv) emulate resembling through higher dimensions and more steps [20].
3.3.1. TabNet Encoder
The encoder architecture shown in Figure 5 comprises an attentive transformer (AT), feature transformer (FT), and feature masking at all decision steps in the TabNet encoder. Tabular data encompass both categorical and quantitative information. In TabNet, raw integer records are used, and a trainable embedding is employed to transform category characteristics into integer features. All decision steps receive the identical B × D attribute matrix, where B represents the batch sizes, and D represents the feature dimension. The encoding of TabNet relies on the execution of several decision processes. The features of all decision steps were established based on the outcomes of the preceding decision steps via AT. The generated feature representation is output and included in the broader decision-making process [35].
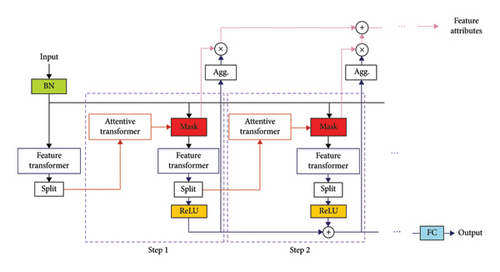
3.3.2. FS
The Mask module of each decision step is responsible for performing FS. The decision step’s AT is responsible for selecting the function to be applied. The AT achieves the FS of the present decision steps by acquiring the mask, as shown in Figure 6. The FS process can be elucidated as follows.
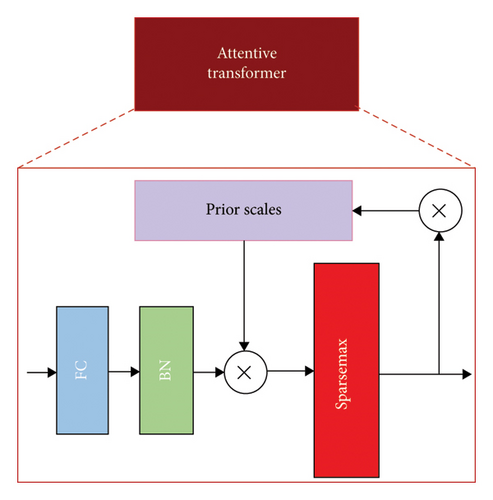
The tensor is output by the FT in the preceding decision step and transmitted to the Split unit. Initially, the Split unit divides the tensor and produces a[i − 1]. The function a[i − 1] traverses the layer hi, which is a combination of fully connected (FC) and batch normalisation (BN) layers. The primary function of layer hi was to facilitate the linear integration of data, thereby enabling the extraction of abstract and higher-dimensional characteristics. In the hi layer, the output is multi-multiplied by the prior scale p[i − 1] from the preceding decision steps. The p[i − 1] denotes the use of characteristics in the preceding decision step. The weight of the present decision steps decreases as the number of characteristics used in the prior decision step increases.
When γ is equal to 1, each feature is limited to a single occurrence in a decision step. This decision phase’s FS involves the multiplication of M[i] and the feature elements. Subsequently, the selected features are sent to the FT of the current decision steps, initiating the subsequent decision step loop.
3.3.3. Processing Features
The FT layer consists of three main components: the FC, BN and gated linear unit (GLU) layers. Figure 7 shows the FT architecture.
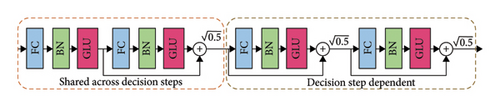
The FT layer comprises two distinct components. The initial portion parameters of the layers were distributed, indicating that they underwent joint training across all iterations. In contrast, the latter portion is not shared and undergoes independent training during each iteration. In each iteration, the input comprises identical features, which allows us to utilise a shared layer for the common feature computation component. Subsequently, distinct layers can be employed to handle the attribute components of all steps. The proposed architecture can enhance the learning capabilities of the model and increase its capacity. The residual connection is employed and multiplied by 0.5 in the layer to ensure the network stability [35].
3.3.4. Decoder Architecture
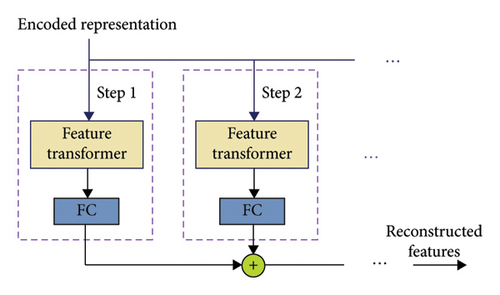
The encoded form shown in Figure 8 represents the summation of the encoder’s vectors, excluding the FC layer. The decoder used the encrypted description as its input. The decoding process employs FT layers to transform the representation vectors into features. The reconstructed features were generated after incorporating many procedures. TabNet was employed in this study, along with pre-training of self-supervised. The self-supervised learning approach masks some aspects of the same sample and then utilises an encoding–decoding model to anticipate the masked features. When trained using this approach, the encoder model can accurately represent the characteristics of a sample, accelerate its convergence and improve its overall performance [36].
3.4. Hyperparameter Tuning and Optimisation of TabNet Using SFO
The proposed SFO algorithm was used to improve the hyperparameter tuning performance of TabNet. The SFO is a metaheuristic approach that operates on a population basis. The SFO emulates the hunting behaviour of sailfish, where they engage in alternating attacks on schooling sardine prey. SFO utilises two distinct groups of predator and prey populations to replicate the group hunting behaviour. Additionally, the approach under consideration employs the strategy of alternating attacks to undermine the shared protection mechanisms of the prey groups. Furthermore, the prey’s movements could be modified throughout the search space, enabling the hunters to capture suitable prey and enhance their fitness compared to previous encounters. The proposed method operates under the assumption that the sailfish represent potential solutions, and the problem variables correspond to the sailfish’s positions inside the search space. Consequently, the population inside the solution space is produced randomly. The sailfish can navigate their location vectors in several spatial dimensions, including one, two, three, or hyper-dimensional spaces [37].
Population initialisation: The populations of sardines and sailfish were initiated using a random process. The random location for each sailfish was denoted as , whereas the random location for each sardine was represented as . In this context, X ∈ {Sailfish}, y ∈ {Sailfish} and q ∈ {Iteration value}. One potential option for the qth iterations is to consider the spatial distribution of sailfishes or sardines .
Elitism evaluation: Based on the fitness function (FF), the determination of the location for all the most recent populations, denoted as Fn, is based on the actions of all quest agents, namely, the sardine or sail. Sardine that has sustained an injury is classified as , inj ∈ {Sardineset}, such as , ∀q, which is considered the most efficient sardine within the sardine population. In addition, in the context of the impedance paradox , ∀q, the sailfish population sustains elite sailfish with reduced fitness, which is referred to as , elit ∈ {Sailfish set}.
Equation (9) represents the quantity of sardines as NMsard and the quantity of sailfish as NMsail. The number of primary sardines exceeded that of sailfish. It is anticipated to be NMsard = 3 × NMsail. The λq fluctuation value is of significant importance in the model because it is crucial to adaptively modify their location by increasing the λq fluctuation value [38].
Here, MS represents the count of misclassified samples, and TS represents the total number of samples. The SFO approach not only aims to optimise the accuracy of TabNet by developing an FF but also establishes a positive integer to indicate the improved efficiency of potential solutions. Here, an FF represents a decrease in the classification error rate. Table 3 shows the hyperparameter details of TabNet and SFO (see Algorithm 1).
| Hyperparameter | Value |
|---|---|
| Learning rate | 0.001 |
| Attention embedding layer width (N_a) | 8 |
| The decision prediction layer width (N_d) | 8 |
| Total number of architectural steps | 3 |
| α | 4 |
| β | 0.001 |
| Max. iteration | 500 |
| Initial population | 30 |
-
Algorithm 1: Sailfish optimisation process.
-
Initialise
-
Populations of sardines (potential solutions) and silkfish (candidate solutions)
-
Parameters (α and β)
-
Fitness(solution): Evaluate the quality of a solution.
-
FOR each Sardine:
-
Calculate fitness
-
For each sailfish species:
-
Update position based on the following:
-
Encircling the best Sardine (using α)
-
Maneuvering strategy (using β)
-
Calculate fitness
-
Identify the best Sailfish (elite) and worst Sardine (injured)
-
Update Sardine positions based on
-
Injured Sardine’s location
-
Random movement
-
Replace injured sardines with fresh ones
-
WHILE termination criteria are not met (e.g., maximum iterations)
-
CONTINUE main loop
-
Best Sailfish position
-
End
4. Experimental Results and Analysis
4.1. Experimental Setup
This section presents a comprehensive experimental analysis of the proposed TabNet-SFO model regarding intrusion detection in SWM in SC applications. The research model TabNet was developed using the Keras API. The Keras library is an open-source software tool that provides a Python-based interface for implementing artificial neural networks. The Keras framework serves as an intermediary for the TensorFlow library. The experiment was conducted on a machine equipped with an 11th Generation Intel Core i7 @ 3.00 and 1.80 GHz processor with 12 GB RAM. The research model was evaluated based on accuracy, recall, specificity, precision and the F1 score. The dataset was split into testing and training sets. The training set was used to train and fine-tune the model’s hyperparameters, and the test set was used to evaluate the performance of the research model.
4.2. Performance Metrics
- •
The measurement of an attack instance is considered TP if it is labelled accurately.
- •
If an incident that is considered normal is classified as an attack, it is quantified as FP.
- •
Normal instances are denoted as TN when labelled as such.
- •
The measurement of an attack occurrence is denoted as FN when the attack is classified as normal [40].
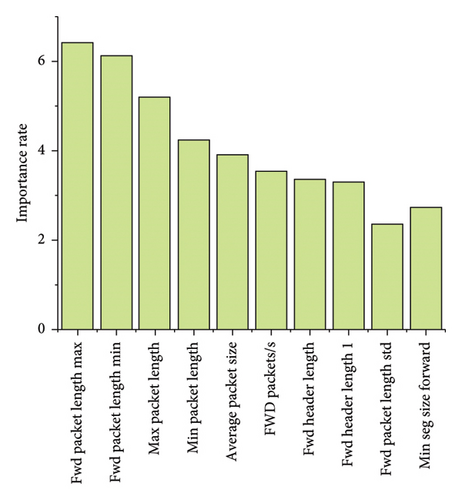
Both the collected real-time and the existing dataset’s data were used to evaluate the performance of the proposed TabNet-SFO model. The dataset was divided into a 70:30 ratio for evaluation, where 70% was used to train the research model and the remaining 30% was used to test the model. The TabNet model selected significant features in the dataset that enhanced the performance of the research model. The CIC-DDoS dataset contains 88 features, where the features selected from the dataset using TabNet comprise 10 features, as shown in Figure 9. The following sections present a performance analysis of the TabNet-SFO model and a comparison with existing models discussed in the literature review.
4.3. Performance Evaluation
This section presents an analysis of the performance results obtained using the proposed TabNet-SFO model based on the CIC dataset and real-time data collected using a smart water metre. The model was evaluated on training and test sets in terms of accuracy, recall, specificity, precision and f1 score. The obtained performances were compared to those of the other models for research validation.
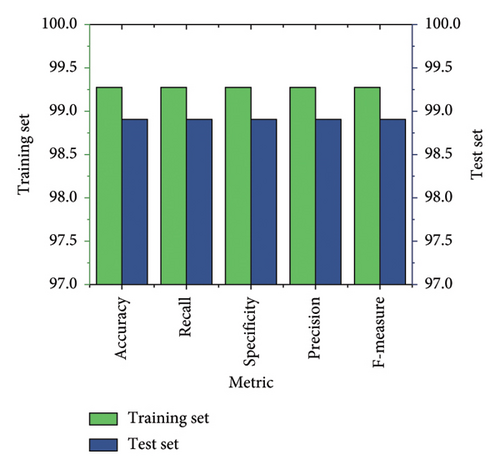
Table 4 presents the results obtained using the CIC-DDoS dataset. The training and test sets were both applied for performance evaluation. The research model obtained an accuracy of 99.28% in training and 98.90% in testing. Both of these performances are nearly close, with a slight difference of 0.38%.
| Metric (%) | Training set | Test set |
|---|---|---|
| Accuracy | 99.28 | 98.90 |
| Recall | 99.10 | 98.85 |
| Specificity | 99.16 | 98.82 |
| Precision | 99.25 | 98.80 |
| F1 score | 99.07 | 98.78 |
The recall or detection rate is a key parameter of the intrusion detection model, where the research model has a recall value of 99.10% in training and 98.85% in testing, which represents a difference of 0.25%. The specificity of the research model was 99.16% in training and 98.82% in testing.
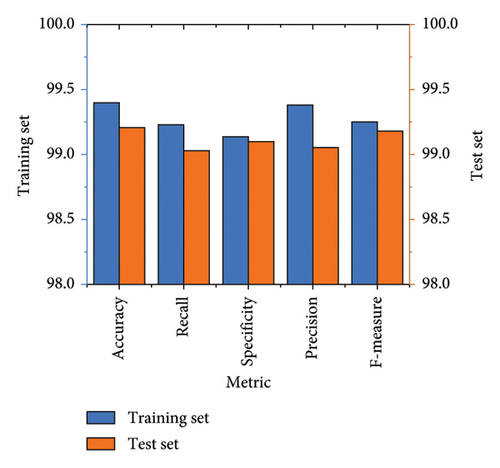
The precision rate of the TabNet-SFO model was 99.25% in training and 98.80% in testing. The research model obtained an F1 score of 99.07% in training and 98.78% in testing. Based on these results, we found that the research model TabNet-SFO is better at detecting attacks while generating the minimum number of false positives. Figure 10 shows a graphical plot of the TabNet-SFO model performance on the CIC-DDoS dataset. Table 5 presents the results of the proposed TabNet-SFO model evaluated on real-time data gathered using a smart water metre implemented for the SWM system. The proposed model used the gathered data to test the TabNet-SFO model, which extracted important features that characterise system activity and help detect intrusions. The comprehensive analysis of real-time data improves the model’s efficiency in promptly detecting and responding to security threats in an SWM system. The research model TabNet-SFO obtained a 99.40% accuracy in training and a 99.21% accuracy in testing, which demonstrates a similar accuracy result. The recall performance of the research model was 99.23% in training and 99.02% in testing.
| Metric (%) | Training set | Test set |
|---|---|---|
| Accuracy | 99.40 | 99.21 |
| Recall | 99.23 | 99.02 |
| F1 score | 99.25 | 99.18 |
| Precision | 99.38 | 99.05 |
| Specificity | 99.14 | 99.10 |
The research model had a specificity rate of 99.14% in training data and 99.10% in test data. The precision rates of the proposed TabNet-SFO model were 99.38% in training and 99.05% in test evaluation. The model obtained an f1 score of 99.25% in training and 99.18% in testing. The performance of the research model obtained greater than 99% for all evaluation parameters; thus, the TabNet-SFO model is effective in attack detection. Figure 11 shows a graphical plot of TabNet-SFO’s findings with real data.
The performance analysis results of the proposed TabNet-SFO and existing models are compared in Table 6. All the current models were either employed to detect DDoS attacks or evaluated using the CIC-DDoS dataset. Compared to the performance obtained from the research model using this dataset, the TabNet-SFO model outperformed all existing models in terms of accuracy by 98.90%. This indicates that the research model has attained 0.3%–2% improved accuracy compared to the current models. The LightGBM model obtained the second-best accuracy score of 98.60%, and the lowest score was 96.91% for MDLIDS-SSE. The detection rate/recall of the research model was 98.85%, which is 0.03%–0.9% higher than that of the compared models.
| Models | Accuracy (%) | Recall (%) | Precision (%) | Specificity (%) | F1 score (%) |
|---|---|---|---|---|---|
| MDLIDS-SSE [22] | 96.91 | 97.91 | 97.24 | 98.26 | 96.25 |
| IDCPRO-DLM [22] | 98.53 | 98.82 | 98.64 | 98.74 | 98.59 |
| DRNN [18] | 98.28 | 98.00 | 97.00 | NA | 98.00 |
| TabNet [16] | 98.51 | 98.40 | 98.50 | NA | 98.44 |
| AE-MLP [41] | 98.34 | 98.48 | 97.91 | NA | 98.18 |
| LightGBM [42] | 98.60 | 98.70 | 98.40 | NA | 98.40 |
| TabNet-SFO (CIC-DDoS) | 98.90 | 98.85 | 98.80 | 98.82 | 98.78 |
| TabNet-SFO (real-time data) | 99.21 | 99.02 | 99.05 | 99.10 | 99.18 |
In this recall comparison, compared to the TabNet-SFO model, the IDCPRO-DLM method demonstrated a very close range of 98.82%. The precision score of the research model was 98.80%, ranging from 0.16% to 1.8%, which is better than the current methodologies. The specificity rate of TabNet-SFO was 98.82%, which was 0.08%–0.56% higher than the other models compared to the two models. Most current models use only four metrics: accuracy, F1 score, recall and precision, for performance analysis. The specificity parameter is not often used in many research works. The f1 score of the TabNet-SFO model was 98.78%, which represents a 0.19%–2.53% improvement over the current model.
By comparing the TabNet-SFO dataset performance with the real-time data performance, the results obtained on real-time data demonstrate better output scores than those obtained on the CIC-DDoS dataset. Figure 12 presents the result comparison analysis of the research model with the current models. Overall, the proposed TabNet-SFO model outperformed all existing models in terms of all performance metrics and validated its efficiency in attack detection.
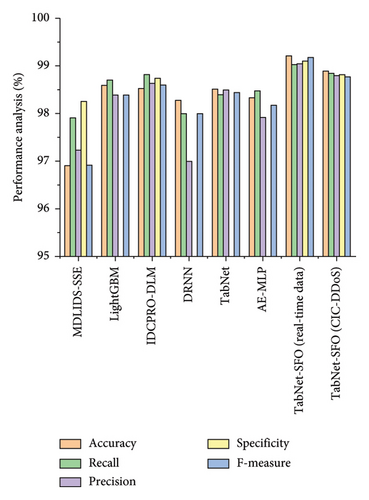
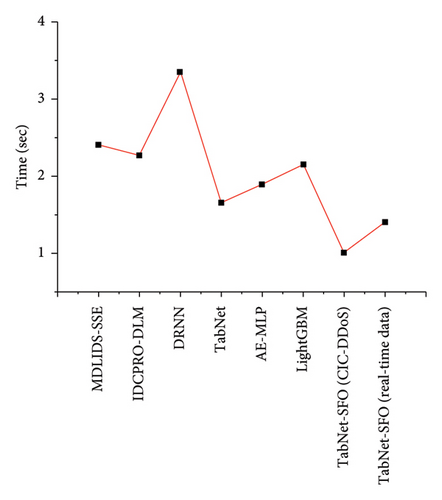
Table 7 presents the time taken to execute the process of detecting attacks by the models. As can be seen, the proposed research model consumed the minimum amount of time to process the data, outperforming all the compared models. Figure 13 shows a graphical plot of the time consumption comparison. The proposed TabNet model is a DL methodology with a compact architecture comparatively related to the other DL models such as CNN, LSTM and DNN. This model typically results in reduced memory consumption in both training and evaluation. Efficient preprocessing and FS processes help the developed model reduce memory usage.
4.4. Pros and Cons of the Proposed Model
The proposed TabNet-SFO model offers several advantages relative to intrusion detection in SWM for SC applications. First, the model’s ability to identify significant features in complex datasets is enhanced by using the TabNet architecture combined with the SFO. This, in turn, improves detection accuracy and reliability. The model’s performance in real-time data collected from smart water metres is demonstrated by its adaptability and effectiveness in dynamic environments. These qualities are crucial for ensuring the security and integrity of SC water infrastructure. By outperforming existing models across multiple performance metrics, the TabNet-SFO model was demonstrated to adapt to IDSs in SC applications. This suggests that it offers robust and efficient solutions for securing critical water resources.
The effectiveness of the TabNet-SFO model depends on several factors, including data availability, quality and the specific characteristics of the SWM system. The computational complexity of training and optimising the model is also recognised as a potential challenge, particularly in resource-constrained environments or large datasets. Further validation across diverse SC contexts is required to ensure the model’s generalisability beyond the analysed scenarios. However, the TabNet-SFO model represents a significant advancement in intrusion detection for SWM, and it offers a promising approach to enhance the security and resilience of SC water infrastructure in the context of an SC environment.
5. Conclusion and Future Work
This research developed TabNet-SFO, which is an IDS model to detect attacks in SWM in SC applications. To train the model, this research used the CIC-DDoS-2019 dataset, and for evaluation, real-time data were collected using an IoT-based smart water metre. The real-time data comprise key metrics, such as flow rates, pressure measurements, valve positions and other pertinent variables. Initially, the model operates by performing data preprocessing using min–max normalisation. After preprocessing, the TabNet model was used to select significant features in the dataset. The TabNet architecture was optimised using the SFO algorithm, which allows hyperparameter tuning and model optimisation. The model attained a 98.90% accuracy, a 98.85% recall, a 98.80% precision, a 98.82% specificity and a 98.78% f1 score on the CIC-DDoS dataset and a 99.21% accuracy, a 99.02% recall, a 99.05% precision, a 99.10% specificity and a 99.18% f1 score on real-time data. Compared to existing models, the TabNet-SFO model outperformed all existing methodologies in terms of performance metrics and validated its efficiency in detecting attacks.
Future exploration could involve integrating the TabNet-SFO framework with IoT devices. This integration can enable real-time intrusion detection and response capabilities directly at the edge of smart water infrastructure. In addition, by using advanced techniques, the scalability of the TabNet-SFO model for large-scale SC deployments can be enhanced. This enhancement ensures efficient detection and mitigation of cyber threats across diverse SC environments.
Conflicts of Interest
The authors declare no conflicts of interest.
Author Contributions
Wahid Rajeh conceptualised the study, led the research design and supervised the entire project.
Majed M. Aborokbah conducted data analysis and algorithm development, contributing significantly to the manuscript writing and review.
Manimurugan S. played a key role in data curation, validation and statistical analysis of the results.
Tawfiq Alashoor contributed to the literature review, prepared initial drafts, data visualisation and was involved in manuscript editing.
Karthikeyan P. provided technical oversight on the implementation of the proposed models and assisted in model validation.
Funding
The authors extend their appreciation to the Deanship of Research and Graduate Studies at University of Tabuk for funding this work through Research no. 0135-1444-S.
Acknowledgments
The manuscript is prepared without the use of AI software.
Open Research
Data Availability Statement
The dataset used in this study can be downloaded at the following link: https://www.unb.ca/cic/datasets/cicev2023.html.




