A Crowdsourcing Information Obtaining Scheme Aiming at Senior Netizens Based on Blockchain
Abstract
Senior netizens play a unique role in crowdsourcing information obtaining, but the traditional crowdsourcing information obtaining scheme based on intermediary platform cannot satisfy the senior netizens’ strong reliability on anonymity. Malicious intermediary platform may leak out the privacy information of both parties. Data stored in intermediary platform may be intercepted, tampered, and fraudulently used by attackers, so smooth crowdsourcing information transactions cannot be ensured. In order to achieve secure and reliable crowdsourcing information obtaining, blockchain technology with decentralization and nontampering was used to propose a crowdsourcing information obtaining scheme, which is independent on intermediary platform. During processes of requirements releasing, information submitting, and rewarding, privacy protection techniques were used to preserve the anonymity of participants and confidentiality of data. Compared with the existing protocols, the proposed scheme has obvious advantages in privacy protection.
1. Introduction
The concept of crowdsourcing was proposed by Howe [1] and refers to outsourcing tasks to unspecified mass networks in a free and voluntary way. The basic model of traditional crowdsourcing includes the outsourcer, the contractors, and the crowdsourcing intermediary, which constitute the crowdsourcing operation organization. The outsourcer issues requirements and the intermediary provides tasks; the contractors submit the information, and the intermediary feedbacks contractors’ submission. Crowdsourcing activities often involve many people in bidding for a task, and the evaluation process is mainly based on the satisfaction of the outsourcer of the task. According to the purpose of crowdsourcing, it can be divided into crowd wisdom [2], crowd creation, crowd voting, and crowdfunding. Crowdsourcing information obtaining activities are crowd wisdom activities, in which the outsourcer attracts netizens to participate voluntarily, and the contracting netizens collect and provide the information to the outsourcer through Web pages, newspapers, and magazines and field investigations, and the outsourcer screens the effective crowdsourcing information manually and systematically and gives appropriate rewards to the participants. In the crowdsourcing information obtaining scheme in this paper, the contractors mainly consist of senior netizens, because the space-time extension and anonymity of the network attract senior netizens to stay on the Internet for a long time, which is an important force to participate in network activities. However, in the traditional crowdsourcing information obtaining scheme that relies on the intermediary platform, it is difficult to ensure senior netizens’ strong requirement of anonymity, and the intermediary platform, driven by its interests, may disclose the private data of the outsourcer and the contractors in the process of crowdsourcing information transactions. At the same time, attackers will take various measures to intercept, tamper, and fraudulently use key data stored in the intermediary platform. Once the intermediary platform is attacked, it will directly threaten the fluent operation of the whole crowdsourcing transaction mechanism.
- (1)
Establish a decentralized and nontampered crowdsourcing information obtaining framework based on blockchain. Before joining the crowdsourcing information obtaining blockchain, the key generation center generates certificateless public and private key pairs, including initialization parameter generation and nodes’ public/private key pair generation
- (2)
Design the release algorithm of the crowdsourcing information requirements. The certificateless multireceiver anonymous signcryption scheme is used to complete the release of the requirements, and the blockchain address of the outsourcer, the information requirements, and reward is encrypted together. Except for the intended contractors, other nodes cannot know the information such as requirements and rewards. In the signcryption information issued by the outsourcer, the blockchain address of the contractor is hidden to prevent other nodes in the network from tracking its identity through the blockchain address of the contractor. At the same time, each contractor only uses its private key and blockchain address in the process of unsigncrypt and does not need addresses of other contractors, thus, ensuring mutual anonymity among contractors
- (3)
Design the submission algorithm of the crowdsourcing information using the idea of random address, the outsourcer generates a temporary public key address and records it in the blockchain. The contractor uses its long-term private key to calculate the temporary private key for the information submission. After receiving the crowdsourcing information returned by the contractor, the outsourcer decrypts and verifies it, thus, realizing the confidentiality of the crowdsourcing information and preventing the identity of the contractor from being exposed in the process of submitting the information many times
- (4)
Design the reward accounting algorithm of the crowdsourcing information. The outsourcer determines the reward accounting of crowdsourcing information by generating ring signcryption, so as to prevent the leakage of identity privacy in the process of awarding. The contractor uses the temporary private key to decrypt the ring signcryption of the outsourcer and confirm the legal reward from the outsourcer. When using legal rewards, the contractor only needs to use its temporary private key to complete the signature, and the payee can verify the signature by using the temporary public key of the contractor recorded in the blockchain. Because the temporary public key addresses of the contractor are different in each crowdsourcing information transaction, the consumer anonymity of the contractor is realized
- (5)
Analyze the privacy protection effect and operation efficiency of the scheme proposed in this paper. In terms of privacy protection, this scheme is compared with existing information sharing schemes based on blockchain, mainly from three dimensions: outsourcer privacy protection, contractor privacy protection, and transaction data privacy protection. By comparison, it is verified that this scheme has obvious advantages over other schemes in privacy protection and has higher calculation efficiency
2. Relevant Work
Traditional crowdsourcing information obtaining is composed of the outsourcer, the crowdsourcing intermediary platform, and the contractors, and the crowdsourcing information obtaining task is completed through 9 steps. In the traditional process of obtaining crowdsourcing information, the outsourcer and the contractor need to release and submit the information through the intermediary crowdsourcing platform, which brings extra cost to both parties. On the other hand, there is no completely trusted intermediary in the real network, and the malicious crowdsourcing intermediary platform may sell the private information of both parties in crowdsourcing information transactions for its own benefits. At the same time, once the intermediary platform is attacked, the whole crowdsourcing transaction mechanism will be paralyzed and chaotic. Therefore, we can introduce decentralized blockchain technology into crowdsourcing information transaction to remove the dependence on crowdsourcing intermediary platform. The traditional crowdsourcing information obtaining process is shown in Figure 1.
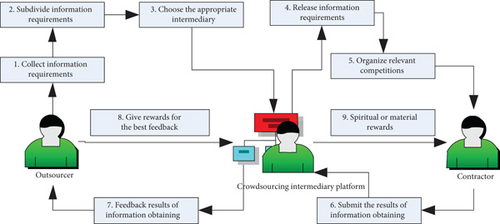
Because blockchain technology has the characteristics of no center, anti-tamper, and anonymity, scholars have applied blockchain technology to the field of network information sharing. Rawat et al. [3] designed a multimember information sharing framework based on blockchain technology, in which nodes in blockchain can share network security protection schemes, and analyzed possible attack behaviors in the system based on game theory. Huang et al. [4] designed a network security threat intelligence sharing model based on blockchain to solve the privacy protection demand of users in the process of threat intelligence sharing. However, this model directly uses the anonymity of users’ accounts in the blockchain to protect the identity privacy of both parties in the threat intelligence sharing, which can only provide weak anonymity. In the frequent information sharing process between the two parties, attackers can infer the true identity of users by analyzing the correlation between transactions, statistical characteristics, and transaction amounts. At the same time, the status of the threat intelligence center in the model is not equal to that of the organization, and the organization needs to register at the threat intelligence center when joining the threat intelligence sharing blockchain. Wang et al. [5] proposed a private data sharing model of medical blockchain based on ring signature. However, this model only considers the anonymity protection of transaction outsourcer and lacks the anonymity protection mechanism of contractor. At the same time, the ring signature message is not encrypted, which easily leads to the leakage of users’ private data. He et al. [6] proposed an incentive mechanism for crowdsensing applications based on blockchain technology, which uses digital signature and watermarking technology to prevent the sensing data from being tampered and used under false pretences, but this scheme does not protect the confidentiality of the sensing data and the identity privacy of the sensing users. Cheng et al. [7] designed a framework of network threat intelligence sharing and rating system based on blockchain, but did not give technical details to protect the confidentiality of threat intelligence and the anonymity of nodes. Cai et al. [8] designed the application framework of Internet public welfare crowdfunding platform on blockchain, but also did not involve specific measures to protect the privacy of platform users and the security of crowdfunding data. Xu et al. [9] designed a privacy protection scheme for electronic health records based on blockchain and homomorphic encryption, which uses proxy reencryption technology to protect the security of patient’s privacy data. However, the protection of patient’s identity privacy only depends on the anonymity of the patient’s Ethereum address, and there is still the risk of identity being tracked and leaked during the frequent use. Sandro et al. [10] designed a secure sharing framework of personal health data based on blockchain, which mainly relies on the anonymity of blockchain addresses to protect user’s personal privacy. Li et al. [11] established a trusted big data sharing model without center by using blockchain and smart contract, but the privacy protection of data provider and data demander mainly depends on the anonymity of blockchain address. Mohammad et al. [12] proposed a data sharing framework based on licensed blockchain to ensure real-time authentication of shared data and tracking audit of data access in blockchain. The scheme uses the public key of data subject to encrypt access records, which protects the privacy of data subject, but does not protect the privacy of data accessor. Fan et al. [13] proposed a data sharing scheme for content-centric 5G networks based on blockchain. The scheme issues identity certificates to each user and uses encryption technology to ensure the confidentiality of data in the network, but it lacks protection measures for the identity privacy of data sharing parties in blockchain. Qiao et al. [14] designed a data sharing scheme for 5G IoT based on blockchain to solve the privacy of transactions under the chain, but did not discuss the privacy protection strategy of both parties in the chain cash withdrawal transaction.
The research of blockchain’s application in information sharing in other industries has made some progress, but these research results cannot be directly applied to crowdsourcing information obtaining. It is difficult to meet the special needs of both parties of crowdsourcing transactions for personal identity privacy and transaction privacy. To solve the above problems, this paper designs a crowdsourcing information obtaining scheme based on blockchain. The scheme uses a certificateless multireceiver anonymous signcryption scheme with anonymous to release crowdsourcing information requirements and rewards, which not only protects the confidentiality of information requirements but also ensures the anonymity of the outsourcer and the contractor. To generate a temporary public-private key pair for the contractor, the contractor uses the temporary private key to signcrypt the collected crowdsourcing information to ensure the secrecy of the returned information and the identity untraceablity of the contractor. The One-Time-Pad ring signcryption algorithm is used to ensure the anonymity of the outsourcer in the reward payment transaction and the secrecy of the reward amount, and at the same time, the untraceability of the contractor in the process of using the reward for consumption is realized.
3. Background Knowledge
3.1. Blockchain Technology Foundation
Blockchain is a distributed ledger that records transaction data permanently [15], which is formed by linking some ordered data structures (also called blocks). All nodes in the blockchain network share a complete ledger, and once the transactions recorded in any ledger are released, it is difficult to modify them. Due to the difference of decentralization degree, there are two forms of blockchain [16]: the unlicensed chain and the licensed chain. The unlicensed chain is completely decentralized, and nodes are free to join and exit. It is suitable for a completely open and highly autonomous application environment. In the licensed chain, there are a few nodes that have higher authority than ordinary nodes. When joining, the nodes need to be authorized by the central node. The licensed chain is mainly suitable for small-scale internal data sharing.
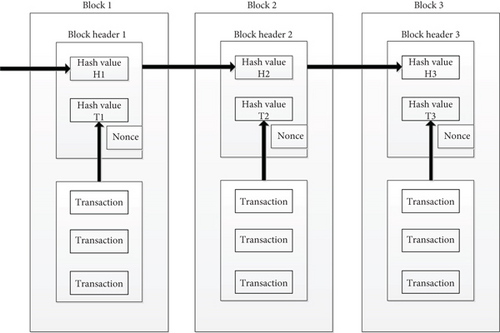
The data structure of blockchain consists of transaction records and blocks [17]. First, both parties create a new transaction and broadcast it to the blockchain. Miner nodes package and merge the transactions generated and verified to be legal within a certain period into blocks, compete for the bookkeeping right through the Proof of Work (PoW) mechanism, and then add the new blocks to the blockchain.
The core unit of blockchain is block, which is composed of block header to ensure the orderly and complete block data and block body containing several transaction records. The block header stores the hash value of the block header of the previous block, Merkleroot, which is the overall hash value of all transaction data in this block, and a random number named nonce, timestamp, and other structured information; The block body is used to record the summary information of all verified transactions and a Merkle Tree [18] which ensures that transactions cannot be tampered. Figure 2 shows the data structure of blockchain.
3.2. Unlicensed Signcryption Scheme [19]
- (1)
Setting of System Parameter. Enter the security parameter η, KGC sets the system public parameters, generates the system master key s, and keeps it secretly
- (2)
Setting of Partial Public and Private Keys. Enter system parameters, master key s and user’s identity IDi, and KGC sets user’s partial public and private key (Di, ui)
- (3)
Setting of User’s Secret Value. Taking system parameters and user’s identity IDi as input, the user sets its secret value xi and keeps it secretly
- (4)
Setting of Complete Private Key. Taking system parameters, user’s identity IDi, partial private key ui, and secret value xi as inputs, the user sets its complete private key (xi, ui)
- (5)
Setting of Complete Public Key. Taking system parameters, user’s identity IDi, partial public key Di, and secret value xi as inputs, the user sets its complete public key (Xi, Di)
- (6)
Signcryption. Take system parameters, message m, signer’s identity IDA, private key (xA, uA), receiver’s identity IDB, and public key (XB, DB) as input, the signer outputs the signcryption σ of message m
- (7)
Verification of Signcryption. Take system parameters, σ, signer’s identity IDA, public key (XA, DA), receiver’s identity IDB and private key (XB, DB) as input, receiver performs decryption and verification, then outputs that m is “True” or “Rejected”
3.3. CryptoNote Protocol [20]
- (1)
The outsourcer randomly selects an integer r and calculates R = rG; use the public key (A, B) of the contractor to calculate the one-time transaction public key P = H(rA)G + B
- (2)
The outsourcer initiates the transaction and releases R, P, and the transaction amount on the blockchain
- (3)
The contractor calculates P’ = H(aR)G + bG by using its private key and compares it with the one-time public key included in the transaction initiated by the outsourcer. If it is consistent, it is determined that it is the legal contractor of the transaction
- (4)
The legal contractor calculates the one-time private key x = H(aR) + b corresponding to the one-time public key and uses this private key to sign and consume the transaction revenues
4. A Crowdsourcing Information Obtaining Scheme Based on Blockchain
4.1. Overall Description of the Scheme
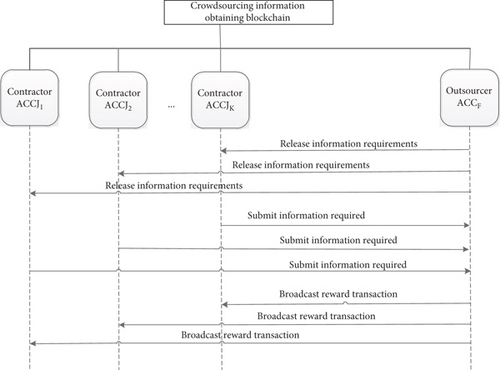
Because the contractors of the crowdsourcing information obtaining scheme in this paper are senior netizens in the network, and the senior netizens often have characteristics such as self-dependence, independence, alertness, and low self-exposure, the anonymity of the network plays a vital role in stimulating senior netizens to participate in crowdsourcing information obtaining. The unlicensed blockchain can be completely decentralized, allowing nodes to freely join and exit the network. This high autonomy is completely consistent with the strong dependence of senior netizens on network anonymity, which can give full play to their own advantages. Therefore, this paper designs a crowdsourcing information obtaining scheme in unlicensed blockchain. The network nodes include the outsourcer node, the contractor node, and the miner node. Among them, miner nodes compete to obtain the bookkeeping right through the PoW mechanism, verify the crowdsourcing transactions, and package the verified transactions into the new block. All miners are jointly responsible for the maintenance of the blockchain. For the sake of simplification, it is assumed that there is one outsourcer node F and multiple contractor nodes J1, J2, ⋯, Jk in the network, and the scenarios of multiple outsourcers and multiple contractor nodes can be discussed similarly. Before joining the crowdsourcing information obtaining blockchain, the outsourcer node and the contractor node need to generate their own public and private key pairs and blockchain transaction addresses.
- (1)
Release Stage of Crowdsourcing Information Requirements. The outsourcer collects information requirements and sends the requirements and reward to the contractor (senior netizens). The release algorithm of the crowdsourcing information requirements in 4.3 will be used in this stage
- (2)
Submission Stage of Crowdsourcing Information. The contractor makes full use of its superior resources to collect the information meeting the task requirements and submit the required information to the outsourcer. The submission algorithm of crowdsourcing information in 4.4 will be used in this stage
- (3)
Evaluation and Reward Stage of Crowdsourcing Information. The outsourcer evaluates the quality, timeliness, and benefit of the crowdsourcing information submitted by the contractor, selects the best result to pay remuneration, and realizes the incentive for the contractor to participate in the crowdsourcing information collection. The reward accounting algorithm of the crowdsourcing information in 4.5 will be used to generate a reward transaction and broadcast the transaction to the crowdsourcing information obtaining blockchain. The basic architecture of crowdsourcing information obtaining scheme based on blockchain is shown in Figure 3
4.2. Initialization Settings
Before joining the crowdsourcing information obtaining blockchain, the outsourcer node and the contractor node first generate certificateless public and private key pairs.
- (1)
Generation of initialization parameters
- (2)
Generation of node’s public/private key pair
Node IDi selects a random number as its secret value, calculates Xi = xiP, and sends Xi‖IDi to the client wallet.
Then, returns to part of the user’s partial public-private key pair Di/ui and the node IDi obtains its complete public-private key pair (Xi, Di)/(xi, ui).
According to the key generation algorithm, the public and private key pair generated for the outsourcer node is (XF, DF)/(xF, uF), and then the blockchain address is ACCF = H0(IDF, DF, XF) calculated from the public key; the certificateless public-private key pair of the contractor node is , and the blockchain address is , 1 ≤ i ≤ k.
4.3. Release Algorithm of the Crowdsourcing Information Requirements
The first stage of the crowdsourcing information obtaining scheme based on blockchain is the release of information requirements and rewards: the outsourcer collects the information requirements of decision makers, subdivides the information requirements, and sends the information requirements and rewards to the senior netizens (contractors) positioned in the early stage. In order to ensure the identity anonymity of the outsourcer and the contractor in the process of releasing crowdsourced information requirements and to realize the privacy of crowdsourcing information and rewards, the certificateless multireceiver anonymous signcryption scheme proposed in reference [19] is used to sign the requirements and rewards. Set M = (T‖requirements‖reward), where T is a timestamp.
- (1)
Randomly select a number calculate R1 = r1P and h = H1(R1 + XF, ACCF, M, DF), SIG = r1 + xF/xF + huF
- (2)
Randomly select , calculate R2 = r2P
- (3)
Calculate , 1 ≤ i ≤ k, and calculate Lagrange interpolation polynomial
- (4)
Calculate
- (5)
The outsourcer broadcasts ciphertext σ = (V1, V2, ⋯, Vk, R1, C) to the group of the contractors
- (1)
Calculate
- (2)
Get the blockchain address ACCF of the outsourcer from the recovered message, and then calculate
- (3)
Verify the equation by using the public key (XF, DF) and address ACCF of the contractor
Whether it is true or not, if so, the contractor confirms that the received signcryption is truly from the address ACCF, otherwise, it refuses the signcryption.
In the above algorithm, the outsourcer encrypts its blockchain address, information requirements, and reward amount, which makes it impossible for other nodes in the blockchain to know from which blockchain address the information requirements are released, except for the nodes in the intended contractor group. At the same time, in the signcryption information released by the outsourcer, the blockchain address of each contractor is also hidden. Not only can the nodes outside the contractor group not know the blockchain address of the contractor but also the contractor only uses its private key and blockchain address in the decryption process and does not use the address of other contractors. This ensures that each contractor cannot know each other’s blockchain address, that is, it can achieve mutual anonymity, which is consistent with the contractor’s requirement for privacy protection.
4.4. Submission Algorithm of the Crowdsourcing Information
- (1)
Randomly select a number , calculate Ti1 = ti1P, Ti2 = ti2P, 1 ≤ i ≤ k
- (2)
Calculate the temporary public key address of this crowdsourcing information transaction , 1 ≤ i ≤ k
- (3)
Record Ti1, Ti2, and , 1 ≤ i ≤ k, in the blockchain
- (1)
Randomly select a number , calculate Zi = ziP,
- (2)
Generate the signature of I
- (3)
Calculate
Send signcryption σ = {Zi, C} to the outsourcer F.
- (1)
Calculate
- (2)
Recover the data returned by the contractor
- (3)
Calculate
Whether it is true or not, if it is true, confirm that the information comes from the contractor corresponding to the blockchain address .
In the above algorithm, the contractor uses the temporarily generated private key to submit the data, so as to ensure the confidentiality of the data and prevent exposing its identity in the process of submitting. Normally, in order to protect the contractor’s enthusiasm to collect information, no disciplinary measures are taken for the contractor submitting information with low quality. If very few contractors maliciously submit irrelevant data for many times, the outsourcer can trace the blockchain address information of the malicious contractor according to the corresponding relationship between its retained contractor blockchain address and the temporary address, thus, excluding the malicious contractor address from the contractor set in the future information requirements release.
4.5. Reward Accounting Algorithm of the Crowdsourcing Information
- (1)
The outsourcer selects the one-time random key kF, calculates the corresponding public key KF = kFP, and then constructs the public key set {K1, K2 ⋯ , Kn}, which does not contain the one-time public key KF
- (2)
The outsourcer selects ai, (1 ≤ i ≤ n) to set the attribute value for the public key in the public key set:
- (3)
Set si = bi, ci = ai, 1 ≤ i ≤ n
- (4)
Calculate
- (5)
Calculate cF = aF − sFkF, and
- (6)
Select random number vF and calculate
- (7)
Calculate
- (8)
Define the reward transaction of crowdsourcing information as <time stamp T, {K1, K2, ⋯, Kn, KF }, , (WF, C)>, and broadcast the transaction to the crowdsourcing information obtaining blockchain
- (1)
Calculate with its temporary private key
- (2)
Restore the ring signature
- (3)
Calculate
- (4)
Verify the equation
Whether it is true, if so, confirm that the electronic money is the legal reward from the outsourcer for providing crowdsourcing information, otherwise, refuse it.
When the contractor uses the obtained reward for consumption, it only needs to use its temporary private key to sign m, without using its long-term private key; the payee uses the temporary public key address of the contractor recorded in the blockchain for verification. Because the temporary public key addresses of the contractor are different from each other in each crowdsourcing information transaction, the nodes in the crowdsourcing blockchain cannot link the real identity of the contractor with its consumption behaviors, thus, realizing the consumer anonymity of the contractor.
5. Privacy Protection and Efficiency Analysis of our Scheme
5.1. Privacy Protection Analysis
- (1)
Releasing of Information Requirements. In this stage, the outsourcer signed the blockchain address, released requirements, and reward together with the public key of the contractor, so that other nodes in the blockchain network could not know the specific information requirements and could not track the specific identity information of the outsourcers from the release of the crowdsourcing information task. In addition, in the signcryption released by the outsourcer, Lagrange interpolation polynomial is used to hide the blockchain address of each contractor, so as to prevent the blockchain address of each contractor from being exposed in the blockchain. Meanwhile, each contractor in the contractor node set only uses its private key and blockchain address information to decrypt the signcryption, and cannot use the addresses of other contractors, thus ensuring mutual anonymity among each contractor
- (2)
Submission of Crowdsourcing Information by the Contractor. In this stage, the contractor does not directly use the private key corresponding to its blockchain address to submit the collected crowdsourcing information, but the outsourcer first uses the public key of the contractor to generate the temporary public key of the contractor for this submission, and then the contractor uses the temporary private key corresponding to the temporary public key to signcrypt and transmit the collected information to the outsourcer. Because the contractor uses different temporary private keys every time, it can ensure the confidentiality of the data and prevent its identity from being exposed in the process of submitting the crowdsourcing information many times
- (3)
Evaluation and Reward Stage of Crowdsourcing Information. In this stage, in order to prevent the identity of the outsourcer from leaking in the process of multiple awards, the outsourcer uses a ring signcryption algorithm to sign the reward amount and then publishes the crowdsourcing information reward transaction in the blockchain. Attackers cannot associate the reward transaction with the real address of the outsourcer, and at the same time, the temporary public key address of the contractor is published in the transaction to prevent attackers from tracking its identity by using the public key address of the contractor
- (4)
When the contractor uses the obtained for consumption, it only needs to use its temporary private key to sign the reward m, and the payee uses the contractor’s temporary public key address for verification. Because the contractor’s temporary public key address is different from each other in each transaction, it realizes the anonymity of the contractor’s consumption
In the following, the privacy protection performance of the scheme in this paper is compared with the existing information sharing scheme based on blockchain. Here, we define the scheme that only relies on the anonymity of user’s blockchain address to protect the anonymity of user’s identity as satisfying weak anonymity and define the scheme that uses other special technologies to ensure the anonymity of user’s identity as satisfying strong anonymity. The results are shown in Table 1. The scheme in this paper has obvious advantages over other schemes in privacy protection.
| [4] | [5] | [6] | [7] | [8] | [9] | [10] | [11] | [12] | [13] | [14] | Ours | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Privacy protection of outsourcer | Weak anonymity | Strong anonymity | × | × | × | Weak anonymity | Weak anonymity | Weak anonymity | Weak anonymity | × | × | Strong anonymity |
| Privacy protection of contractor | Weak anonymity | Weak anonymity | × | × | × | Weak anonymity | Weak anonymity | Weak anonymity | × | × | × | Strong anonymity |
| Privacy protection of transaction data | No protection of transaction amount | × | × | × | × | √ | √ | √ | √ | √ | √ | √ |
5.2. Efficiency Analysis
In this section, the calculation efficiency of this scheme is quantitatively evaluated. The calculation cost of the scheme mainly depends on the calculation amount of the outsourcer and the contractor in the release of the requirements, the submission of the information, and the reward accounting. In order to improve the calculation efficiency, the above algorithms do not use bilinear pairing operation and exponential operation on multiplication group [22], but mainly use scalar multiplication operation on elliptic curve to design. “SM” is used to represent scalar multiplication operation on elliptic curve. Table 2 shows the calculation statistics of the outsourcer and the contractor in the scheme. Because other operations (hash operation and point addition operation) consume much less time than scalar multiplication operation, they are not included in the statistics here.
| Release algorithm | Submission algorithm | Reward accounting algorithm | |
|---|---|---|---|
| Outsourcer | (k2 + k + 2)SM | (4k + 3)SM | (2n + 3)SM |
| Contractor | (k + 2)SM | 4SM | (2n + 3)SM |
Among them, the parameter k is the number of contractors in the crowdsourcing blockchain, and n is the number of public keys in the public key set in the ring signature algorithm (which is a fixed parameter). If choose a 160-bit elliptic curve group on a hypersingular curve over a 512-bit finite field based on PBC library (Version 0.5.14), one SM operation takes about 1.51 ms [23]. It can be seen from Table 2 that the calculation cost of the outsourcer in the three algorithms of crowdsourcing information obtaining scheme is O(k2), O(k), and O(1), which are all effective polynomial time algorithms; as a contractor with weak computing power, the computational overhead in the three algorithms is O(k), O(1), and O(1) separately, which are all effective polynomial time algorithms with less computation, especially in the submission and reward accounting algorithms that the contractor frequently participates in.
6. Conclusion
On the basis of traditional crowdsourcing information obtaining scheme based on intermediary platform, this paper designs a crowdsourcing information obtaining scheme aiming at senior netizens based on blockchain. The scheme does not need intermediary platform, and in order to satisfy the absolute dependence of senior netizens on personal anonymity, the scheme uses the certificateless multireceiver anonymous signcryption scheme to release information requirements and rewards, so as to ensure the identity anonymity of the outsourcer and the contractor and the confidentiality of crowdsourcing information. In the submission stage, a temporary public-private key pair is generated for the contractor, and the contractor uses the temporary private key to sign and return the data to ensure the identity anonymity of the contractor in the process of submitting information for many times; in the process of reward accounting, the outsourcer uses the one-time temporary public key of the contractor to signcrypt the reward, so as to ensure the anonymity of its identity and the secrecy of the remuneration, and at the same time realize the untraceability of the consumption. Compared with the privacy protection of similar schemes, this scheme has obvious advantages.
Conflicts of Interest
The authors declare that they have no conflicts of interest.
Open Research
Data Availability
The experimental data used to support the findings of this study are included within the article.




