Ensuring Security and Privacy in VANET: A Comprehensive Survey of Authentication Approaches
Abstract
Vehicular ad hoc networks (VANET) are revolutionizing intelligent transportation systems (ITS), and as a result, research on their security is becoming increasingly important. As the primary security concern for VANET, authentication security is still quite difficult to achieve. Consequently, the prior knowledge of VANET is covered in this survey before outlining the primary security concerns. To set itself apart from previous surveys, this study suggests security properties and challenges among VANET. Next, the essential and significant features of a secure VANET system, such as confidentiality and integrity of data, and the availability of network systems have been reported, the authenticity of nodes and messages, and the refusal to deny data once it has been transmitted is detailed. Later, it outlined the requirement of the ITS which makes the survey unique. More importantly, the report on the most recent developments in VANET concentrates on the authentication schemes that have been proposed recently. The security features and authentication resistance against attacks, along with the overhead and efficiency of these schemes, are thoroughly examined and contrasted. A detailed analysis of V2V, V2I, and V2X authentication is been reported. Various cryptographic schemes have been discussed along with some advanced techniques such as Blockchain and hybrid schemes. An overview of the integration of 5G/6G networks is documented. Applications of VANET have been discussed in detail along with some open challenges in VANET. In summary, this work reviews a few lessons learned and explores different possibilities for future research.
1. Introduction
The rapid growth of connected vehicles and intelligent transportation systems (ITS) is attracting significant focus from the academic and business communities. The vehicle’s connectivity is transforming the transportation landscape, offering new opportunities for innovation and improved user experience [1]. Traffic congestion and road accidents are predicted to be two of the major challenges facing our transportation system in 2030 [2]. The connected vehicle market is expected to grow significantly over the next several years due to factors like the growing adoption of autonomous vehicles, the growing demand for safety and security features, and the growing popularity of infotainment and entertainment services. Thus, robust and secure networks are essential for ITS to function effectively. Dedicated Short-Range Communications (DSRC) and Wireless Access in Vehicular Environment (WAVE) operate in the 5.9 GHz spectrum and provide short-range, high-speed connectivity between automobiles and the infrastructure beside the road [1–3].
Vehicular ad hoc networks (VANET) are highly dynamic networks, with vehicles constantly joining and leaving the network. This makes it difficult to design and deploy VANET that are scalable, reliable, and secure. Say, for example, there are two vehicles in the networks V1 and V2. V1 wants to establish communication with V2 by sending a basic safety message, and it is necessary to verify the authenticity of vehicles and their messages to prevent malicious actors from impersonating legitimate vehicles or sending false or malicious messages. There must be a way to ensure that only authorized vehicles can communicate and will ensure that the messages are not tampered with. The authenticity of vehicles and messages is acknowledged as the authentication of entities and the authentication of the messages, respectively. VANET has to be resilient to a wide range of cyberattacks, including spoofing, impersonation, and denial-of-service attacks, to guarantee the security of their communication, and the safety of their users. VANET must protect the privacy of vehicles and their drivers, ensuring that their identity (ID) and location are only known to authorized entities. Privacy, conditional privacy, and scalability are essential factors to consider when designing and deploying VANET, in addition to security services.
1.1. Survey of a Few Existing Works
Various levels of privacy and security solutions have been proposed for VANET, and researchers have conducted extensive surveys of these solutions. Table 1 consists of a few surveys that have been done recently in VANET, which are discussed briefly in the following section.
| Paper | Domain surveyed | Year |
|---|---|---|
| [4] | VANET authentication schemes | 2017 |
| [5] | Security problems and solutions in VANET | 2017 |
| [6] | Security attacks and detection mechanisms on ITS | 2017 |
| [6] | VANET attacks: communication, implementation, and difficulties | 2019 |
| [7] | The latest advances in privacy, trust, and security for VANET networks | 2019 |
| [8] | Techniques for privacy preservation and authentication in VANET | 2020 |
| [9] | Certificate revocation (CR) schemes in VANET | 2020 |
| [10] | Authentication techniques in VANET | 2020 |
| [11] | Privacy and authentication techniques in VANET | 2021 |
| [12] | VANET’s privacy-preserving authentication schemes: threats, difficulties, and unresolved problems | 2021 |
| [13] | Issues and recent advances in vehicular public key infrastructure (VPKI) | 2022 |
| [14] | Vehicular ad hoc networks: authenticity and threat detection schemes endangering it | 2023 |
| [15] | Security and privacy in vehicular ad hoc network and vehicle cloud computing | 2020 |
| [16] | Intrusion detection systems and honeypot proactive security mechanisms in VANET and VANET cloud | 2018 |
| [17] | VANET security services in traffic management system | 2019 |
In [4], the investigation of VANET authentication protocols and comparing them based on their security, performance, and efficiency has been discussed. The survey was lacking in comparing the conditional privacy-based schemes, unobservability, tracking of location, and scalability. They did not discuss the latest techniques such as Blockchain, which have the potential to revolutionize security and privacy in VANET. In [5], the authors have discussed the characteristics of VANET, the challenges of implementing them efficiently, the widely recognized security standards and architectures, and the grouping of attacks and their solutions. Nevertheless, the writers did not talk about simulators or provide a clear overview of the authentication schemes as described in [4]. In [6], the authors discussed the threats and prevention mechanisms for VANET identified in the existing literature and presented an onboard unit (OBU)–based solution. They claimed that the researchers have addressed the Sybil attack more than various kinds of intrusions. The authors additionally talked about the Internet of Vehicles (IoV) and stated that the majority of Internet of Things (IoT) gadgets will be in vehicles and that steps to enhance the multiple security difficulties need to be given attention. Nevertheless, the writer did not provide a comprehensive resolution to IoV security. The use of ITS in VANET has been discussed in [6], as well as the privacy and security matters involved. The writer also discussed the effectiveness of VANET and cloud-based computing in addressing security as well as privacy concerns and talked about the uses and unresolved problems with VANET. In [7], the writers talked about the VANET architecture, the grouping of security attacks as well as security resolutions for VANET. They also discussed trust in VANET, and the challenges involved in establishing trust and mitigation strategies. Additionally, they discussed various simulators that can be used to test and evaluate VANET security solutions. In [8], the authors discussed the key security, privacy, and message dissemination challenges in VANET and also reviewed the progress that has been made in addressing these challenges over the past 10 years. In [9], the authors discussed the different types of certificate revocation schemes, based on where the revocation information is stored. They also identified the key challenges and techniques at each stage of the certificate revocation process. In [10], the authors discussed the different types of VANET authentication schemes, their effectiveness in mitigating various attacks, and their advantages and disadvantages. They also identified the key research directions regarding the domain of VANET authorization. In [11], the authors discussed the security and privacy trade-offs in VANET by presenting a detailed comparison of different privacy and security solutions concerning privacy and security requirements, computational overhead, and security threats. Additionally, they identified the open challenges in VANET security and privacy. In [12], the authors have provided a thorough investigation of current security measures and classified different security breaches in VANET. They classify the security schemes based on various characteristics and discuss the performance analysis, controlled attacks, and security requirements of each classification briefly. The authors highlight some of the obstacles that must be addressed to deploy secure VANET. In [13], the authors present a state-of-the-art review of VPKI, including a discussion of the latest issues and advances in the field. They also evaluate existing VPKI proposals based on privacy and availability metrics and suggest future research. In [14], the writers offer a thorough analysis of VANET, covering topics such as their design, privacy protection, secure communication, communication standards, and authentication methods. Additionally, they analyze the authentication features and attack resistance of various authentication schemes, classify attacks, and summarize attack detection schemes. The location privacy mechanism and trust models in VANET have been discussed by Sheikh, Liang, and Wang [15]. They additionally addressed the issue of the potential applications that could be impacted by threats or attacks. In VANET, they also discovered a few unresolved issues. In their comprehensive analysis and comparison of the benefits and drawbacks of each approach, Sparsh and Kaula [16] explored several intrusion detection systems. The most advanced VANET techniques currently in use have been examined by Sheikh and Liang [17]. Later, they conversed about the in-depth examination of security and authentication scheme designs. They also spoke about some of the safety uses for VANET.
Existing surveys on VANET security have not provided a thorough and understandable review of the VANET authentication and key distribution methods. Furthermore, neither of these studies has covered how Blockchain and 5G technology might be used in VANET. This study will complement existing surveys by providing a lucid and easy-to-understand overview of authentication, key distribution, and other security topics in VANET.
1.2. Contributions From This Study
- 1.
To ensure the comprehensiveness and independence of this survey, let us begin by providing a detailed overview of the VANET, encompassing its design, accepted communication protocols, safe communication mechanisms, and protocols for authentication. Later, discuss the security concerns that are unique to VANET.
- 2.
Next focus on recent advances in VANET authentication and privacy protection schemes. Later talk about and examine these schemes in a detailed manner, categorizing them based on their underlying principles and comparing them concerning the attributes related to security, resistance to attacks, effectiveness, and overhead.
- 3.
Various authentication topologies have been discussed in detail along with recent technologies.
- 4.
This study discusses the requirements of ITSs in detail. Finally detailed a few open challenges in VANET and reported 5G and 6G networks and applications of VANET.
The VANET is an emerging technology, and a lot of changes are anticipated regularly in terms of security, privacy, and trust implementation by both the academia and the industry. In this regard, adding the advancement to the existing survey mandated the proposal of this survey work. Also, the researchers need to stay updated; this survey stands unique, as it discusses the taxonomy of the secure ITS requirement and a deep insight into vehicle to vehicle (V2V), vehicle to infrastructure (V2I), and vehicle to everything (V2X). Moreover, recent work related to hybrid authentication schemes, Blockchain, 5G, and 6G technologies has been incorporated.
The remaining sections of the article are structured like this: Section 2 provides an extensive summary of the VANET architecture, communication protocols, features, attack types, and security requirements of VANET. Section 3 provides a comprehensive overview of secure communication and validation techniques in VANET, focusing on node verification and message authentication. Section 4 discusses the taxonomy of secure ITSs. Section 5 discusses the categorization of VANET authentication methods, analyzing the safety, privacy, and scalability requirements of each category. Section 6 discusses some of the open challenges in VANET. To summarize, we have presented the conclusions and suggestions for future research in Section 7. Figure 1 shows the flow of the manuscript.
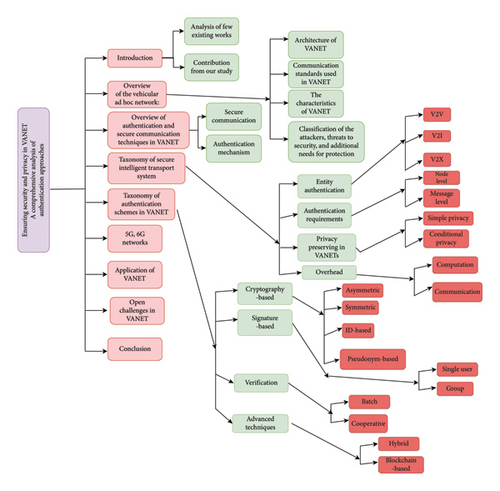
2. Preliminaries
2.1. Architecture of VANET
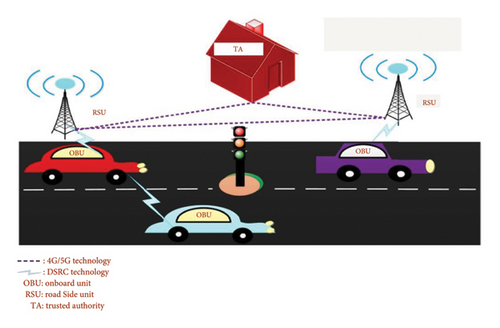
Figure 2 illustrates a recommended VANET system comprising vehicles, OBUs, roadside units (RSUs), trusted authorities (TAs), and other components [18, 19].
2.1.1. OBU
The Heart of V2X Communication. The OBU is a part of VANET. It acts as one of the communication hubs, for automobiles within a network enabling real-time information exchange between vehicles and roadside infrastructure. The OBU mounted on each connected vehicle has a significant impact in supporting driving applications. To fulfill its role in VANET communication, the OBU integrates sensors, processing units, and storage units [21].
Sensors: Within the OBU, some sensors gather data about the vehicle’s surroundings. They provide information such as position, speed, direction, and acceleration in time. These data are vital for enabling cooperative driving applications.
2.1.2. Processing Unit
The OBU processing unit has the responsibility of analyzing the sensor data and generating messages. These messages contain details about the vehicle’s state and intentions. They help vehicles and roadside infrastructure make decisions.
2.1.3. Storage Unit
The OBU also includes a storage unit that stores data collected from the sensors as generated messages. This stored information serves purposes like providing drivers with data, about their driving habits or assisting in accident investigations.
2.1.4. Enabling Cooperative Driving Applications
The Power of Real-Time Information Exchange: The real-time exchange of information, by the OBU, forms the basis, for driving applications. These applications utilize the shared data to improve traffic safety enhance traffic flow and give information to drivers.
2.1.5. Cooperative Adaptive Cruise Control (CACC)
Vehicles equipped with OBUs can share their speed and acceleration data, so they can maintain a safe distance from each other and smoothly adjust their speeds, reducing traffic congestion and improving fuel efficiency.
2.1.6. Traffic Signal Optimization
OBUs can communicate with RSUs at traffic junctions to provide real-time information on traffic flow. These data can be used to optimize traffic signal timing to reduce wait times and improve overall traffic flow.
Avoiding Collisions: OBUs can share their positions and intentions enabling vehicles to anticipate dangers and take measures to prevent accidents.
2.1.7. RSUs
The Pillars of Vehicular Communication Infrastructure. A vital part of VANET are RSUs, serving as fixed communication hubs along roadsides. Strategically deployed at intersections, along highways, and in dedicated buildings [22], RSUs facilitate real-time information exchange between vehicles and infrastructure, enabling a wide range of cooperative driving applications. The system utilizes DSRC technology to establish communication links with other DSRC-enabled devices, including OBUs, RSUs, and TAs. The RSU serves two main purposes: (a) broadcasting messages to OBUs, RSUs, and TAs; (b) the RSU periodically executes security applications to maintain network integrity [23] and provide reliable services to connected OBUs. Additionally, it communicates timely traffic details to automobiles inside its coverage region.
The certificate authority (CA), also known as the TA, holds the responsibility of keeping track of digital certificates and vehicle registration, assigning verified aliases for automobiles, maintaining system parameters, and verifying the authenticity of several public keys within the public key infrastructure (PKI). Entities like the Division of Motor Vehicles can carry out this crucial function [24, 25] or automobile manufacturers. Moreover, the TA is equipped to identify and isolate vehicles engaging in malicious activities, such as spreading false messages and ensuring network security and trust.
2.2. Communication Standard Used in VANET
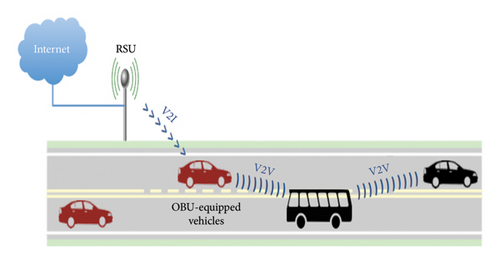
The communication range of DSRC [26, 27] varies from 100 to 1000 m with data rates ranging from 6 to 27 Mbps. Safety-related messages are typically transmitted every 100 to 300 s [28, 29]. Vehicles can communicate with each other or with RSUs, which periodically broadcast beacon messages. Figure 3 represents the DSRC-based communication for V2V and V2I. DSRC offers exceptional resilience in the face of obstacles and dynamic environments, ensuring uninterrupted connectivity at speeds reaching 500 km/h. Its non-line-of-sight (NLOS) capability enables communication even when direct paths are blocked, making it ideal for applications that demand reliable data exchange in complex scenarios. Additionally, DSRC’s ability to function in extreme weather conditions further expands its versatility and applicability.
The 5.85 GHz to 5.925 GHz band has a 75-MHz bandwidth spectrum [31] that has been set aside by the Federal Communications Commission (FCC) for “DSRC.” This dedicated spectrum allocation ensures reliable and interference-free communication for V2V and V2I applications. WAVE [32] is a dedicated wireless communication standard designed to facilitate communication between vehicles and infrastructure (V2I and V2V), building the basis for ITS. WAVE’s short-range communication capabilities, high data rates, and dedicated safety channel make it ideal for a variety of applications that boost traffic flow, increase road safety, and give drivers useful information. The key features of WAVE are as follows: (a) 5.9 GHz is the frequency range used for short-range communication. WAVE provides reliable and timely data exchange between vehicles and infrastructure within a range of up to 1000 m. (b) High Data Rates: With data transmission rates reaching up to 27 Mbps, WAVE effectively transfers traffic data, safety messages, and other kinds of critical information. (c) Dedicated Safety Channel: WAVE prioritizes public safety by allocating a dedicated channel for emergency messages related to accidents, road closures, and other critical events. (d) Ease of Deployment and Cost-Effectiveness: WAVE leverages existing DSRC technology, making it relatively simple to deploy and cost-effective compared to other communication standards.
IEEE802.11p—The Foundation of Short-Range Communications (DSRC) with Specialized Focus on Vehicle Networks [33]. IEEE802.11p functions as the foundational technology of DSRC, which utilizes channels with a 10-MHz bandwidth in the 5.9-GHz range (5.850–5.925 GHz) to facilitate communication in VANET. IEEE802.11p specifies the media access layer (MAC) and physical access layer (PHY) requirements for VANET operations [34].
2.3. The Characteristics of VANET
- •
Limited Latency: Due to the high speeds of vehicles in VANET, even a small delay in V2V communication can have disastrous consequences.
- •
Evolving Network: Because of its dynamic character, automobiles continuously entering and leaving the network complicate the task of identifying and tracking malicious nodes.
- •
Time-Critical Communication: Messages in VANET must be transmitted and processed within specific time limits to maintain the effectiveness of safety applications.
- •
Resource Constraints in VANET: VANET typically operates with limited computational resources and storage capacity, making it difficult to efficiently handle the large volume of data generated by vehicles and infrastructure.
- •
Dynamic Nature of VANET: VANET is a highly dynamic network, with vehicles constantly joining and leaving the network, making it challenging to maintain a stable and secure communication environment.
2.4. The Classification of the Attackers, Threats to Security, and Additional Needs for Protection
- •
Active Assailant: These assailants cease transmitting the received message and create fake ones.
- •
Passive Attacker: These hackers will listen over the wireless channel, collecting traffic data and forwarding it to additional hackers.
- •
Internal Attacker: When considering other perpetrators, these ones are much more hazardous because they have comprehensive knowledge of the network configuration.
- •
Outsider Attacker: Since these attackers lack authentication, they pose a lesser threat than insider attacks.
- •
Malicious Attackers: These attackers’ primary objective is to damage other nodes for no personal gain. They could seriously harm the network.
- •
Rational Attacker: These attackers are easily traced and cause harm to the network for their gain.
- •
Local Attacker: These assailants are capable of targeting a small area.
- •
Extended Attacker: These attackers can launch network-wide attacks and have a longer range.
- •
Attacks by Eavesdroppers: This demonstrates an automobile’s reliability by using the ID of another vehicle.
- •
Modification Attack: The attacker in this case modifies the message to contain false data.
- •
Replay Attack: This involves the assailant continuously injecting outdated beacons and messages into the VANET, making it difficult for vehicles to navigate in an emergency.
- •
Bogus Information Assault: The attacker alters the message broadcasted by adding false and inaccurate information.
- •
Sybil Attack: Any vehicle impersonating another vehicle to disrupt the VANET regular operation is considered a Sybil.
- •
ID Disclosure Attack: Vehicle ID theft occurs when a vehicle’s identifying information is stolen or spoofed, allowing the perpetrator to impersonate the original vehicle.
- •
Location Tracking: Vehicle location tracking attack involves an unauthorized attempt to monitor the real time or historical whereabouts of a vehicle.
- •
DoS Attacks: Attacks that cause a denial of service in VANET involve disrupting the network’s communication channels or overwhelming its resources, rendering it unusable for legitimate users.
To ensure secure communication, VANET authentication schemes need to meet certain requirements, including node authentication, message authentication, privacy preservation, nonrepudiation, low computational overhead in communication, traceability, and unlinkability.
3. Overview of Authentication and Secure Communication Techniques in VANET
3.1. Secure Communication
During V2V communication, messages are transmitted in large quantities from one vehicle to another. These messages include alerts concerning accidents and gridlock on the road, group communications among vehicles sharing characteristics, and beacon communications that contain information about the vehicle’s current speed, acceleration, and other states [42]. Every message must be authenticated in order to guarantee security. Figure 4 illustrates how secure messages are authenticated in vehicles [43].
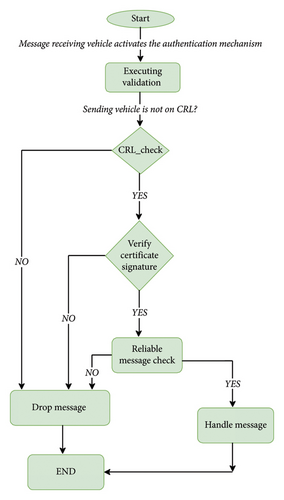
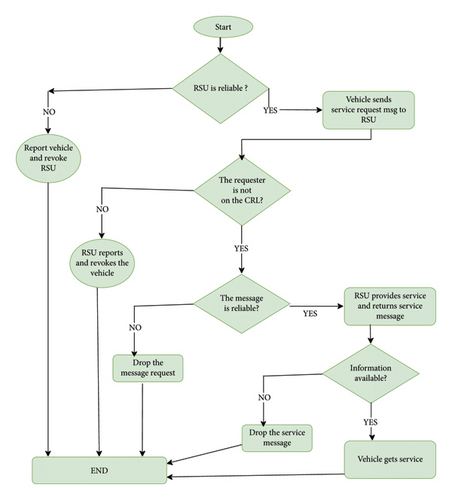
In V2I communication, the same high volume of beacon and warning messages are sent in V2I communication [44], in addition to messages from the vehicle to the RSU regarding service requests, like requests for information about hotels in the area. Figure 5 displays the requested services flowchart [30].
3.2. Authentication Mechanism
The following steps comprise the authentication mechanism in general [45, 46].
3.2.1. System Setup
During this stage, the TA is in charge of finalizing the system’s deployment and initialization as well as creating a set of system parameters [47].
3.2.2. Node Registration
For OBU and RSU to access VANET and obtain services, and registration details, such as node ID, they must first apply for TA registration and obtain license credentials. Next, the registered OBU and RSU have their credentials preloaded, and after that, the nodes have been installed and made available.
3.2.3. Sign-Up of Users
Users must first apply for registration and then receive access credentials from the TA legal. Registration details include login credentials, biometric attributes, and user ID, among other things. After reviewing the application, the TA grants official credentials to the registration applicant and authorizes the user to access the service.
3.2.4. Sign In
Registered users message the RSU through the public channel to request access.
3.2.5. Authentication
After getting the message about the user request, RSU sends the notification to the user and TA of their ID verification while simultaneously sending the user’s authentication request message. The user’s request for login is either accepted or rejected after getting replies from both.
3.2.6. Creating Secure Communication
To create secure communication, authorized users can log in to the RSU and quickly create a session secret key.
3.2.7. Password and Biometric Update
This stage takes place when users want to modify biometric features or passwords to guarantee information security. The storage device has to be promptly updated with the updated data.
3.2.8. Revocation of the Access Certificate
This step is required if a legitimately registered user’s ID, password, or biometric data are allegedly taken in the actual world. Upon intercepting and deciphering the login request, the user notifies the platform right away. In this case, the TA will give the user a new access certificate and cancel their current one [48].
When entities receive a message, they will first verify the message’s authenticity and integrity to make sure that it should cease interfering with message delivery since it is not originating from a malicious node [49]. Message authentication and node authentication are the two components of VANET ID verification.
3.2.9. Authentication of Nodes
Illegal access, ID theft, and phishing websites are prohibited. As primary VANET components, OBU and RSU work together and also make up the initial group of security for authentication. The regulatory frameworks that are in place in most countries now require OBU and RSU to provide ID authentication services with unique ID digital certificates. Unlike a node that an attacker could spoof in a virtual environment, this ensures the communication object’s legitimacy, authenticity, and dependability [50]. As such, the vehicle may confer adequate trust upon every entity that successfully completes the verification, guaranteeing that the system remains unlocked to authorized users and closed to unauthorized attackers.
3.2.10. Authentication of Messages
Message authentication is the second type of authentication security that deals with communication messages between entities. Message authentication characteristics like accessibility, privacy, accuracy, traceability, low overhead, unlinkability, and nonrepudiation of privacy protection and an authentication system [51] are vital for ensuring the security of VANET communication.
Ensuring dependability between system entities is the goal of both message and node authentication. The level of conviction in a message’s ability to be comprehended, acknowledged, and acted upon is known as reliability. Message validation verifies the integrity of the message data, while node authentication verifies the trustworthiness of the entities. For secure communication in VANET, the reliability of message and entity data is equally important [52].
4. Taxonomy of Secure ITS
An ITS is a sophisticated system designed to enhance the sustainability, safety, and efficiency of transportation networks by integrating multiple ICTs. Data regarding road infrastructure, vehicle movements, and traffic conditions are gathered, analyzed, and shared using ITS technologies. By using these data, traffic flow can be optimized, congestion can be decreased, safety can be increased, and travelers can get real-time trip information. Figure 6 shows the taxonomy of a secure ITS.
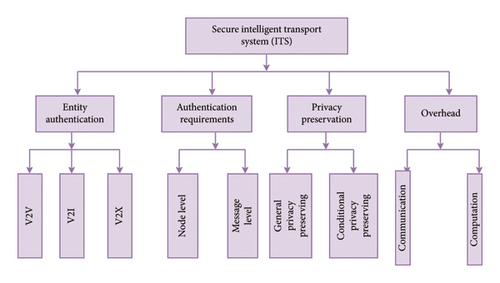
4.1. Authentication Based on Entities
When it comes to ITSs, the first thing to ensure is the entities involved. Entities play an important role in the ITS, and there are basically three entities involved (i) V2V, (ii) V2I, and (iii) V2X.
V2V Authentication: For ITS to facilitate safe communication between automobiles, V2V authentication is a vital security feature. To stop impersonation, replay, and message modification attacks, it makes sure that cars can confirm each other’s identities and the veracity of the messages they exchange. Information about traffic and warning messages is transferred in vehicular communication network types. To reduce accidents and traffic congestion, vehicle communication systems are useful. The study of V2V communication has increased recently due to the growing significance of road safety. IEEE 802.11p establishes a global standard for wireless connectivity in vehicle settings (WAVE). V2V and V2I are the two main networking protocols found in vehicular environments when using wireless access; these protocols are grouped under the umbrella of ITS. Additionally, several applications such as traffic management and road conditions will be made possible by vehicular communication networks [53].
A combination of three networks, namely, intravehicle, intervehicle, and vehicular ad hoc, is known as the V2V network. V2V refers to a spread wireless communication and exchange of data system that is large in scope and connects nearby automobiles in accordance with standard data interaction protocols and communication protocols, predicated on the notion that three networks can merge to form one. It is an integrated network for smart management of traffic, intelligent data service, and smart vehicle control, and it represents a typical use of the IoT technology for innovative transportation systems (ITSs). It will be crucial to acquire core technologies and standards to succeed in this developing market. But just as crucial as developing the V2V technologies themselves should be the integration of those technologies with other infrastructures. This will lead to the V2V being a crucial component among the most extensive IoT [53].
Mahmood et al. [54] suggested a secure V2V message transmission system for VANET, enhancing privacy preservation and meeting security and performance requirements.
Bansal et al. [55] provide an ID-based computationally efficient privacy-preserving authentication (ID-CEPPA) V2V communication system for V2V (VANET) networks and elliptic curve cryptography (ECC). In V2V communications, the scheme effectively ensures message originality and nonrefutation, source authentication, and vehicle’s absence of ID.
Lim and Tuladhar [56] discussed that driving safety and traffic efficiency are increased when vehicles are authenticated locally without the use of infrastructures or trusted authorities thanks to LIDAR, a lidar information-based authentication mechanism for V2V communication.
Hasrouny et al. [57] have looked into a secure design that ensures integrity in V2V communication. It suggests group-oriented V2V communication and authentication for the distribution of safety messages with a lightweight solution that is decentralized through group leaders (GLs), effective, affordable, and suitable in real-world scenarios.
Snehal and Hajare [58] have provided a review on group-oriented V2V communication authentication and authentication in VANET.
Aliev and Choi [59] put forth a scalable, secure, and group key management approach for message encryption. The suggested approach for managing group keys is scalable and can effectively manage different situations, such as joining a node or departing the group, using an algorithm called rekeying.
4.1.1. V2I Authentication
A communication model known as V2I enables vehicles to exchange data with the elements that make up a nation’s highway network. These components include parking meters, lane markers, traffic lights, streetlights, RFID readers overhead, and cameras. Typically, V2I communication is wireless and bidirectional. An ad hoc network can transmit data from infrastructure elements to the vehicle and vice versa. V2I, like V2V communication, transfers data using short-range communication (DSRC) frequencies.
V2I sensors play a crucial role in gathering infrastructure information and delivering instant guidance to travelers regarding road conditions, traffic density, incidents, ongoing construction zones, and parking availability within an ITS. Likewise, to enhance fuel efficiency and streamline traffic, traffic management oversight systems can adjust traffic signal phase and timing (SPaT) and establish flexible speed limits based on data obtained from both vehicles and infrastructure. A fundamental element integral to all autonomous vehicle initiatives encompasses the hardware, software, and firmware facilitating seamless communication between vehicles and the road infrastructure [60].
Federal Highway Administration (FHA) V2I guidelines were released in January 2017 [60] by the U.S. Department of Transportation to enhance safety and mobility through a faster rollout of V2I communication systems. The guidelines are intended to assist state and local governments in organizing and managing the data necessary to support V2I initiatives. One of the main issues is financing, which is probably going to lead to a change from public financing through toll roads and fuel taxes to increase public–private collaboration involving the automakers, who stand to gain from having access to the big data generated by V2I [60].
Showkat Moni and Manivannan [61] provided a lightweight authentication system for VANET based on cuckoo filters that lower the overhead of CRL verification. Security verification and analysis indicate that the suggested protocol is resilient to impersonation, replay, and man-in-the-middle attacks.
Qi, Ding, and Zheng [62] presented that based on ECC, a simple, anonymous, and batch-verified V2I and V2V authentication protocol is suggested. We use biological keys and physically unclonable function (PUF) to prevent OBU intrusion attacks and RSU-captured attacks. We also create a feature embedding strategy with dynamic pseudo-ID to enable the TA to recover the personality of the malicious vehicle.
Wang, Shen, and Lai [63] discussed a trustworthiness-based time-efficient scheme for V2I authentication that transfers ownership securely between infrastructures, enabling fast reauthentication of vehicles.
In [64], the authors discussed that to facilitate communication from V2I in VANET and suggest a privacy preservation authentication scheme (PPAS). To minimize authentication latency, PPAS performs the authentication process locally, bypassing the need to return to the TA.
Wang, Shen, and Lai [65] presented that to improve the trustworthiness of scalable computation’s scalability, Blockchain is employed. The B-TSCA scheme, which facilitates secure ownership transfer between infrastructures, enables swift reauthentication of vehicles through Blockchain assistance and scalable computation.
Son et al. [66] discussed that due to its potential to offer decentralization, transparency, and data integrity, Blockchain-based VANET are currently the subject of active research. They proposed a Blockchain-based handover authentication protocol for VANET, leveraging the power of Blockchain technology. For network efficiency, the suggested protocol limits the computation that cars do during handovers.
Lv and Liu [67] discussed a lightweight, privacy-preserving V2I authentication protocol called PLVA. More specifically, during the initial stage, every RSU within an area is transformed into a vector by means of the Moore curve approach, a car determines the RSUs’ details of its planning path utilizing BGN homomorphic encryption prior to the car starting its journey, while CA understands nothing about the route plan, but it helps with the aforementioned method.
4.1.2. V2X Authentication
V2X refers to the exchange of information between a car and any object that could influence or be impacted by it. In addition to other more specialized forms of communication, such as V2I, vehicle-to-network (V2N), V2V, vehicle-to-pedestrian (V2PED), and vehicle-to-device (V2D), it is a vehicular communication system.
The primary driving forces behind V2X are mass surveillance, energy savings, traffic efficiency, and road safety. According to U.S. NHTSA estimates, if a V2V system were put in place, there would be at least a 13% decrease in traffic accidents annually, or 439,000 fewer crashes [68]. V2X communication technologies can be either of two types, in accordance with what technology is being used: WLAN-based or cellular-based.
- •
Interaction between an automobile and any organization that could influence or be impacted by the automobile is known as V2X.
- •
Bluetooth and Wi-Fi Direct V2D systems, such as Google’s Android Auto and Apple’s CarPlay.
- •
Vehicles to Grid (V2G): Sharing data with the smart grid to improve load balancing.
- •
Likewise referred to as vehicle-to-home (V2H) and vehicle-to-building (V2B).
- •
Vehicle-to-load (V2L) cellular (3GPP)/802.11p-based V2N communication.
- •
Remote vehicle diagnostics (DoIP) and over-the-air (OTA) updates are examples of vehicle-to-cloud (V2C) technology.
- •
V2I includes things like parking meters, lane markers, and traffic signals.
- •
Wheelchairs and bicycles are examples of vehicle-to-passenger (V2P) transportation.
- •
V2V refers to the transfer of data in real time between adjacent vehicles.
Cellular-based V2X systems are not as standardized as WLAN-based V2X systems. IEEE released the WLAN-based V2X (IEEE 802.11p) specification for the first time in 2010 [69]. It facilitates direct communication between automobiles and infrastructure (V2I) as well as between vehicles (V2V). The term DSRC describes this technology. DSRC makes use of 802.11p′s radio communication infrastructure.
Toyota launched cars with V2X technology in 2016—becoming the first manufacturer to do so globally. Only available for purchase in Japan, these cars are equipped with DSRC technology. The second carmaker to launch V2X was GM in 2017. Additionally, DSRC V2X is available on a Cadillac model sold by General Motors in the United States.
V2X specifications, which use LTE as the foundational technology, were released by 3GPP in 2016. To distinguish it from the V2X technology based on 802.11p, it is commonly called “cellular V2X” (C-V2X). Apart from V2V and V2I direct communication, C-V2X facilitates wide-area communication via a cellular network (V2N).
An announcement made by a European automaker in December 2017 revealed its plans to incorporate V2X technology, utilizing the 802.11p standard, commencing from 2019 [70]. Research and analysis conducted during 2017 [70] and 2018 [71] by the 5G Automotive Association (5GAA), an industry body dedicated to advancing C-V2X technology, suggested the superiority of cellular-based C-V2X technology in direct communication mode over 802.11p in various aspects such as performance, communication range, and reliability. However, these assertions have faced challenges, notably in a whitepaper released by NXP [72], a company actively involved in the development of 802.11p-based V2X technology, which has also been documented in peer-reviewed journals [73].
Karati et al. [74] suggested cryptanalysis a recently suggested AKA protocol that is demonstrated to be more lightweight than the current best practices. They release numerous forgeries while using both traditional and novel methods to decode algebraic systems. They prove through cryptanalysis that various security issues, including replay, vehicle impersonation, session-independent key agreement, inadequate anonymity, and multiple key exposures, can be exploited against the algorithms and characterizations of this protocol. This article also offers suggestions for creating a safe, lightweight V2X authentication system.
Mohamed and Helmy [75] addressed the integration of IEEE security standards and AUTOSAR implementation of V2X security requirements, as well as the application of integrity and authentication to messages between two nodes. As well as how the AUTOSAR platform implements the CAR-2-CAR consortium’s requirements.
To improve road safety, efficiency, and connectivity, vehicles in VANET communicate with roadside infrastructure (V2I), with each other (V2V), and possibly with other entities (V2X). Real-time safety alerts, cooperative driving techniques, and optimized traffic flow are all made possible by V2V communication. V2I communication allows cars to get traffic updates, alerts, and details about services that are close by. V2X stands for the more expansive idea of cars interacting with other cars, bikes, pedestrians, and weather stations, among other things, to enhance the information that drivers have access to and create a safer and more intelligent transportation network. Table 2 shows the analysis of V2V, V2I, and V2X in this each cell in the table indicates whether a particular paper covers a specific communication technology.
| Entities | Papers | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 57 | 58 | 59 | 60 | 61 | 62 | 64 | 65 | 66 | 67 | 68 | 69 | 70 | 77 | 78 | |
| Vehicle-to-vehicle (V2V) | √ | √ | √ | √ | √ | √ | × | √ | × | × | × | × | × | √ | √ |
| Vehicle-to-infrastructure (V2I) | × | × | × | × | × | × | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| Vehicle-to-everything (V2X) | × | × | × | × | × | × | × | × | × | × | × | × | × | √ | √ |
The goal of both C-V2X and DSRC is to transform transportation via V2X communication. But their approaches are very different, and they each have unique benefits and drawbacks. Table 3 shows the comparative analysis of DSRC and C-V2X.
| Technology | Communication range | Deployment cost | Data latency | Security | Scalability | Current landscape |
|---|---|---|---|---|---|---|
| Dedicated short-range communication | Up to 1 km (line-of-sight) | Potentially higher | Very low (around 0.4 milliseconds) | Standardized protocols, vulnerable to jamming/spoofing | Limited scalability | Initially considered frontrunner, facing challenges |
| Cellular vehicle-to-everything | Potentially exceeding 1 km (not strictly line-of-sight) | Potentially lower | Slightly higher (around 1 millisecond, improving with 5G) | Leverages cellular network security | Highly scalable | Gaining significant traction |
4.2. Authentication Requirements
To guarantee safe and dependable communication between cars and RSUs, authentication in VANET is essential. In order to stop malicious actors from posing as authorized users and introducing erroneous or misleading information into the network, it allows the ID of communicating entities to be verified.
In VANET, there are two levels of authentication: message level and node level. RSUs and vehicles undergo node-level authentication, while messages are shielded from manipulation through message-level authentication.
4.2.1. Node-Level Authentication
To make sure that only approved cars and RSUs can interact with the network, node-level authentication is essential. By doing this, malicious actors are prevented from posing as trustworthy users and infiltrating the network with inaccurate or misleading data.
4.2.2. Importance of Node-Level Authentication
- •
Prevents Impersonation: It guards against ID theft and unauthorized access, protecting against malignant entities disguising themselves as authorized cars or RSUs.
- •
Ensures Message Integrity: By ensuring that messages come from reliable sources, it stops tampered or false messages from proliferating over the network.
- •
Prevents Unauthorized Access: By limiting network participation to approved cars and RSUs, it stops illegal parties from listening in on conversations, interfering with legitimate ones, or introducing malicious data.
- •
Enhances Accountability: By establishing accountability for network actions, it makes it possible to track down and identify misbehaving entities.
4.2.3. Challenges of Node-Level Authentication
- •
Dynamic Network: Because vehicles are continually entering and leaving VANET, it is challenging to maintain consistent authentication across entities.
- •
Resource Constraints: Due to their limited computational power and battery life, vehicles and RSUs cannot implement sophisticated authentication mechanisms.
- •
Privacy Concerns: It is crucial to strike a balance between user privacy and robust authentication to stop illegal tracking or profiling of specific people.
- •
Interoperability: To guarantee smooth communication, authentication schemes should work with both current and upcoming VANET standards and protocols.
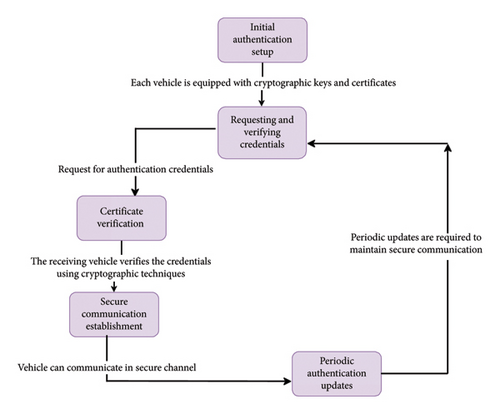
4.2.4. Steps Involved in Node-Level Authentication
- •
Initial Authentication Setup: Before joining the network, each car is outfitted with cryptographic keys and certificates (if PKI is being used).
- •
Requesting and Verifying Credentials: Authentication credentials, such as digital certificates, are requested by a vehicle seeking to establish communication with another.
- •
Certificate Verification: The receiving vehicle uses cryptographic techniques to verify the sender’s certificate’s authenticity or credentials, confirming they come from a reliable source and are not revoked or expired.
- •
Secure Communication Establishment: After a successful verification, the cars can create a secure communication channel and encrypt data to guarantee integrity and confidentiality.
- •
Periodic Authentication Updates: The credentials for validation may need to be updated regularly as cars move and communicate to ensure secure communication.
Figure 7 shows the steps involved in node-level authentication.
4.2.5. Message-Level Authentication
In VANET, message-level authentication is a vital security feature that guarantees the legitimacy and accuracy of messages sent back and forth. By confirming that the messages have not been altered or tampered with while in transit, it guards against malevolent parties introducing inaccurate or deceptive data into the network.
4.2.6. Importance of Message-Level Authentication
- •
Prevents Message Tampering: By shielding messages from unwanted changes, it guarantees that the message sent and received are identical.
- •
Protects Against False Information: It guarantees the accuracy of traffic data and alerts by preventing malicious entities from introducing erroneous or misleading data into the network.
- •
Enhances Message Trustworthiness: It improves message dependability so that cars and RSUs can make judgments based on real information.
- •
Prevents Malicious Attacks: It protects against attacks that aim to disrupt or manipulate traffic information, maintaining the safety and efficiency of the network.
4.2.7. Challenges of Message-Level Authentication
- •
Real-Time Requirements: Because VANET require real-time communication, the computational overhead of complex authentication mechanisms renders them impracticable.
- •
Resource Constraints: Authentication schemes can be limited in complexity by the limited computational and battery power of vehicles and RSUs.
- •
Dynamic Network: Consistent message authentication is challenging to maintain in dynamic VANET where vehicles are constantly entering and leaving the network.
- •
Privacy Concerns: To stop illegal tracking or personal profiling, it is essential to strike a balance between robust authentication and user privacy.
In VANET, message-level authentication is a vital security feature that guarantees the authenticity and integrity of messages sent back and forth. By confirming that messages have not been altered or tampered while in transit, it guards against malevolent parties introducing inaccurate or deceptive data into the network. Figure 8 shows that the message-level authentication.
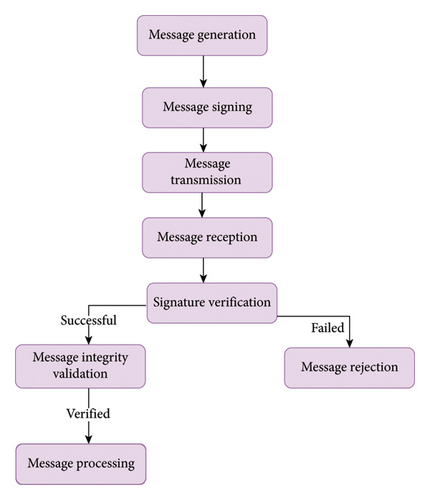
-
Step 1: Message Generation: The sender composes a message with the required details, like vehicle status, safety alerts, and traffic updates.
-
Step 2: Message Signing: Digital signatures or message authentication codes (MACs) are used by the sender to sign the communication.
-
Step 3: Message Transmission: When another vehicle or RSU comes within communication range, the sender broadcasts the signed message to them.
-
Step 4: Message Reception: The broadcast message is sent to receiving entities along with the digital signature or MAC.
-
Step 5: Signature Verification: Using the public key of the sender or a shared secret key, the recipient confirms the signature or MAC.
-
Step 6: Message Integrity Validation: The integrity and authenticity of the message are verified if the signature or MAC verification is successful.
-
Step 7: Message Rejection: A failed signature or MAC verification indicates tampering or unauthorized modification, and the message is rejected.
-
Step 8: Message Processing: The recipient can process the message and make use of the information it contains after the message’s integrity has been confirmed.
4.3. Privacy-Preserving Schemes in VANET
In VANET, protecting privacy is essential to protecting user data and anonymity, as well as facilitating safe and effective communication between vehicles and RSUs. Effective privacy-preserving mechanisms are becoming more and more important as VANET become more common.
-
4.3.1. Simple or general privacy preserving
-
4.3.2. Conditional privacy preserving
4.3.1. Simple or General Privacy Preserving
In VANET, privacy-preserving schemes are intended to guarantee data authentication and protect vehicle owners’ privacy [115]. These protocols are necessary for safe communication between infrastructure and automobiles. Conditional privacy preservation (CPP) and a mechanism for validating authenticated transmissions are essential components of an ideal privacy-preserving authentication (PPA) scheme in VANET [114].
The mutual authentication scheme proposed in [113] is an example of a privacy-preserving scheme for group communication in VANET. Mutual authentication between vehicles in a group is ensured by the scheme, which protects group members’ privacy without requiring the TA to be actively involved. One more illustration can be found in [115]. It provides a PPA scheme for VANET that is both effective and physically secure. An attacker who manages to get their hands on the private key kept in OBUs will be unable to deduce the true ID and key of the vehicles from their communications thanks to the scheme’s support for CPP.
A summary of the different privacy-preserving VANET schemes, such as VSPN, SPACF, 2-Flip, EAAP, NECPPA, and PSPPS, is given in [116]. A thorough analysis of these schemes is presented in the study, along with an emphasis on their effectiveness and privacy-preserving qualities.
In conclusion, VANET’s privacy-preserving schemes are made to protect vehicle owners’ privacy while guaranteeing safe communication between cars and infrastructure. Data authentication and CPP must be included in these schemes. In the literature, a number of schemes have been put forth; their levels of efficiency and privacy preservation vary.
4.3.2. Conditional Privacy Preserving
In VANET, CPP seeks to achieve a compromise between safeguarding vehicle privacy and permitting efficient communication for safety and traffic control applications. CPP schemes add an extra degree of control by enabling vehicles to selectively reveal their identities under predetermined circumstances, whereas traditional privacy-preserving schemes prioritize anonymity and unlinkability to protect vehicle identities.
Cryptographic methods are usually used in CPP schemes to accomplish this kind of selective privacy disclosure. For example, cars could have ID cards or other tokens that can be used to authenticate a driver when needed, like in an emergency or by law enforcement. These credentials are conditionally used, meaning that vehicle identities are never revealed during regular communication unless they are absolutely necessary.
The comparative analysis of simple privacy-preserving and conditional-preserving schemes is shown in Table 4.
| Feature | Simple/general privacy-preserving | Conditional privacy preserving |
|---|---|---|
| Definition | General techniques to protect user data and privacy without considering specific conditions or contexts | Techniques that protect user data and privacy while considering specific conditions, contexts, or attributes |
| Privacy focus | Anonymity, often coarse-grained; applies uniformly across all data | Granular control, fine-grained; applies selectively based on conditions or contexts |
| Flexibility | Limited, one-size-fits-all approach | More flexible; tailored to specific requirements or conditions |
| Implementation complexity | Relatively simpler to implement and manage | More complex due to the need to define and manage conditions |
| Performance overhead | Typically lower due to simpler mechanisms | Potentially higher due to the complexity of managing conditions |
| Scalability | Generally more scalable due to simplicity | Scalability can be challenging due to condition management |
| Suitability examples | ∗ User anonymity is paramount (e.g., online browsing) | ∗ Location data for emergency services while keeping identity hidden. ∗ Revealing purchase history for personalized discounts while protecting sensitive financial details |
| Advantages | ∗ Easy to implement and manage. ∗ Lower computational overhead | ∗ More nuanced privacy control. ∗ Can be more secure |
| Disadvantages | ∗ Less flexibility. ∗ May reveal unnecessary information | ∗ More complex to implement and manage. ∗ May require additional computational resources |
With this comparative analysis, we cannot say which scheme is better it purely depends on the scenario and specific needs. In conclusion, applications with complex, changing, or context-specific privacy needs are typically better suited for conditional privacy-preserving techniques. In contrast, applications with simple, uniform privacy protection requirements are better suited for simple/general privacy-preserving techniques. Although conditional privacy-preserving techniques have a higher risk of misconfiguration and are more complex, they may provide stronger and more flexible security for sensitive data. Simple/general privacy-preserving techniques offer dependable, more manageable security, but they might not be flexible enough to properly handle particular, subtle threats. The optimal option is determined by the particular security needs, threat landscape, and implementation and management resource availability.
There are various important factors to take into account when implementing CPP in VANET.
4.3.3. Requirements for Privacy
The plan must guard vehicle privacy successfully and stop unwanted ID disclosure.
4.3.4. Traceability
The plan should make it possible for cars to be tracked down in certain situations, like when there are accidents or possible infractions.
4.3.5. Efficiency
The plan should not add a lot of overhead that reduces the effectiveness of VANET communication.
4.3.6. Revocation Procedure
A procedure for withdrawing hacked credentials or tokens should be in place to avoid abuse.
4.3.7. Authentication and Integrity
To guard against intrusions and guarantee the authenticity of communications, robust authentication and integrity procedures must be used.
4.3.8. Scalability
The plan needs to be scalable to support a huge number of cars and different network circumstances.
CPP schemes offer a more sophisticated method of protecting privacy in VANET by striking a balance between the requirement for anonymity and the capacity to track down vehicles when needed. CPP schemes are expected to become more crucial as VANET develop and privacy concerns grow in order to maintain safe and private communication between moving vehicles.
4.4. Overhead
In VANET, “overhead” refers to the extra processing power and network resources used by security mechanisms to guarantee the security and integrity of communications, such as message signing, authentication, and encryption. In addition to adding extra overhead that may affect network performance and resource usage, these mechanisms are necessary to safeguard VANET against hostile attacks and preserve data confidentiality.
- •
Computation Overhead: This kind of overhead is the extra computing power needed to carry out security protocol operations like the creation and verification of signatures as well as encryption and decryption. Message delivery delays and network latency can be caused by processing overhead, particularly in vehicles with limited resources and RSUs.
- •
Communication Overhead: This kind of overhead is the extra bandwidth that security mechanisms use on the network to send encrypted messages, digital signatures, and authentication credentials. Increased energy consumption, decreased network throughput, and congestion can all result from communication overhead.
VANET security mechanisms have an inherent overhead component. Reduced overhead is necessary to guarantee network performance, resource utilization, and energy efficiency, even though protecting VANET from malicious attacks and maintaining data confidentiality are paramount. Secure and dependable communication between vehicles and RSUs can be ensured by VANET by carefully choosing lightweight security mechanisms, putting adaptive protocols into place, and using effective data encoding and scheduling techniques.
5. Taxonomy of Authentication Schemes in VANET
The most crucial requirement for security is authentication. As the first line of defense, it ensures that the message was sent by an authorized party and thwarts masquerading attacks. The taxonomy of authentication schemes is displayed in Figure 9.
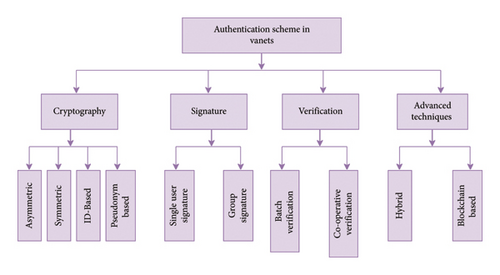
5.1. Cryptography-Based Authentication Schemes
In the realm of authentication schemes rooted in cryptography, there exist three primary types: asymmetric, involving two keys—a first key for encryption and a second for decryption; symmetric, relying on a single key for both encryption and decryption purposes; and ID-based, resembling asymmetric schemes but distinct in the generation of the public key, which is derived from the user’s ID information.
A framework known as PKI binds public keys to user identities. The binding is completed by certificate issuance and registration by the CA. The person who registers is registering authority (RA): This body guarantees the authenticity of the asking party. The secret key, sometimes known as the private key, is utilized for signing, and verification is done using the public key. Figure 10 illustrates how a PKI-based system functions.

Elliptic Curve Digital Signature Algorithm (ECDSA), a variant of the digital signature algorithm, incorporates ECC. Its primary function involves encrypting messages, thereby restricting data access solely to authorized users, significantly bolstering security measures. The digital realm offers a range of diverse digital signature algorithms to explore.
Examples of asymmetric cryptography schemes are PKI and ECDSA. While privacy preservation is a crucial requirement that should not be overlooked, authentication is an essential prerequisite for secure communication in VANET. The ability to reveal personal information only to specific individuals or organizations is known as privacy.
The user’s private information, such as the owner’s ID, address, and vehicle location, should not be disclosed to any other party or vehicle during the authentication process other than the appropriate authority, such as a CA or TA. Thus, privacy preservation must be guaranteed by the authentication scheme. Therefore, privacy-preserving requirements like location tracking, unlinkability, and unobservability need to be protected.
When someone is anonymous, their true ID is not disclosed to others. Large anonymous certificates, approximately 43,800, and corresponding private keys are preloaded into PKI authentication schemes. Anonymous authentication was proposed by Raya and Hubaux [35], where privacy was maintained by using anonymous public keys instead of a single public key. This prevents the receiver from knowing who owns the keys. The list is growing because malicious nodes have a high revocation rate.
Challenges identified in VANET, as highlighted by the authors in [76, 77], encompass substantial storage demands, latency concerns in verifying revocation lists, and the timely distribution of CRLs.
In their work (Calandriello et al. [78]), the suggestion entails the creation of pseudonyms in real time, employing a combination of self-certification and a fundamental pseudonym strategy alongside group signature. This approach aims to tackle the storage constraints and latency issues outlined in [35].
If the ID is anonymous and the node is not malicious, this is known as conditional privacy. A method for achieving conditional privacy was suggested by Rajput et al. [79]. The approach involved assigning two tiers of pseudonyms, namely, foundational and short-term pseudonyms, to individual vehicles.
By using a digital signature, VANET security can be improved and the message’s authenticity, integrity, and nonrepudiation can be guaranteed. IEEE 1609.2 recommends ECDSA schemes for message verification [80]. Compared to authentication schemes that use the Rivest–Shamir–Adleman (RSA) algorithm, ECDSA produces less computational overhead. Investigators [81–83] have talked about ECDSA.
Symmetric key cryptography, also known as private key cryptography, relies on a single secret key for both encryption and decryption purposes. Compared to asymmetric cryptography schemes, it is faster to execute and easier to design because the sender and the recipient share the same secret key.
The idea of a symmetric random key set technique has been employed by Xi et al. [84] to guarantee privacy and reduce OBU overhead. Nevertheless, since both the sender and the recipient use the same secret key for authentication, symmetric cryptography schemes cannot ensure nonrepudiation.
Symmetric key cryptography encompasses authentication schemes like hash function, timed efficient stream loss-tolerant authentication (TESLA), and MAC.
The message and secret key are entered into the MAC algorithm, which creates the tag and adds it before sending. The same secret key is utilized at the receiver’s end to compute the label. The authenticity of a message is only established when both tags are equivalent. Message integrity is guaranteed by the MAC algorithm and genuineness.
Lin et al. [85] introduced the timed, efficient, and secure vehicular communications (TSVC) scheme in their work. For packet authentication, each packet has a short MAC tag appended to it. According to simulation results, under high-traffic conditions, TSVC outperforms other PKI-based schemes with regard to packet loss ratio.
A CPP scheme based on a MAC was proposed by the author in [86]. In this, message generation and authentication are accomplished through verifiable secret sharing, which allows a car to obtain its group key. It requires less computation and communication overhead and satisfies the fundamental security and privacy requirements.
The verification of message integrity involves employing a hash function. This function appends a message’s hash value or digests to the message itself before transmission, ensuring its integrity. If an attacker manipulates the message during transit, any alterations will result in a distinct hash value, prompting the recipient to reject the modified message.
In [87], authors have put forth an authentication scheme that preserves conditional privacy by utilizing the Chinese remainder theorem (CRT). To cut down on computational overhead, they have done away with storing the master key inside the tamper-proof device (TPD). Because the scheme does not employ binary pairing or operations like map to point during the authentication process, it verifies signatures more quickly even when the number of signatures increases. The system can withstand frequent attacks and provide improved performance with reduced computational and communication overhead.
Authors in [88] used the Trust-Extended Authentication Mechanism (TEAM), a decentralized lightweight authentication scheme, for V2V communication. To determine the safe secret key set, they employed a hash chain. It complies with security requirements, including anonymity.
The TESLA makes use of hash chains in addition to precise MAC. With broadcast or multicast data streams, TESLA enables the recipients to verify the legitimacy and integrity of the source for every packet [89].
Bao et al. [90] introduced a lightweight authentication system that combines TESLA and Bloom Filters in their work. This system aims to safeguard against active attacks while ensuring privacy preservation.
ID-based cryptography (IBC) generates the public key using ID information, like email addresses. Since a certificate is not needed for message authentication, there are fewer messages overhead. Additionally, because of the management and lack of maintenance for CRL, it enhances VANET communication.
Authors in [91] have presented a decentralized privacy preservation scheme that makes use of hash-based message authentication codes (HMAC) and asymmetric identities. The outcome of the simulation indicates that the proposed scheme is resilient, lightweight, and able to withstand typical attacks. Nevertheless, conditional privacy, location tracking, and unobservability are not guaranteed by the scheme.
In [92], the authors detail a privacy-focused authentication framework comprising a single hash function, secret key, pseudo-ID, and segmented into four distinct stages. Validation of its security and privacy adherence was conducted using the ProVerif tool. Leveraging only hash and exclusive-OR operations, the scheme stands out for its resilience, lightweight nature, and minimal computational and communication burdens. Furthermore, the authors discuss potential enhancements for this framework concerning its applicability within 5G and edge computing scenarios in VANET.
Azees and Deboarh [93] employed tracking mechanisms with conditional privacy to withdraw the automobile in the event of any misbehavior and anonymous authentication to prevent malicious vehicles from entering the VANET. Bilinear pairing was the method they employed. Five distinct steps are involved in achieving anonymous authentication: (1) key generation and registration, (2) generation of anonymous certificate, (3) generation of signature, (4) verification, and (5) conditional tracking. The certificate’s computational cost, RSU serving capacity, and signature verification procedure have all been examined in terms of performance analysis. With location tracking, it offers the lowest cost for verifying certificates and signatures. The system can fend off frequent attacks and guarantee privacy protection.
5.2. Signature-Based Authentication Schemes
Authentication in cryptographic schemes such as asymmetric, symmetric, and ID-based ones often relies on single-user signatures. However, this approach introduces complexities like key management, frequent alterations to public and private key pairs, as well as computational and communication overhead. To address these challenges, researchers have proposed group signature-based authentication systems. With a single modification, group signature authentication demonstrates a resemblance to the functionality of a public and private key pair. An essential feature of group signature is its ability to offer anonymous authentication to safeguard privacy, as discussed in [94]. In this system, any member within the group can sign the safety message using its private key. The recipient validates the sender by verifying the signature with the group public key, thereby revealing only the ID of the group manager.
On the basis of group communication in VANET, the authors in [95] have employed a dual authentication scheme. The plan relies on each user’s fingerprint and the vehicle’s secret key.
To reduce the computation in this case, CRT-based key management is employed. Additionally, there is a minimal amount of information needed to update the group key in the event that a group is joined. The plan has less overhead in terms of computation and communication and can withstand common attacks, but it cannot withstand conditional privacy or location tracking.
The anonymous authentication scheme (AAAS) in VANET has been implemented by the authors in [96] using regional trust authority. To ensure anonymity and conditional privacy, they have employed group signatures.
To achieve conditional privacy, Islam et al. [97] used group key generation protocols and password-based systems. Because the protocol does not use an elliptical curve or bilinear pairing, it has a lower computational overhead.
5.3. Verification-Based Authentication Schemes
A vehicle using VANET communication can send safety messages, which need to be confirmed by the RSU or other nearby vehicles in less than 300 milliseconds. In high-traffic areas, the quantity of messages increases and begins to build up for validation. The messages will be invalidated or discarded if they are not verified within the allotted time. It might also result in an accident or other dire circumstances. Messages can be verified cooperatively or in batches to address the issue of timely message verification with less delay, communication overhead, and computational overhead. The types of authentication algorithms that can be designed are as follows: (1) authentication schemes based on batch verification and (2) authentication schemes based on cooperative verification.
A batch-aided verification scheme has been proposed by Wu et al. [98] to validate the message more quickly and with less delay. They have enlisted the help of RSU and a few terminals to work together on the message verification task in this scheme. Additionally, the scheme scales 10 times faster than schemes in which the only message verifier is RSU.
To guarantee security and conditional privacy, authors in [99] have suggested an ID-based batch verification scheme. When compared to schemes that employ the binary pairing technique, the scheme performs admirably.
In VANET, every vehicle undertakes the verification of safety messages upon reception—a departure from the traditional system where this redundant verification process often leads to delays, particularly during high message volume scenarios. Employing cooperative message authentication stands out as a viable solution to mitigate this issue.
An effective cooperative messaging authentication (ECMA) scheme has been proposed by Lin and Li [100] to lessen the need for duplicate authentication for each vehicle within the range of the same message. Selfish vehicles utilize free-riding attacks. The strategy involves implementing an evidence token aimed at assessing the vehicle’s authentication process contribution independently, eliminating the reliance on TA assistance to thwart free-riding attacks. Upon a vehicle passing the RSU, it acquires an evidence token reflective of its past contributions.
A few key concerns must be resolved to have an ECMA. One of the serious issues with the implementation of an ECMA is handling potential failures. Failures are the most critical problems, and causations arise from a variety of sources, including system crashes, network errors, or even malicious attacks. To diminish these failures, you must have a solid design in place which will be able to detect and recover from such failed conditions soon.
Another key issue is the design of participation incentives, which is essential for motivating users to take part in the cooperative message authentication in an interface. It can be achieved by designing some mechanisms to rewarding, including encouraging rewards, reputation system, and other benefits, the users for contributing messages in an interface system.
Privacy is also a major concern in ECMA since it requires gathering and processing personal data, thus, in this context, privacy regulations that should be considered that includes European General Data Protection Regulation (GDPR), and California Consumer Privacy Act (CCPA) for instance to obtain the user’s consents, apply data protection, and ensure the transparency of data processing.
Furthermore, other eminent issues need to be discussed in the context of ECMA, i.e., security, scalability, usability, and interoperability in order to develop a cooperative messaging authentication system that is secure, scalable, easy to use, and interoperable.
The authors of [101] have used a trustworthy cooperative authentication system. To prevent synchronization issues between cooperative and non-cooperative vehicles, they have employed success reports in this. According to the simulation results, even at 200 vehicles per km, there will be no message loss.
Tables 5 and 6 provide a comparison of schemes (A, B, and C) covered in Section 5 considering the criteria for (1) security, (2) privacy, and (3) scalability.
| Criteria | Papers | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 43 | 81 | 82 | 85 | 87 | 88 | 89 | 90 | 91 | 93 | 94 | 95 | 96 | 98 | 99 | 101 | 102 | 103 | 104 | |
| Entity validation | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| Message validation | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| Trackable | × | × | × | × | × | × | × | √ | √ | × | √ | √ | √ | √ | √ | × | √ | √ | √ |
| Nonrepudiation | × | × | × | √ | × | × | × | √ | × | × | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| Sybil attack | × | × | × | × | × | × | × | √ | × | × | √ | √ | √ | √ | √ | × | × | √ | √ |
| Tampering attack | × | × | × | × | × | × | × | √ | √ | × | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| DOS | × | × | × | × | × | × | × | × | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| Spoofing attack | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | × | √ | √ | √ |
| ID revelation | √ | √ | √ | × | × | × | × | √ | √ | × | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| Replay attack | × | √ | √ | × | × | × | × | √ | √ | × | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| Location track | × | × | × | × | × | × | × | √ | √ | × | × | √ | √ | × | √ | × | √ | × | √ |
| Criteria | Papers | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 43 | 81 | 82 | 85 | 87 | 88 | 89 | 90 | 91 | 93 | 94 | 95 | 96 | 98 | 99 | 101 | 102 | 103 | 104 | |
| Privacy | √ | √ | √ | × | × | √ | √ | √ | √ | × | √ | √ | √ | √ | √ | √ | √ | √ | √ |
| Less communication | × | × | × | × | × | × | √ | √ | × | × | √ | √ | √ | √ | × | × | × | × | × |
| Less computation | × | √ | × | √ | √ | √ | √ | √ | × | × | √ | √ | √ | √ | × | × | × | √ | √ |
| Unlinkability | × | × | × | × | × | × | × | √ | √ | × | √ | √ | √ | √ | √ | × | √ | √ | × |
| Unobservability | × | × | × | × | × | × | × | √ | × | × | × | × | √ | × | √ | × | √ | √ | × |
| Conditional privacy | × | × | √ | × | × | × | √ | √ | × | × | × | × | × | × | √ | × | √ | × | × |
| Scalability | × | × | × | × | × | × | × | √ | × | × | √ | √ | × | √ | √ | √ | √ | √ | √ |
5.4. Advanced Authentication Schemes in VANET
VANET are built to handle the special difficulties of securing communication in constantly changing and limited resources vehicular environments. This is why advanced authentication schemes are implemented in VANET. With the least amount of overhead and flexibility to accommodate the dynamic nature of VANET, these schemes seek to offer robust authentication, privacy protection, and efficiency. The types of authentication algorithms is designed as (i) hybrid scheme and (ii) Blockchain-based authentication.
An authentication scheme based on the hybrid proxy (HPBS) was suggested by Liu, Wang, and Gu [102]. Three issues in the VANET environment were resolved in HPBS by introducing the idea of agent vehicles and combining ID-based and PKI-based hybrid authentication: RSUs can be made more efficient in terms of message authentication; their computational load can be decreased; and user privacy can be safeguarded.
Tangade, Manvi, and Lorenz [103] suggested a hybrid cryptography (TMHC)–based trust management system to further secure VANET. Since secure communications and the establishment of trust between vehicles depend on authentication, the suggested TMHC incorporates hybrid cryptography–based authentication for an effective and reliable trust management system. HMAC and asymmetric ID-based digital signature (ID-based) are two components of hybrid cryptography.
Wang et al. introduced an innovative group signature-based algorithm in their work [104], aiming for mutual authentication within V2V communication within a hybrid D2D message authentication (HDMA) scheme designed for 5G-enabled VANET. Furthermore, to reduce the computational load of the modular exponentiation operation, they incorporated a precomputed lookup table.
Addressing the security prerequisites of diverse V2I communications, Ali and colleagues introduced a hybrid signcryption protocol based on elliptic curve cryptosystems (ECCHSC) in their work [105]. This protocol offers a single-step implementation and fulfills essential security requisites, encompassing message confidentiality, integrity, nonrepudiation, and ID anonymity.
Blockchain technology has been used by Ma et al. [106] to propose a decentralized key management protocol for VANET that automatically registers, updates, and revokes the user’s public key. They have suggested using bivariate polynomials for both key agreement and mutual authentication. The plan can counteract denial-of-service attacks, collusion attacks, internal attacks, and public key tampering attacks. In addition, the protocol operates efficiently with reduced overhead in terms of computation, storage, and communication. The plan eliminates the reliance on TA, as with a PKI system, while also guaranteeing the anonymity needed to protect privacy.
A PPA scheme for VANET has been proposed by Lu et al. [107]. Revocation list-free distributed authentication schemes are offered by the Merkel Patricia tree (MPT). Multiple certificates could be used by vehicles to obtain conditional certification. Every entity’s performance has been examined using the Hyperledger Fabric (HLF) platform. Based on the simulation results, which show that every vehicle can authenticate in less than 1 millisecond, the scheme meets the real-time time constraint. Also, compared to the previously used schemes, storage and processing times have been significantly decreased.
Lin et al. introduced an efficient certificate management scheme [108] employing the ECDSA rooted in the Ethereum public Blockchain to ensure secure communication among vehicles. This innovative system minimizes the need for vehicles to store private keys, subsequently reducing verification costs and time. The scheme underwent verification on Rinkeby, the Ethereum test network, and simulation was conducted using NS-2, with VanetMobiSim chosen for its efficacy. Further exploration is warranted to ascertain how this approach aligns with the prerequisites for conditional privacy and security in VANET deployment.
In [109], authors present a secure payment scheme based on Blockchain technology for VANET, taking into account two situations: (1) management of park toll systems and (2) electronic toll collection.
The payment plan, which consists of two transactions: (i) V-R and (ii) V-Rs, is reliable and efficient. In this scenario, the smart contract handles all transactions automatically, and only RSU participates in the consensus. Additionally, it can lessen security and privacy requirements.
A consortium Blockchain-based unlinkability authentication scheme was employed by Liu et al. [110]. The distributed nature of the service manager (SM) creates a distributed database that facilitates data sharing. Every vehicle starts the authentication process and creates a unique pseudonym. To confirm the legitimacy of the car, SM consults local data. Stronger anonymity and unlinkability can be ensured by this scheme, but cooperation among SMs makes it vulnerable to collusion attacks and linkability.
Bi et al. [111] suggested a productive Blockchain-based, anonymous, certificate-less authentication system for VANET. In order to lower the computational overhead in VANET, they first suggest a novel signature scheme devoid of bilinear pairing. Second, they use Blockchain technology to enable the sharing of trustworthy information. Third, they offer privacy-preserving by using anonymous keys and allow vehicle ID tracing in case of malicious activity. Table 7 gives a comparative analysis of the schemes which were discussed so far in the article.
| Scheme | Description | Type | Strengths | Limitations |
|---|---|---|---|---|
| Asymmetric | Uses a public key for encryption and a private key for decryption | Cryptography | High security, scalability, widely used, suitable for public key infrastructure | Computationally intensive, requires key management |
| Symmetric | Uses the same key for encryption and decryption | Cryptography | Faster than asymmetric, suitable for real-time applications, simpler key management, lightweight | Less secure if key is compromised, key distribution is challenging |
| ID-based | Uses an identity (such as an email address) as the public key | Cryptography | Simplifies key management, eliminates need for public key infrastructure | Key escrow problem, potential privacy concerns |
| Pseudonym-based | Uses temporary identities (pseudonyms) to improve privacy | Cryptography | Enhances privacy, provides unlinkability | Requires frequent pseudonym changes, increased overhead |
| Single-user signature | A user signs a message with its private key | Signature | Simplicity, lower computational cost | Does not support group communication, single point of failure |
| Group signature | A group member can anonymously sign a message on behalf of the group | Signature | Anonymity within the group, supports group communication | Complex key management, computationally intensive |
| Batch verification | Verifies multiple signatures at once | Verification | Efficient for verifying multiple messages simultaneously, reduces computational load | Potential security risks if one message in the batch is compromised |
| Cooperative verification | Enables multiple users to verify a signature | Verification | Enhances security through collective verification, reduces individual computational load | Requires coordination among multiple nodes, communication overhead |
| Hybrid | Combines different cryptographic techniques | Advanced | Combines strengths of multiple schemes, flexible and adaptable to different scenarios | Complexity in implementation, potential for combined vulnerabilities |
| Blockchain-based | Uses blockchain to secure communication and store cryptographic keys | Advanced | High security, immutability, decentralization, transparent auditing | High computational and storage costs, latency issues in real-time applications |
The integration of Edge computing, Fog computing, and Cloud computing forebodes a lot of improvement in VANET. Of these techniques, some salient features are being highlighted here that make VANET better.
5.4.1. Edge Computing
It is data processing that takes place close to its point of origin, the data get analyzed and processed near their origin, hence decreasing latency. There is a faster response time and lower data transfer latency. A significant role of edge computing in time-sensitive VANET applications: emergency response and traffic update [130, 131]. This way, edge computing allows the management for connection and monitoring of a huge number of devices and applications, which makes it scalable. This can be used in VANET when there is a need to send vast amounts of data back and forth to multiple terminals, which is then processed speedily [130].
5.4.2. Fog Computing
Fog computing created an intermediate, very significant dimension between the edge and the cloud. This reduction in latency and improvement in overall system performance occurs because the edge processes the data and transfers it to the cloud [131].
Fog computing is resource-intensive in computational methods and may divide computation among a number of nodes; this happens more in VANET, where efficient communication is most needed [131].
5.4.3. Cloud Computing
Cloud computing is a centralized storage that enables the storage and processing power of terabytes of data. I think it will be useful in VANET, where a lot of data will be stored and analyzed, including daily traffic flow and real-time road condition monitoring [132]. These resources are modified to ensure that the network receives more traffic and data when needed by virtual applications [132].
Integrating the mentioned techniques with VANET will make the following possible.
5.4.4. Real-Time Information
VANET integrated with edge, fog, and cloud computing provide at the right time and accurate real-time information at every moment, which is quite necessary for the prevention of road accidents and efficient management of traffic [130].
5.4.5. Improved Communication
It is through the integration of these technologies in VANET that it makes communication effortless, faster, and reliable for transferring data between vehicles and infrastructure [132].
It can be stated that VANET perform better using the advantages of edge, fog, and cloud computing to cut down latency and increase scalability.
Software-defined network (SDN) is one of the most attractive solutions for increasing performance and efficiency in VANET.
5.4.6. Advantages of SDN in VANET
Improved Traffic Efficiency: The SDN controllers can modify the network resources in real time and optimize data flows with a changing pattern of vehicular traffic. An example of this could be rerouting vehicles to the other route in order to avoid congestion by the SDN controller [134, 135].
Improved Safety: Integrating SDN into VANET can improve safety to a great extent through the rapid and reliable dissemination of information related to any critical event. For example, in the case of a hazard being detected by any vehicle, that vehicle will be able to immediately propagate a warning to the other vehicles in its vicinity through the SDN-controlled VANET, avoiding the potentials for an accident [133, 136].
Improved Security: SDN provides a single point of control for security management and various authentication mechanisms that reinforce the protection of the VANET against cyber attacks. Besides, it allows for flexible and fast implementation of security policies [134, 136].
5.4.7. Improved Scalability
With its central mechanism for control, SDN is well-placed to effectively manage the highly dynamic nature of VANET, in which vehicles leave and join the network almost continuously [134, 136].
5.4.8. Challenges in SDN for VANET
Standardization: There is no standard for SDN in VANET, and it could act as a barrier to the generalized implementation of this technology [134, 136].
5.4.9. Privacy
As SDN is centralized in nature, there are several concerns regarding data privacy; hence, strict measures shall be taken to protect private data or classified information [134, 136].
5.4.10. Dynamic Topology
With respect to the network topology of VANET, it is highly dynamic; because of this, it is difficult for the SDN controllers to capture the correct state of the network [135, 136].
5.4.11. Limited Resources
The processing power and storage of vehicles are limited; thus, this is another constraint in implementing SDN in VANET [136].
As such, SDN provides several benefits for VANET in terms of improving traffic efficiency, safety, security, and scalability. Some of the key issues to be addressed to establish the successful integration of SDN with VANET are standardization, privacy concerns, dynamic topology, and limited resources.
5.4.12. Lightweight Cryptography in VANET
Lightweight cryptography is one important technique for securing communication in VANET. VANET require efficient and low-resource cryptographic algorithms so that V2V and V2I communications can be strongly protected.
Researchers proposed lightweight cryptography algorithms for the security of VANET communication. All these algorithms are designed with the features of low computational and memory requirements, making them fit for the resource-constrained edge devices available in vehicles [137, 138].
One of the lightweight cryptographic algorithms over VANET is referred to as LWC-DFFF; Dragonfly Firefly optimization algorithm drives it to achieve high throughput and low power consumption [137].
The lightweight cryptography in VANET is proposed to provide security features like authentication, confidentiality, integrity, and nonrepudiation, protecting against impersonation attacks, stolen ID attacks, eavesdropping attacks, and message tampering attacks [138–141].
Lightweight cryptography algorithms have been previously analyzed with their hardware implementations for proving high throughput and low power consumption attributes in edge devices within VANET [138]. Lightweight cryptography is an important technique for securing VANET communications, as it provides efficient schemes of encryption and authentication mechanisms concerning the resource constraints of vehicular systems.
5.5. 5G and 6G Networks in VANET
Research on the integration of 6G and 5G networks in VANET is still ongoing. Research has been done to address the design and implementation issues that the emergence of 5G networks presents for VANET security [117]. The expectations for 6G networks are that they will overcome the shortcomings of 5G and offer massive connections, excellent dependability, and extremely low latency. As a result, they will be a major contributor to the advancement of the ITS and the concept of the Smart City [118]. The IoV is anticipated to have a high degree of security and privacy thanks to the incorporation of cutting-edge technologies such as edge computing, Blockchain, artificial intelligence (AI), network automation, slicing, terahertz links, visible light communications, backscatter communications, physical layer authentication, and cell-free massive multiple-input multiple-output (MIMO) [118]. Still, there are unresolved issues with VANET, including the absence of international standards and the requirement to address inadequate system reliability, low intelligence levels, and weak network security [119].
Research and interest in the integration of 5G and 6G networks in VANET are high. 5G network development has brought up design and implementation concerns for VANET security. Studies have been carried out to examine the security characteristics of 5G networks and how they can be utilized in automobile networks to facilitate a smooth and effective integration [117]. Moreover, it has been emphasized how important automotive applications will be to the architecture of future 6G networks. In autonomous vehicles, 5G communications and related technologies are integrated to enable cooperative perception [120]. SDN control and virtual network functions (VNFs) are two well-known technologies that are essential to 5G-based flexible security. As a result, 5G uses these technologies to enable the integration of VANET and 5G security [117]. Still, there are unresolved issues with VANET, including the absence of international standards and the requirement to address inadequate system reliability, low intelligence levels, and weak network security [121].
To sum up, the amalgamation of 5G and 6G networks within VANET represents a multifaceted and dynamic field of study. While 5G networks have brought new security features that VANET can take advantage of, 6G networks are anticipated to emerge in order to address 5G’s shortcomings and offer the ultra-low latency and high reliability needed for ITSs of the future. In order to successfully integrate 5G and 6G networks in VANET, it will be imperative to address the outstanding challenges in VANET.
5.6. VANET Security and Privacy Applications
VANET allows data exchange and communication between infrastructure and vehicles, which is critical to improving transportation systems. There are several known uses for VANET, including infotainment, safety, and traffic efficiency. The application of VANET into three categories, viz., safety application, nonsafety application, and other applications, is depicted in Table 8.
| Category | Application | Description | Benefits |
|---|---|---|---|
| Safety | Collision avoidance | Vehicles alert one another about potential dangers, enabling quicker responses and possibly preventing collisions | Better driver awareness and fewer accidents |
| Emergency response | Rapid tracking and support in the event of an accident or malfunction | Quicker assistance to those in need and better emergency response times | |
| Cooperative traffic management | Dynamic route optimization using traffic data collected in real time | Decreased traffic and increased effectiveness of travel | |
| Improved driver awareness | Driver decision-making is improved when information about weather, road closures, and other events is shared | Improved safety and awareness of possible risks | |
| Nonsafety | Infotainment | Access to current information on weather, traffic, news, and entertainment options | Better passenger comfort and an enhanced in-vehicle experience |
| E-commerce | Smooth integration for deliveries and purchases made inside the car | Convenience with a lesser need to visit physical establishments | |
| Parking management | Automated payments and parking spot guidance are features of smart parking systems | Less time spent looking for parking and increased productivity | |
| Environmental monitoring | Gathering and exchanging of data on various topics, such as noise pollution and air quality | Increased environmental consciousness, data for developing policies, and a decrease in pollution | |
| Other potential applications | Improved public transportation | Improve traveler experience and streamline routes | Improved service and increased efficiency for users of public transportation |
| Electronic toll collection | Streamlined and effective processes for collecting tolls | Faster travel times and less traffic at toll booths | |
| Vehicle fleet management | Vehicle tracking and management in real time for logistics firms | Enhanced fleet management, increased fuel efficiency, and optimized operations | |
6. Open Challenges in VANET
VANET have the potential to significantly evolution road transportation by facilitating communication between vehicles and roadside infrastructure. This communication can lead to improved traffic efficiency, safety, and infotainment services. Though VANET technology has made great strides, there are still several unresolved issues that prevent it from being widely used and reaching its full potential. Table 9 depicts the open challenges in VANET.
| Challenges | Description |
|---|---|
| Security and privacy | VANET require strong security measures to safeguard data and guarantee privacy because they are susceptible to a variety of attacks, including sybil attacks, tunnelling attacks, and communication link failures [126, 127] |
| Routing protocols | High node mobility, hidden nodes, and evolving network architecture present design challenges for MAC protocols in VANET, necessitating effective routing protocols to guarantee dependable data transmission [128] |
| Spectrum utilization | Using cognitive radios in VANET presents a variety of challenges, including spectrum duration, interference, delay, and security when coordinating between licensed and unlicensed users [128] |
| Dynamic network topology | Due to high mobility of vehicle, the network topology changes quickly, which makes it difficult to identify suspicious vehicles and leaves VANET open to attacks [126] |
| Driver safety | In order to enhance traffic flow, passenger comfort, and driver safety via direct vehicle communication, network strength and security issues must be resolved [126] |
| Wireless communication | Given that VANET connections are wireless, secure communication is essential during data transmission [126] |
| Data collection protocols | Developing effective data-gathering protocols for VANET manifests challenges in real-time data distribution, delay-tolerant protocols, and best-effort protocols for a range of applications [129] |
A significant challenge is the high degree of vehicle mobility, which can lead to frequent topology changes and network disconnections. Safety messages must be delivered with minimal latency and maximum reliability, so this may affect their delivery. To overcome this difficulty, experts have suggested using SDNs, which offer global network knowledge, flexibility, and programmability, and fog computing, which brings cloud computing capabilities closer to the network edge [122].
Another concern is the IEEE 802.11p protocol’s contention-based carrier-sense multiple access with collision avoidance (CSMA/CA) scheme and the DSRC’s constrained transmission range. Delays in the transmission of important messages can be caused by these factors, and in dangerous situations, this can have serious implications. Researchers have suggested using IEEE 802.11p and cellular networks together to create heterogeneous VANET to overcome this problem [123].
In addition, VANET generate a large amount of traffic data, which can be challenging to collect and process using traditional centralized VANET technology. Researchers have suggested using cloud computing to increase VANET capabilities in order to overcome this difficulty. Nonetheless, the current paradigm for cloud computing might not be effective in managing the vast volumes of traffic data produced by intelligent vehicles. To overcome this challenge, academicians have suggested the use of edge cloud computing, also known as fog computing, which provides low latency and high mobility support [124].
Furthermore, a lot of traffic data is generated by VANET, and this traffic data can be difficult to gather and handle with conventional centralized VANET technology. Researchers have suggested using cloud computing to increase VANET capabilities to overcome this difficulty. Nevertheless, the current paradigm for cloud computing might not be effective in managing the vast volumes of traffic data produced by intelligent automobiles. Researchers have suggested using edge cloud computing, sometimes referred to as fog computing, which offers high mobility support and low latency, as a solution to this problem [125].
Conclusively, VANET possess the capability to transform transportation systems; however, their effective implementation and administration necessitate the resolution of multiple outstanding issues. Fog computing, SDN, and heterogeneous networks working together can help overcome these obstacles and offer a more enjoyable, safe, and effective mode of transportation.
7. Conclusion
Focused on addressing VANET authentication challenges and associated attack detection techniques to ensure the security and privacy of VANET. Our analysis involves a comprehensive comparison and discussion of diverse authentication schemes, highlighting their features and antiattack capabilities. Among cryptography-based authentication schemes, initial attention was directed toward a distributed symmetric encryption approach known for its low computational overhead and efficiency. However, its security is compromised due to potential interception during key transmission and issues related to nonrepudiation. While asymmetric encryption offers better security compared to symmetric encryption, it falls short in terms of performance efficiency and relies on centralized control and trusted third-party authentication (TA). Considering the pursuit of a verification scheme that balances high security, low overhead, distributed management, and efficiency, hybrid cryptography emerges as a potential solution. In contrast to single-user signature-based cryptography schemes that grapple with challenges such as key management and frequent changes in public/private key pairs, authentication schemes utilizing group signatures ensure the authenticity, integrity, and nonrepudiation of the data. These schemes are progressively improving in decreasing the computation time, delay in authentication, and message loss rate. On the other hand, schemes based on authentication exhibit enhanced authentication efficiency owing to their collaborative and batch authentication approaches.
In conclusion, strong and lightweight intrusion detection and authentication protocols must be offered in the context of fragile VANET. To maintain VANET security and privacy protection, additional requirements include the authenticity of nodes and messages, network availability, ensuring the integrity and confidentiality of messages, and guaranteeing nonrepudiation post-transmission. Additionally, to maintain security and privacy safeguards, one should proactively investigate fusing various attack detection and authentication schemes or integrating technologies in particular domains. By doing this, one can create comprehensive, reliable, effective, and sustainable solutions for the establishment of VANET while also finding a middle ground on some challenging issues. Some of the open challenges have been discussed which will help the researchers to get a new perspective. As society develops, technology advances, and researchers continue to work, the forthcoming VANET will revolutionize people’s lifestyles.
Conflicts of Interest
The authors declare no conflicts of interest.
Author Contributions
All the authors have contributed to this research.
Funding
No financial assistance was received for this research.
Acknowledgments
The authors thank REVA University for support and encouragement.
Open Research
Data Availability Statement
No dataset was used in this review work.




