Internal Control Model of Enterprise Financial Management Based on Market Economy Environment
Abstract
In order to better solve the problems existing in the internal environment, risk assessment, and internal supervision of enterprise financial management, this paper proposes a method of enterprise financial analysis and control model based on artificial neural network algorithm. The results show that, through the internal control model and management optimization of financial management, a large number of calculations and subjective affairs in the process of financial work can be avoided to the greatest extent. For enterprises, a large number of human, material, and financial resources can be saved for data collection, which is more conducive to improving the enterprise financial management system, improving the quality of financial information, providing technical support for enterprise decision-making, and further reducing the risk in the process of enterprise operation.
1. Introduction
In today’s society, with the continuous development and improvement of the market economic environment, enterprises have obtained opportunities for rapid development in this environment. At the same time, facing the increasingly competitive market economic environment, enterprises are facing more and more severe challenges. The development of modern enterprises is increasingly dependent on emerging technologies such as Internet and computer network. Especially with the popularization and application of various office software, it provides convenience for the internal management and control activities of enterprises [1]. As an important part of internal management control, enterprise financial management activities also need to face the reform and innovation of technological development. Under the background of the continuous development of various office software, the internal control system of enterprise financial management under the traditional mode is no longer suitable for the current development environment [2]. Enterprises urgently need to innovate and improve the financial management control system in combination with internal and external development needs. Therefore, in order to further solve the internal control problem of enterprise financial management and improve the financial management system, this paper proposes a financial analysis and control model based on artificial neural network algorithm.
2. Literature Review
Yang, Q. and others believe that the theory, evaluation, and planning of internal control are the main concerns of relevant foreign scholars. First of all, internal control theory is a very basic concern in academic circles. Some foreign scholars believe that internal control needs to establish a stable model, which can measure the measures of internal control [3]. Yin, Z. and others proposed a new model to ensure the effectiveness of internal control measures. Under this model, new internal control measures are proposed, but the reliability becomes uncertain [4]. Li, X. and others believe that the evaluation and planning of internal control have attracted extensive attention of relevant scholars abroad. They designed a questionnaire containing various internal control cases and then looked for some qualified experimental objects, such as auditors and students, and asked them to answer the questions on the questionnaire. Through the questionnaire, it is found that, in the evaluation of internal control, the separation of responsibilities is the most important part in the design of internal control. Through the questionnaire survey, it is found that the quality of internal control evaluation is closely related to the experience and judgment of auditors in the process of internal control evaluation. At the same time, in the process of audit, the variable factor of environment is also extremely important [5].
Zhang, T. and others believe that, with regard to the internal control system, some domestic scholars believe that the establishment of the internal control system should keep up with the pace of the times and fully consider the culture, policy, environment, and other problems existing in their own enterprises. They believe that the attitude of enterprise managers is extremely important to the enterprise’s internal control system. Only when enterprise managers recognize the importance of internal control and strengthen the supervision of the operation of internal control can the enterprise’s internal control operate effectively [6]. As for the evaluation of internal control, Wang, Y. and others believe that the evaluation of enterprise internal control should be analyzed from two aspects: internal environment and external environment. First of all, they believe that the internal guarantee mechanism of the enterprise is extremely important for the evaluation of the internal control of the enterprise [7]. Beridze, T. and others believe that an effective internal guarantee mechanism can ensure the implementation of the internal evaluation system. Secondly, they believe that the effective evaluation of enterprise internal control requires the relevant external supervision departments of the enterprise to do a good job of supervision and review. However, in China, the provisions used to ensure the effective evaluation of enterprise internal control are still imperfect [8].
At present, the research on financial sharing abroad focuses on the connotation and characteristics of financial sharing, the connotation and evaluation of internal control, and so on. Liu, J. and others believe that the domestic research on financial sharing is biased towards practice, and the research on internal control focuses on concepts, objectives, elements, etc. However, there is little research on the internal control of enterprises under the financial sharing mode at home and abroad. At present, most of the research on internal control under the financial sharing mode in China is based on practice [9]. Zhang, R. and others believe that the implementation of financial sharing mode by enterprises can improve the processing efficiency of basic financial work of enterprises, ensure the accuracy of financial business processing, and meet the financial requirements of enterprise business. However, most of the research focuses on the internal control during the construction of enterprise financial sharing mode, but the research on the continuous optimization of internal control in the operation process of enterprises is reduced. Financial sharing is a double-edged sword. Enterprises should not only pay attention to the benefits it brings to the enterprise, but also realize its impact on the quality of internal control [10], for example, the separation of financial personnel from business posts, the high informatization of financial information, and the increase of personnel turnover rate.
3. Design of Internal Control System of Enterprise Financial Management
3.1. System Requirements
3.1.1. Main Contents of Financial System Requirements
Many contents in the financial management system are interrelated, mainly including bookkeeping management, voucher management, salary management, fixed assets management, account book report analysis, and transaction cashier management. Common master data include currency and account common summary, which are connected with each other through basic data. When an enterprise has economic and business activities, the system user can easily enter fixed assets, business vouchers, etc. on the system operation interface [11].
3.1.2. Management of Master Data
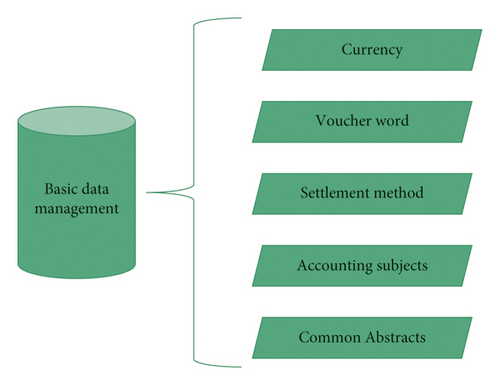
The management of master data in financial management mainly includes the following six elements: currency type, voucher word, and settlement method (as shown in Figure 1). These six elements correspond to six accounting subjects, respectively. In the process of managing master data, the management of accounting subjects is one of the cores of the whole process [12].
3.1.3. Handling of Financial Business
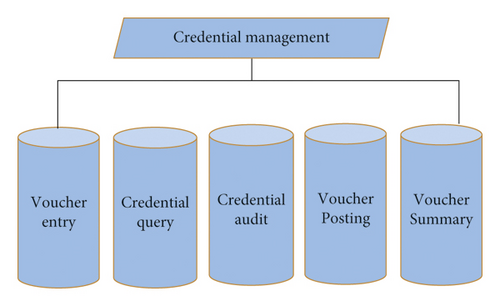
Accounting voucher: it is mainly a written proof that is recorded in the business activities of the enterprise and clearly records the economic responsibility. In addition, it is also a main basis for accounting and analyzing financial statements. The steps are as follows: whenever business activities occur, the first step is to fill in the original voucher, and the second step is to review and record according to this voucher. Only the approved and qualified original voucher can be used as bookkeeping voucher, so as to serve as the basis for the preparation of financial statements [13].
Bookkeeping method: it is the method by which accountants register and record business in economic and business activities. Accounting elements will increase or decrease in economic transactions, which are based on vouchers. Single entry bookkeeping and double entry bookkeeping are often adopted in economic activities. Debit and credit bookkeeping belongs to the category of double entry bookkeeping. Among these current bookkeeping methods, it is the most frequently used method. Its main feature is to take the accounts of both lenders and borrowers as bookkeeping vouchers [14]. The most basic bookkeeping rule is to ensure the equality of debit and credit. See Figure 2 for details.
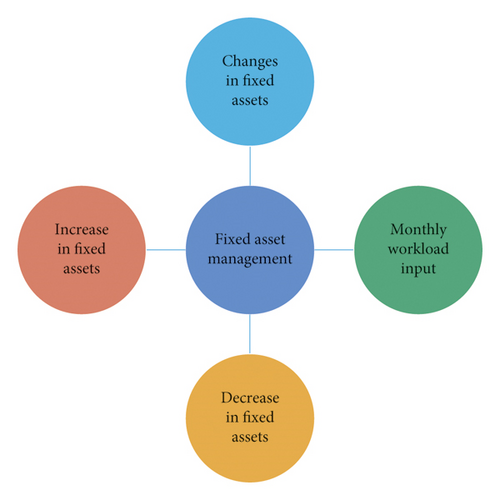
Management of fixed assets: the fixed assets management method is used to manage and calculate the increase and decrease of fixed assets or the calculation of depreciation [15]. Depreciation of assets refers to the systematic allocation of the recorded depreciation value by a certain method within a specified range. Depreciation preparation should be carried out in this function according to the specific conditions of fixed assets. See Figure 3.
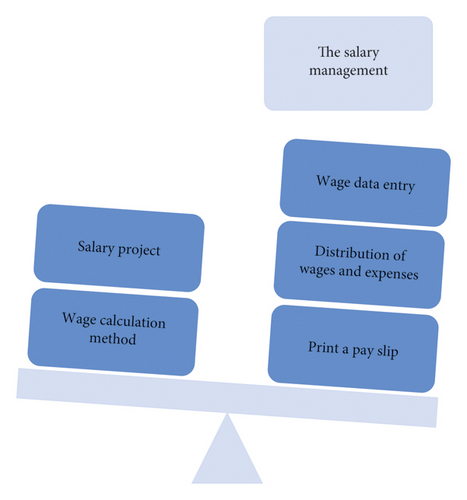
Salary management: it refers to business activities such as accounting and payment of work issued by enterprise employees, which belong to this management category [16]. Generally, the main contents of salary management include salary items, salary data input, salary expense allocation, salary statistics, and many other businesses, as shown in Figure 4.
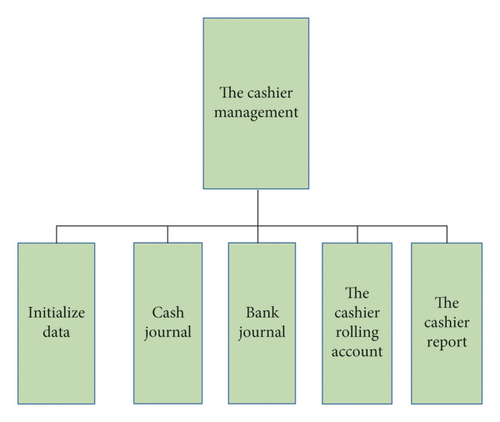
Cashier management: it is one of the most important positions in enterprise financial accounting, as well as cashier, who is mainly responsible for the collection and payment of cash deposits and withdrawals in the enterprise and between banks. Cashier management includes the functions of initializing data entry, bank journal, and cash journal, cashier account, and report [17]. It can be provided to the cashier staff alone or combined with the general accounting system. See Figure 5.
3.1.4. Analysis of Financial Books and Statements
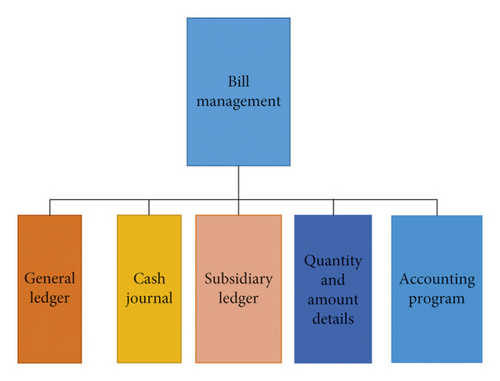
Account book management: account book management includes general ledger module, subledger module, quantity and amount details, quantity and amount total, and other account modules and provides filtering and query functions for various result account books and accounting processing [18]. The general ledger can perform query under various conditions during the accounting period and query according to different currencies. See Figure 6 for details.
Statement and analysis: generally, financial statements are composed of various statements, such as account daily report, account balance statement, trial balance statement, balance sheet, accounting item list, and profit statement. In addition, financial analysis is another important component [19]. On the basis of accounting, through accounting, based on the form of financial statements and account books, further analyze the data summarized in the financial part according to the specified methods, so as to obtain the overall financial analysis results.
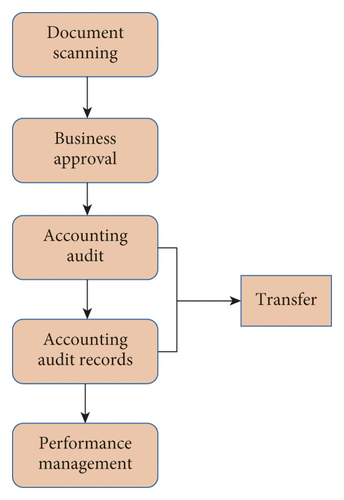
Performance management: it uses the evaluation method of piecework salary. The daily and monthly workload of each service personnel can be visually displayed on the wall display. The flow chart is shown in Figure 7:
3.2. Overall System Architecture
3.2.1. Overall Structure Design of the System
The characteristic of C/S structure is the main characteristic of the system. The client is responsible for the operation of relevant services, and the server is responsible for the management and storage of data. Some C/S structure modes are characterized by the hardware environment in which the software client on the LAN works and the data exchange speed is fast [3]. The security requirements of their customers can be met. They can meet the basic framework of business process processing with complex business logic.
3.2.2. Overall System Architecture Design
The user interface of the system is developed by using the WinForm developer tool of VS2005. The corresponding business process processing of the system is completed by c# language, and the function of aspect layer is also the result of the combination of net platform and Spring.NET framework technology. Finally, the database management of the system is completed by using SQL Server 2005. The specific architecture is shown in Figure 8.
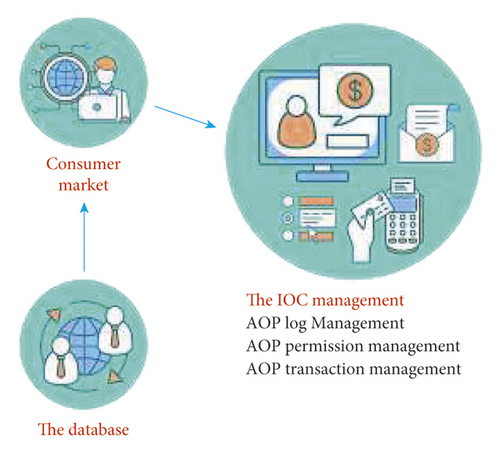
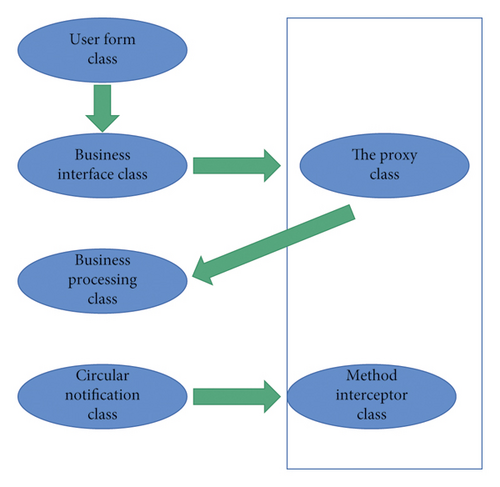
In this system, different system functions have corresponding module design, and each part of the modules are connected through the database, so as to realize the whole process of data exchange. Each module has its own special structural characteristics in order to deal with different services [20]. The interception of data information by each module corresponds to the whole business processing process. The acquisition of surround notification is the result of analysis and processing in IOC container and agent class. During this process, the system will perform permission detection to complete the corresponding log management function. The detailed calling relationship is shown in Figure 9.
3.3. Design of Business Processing Layer
After completing the interface design of the form, the system will further design the business processing layer. Take the business layer of the voucher management module as an example for further analysis [21]. Firstly, the system will create a business type voucher class for the module to realize the agent and interception of information more conveniently and quickly and then create an interface class: ivoucher class. In this process, the business to be processed needs to declare the business processing methods. Specifically, the main declaration methods include save, delete, audit, and other methods. These declarations will realize their processing functions in the voucher class, so as to facilitate the data exchange in the database.
3.4. Database Connection and Design
3.4.1. Design of Database Table Items
Usually, the form of tables in the database is mainly determined by the corresponding attributes of the data entity to be designed. When setting each attribute, it should be determined according to the corresponding fields. At the same time, each field can also have its own attribute characteristics. The main entities it contains include voucher date, voucher number, and voucher amount involved. These data can also be specifically divided into corresponding fields, so as to ensure that there is no duplication of data in the entity. In this way, the voucher information involved in the voucher is unique. In addition, another field can be set to indicate the personnel information involved in voucher processing, as shown in Table 1.
| Field name | Data type | Restrain | Describe |
|---|---|---|---|
| FSerialNumber | Int | Major key | Order number |
| FDate | Datetime | Nonempty | Date |
| FGroup | Nvarch ar | Nonempty | Certificate word |
| FNumber | Int | Nonempty | Certificate number |
| FExp | Nvarch ar | Nonempty | Abstract |
3.4.2. Database Connection and Interaction
In the net framework of the system, the ADO.NET program is used to realize the connection between it and the database. There are two main methods used in this process [6]. The first method is to use SQL Command class to obtain relevant operation commands and then relevant data information. Generally, this method is suitable for data types with relatively single type. Another method is the Dataset class. This method can obtain the relevant data in the database, and it can also meet the function of obtaining data under offline conditions. On the contrary, it is suitable for databases with many data or many data reports.
By analyzing the functional requirements of the financial system, we get the structural characteristics that the system software should have and then use the corresponding system development software to carry out the detailed design of the system. After analyzing the function realization form of the system in theory and time, we also get the overall architecture of the system and the design of corresponding function modules.
4. Enterprise Financial Control Model Based on Artificial Neural Network Algorithm and Its Application
4.1. Mathematical Model of BP Neural Network
The above formula is the weight coefficient of the i th neuron to x1, x2, …, xn, that is, the transmission efficiency of synapse. yi is the output of the i th neuron, and f(⋅) is the excitation function, which determines how the neuron outputs when it is stimulated by the input and reaches the threshold.
This method is a BP algorithm with variable learning rate, which belongs to the heuristic improvement of SDBP algorithm. It can improve the learning speed of BP network and accelerate the convergence.
4.2. Application of Artificial Neural Network in Financial Control Analysis
4.2.1. Model Construction
First, the structure of the BP neural network is selected and developed. This material creates a three-layer conductive neural network. The number of vessels in the entry process is the number of options in this form. The process of determining the number of neurons in the latent layer has not yet reached a unified theory. However, experience has shown that the number of nodes in the n layer is equal to 2n > m, and M is the number of nodes in the n layer. Therefore, the presence of three neurons in the latent layer and a neuron in the output layer, i.e., the complex value of the enterprise profitability, was determined.
Second, initialize the network parameter, assign the weight and initialization of the connection between the network access layer and the encryption process, and set the weight and initialization of the connection between the encryption process and the encryption process output by random number [22].
Use the next extension line as a signal to suggest and train all types of training for a week until all errors reach reality; then stop the training. Otherwise, change the training time and return to the training.
4.3. Application and Empirical Analysis of Artificial Neural Network in Comprehensive Analysis of Financial Situation
4.3.1. Empirical Analysis
The data in this paper is the actual basic financial data of 31 listed companies in the third quarterly report of Shanghai and Shenzhen in 2009 published by Tsinghua financial research database, and then calculate the index values of return on net assets, stock return, and total asset profit margin of each listed company according to the corresponding formula, as shown in Table 2.
| Securities name | Forecast return on equity | Return on equity | Earnings per share |
|---|---|---|---|
| ST waveguide | 0.3 | −6.34 | −0.04 |
| Orchid kechuang | 21.77 | 21.71 | 1.63 |
| SST Huaxin | 35 | 16.45 | 0.04 |
| ST northeast high | 20.3 | 4.51 | 0.18 |
| Guan aluminum shares | 0.6 | −35.12 | −0.42 |
| Hubei yihua | 15.1 | 7.68 | 0.24 |
| S “ST tianxiang | 19.64 | 8.28 | 0.16 |
| New and into | 35.21 | 31.21 | 1.85 |
| Securities name | Operation can force index | Operation can force to one spend | Comprehensive financial condition |
|---|---|---|---|
| ST waveguide | 0.23490 | 0.837090 | 0.11169 |
| Orchid kechuang | 1.44229 | 1.90917 | 1.37009 |
| SST Huaxin | −0.33428 | −0.12453 | 0.54991 |
| ST northeast high | 0.73967 | −0.48896 | −0.00401 |
| Guan aluminum shares | 12.63627 | 14.86810 | 13.27131 |
Because there are many indicators that make up the profitability of enterprises, and there are mutual influence and complex nonlinear relationships among various indicators, this paper applies artificial neural network to the evaluation of enterprise profitability. Compared with the traditional method, it has the advantages of simple principle, strong operability, fast speed, and high fitting accuracy, avoiding a large number of calculations and human subjective errors in the working process. More importantly, for enterprises, establishing the network model does not need to spend a lot of human, material, and financial resources to collect data, and the network has good generalization ability and strong universality after training. Therefore, in today’s highly competitive era, the model has great use value.
4.3.2. Specific Application
Enterprises are in the need of maintaining daily business activities and long-term development, and considering the application of financial leverage, they generally raise funds by borrowing from abroad, so as to form the liabilities of the enterprise. Solvency reflects the financial situation of an enterprise to a certain extent and is an important content of enterprise financial analysis. In the general solvency analysis, it is divided into short-term solvency analysis and long-term solvency analysis. The analysis of short-term solvency mainly focuses on the relationship between current assets, asset liquidity, and current liabilities, while the analysis of long-term solvency involves the capital structure, profitability, and liquidity of enterprises. This solvency analysis method is undoubtedly a waste of resources from a certain point of view. On the basis of retaining the traditional analysis methods and perspectives, this paper combines the short-term solvency and long-term solvency by using the weighted average method. Different analysts can not only determine the weight of the two solvency types according to different purposes, but also see the comprehensive solvency concisely and intuitively.
Considering the availability of indicators and the needs of analysis, this paper selects three aspects: profitability, solvency, and operational capacity, with a total of 13 indicators as the elements of comprehensive financial situation analysis. They are current ratio, quick ratio, asset load ratio, shareholder’s equity ratio, profit margin of main business, return on net assets, return on total assets, earnings per share, growth rate of main business income, growth rate of total assets, growth rate of net profit, turnover rate of total assets, and turnover rate of accounts receivable. All the data are from Tsinghua financial research database.
4.4. Suggestions on Internal Financial Control of Enterprises
4.4.1. Attach Importance to Self-Evaluation of Internal Control
Enterprises should pay attention to the self-evaluation of internal control. Effective self-evaluation can fundamentally combine the strategic objectives of enterprises with risks and control processes, ensure the reliability of internal control system, reduce fraud risk, and strengthen the grasp of the overall risk status of enterprises. Enterprises can use seminars, questionnaires, data analysis and trends, communication audit, and other methods in self-evaluation. No matter what kind of self-evaluation method, the following three key issues should be designed. The first is whether the internal control operates according to the design. This problem can avoid the embeddedness of ownership and responsibility in the process of risk and control. The second is how to monitor the effectiveness of control? This question helps to identify other risks and improvement opportunities in control activities. The third is how to report and correct control defects? This problem is helpful to understand and solve the identified problems. In addition, when conducting self-evaluation, we should also consider whether self-evaluation can be effectively implemented. First, ensure that stakeholders support the implementation of self-evaluation. Auditors themselves cannot fully evaluate this broad-based control perspective, and all stakeholders need to participate and contribute. Secondly, we should have the idea of continuous improvement and set aside enough time and resources for thorough evaluation.
4.4.2. Refine Risk Types
- (1)
In view of the risk of business process, make appropriate changes to the process according to the existing business, increase the effective supervision links in the process, and eliminate the cumbersome and meaningless links.
- (2)
Operational risk: mistakes in the operation process under the financial sharing mode are very easy to occur, which has a serious impact on the business processing and information accuracy of the enterprise. The audit operation can be added in the appropriate process to find the errors in the operation in time and reduce the risk.
- (3)
Communication risk: because a great disadvantage of the financial sharing mode is that the financial personnel are far away from the business unit, this leads to the failure of the employees of the financial sharing center to provide guarantee for the authenticity and accuracy of the business, resulting in a certain risk. Communication needs to be strengthened so that every financial personnel can have a basic understanding of the business process of the enterprise, so as to avoid the risk caused by the financial personnel leaving the business unit.
- (4)
In the mode of risk management and financial sharing, the work of employees is too detailed, resulting in that each employee is only responsible for the business of his own post and can not fully understand the financial process of the enterprise. This will lead to the questioning of the work quality of enterprise employees, which will also bring certain risks to the enterprise. Therefore, enterprises can adopt the employee rotation system, so that employees can have access to comprehensive financial processes, improve work quality, and reduce enterprise risks.
- (5)
Information technology risk: financial sharing mode is to carry out financial management on the basis of information technology. This needs to ensure the reliability of information technology. The defects of information technology may lead to information leakage and information asymmetry and increase the risk of enterprises. Therefore, enterprises can strengthen the supervision of information technology and strengthen control by establishing systems.
4.4.3. Strengthen Enterprise Information Sharing
Send some representatives to the business units in the financial sharing center to exchange operations, so that the employees of the financial sharing center can have a general understanding of the company’s business environment and business process. In addition, company E can also establish an information base for some important suppliers and customers of the enterprise and enter all the information of important suppliers and customers of the enterprise, which can be viewed by the employees of the enterprise. At the same time, the enterprise can also establish a WeChat official account for enterprise business, edit the recent important business and recent business objectives of the enterprise into enterprise news, and send it to the enterprise WeChat. Employees in different regions can also communicate on the WeChat official account. This not only enhances the communication between enterprise employees, but also strengthens the transmission of enterprise business information.
5. Conclusion
Based on the AOP design mode, this paper studies, analyzes, designs, and implements the financial management platform, takes the traditional software system engineering as the theoretical basis, according to the needs of users, grasps the overall framework and functional modules of the system, and realizes its functions through programming. In the process of R&D, after long-term and serious thinking, summary, and demonstration, and with a new programming R&D and design concept, it combines program-oriented programming with object-oriented programming in the past. Thus, the two complement each other, which greatly reduces the workload of R&D personnel in the process of separating logical business layer and programming and makes the interface design of the system more friendly and convenient, so that the financial system platform can meet the needs of the company’s internal financial management to the greatest extent. When designing and determining the general structure of the system, we need to consider the business characteristics of enterprise finance and take this as the basis for analysis and research. For example, the check of user authority, the processing of voucher number, the caching technology of general basic data, the requirements of data accuracy in the financial system, and the architecture design are carried out to realize the relevant design of users’ viewing and using data authority. The AOP design mode is based on the Spring.Net framework. The results of user authority verification are divided into operation, sealed, and separated. Compared with the previous financial system, the results are scattered in various functional modules. The log management function and authority management function are provided for managers. It can better grasp the information in the operation and use of the financial system, so as to make the best decisions and strategies.
Conflicts of Interest
The author declares that there are no conflicts of interest.
Acknowledgments
This work was supported by the Economics and Trade Department, Shijiazhuang University of Applied Technology.
Open Research
Data Availability
The labeled data set used to support the findings of this study is available from the author upon request.




