Symmetric Encryption Algorithms in a Polynomial Residue Number System
Abstract
In this paper, we develop the theoretical provisions of symmetric cryptographic algorithms based on the polynomial residue number system for the first time. The main feature of the proposed approach is that when reconstructing the polynomial based on the method of undetermined coefficients, multiplication is performed not on the found base numbers but on arbitrarily selected polynomials. The latter, together with pairwise coprime residues of the residue class system, serve as the keys of the cryptographic algorithm. Schemes and examples of the implementation of the developed polynomial symmetric encryption algorithm are presented. The analytical expressions of the cryptographic strength estimation are constructed, and their graphical dependence on the number of modules and polynomial powers is presented. Our studies show that the cryptanalysis of the proposed algorithm requires combinatorial complexity, which leads to an NP-complete problem.
1. Introduction
Recently, with the growth of confidential information and the spread of computer systems, the task of ensuring information security has become increasingly important [1–3]. To minimize the risks of unauthorized access, cryptographic methods of information protection are widely used [4, 5], which are divided into symmetric and asymmetric [6, 7]. In practice, symmetric cryptographic transformations are more common for encrypting large amounts of information, as asymmetric ones are quite laborious [8, 9]. The requirements for symmetric methods have become more stringent in terms of ensuring their cryptographic strength due to the rapid development of computing tools and their increased speed. Polynomial algorithms are an alternative to modern numerical cryptoalgorithms [10–12]. In the ring Z[x], as in any other ring of polynomials, basic cryptographic operations are performed: addition, multiplication, and division with remainder [13–15]. The main idea of using polynomials in cryptography is that they can be used as plaintext, keys for encrypting and decrypting messages, building electronic digital signatures, and other cryptographic protocols [16–18].
The use of the residue number system (RNS) [19–21] in the implementation of cryptographic algorithms for information security based on polynomial arithmetic in the Z[x] ring [22, 23], by analogy with the integer RNS [24, 25], leads to parallelization of the computation process [26, 27] and reduction of the amount of data that must be processed during cryptographic operations [28–30]. In turn, it reduces the implementation time and improves the efficiency of the encryption method.
Therefore, our work is aimed at developing the concept of polynomial symmetric cryptographic algorithms based on the RNS and their practical application.
1.1. Our Contribution
- 1.
A theoretical provision for symmetric cryptographic algorithms based on the polynomial RNS was developed.
- 2.
Mathematical frameworks and schemes for the proposed polynomial symmetric encryption within the RNS were devised. To ascertain its resilience, a deep dive was made into constructing analytical expressions, revealing that the process of cryptanalyzing the proposed algorithm required dealing with combinatorial complexity, ultimately leading to an NP-complete problem.
- 3.
It was established that cryptographic strength notably improved with increasing degrees and dimensions of the Galois field p. The peak of cryptographic strength was reached when the number of modules equaled half of the potential count of irreducible polynomials with the given polynomial degrees and Galois field orders.
1.2. Related Work
Most modern symmetric cryptographic algorithms are block-based, and this feature limits the functionality of their implementation. In particular, the key size must be equal to or larger than the block size, leading to the encryption algorithm’s multiple uses for a large message. This procedure reduces the cryptographic strength of the algorithm, increases the time complexity, and, at the same time, complicates the implementation. Many authors have studied symmetric encryption algorithms in the polynomial number system. For example, Lemaire [31] proposes an 8-bit encryption algorithm based on the ideas of well-known symmetric cryptoalgorithms. The authors use divergent polynomials with variable coefficients, bitwise data operations, and two-password identification when generating pseudorandom keys. The hardware implementation of the proposed approach and comparison of the time characteristics with the AES algorithm of the 8-bit architecture based on the Arduino Uno microcontroller (ATmega328) were carried out.
A work [32] is devoted to developing and studying hardware-implemented methods of fast polynomial arithmetic for some homomorphic encryption operations based on the Karatsuba algorithm. In addition, Jayet-Griffon et al. [33] consider the possibilities of speeding up the polynomial multiplication operation for homomorphic encryption when implemented on an FPGA. In [34], a characterization of polynomial multiplication implementations for GPU-based homomorphic encryption is presented.
In [35], a highly efficient image encryption method based on permutation polynomials in finite fields was developed that is resistant to various types of attacks. In addition, the proposed encryption algorithm has no rounding errors, so encryption is lossless.
In the work [36], our effort was dedicated to developing a multifunctional architecture for the polynomial RNS within the context of cryptography. Detailed comparisons with contemporary implementations have indicated the potential utility of polynomial residue arithmetic in modular multiplication. Article [37] presents a schematic diagram of a modular pipeline multiplier, which allows for high-speed data encryption and decryption based on nonpositional polynomial RNS. The authors substantiate the efficiency of the proposed hardware design through a timing diagram. The developed pipeline device can find application in digital computing devices, particularly for high-speed data encryption based on nonpositional polynomial RNS.
In [38], a new method for constructing S-blocks of the AES algorithm is proposed based on replacing the irreducible polynomial and affine mapping. The cryptographic strength of the created S-block is evaluated by several standard tests (bijectivity, nonlinearity, strict avalanche criterion (SAC), and bit-independence criterion). It surpasses the cryptographic strength of the known S-boxes.
An article [39] proposes a method for constructing the S-block of the AES algorithm based on the smallest number of selected irreducible polynomials that meet specific criteria. There are 17 such polynomials, and their use simplifies the hardware implementation of the S-block. The SAC is studied, and it is noted that the polynomial p(x) = x8 + x7 + x6 + x + 1 is the best, with an outstanding value of SAC = 0.5, which indicates the cryptographic strength and reliability of the constructed S-block.
A paper [40] proposes improving the symmetric AES encryption algorithm using dynamic S-blocks whose parameters depend on the key, dynamic irreducible polynomials, and affine constants.
A paper [41] presents the most commonly used symmetric cryptosystem AES in the ring of polynomials today. The main idea is to choose an irreducible polynomial on the basis of which the encryption algorithm is built. The proposed approach was implemented in MATLAB for 30 different irreducible polynomials. As a result of the numerical experiments, it was possible to establish a negligible effect of changing irreducible polynomials on the level of the avalanche.
The authors in [42] proposed a novel method to enhance AES security against fault attacks using the polynomial RNS. The authors parallelize byte-level AES operations over GF(28) by utilizing residues over smaller fields, introducing extended functionalities into AES for side-channel vulnerability analysis.
Polynomial arithmetic has also been used for asymmetric cryptosystems. In particular, in [43], modified arithmetic was developed for the RSA cryptosystem with Gauss integers and polynomials over finite fields. The analysis of the described computational procedures made it possible to determine their advantages over the classical ones. In [44], algorithmic support for the Rabin cryptosystem in the polynomial number system was proposed.
The analysis of the literary sources shows the relevance and importance of polynomial algorithms for protecting information flows. Accordingly, the development of new methods that are resistant to attacks of various types is an important direction in the development of modern cryptosystems. In particular, the combination of polynomial arithmetic and RNS in a ring of polynomials will allow parallelizing the process of performing basic operations in a ring of polynomials, which, in turn, will increase the speed of software implementation and reduce the time complexity of the algorithm, providing the required level of security.
1.3. Organization
Section 2 of this article discusses in detail the theoretical foundations for constructing symmetric cryptographic algorithms based on a polynomial RNS. Subsequently, in Section 3, the cryptographic strength of a polynomial symmetric encryption algorithm in the system of residual classes was evaluated. Finally, in Section 4, the content of this article is summarized.
2. Materials and Methods
In Subsection 2.1, the theoretical foundations for constructing symmetric cryptographic algorithms based on a polynomial RNS are proposed. Subsection 2.2 described the features of developing polynomial symmetric encryption methods in the RNS. An example of symmetric polynomial encryption in RNS presents in Subsection 2.3. In Subsection 2.4, the polynomial symmetric encryption method based on the Chinese remainder theorem (CRT) is proposed.
2.1. Theoretical Foundations of Polynomial RNS
2.2. Development of Polynomial Symmetric Encryption Methods in the RNS
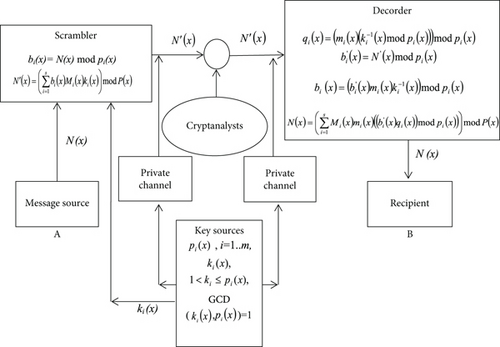
The essence of one of the methods of polynomial symmetric encryption in RNS is that when recovering a polynomial from its residuals in the sum (2), the multiplication is not by the parameters , but by arbitrarily chosen polynomials ki(x), mutually prime with pi(x).
Therefore, to generate keys, both subscribers must choose module systems known only to them pi(x) and the corresponding polynomials ki(x), for which the following conditions are met: 1 < degki(x) < degpi(x) and GCD(ki(x), pi(x)) = 1, where GCD denotes greatest common divisor. If pi(x) is an irreducible polynomial, then the second condition is always met. Accordingly, both the sender and the receiver know the parameters Mi(x) and mi(x).
The found polynomial is a ciphertext that is transmitted over an open communication channel from one subscriber to another.
Figure 1 shows a schematic of the proposed polynomial encryption method based on the RNS.
2.3. An Example of Symmetric Polynomial Encryption in RNS
Let us consider the plaintext PSMFSRD = (15181205181703), which corresponds to the polynomial N(x) = 15x6 + 18x5 + 12x4 + 5x3 + 18x2 + 17x + 3. According to the developed polynomial symmetric cryptosystem for three modules (s = 3), p1(x) = x2 + x + 1, p2(x) = x3 + x + 1, and p3(x) = x2 + 1 and the chosen coefficients k1(x) = x2 + 2x + 3, k2(x) = x3 + x2 + 1, and k3(x) = x2 + 3x + 2, all the parameters are calculated as follows: P(x) = p1(x)p2(x)p3(x) = x7 + x6 + 3x5 + 3x4 + 4x3 + 3x2 + 2x + 1, M1(x) = P(x)/p1(x) = (x7 + x6 + 3x5 + 3x4 + 4x3 + 3x2 + 2x + 1)/(x2 + x + 1) = x5 + 2x3 + x2 + x + 1, M2(x) = P(x)/p2(x) = (x7 + x6 + 3x5 + 3x4 + 4x3 + 3x2 + 2x + 1)/(x3 + x + 1) = x4 + x3 + 2x2 + x + 1, and M3(x) = P(x)/p3(x) = (x7 + x6 + 3x5 + 3x4 + 4x3 + 3x2 + 2x + 1)/(x2 + 1) = x5 + x4 + 2x3 + 2x2 + 2x + 1.
The search for is performed using the method of undetermined coefficients. Firstly, we look for . To do this, we write the equation (x + 2)(Ax + B)mod(x2 + x + 1) = 1, and after transformations, we obtain (Ax2 + (2A + B)x + 2B)mod(x2 + x + 1) = (A + B)x + 2B − A = 1. From the last equation, it follows that 2B − A = 1 and B + A = 0 and takes the form A = 1/3 and B = 2/3. So, the sought-after inverse polynomial takes the form m1(x) = (x + 2)−1mod(x2 + x + 1) = (1/3)x + 2/3. Similarly, the search for is carried out. We write (x2 − x)(Ax2 + Bx + C)mod(x3 + x + 1) = 1, where Ax2 + Bx + C is the inverse polynomial modulo. We need to find the coefficients A, B, and C that satisfies the equation. After transformations (2Ax4 + 2Bx3 + (A + 2C)x2 + Bx + C)mod(x3 + x + 1) = (C − A − B)x2 + (−C − B)x + A − B = 1, we obtain 2C − A = 0, C − B − A = 0, −C − B = 0, and A − B = 1. From here, A = 2/3, B = −1/3, and C = 1/3. So, the inverse polynomial takes the following form: . Similarly, the value is computed. By applying the method of undetermined coefficients, the following transformations can be performed: (x)(Ax + B)mod(x2 + 1) = (Ax2 + Bx)mod(x2 + 1)⇒Bx − A = 1. The last equation leads to a system of equations that allows us to compute the coefficients’ values A = −1 and B = 0 and thereby find the inverse polynomial modulo m3(x) = −x. Thus, b1(x) = N(x)mod p1(x) = (15x6 + 18x5 + 12x4 + 5x3 + 18x2 + 17x + 3)mod(x2 + x + 1) = −7x − 13, b2(x) = N(x)mod p2(x) = (15x6 + 18x5 + 12x4 + 5x3 + 18x2 + 17x + 3)mod(x3 + x + 1) = 3x2 + 48x + 31, and b3(x) = N(x)mod p3(x) = (15x6 + 18x5 + 12x4 + 5x3 + 18x2 + 17x + 3)mod(x2 + 1) = 30x − 18.
Therefore, according to expression (3), the ciphertext is given by .
The parameters are computed using the method of undetermined coefficients. To find the inverse polynomial , we write (x + 2)(Ax + B)mod(x2 + x + 1) = 1⇒(Ax2 + (2A + B)x + 2B)mod(x2 + x + 1) = (A + B)x + 2B − A = 1, where (Ax + B) is the desired value. To determine the coefficients A and B, we compute the remainder and equate the corresponding values: (A + B)x + 2B − A = 1; from here, A = −1/3, and B = 1/3. Thus, .
Similarly, we search for , where Ax2 + Bx + C is the inverse polynomial modulo. After the transformation (2Ax4 + 2Bx3 + (A + 2C)x2 + Bx + C)mod(x3 + x + 1) = (C − A − B)x2 + (−C − B)x + A − B = 1, we obtain a system of three equations with three unknowns: C − B − A = 0, −C − B = 0, and A − B = 1. From here, A = 2/3, B = −1/3, and C = 1/3. Therefore, the sought inverse polynomial in Z[x] will take the following form: ; similarly, we can obtain .
In the next step, the following quantities are computed: , , and .
Additionally, for decryption, the following parameters need to be found: , , and .
Then, according to Formula (6), the original message is recovered as the plaintext: .
For the same input parameters as in the previous example, according to Formulas (8) and (9), the following ciphertext is obtained: . To decrypt, it is necessary to compute additional parameters according to Formula (4): .
The decryption process is carried out according to Formula (9): .
This simplification reduces computational complexity by avoiding the operation of finding the parameters qi(x) and .
2.4. Polynomial Symmetric Encryption Method Based on CRT
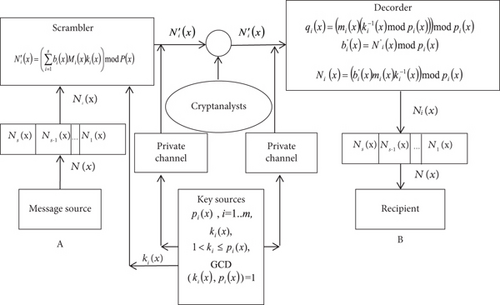
Another polynomial method of symmetric encryption based on the CRT involves breaking the plaintext N(x) into blocks—polynomials Ni(x) of lower order than the selected polynomial modules. These blocks will act as remainders bi(x) modulo the chosen moduli, such that if degpi(x) = n, then degNi(x) ≤ n − 1; that is, Ni(x) = an−1xn−1 + an−2xn−2 + ⋯+a0x0. After selecting the encryption parameters, the encryption is performed according to the expression (3). The ciphertext will be the value N′(x).
Decryption is carried out using Formulas (4) and (5), which are used to find the parameters and . Concatenating the coefficients an−1 of the polynomials Ni(x) forms the plaintext. It should be noted that in the case of requiring fast decryption, the ciphertext can also be represented by the parameters bi(x).
Figure 2 depicts the scheme of the polynomial symmetric encryption method in the CRT-based encryption system.
To encrypt using the aforementioned method, the chosen plaintext PSMFSRND = 1518120518171303 is divided into four blocks of two characters each: PS = 1518, MF = 1205, SR = 1817, and ND = 1303. Then, the plaintexts are formed as polynomials, N1(x) = 15x + 18, N2(x) = 12x + 5, N3(x) = 18x + 17, and N4(x) = 13x + 3, which are remainders modulo the chosen moduli p1(x) = x2 + x + 1, p2(x) = x3 + x + 1, and p3(x) = x2 + 1, and the corresponding coefficients k1(x) = x2 + 2x + 3, k2(x) = x3 + x2 + 1, and k3(x) = x2 + 3x + 2. The ciphertext for the first block is computed based on Formula (3): .
Upon decryption using Formulas (4) and (5), the following results are obtained: , , and . The message is reconstructed based on the relation (5): .
For the second block of the input message N2(x) = 12x + 5, the following ciphertext value is obtained: .
According to Formula (4), the remainders obtained are , , and . The restoration of the second block of the input message is done using relation (5): .
The ciphertext for the third block of the input message N3(x) = 18x + 17 will have the following form: .
Then, according to Formula (4), the remainders obtained are , , and . The restoration is done using relation (5): . Hence, .
Therefore, the encrypted message for the fourth block, N4(x) = 13x + 3 according to (3), will be the following polynomial: .
Then, according to Formula (4), the obtained remainders are , , and . The restoration of the fourth block is done based on expression (5): and .
The concatenation of the coefficients of the remainders corresponds to the input text PSMFSRND = 1518120518171303. According to the agreements between the participants, the ciphertext can be either the parameter Ni(x), or the remainders , where j is the block number of the message.
3. Results
In this section, we evaluate the cryptographic strength of a polynomial symmetric encryption algorithm in the system of residual classes.
| d | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|
| μ(d) | 1 | −1 | −1 | 0 | −1 | 1 | −1 | 0 |
| d | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 |
| μ(d) | 0 | 1 | −1 | 0 | −1 | 1 | 1 | 0 |
| d | 17 | 18 | 19 | 20 | 21 | 22 | 23 | 24 |
| μ(d) | −1 | 0 | −1 | 0 | 1 | 1 | −1 | 0 |
| d | 25 | 26 | 27 | 28 | 29 | 30 | 31 | 32 |
| μ(d) | 0 | 1 | 0 | 0 | −1 | −1 | −1 | 0 |
| d | 33 | 34 | 35 | 36 | 37 | 38 | 39 | 40 |
| μ(d) | −1 | 1 | 1 | 0 | −1 | 1 | 1 | 0 |
| d | 41 | 42 | 43 | 44 | 45 | 46 | 47 | 48 |
| μ(d) | −1 | −1 | −1 | 0 | 0 | 1 | −1 | 0 |
| d | 49 | 50 | 51 | 52 | 53 | 54 | 55 | 56 |
| μ(d) | 0 | 0 | 1 | 0 | −1 | 0 | 1 | 0 |
| d | 57 | 58 | 59 | 60 | 61 | 62 | 63 | 64 |
| μ(d) | 1 | 1 | −1 | 0 | −1 | 1 | 0 | 0 |
So, to find the number of irreducible polynomials f(x) = anxn + an−1xn−1 + an−2xn−2 + ⋯+a0x0 over GF(p), you need to determine all divisors of degree n, calculate the Möbius function for each of them, substitute them into Formula (10), and sum them. For example, for irreducible polynomials over GF(p) of degree n = 3 with divisors 1 (the value of the Möbius function is 1) and 3 (the value of the Möbius function is −1), their number can be found by the following formula: Sp(n) = (1/3)∑n/dμ(d)pn/d = (1/3)(μ(1)p3/1 + μ(3)p3/3) = (p3 − p)/3.
For a polynomial of degree 32 (the divisors are 1, 2, 4, 8, 16, and 32) over GF(2), according to Formula (10), the number of irreducible polynomials is as follows: S2(32) = (1/32)∑32/dμ(d)232/d = (1/32)(μ(1)232/1 + μ(2)232/2 + μ(4)232/4 + μ(8)232/8 + μ(16)232/16 + μ(32)232/32) = (1/32)(232 − 216) = 227 − 211 = 134215680.
Table 2 shows the number of irreducible polynomials for powers of n = 4, 8, 16, 32, 64, 96, and 128 and parameter p = 3, 5, 7, 11, 13, 17, 19, 23, 29, 31, 37, and 43.
| p/n | 4 | 8 | 16 | 32 | 64 | 96 | 128 |
|---|---|---|---|---|---|---|---|
| 2 | 3 | 30 | 4080 | 134215680 | 2.88 × 1017 | 8.25 × 1026 | 2.66 × 1036 |
| 3 | 18 | 810 | 2690010 | 5.79 × 1013 | 5.37 × 1028 | 6.63 × 1043 | 9.21 × 1058 |
| 5 | 150 | 48750 | 9.54 × 109 | 7.28 × 1020 | 8.47 × 1042 | 1.31 × 1065 | 2.29 × 1087 |
| 7 | 588 | 720300 | 2.08 × 1012 | 3.45 × 1025 | 1.90 × 1052 | 1.40 × 1079 | 1.16 × 10106 |
| 11 | 3630 | 26793030 | 2.87 × 1015 | 6.60 × 1031 | 6.97 × 1064 | 9.80 × 1097 | 1.55 × 10131 |
| 13 | 7098 | 1.02 × 108 | 4.16 × 1016 | 1.38 × 1034 | 3.06 × 1069 | 9.04 × 10104 | 3.00 × 10140 |
| 17 | 20808 | 8.72 × 108 | 3.04 × 1018 | 7.40 × 1037 | 8.76 × 1076 | 1.38 × 10116 | 2.46 × 10155 |
| 19 | 32490 | 2.12 × 109 | 1.8 × 1019 | 2.60 × 1039 | 1.08 × 1080 | 5.99 × 10120 | 3.74 × 10161 |
| 23 | 69828 | 9.79 × 109 | 3.83 × 1020 | 1.18 × 1042 | 2.21 × 1085 | 5.54 × 10128 | 1.56 × 10172 |
| 29 | 176610 | 6.25 × 1010 | 1.56 × 1022 | 1.96 × 1045 | 6.12 × 1091 | 2.55 × 10138 | 1.20 × 10185 |
| 31 | 230640 | 1.07 × 1011 | 4.55 × 1022 | 1.65 × 1046 | 4.37 × 1093 | 1.54 × 10141 | 6.12 × 10188 |
| 37 | 468198 | 4.39 × 1011 | 7.71 × 1023 | 4.75 × 1048 | 3.62 × 1098 | 3.67 × 10148 | 4.19 × 10198 |
| 41 | 706020 | 9.98 × 1011 | 3.98 × 1024 | 1.27 × 1050 | 2.58 × 10101 | 6.99 × 10152 | 2.13 × 10204 |
| 43 | 854238 | 1.46 × 1011 | 8.54 × 1024 | 5.83 × 1050 | 5.44 × 10102 | 6.77 × 10154 | 9.47 × 10206 |
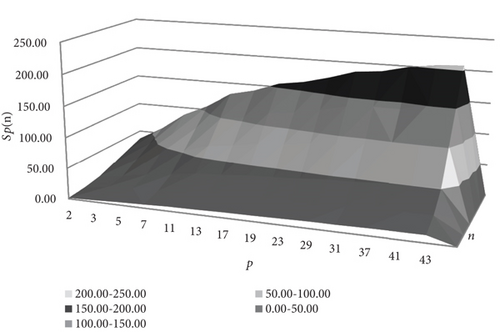
The numerical experiment shows that the number of irreducible polynomials increases with the expansion of the Galois field and the growth of the power. For the specified parameters p and n, it will lie in the following ranges: 30 ≤ Sp(8) ≤ 1.4612, 4048 ≤ Sp(16) ≤ 8.54∗1024, 1.34∗108 ≤ Sp(32) ≤ 5.832∗1050, 2.8823∗1017 ≤ Sp(64) ≤ 5.4425∗10104, 8.25293∗1026 ≤ Sp(96) ≤ 6.7717∗10154, and 2.65846∗1036 ≤ Sp(n) ≤ 9.4788∗10206. In addition, a given number of irreducible polynomials can be obtained either by changing the degree n or by expanding the field GF(p). For instance, S43(8) ≈ S7(16), S43(16) ≈ S7(32), S43(32) ≈ S7(64), S43(64) ≈ S7(96), and S43(96) ≈ S7(128).
Figure 3 shows the graphical dependence of the number of irreducible polynomials on these parameters on a logarithmic scale with base 10.
For instance, we can calculate the time (in clock cycles) needed to cryptanalyze the proposed encryption system with l = 5 and n = 32 in the Galois field GF(3) as follows: .
Table 3 estimates the cryptanalysis time in clock cycles for different parameter values of l, n, and Sp(n). Notably, the modern symmetric encryption algorithm AES-128 requires around 2128 ≈ 1037 clock cycles for resilience. Table 3 indicates that the proposed cryptosystem achieves a comparable level of security with the following parameters: S31(4), l = 7, and n = 4; S11(8), l = 5, and n = 8; S3(16), l = 6, and n = 16; S2(32), l = 3, and n = 32; and S2(64), l = 2, and n = 64.
| l/n(Sp(n)) | 4(S31(4)) | 8(S11(8)) | 16(S3(16)) | 32(S2(32)) | 64(S2(64)) |
|---|---|---|---|---|---|
| 2 | 1.5 × 1011 | 7.9 × 1015 | 3.17 × 1014 | 5.879 × 1029 | 5.8 × 1037 |
| 3 | 1.7 × 1016 | 1.03 × 1023 | 4.2 × 1020 | 1.674 × 1043 | 8.3 × 1054 |
| 4 | 3.8 × 1021 | 2.8 × 1030 | 1.1 × 1027 | 9.595 × 1056 | 2.4 × 1072 |
| 5 | 2.02 × 1026 | 1.7 × 1037 | 6.98 × 1032 | 1.29 × 1070 | 1.6 × 1089 |
| 6 | 8.6 × 1031 | 8.5 × 1043 | 3.5 × 1038 | 1.386 × 1083 | 8.4 × 10105 |
| 7 | 3.09 × 1035 | 3.5 × 1050 | 1.5 × 1044 | 1.245 × 1096 | 3.8 × 10122 |
Table 3 shows that adding one module for parameters n = 4 and S31(4) increases the strength by about 5 orders of magnitude, for n = 8 and S11(8) by 7 orders of magnitude, for n = 16 and S3(16) by 6 orders of magnitude, for n = 32 and S2(32) by 13 orders of magnitude, and for n = 64 and S2(64) by 17 orders of magnitude.
Figure 4 shows the graphs of cryptographic strength dependencies O(n, l) on a logarithmic scale with a base of 10 of the proposed symmetric polynomial encryption algorithm in RNS on the number of modules l for the polynomial powers n = 4 and 8 and the parameters p = 2, p = 3, p = 5, and p = 7. The horizontal line 6 corresponds to the strength of the modern symmetric encryption algorithm AES-128.

The figure shows that all graphs have the same bell-shaped character. The cryptographic strength increases significantly with increasing degree and dimension of the Galois field p and reaches its maximum at l = Sp(n)/2. This means that the cryptanalysis of the proposed algorithm requires combinatorial complexity, which leads to an NP-complete problem.
4. Conclusion
In this article, we first developed symmetric cryptographic algorithms based on the polynomial RNS. The mathematical support and schemes of the proposed polynomial symmetric encryption in the RNS are developed. To evaluate its robustness, we have studied and constructed analytical expressions that indicate that the cryptanalysis of the proposed algorithm requires combinatorial complexity, which leads to an NP-complete problem. It is established that the cryptographic strength increases significantly with the increasing degree and dimension of the Galois field p and reaches its maximum in the case when the number of modules is equal to half the possible number of irreducible polynomials with given polynomial degrees and Galois field orders. This means that finding an efficient algorithm to solve this problem requires significant computing resources and time.
We compare the strength of the proposed encryption method with the modern symmetric encryption algorithm AES-128. As a result of numerical experiments, it was found that the developed polynomial encryption methods in the RNS provide a level of resistance similar to AES-128 with the following parameters: S31(4), l = 7, and n = 4; S11(8), l = 5, and n = 8; S3(16), l = 6, and n = 16; S2(32), l = 3, and n = 32; and S2(64), l = 2, and n = 64.
Thus, the proposed cryptographic algorithm based on the polynomial RNS can be used to ensure reliable protection of confidential information in systems with limited computing resources.
Consent
All authors have provided their consent for the publication of this research.
Conflicts of Interest
The authors declare no conflicts of interest.
Author Contributions
Conceptualization: I.Y. and M.K. (Mykhailo Kasianchuk); methodology: I.Y. and M.K. (Mykhailo Kasianchuk); validation: M.K. (Mykhailo Kasianchuk), M.K. (Mikolaj Karpinski), and R.S.; formal analysis: M.K.(Mykhailo Kasianchuk) and M.K.(Mikolaj Karpinski); investigation: I.Y., M.K. (Mykhailo Kasianchuk), M.K.(Mikolaj Karpinski), and R.S.; data curation: I.Y. and M.K.(Mykhailo Kasianchuk); writing—original draft preparation: I.Y., M.K.(Mykhailo Kasianchuk), and R.S.; writing—review and editing: I.Y., M.K.(Mykhailo Kasianchuk), and R.S. All authors have read and agreed to the published version of the article.
Funding
The authors received no specific funding for this work.
Acknowledgments
The authors express their sincere gratitude to the Armed Forces of Ukraine for providing security, which made it possible to conduct our research.
Open Research
Data Availability Statement
The authors confirm that the data supporting the findings of this study are available within the article.




