Underlay Cognitive Radio with Full or Partial Channel Quality Information
Abstract
Underlay cognitive radios (UCRs) allow a secondary user to enter a primary user′s spectrum through intelligent utilization of multiuser channel quality information (CQI) and sharing of codebook. The aim of this work is to study two-user Gaussian UCR systems by assuming the full or partial knowledge of multiuser CQI. Key contribution of this work is motivated by the fact that the full knowledge of multiuser CQI is not always available. We first establish a location-aided UCR model where the secondary user is assumed to have partial CQI about the secondary-transmitter to primary-receiver link as well as full CQI about the other links. Then, new UCR approaches are proposed and carefully analyzed in terms of the secondary user′s achievable rate, denoted by C2, the capacity penalty to primary user, denoted by ΔC1, and capacity outage probability. Numerical examples are provided to visually compare the performance of UCRs with full knowledge of multiuser CQI and the proposed approaches with partial knowledge of multiuser CQI.
1. Introduction
Cognitive radios convey a dynamic and flexible spectrum allocation policy that allows a secondary user to access a primary user′s spectrum through exploitation of advanced air-interface techniques and intelligent utilization of multiuser side information such as user activity, channel quality information (CQI), message, codebook, and location information, and so forth. A good tutorial about cognitive radios can be found in [1], focused on the signal-processing perspective, and in [2], focused on the information-theoretic perspective. One group of cognitive radios is known as the interweave paradigm, where a secondary user can opportunistically enter temporary spectrum holes and white spaces existing in both licensed or unlicensed radio spectrum [3]. Fast and reliable spectrum sensing techniques are the key to the success of interweave cognitive radios. The other group of cognitive radios includes overlay and underlay paradigms, where the secondary user and the primary user form a cognitive interference channel (e.g., [4–6]). Specifically, the overlay cognitive user is able to sense the primary user′s message, and then employs advanced coding schemes such as the Gel′fand-Pinsker code [7] or the dirty-paper code [8] for interference precancellation. In the underlay paradigm, the secondary user enters the primary spectrum only when its activity will not cause considerable interference or capacity penalty to the primary user. Measure of interference requires knowledge about multiuser CQI. The focus of this paper is on the two-user Gaussian underlay cognitive radios (UCR).
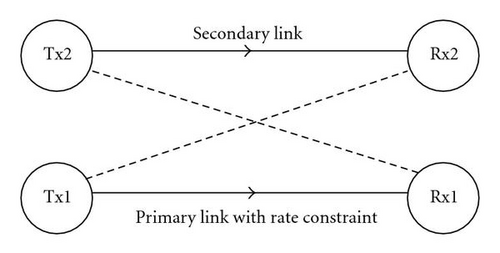
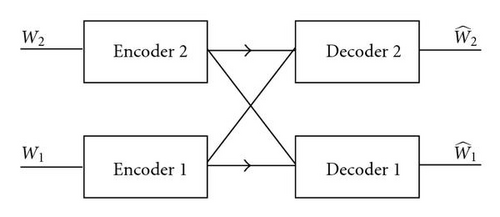
(1) Individual Decoding Both the primary user and the secondary user always deal with the mutual interference as noise in their decoding process.
(2) Secondary-User Side Multiuser Decoding (SSMD) The secondary user optimally deals with the interference term (a12X1) in its decoding process. But, the primary user always deals with the interference term (a21X2) as noise.
(3) Primary-User Side Multiuser Decoding (PSMD) The primary user optimally deals with the interference term (a21X2) in its decoding process. But, the secondary user always deals with the interference term (a12X1) as noise.
(4) Two Sides Multiuser Decoding (TSMD) Both the primary user and the secondary user perform an optimal treatment about the corresponding interference term in their decoding process.
Key physical layer issues this work seeks to address are mainly in two folds:
Issue 1 Provided full knowledge about multiuser CQI, what is the fundamental relationship between the secondary user′s achievable rate, denoted by C2, and capacity penalty to the primary user, denoted by ΔC1? What are criteria for Tx2 to perform efficient power allocation? Those questions require an answer for various UCR modes.
Issue 2 In many practical environments, having full knowledge of CQI about all links of the UCR system is not a suitable assumption. What are more suitable assumptions in practice? What is the efficient UCR strategy under new assumptions? What is the secondary user′s achievable rate? Those questions require a satisfactory answer.
-
(A1) We consider a two-user UCR system accommodating one primary transmitter-receiver pair and one secondary transmitter-receiver pair. This assumption can be easily assured by introducing orthogonal multiple-access schemes such as TDMA or FDMA to multiuser systems.
-
(A2) Users in the system are synchronized in both the time and frequency. Although the time-frequency synchronization is a challenge in practice, we would argue that the achievable rate produced under this assumption can be regarded as an upper bound of the practical performance.
-
(A3) Both receivers employ maximum-likelihood (ML) detector/decoder to offer the optimum decoding performance.
-
(1) The first work is to answer those questions listed in Issue 1. Provided full knowledge of multiuser CQI, the fundamental relationship between C2 and ΔC1 is investigated for four UCR groups. Criteria for efficient power allocation at Tx2 are established. The produced results are the key to new UCR strategies proposed for the case with partial knowledge of the multiuser CQI.
-
(2) As a starting point of the work towards Issue 2, we study modeling of UCR systems in the absence of full knowledge of multiuser CQI. After a careful justification, we establish an UCR system model, where the secondary user is assumed to have partial knowledge of CQI about the Tx2-Rx1 link, and have full knowledge of CQI about the other links. Location-aided UCR is employed as an example to support our justification.
-
(3) We propose new spectrum-access approaches for various UCR groups by assuming the availability of p.d.f. of CQI about the Tx2-Rx1 link. Power allocation criteria are carefully investigated in terms of C2, ΔC1, and capacity outage probability. (In practice, the performance of power allocation will be influenced by air-interfaces and synchronization errors. The results presented in this paper are to provide an information-theoretic guidance to practical designs.) Assuming the channel to be Rayleigh, numerical results are provided to visually show the performance of UCRs with full knowledge of multiuser CQI and the proposed approaches with partial knowledge of multiuser CQI.
The rest of this paper is organized as follows. Section 2 offers a brief review about capacity theorem of Gaussian interference channel (GIC) and relates it to the UCR system. Moreover, modeling about the UCR system with partial knowledge of multiuser CQI is also presented. Technical contributions towards four UCR groups are presented in Sections 3–6, respectively. Section 7 draws the conclusion.
2. System Model and Preparation
This section first presents capacity theorem about two-user GIC and its relationship with the UCR system, and then presents modeling of the UCR system with partial knowledge of the multiuser CQI.
2.1. Two-User UCR with Full Multiuser CQI
The UCR system is a special case of interference channels. The information-theoretic research towards interference channels started from Carleial′s work published in [9]. Although lots of research efforts have been paid in the last 30 years, capacity region of interference channels has been found only for the case of strong interference [13]. To the best of our knowledge, the state-of-the-art capacity bound of two-user GIC has recently been reported in [11, 12]. Next, we provide a brief review about capacity theorem of two-user GIC, which offers the theoretical support to our further investigation about the two-user UCR system.
2.1.1. Two-User GIC with Strong Interference
2.1.2. Two-User GIC with Weak or Mixed Interference
This scenario includes cases other than the case of strong interference. The closed form of capacity region is unknown to this date. A lookup table (but incomplete) about the channel capacity with respect to various channel conditions has been reported in [12]. Alternatively, we can divide the two-user GIC into the following three groups with respect to the way of dealing with the interference. The following result is adequate for us to investigate the two-user Gaussian UCR system.
Group I Each receiver can reliably decode the message sent by Tx1 and Tx2, respectively. The achievable rate region, denoted by ℛI, is (3).
Group II Each receiver can only decode the message sent by its corresponding transmitter. The interference will be regarded as noise. The achievablerate region, denoted by ℛII, is (see [9])
Group III One receiver can decode the message sent by both transmitters, and the other can only decode the message sent by its corresponding transmitter. In this group, the achievable rate region, denoted by ℛIII, is (see [12])
2.1.3. Two-User Gaussian UCR
2.2. Two-User UCR with Partial Multiuser CQI
-
(i) The secondary receiver Rx2 listens to the conversation between Tx1 and Rx1. Then, Rx2 can estimate the CQI of Tx1-Rx2 link.
-
(ii We assume that Rx1 employs a simple common codebook such as repetition code to perform the feedback of CQI. Then, Rx2 can obtain the CQI about Tx1-Rx1 link through sensing of the primary user′s feedback channel.
-
(iii) At the beginning of cognitive communication, Rx2 requests Tx2 to send a training sequence over the primary spectrum. This offers the knowledge of CQI about the Tx2-Rx2 link, but introduces a short burst of interference to the primary user. We argue that this burst of interference will not cause considerable performance loss to the primary user.
-
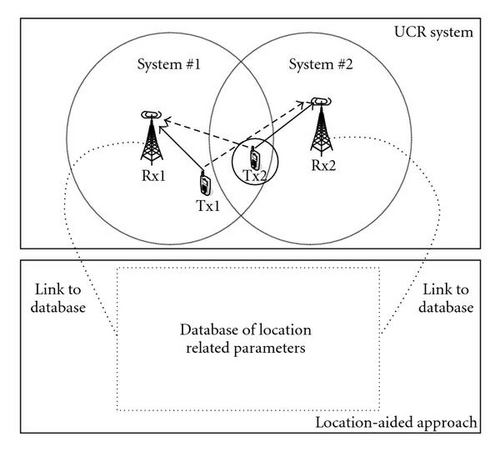
(iv) Rx1 may estimate the CQI of Tx2-Rx1 link if appropriate, but does not show this information in its feedback channel due to an upper-layer protocol. In this case, Rx2 cannot know the CQI of Tx2-Rx1 link. Then, our assumption is that the secondary user knows the p.d.f. of CQI about the Tx2-Rx1 link. This assumption is suitable for a scenario such as where the secondary user has the location information about itself and the primary user. The secondary user can access a well-designed and maintained database, which records the p.d.f. of CQI between two locations. Figure 1 illustrates an example of location-aided UCR system, where Rx1 and Rx2 are fixed network nodes such as base-stations or access points, and Tx1 and Tx2 are mobile stations. The database has a lookup table about the p.d.f. of CQI between each fixed network node and a certain area such as the black circle with solid line. Provided the location of Tx2, Rx2 knows which circle Tx2 is currently in, and thus can look up the database to find out the p.d.f. of CQI about the Tx2-Rx1 link. Recently, how to design and maintain the location-related database is becoming an important research topic. However, it is out of the scope of this paper. Further information about location estimation and location-related database can be found in European ICT WHERE [15].
-
(A4) Rx2 has full knowledge of CQI about the Tx1-Rx1 link, the Tx1-Rx2 link, and the Tx2-Rx2 link, but only knows p.d.f. of CQI about the Tx2-Rx1 link, denoted by p(|a21|2) as well as the mean E(|a21|2).
-
(A5) Rx2 determines the secondary user′s power and transmission rate, and then informs Tx2 through the feedback channel.
3. The Individual Decoding Mode
- (i)
Both the primary user and secondary user employ their private codebook;
- (ii)
Even if both users employ a common codebook, each receiver cannot decode the other user′s message due to reasons such as channel conditions and upper layer protocols.
In this situation, the UCR system can be regarded as a simple collection of individual links. This mode has recently received an intensive investigation in both the basic and system-level research, for example, in [16, 17].
3.1. Capacity Results with Full Knowledge of CQI
Remark 1. A remarkable issue is that ΔC1 in (10) is a monotonically decreasing function of γ11 due to the partial derivative (∂ΔC1)/(∂γ11) < 0. This means that the primary user operating at a high-SNR scenario is less sensitive to the interference. Considering a high-SNR scenario that fulfills the conditions (C1) γ11 ≫ 1, and (C2) γ11 ≫ γ21, (10) approximates to
3.2. The UCR Strategy with Partial Multiuser CQI
Section 3.1 shows that, provided the power P2, the secondary user can employ (4) to configure its transmission rate. However, using (11) or (13) to configure P2 requires the knowledge about , which is supposed to be unknown in some situations. Next, we propose a new power-allocation criterion based on the assumption (A4).
Criterion. The power P2 should be appropriately configured so that the capacity-outage probability of primary user is not larger than a given threshold 𝒪t.
Based on Criterion 1, the power-allocation strategy can be summarized into the following two steps.
Step 1. Outage probability to the primary user is a function of the SNR mean of Tx2-Rx1 link denoted by . Motivated by this fact, the secondary user can first calculate the outage probability for a given p(|a21|2), and then determine a threshold corresponding to 𝒪t.
Step 2. The secondary user can access the primary spectrum for the condition . The maximum of P2 is therefore given by
3.3. Numerical Example
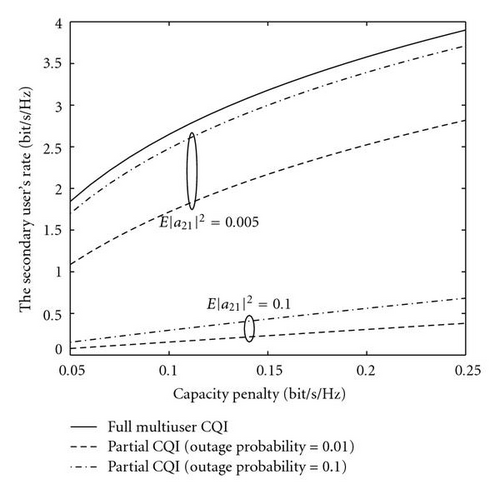
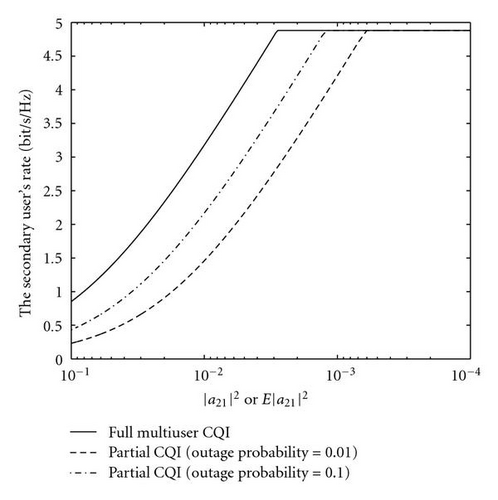
Based on the above analytical results, we use a visual example to exhibit the performance. In this example, the UCR system is configured as |a11 | = 1, |a22 | = 1, |a12 | = 0.1. The primary user′s power-to-noise ratio is P1/No = 16 dB. The secondary user′s power-to-noise ratio is also limited by 16 dB. This ratio is one of typical configurations for high-data-rate systems. For the scenario with full multiuser CQI, we set |a21 | = 0.1. Figure 3 illustrates the secondary user′s achievable rate (see (4)) against the capacity penalty ΔC1 (see (10)) for cases with full or partial multiuser CQI. It is observed that the secondary user′s achievable rate generally increases with the pay of capacity penalty to the primary user. Moreover, in the scenario with partial multiuser CQI, the secondary user shows increased achievable rate for the case of larger outage probability, for example, 𝒪t = 0.1 or smaller E(|a21|2), for example, E(|a21|2 = 0.005). Figure 4 illustrates the secondary user′s achievable rate with respect to the channel quality of Tx2-Rx1 link (ΔC1 = 0.15 bit/sec/Hz). It shows that the UCR approach with partial CQI offers the same performance as the UCR with full CQI when the Tx2-Rx1 channel is deep faded.
4. The SSMD Mode
- (i)
The secondary user knows the primary user′s codebook, and thus has a chance to decode the primary user′s message. This is possible if the primary user is either using a common codebook or broadcasting its own codebook to support, for example, user cooperation. On the other hand, the primary user may be not aware of the existence of secondary user, or does not know the secondary user′s private codebook.
In this situation, the receiver Rx2 can reliably decode the primary user′s message only for the channel condition |a12 | ≥|a11|, otherwise the SSMD mode reduces to the individual decoding mode presented in Section 3. (Multiuser information theory about the interference channel shows that Rx2 can decode the signal X1 if the rate of X1 is not larger than the achievable rate of Tx1-Rx2 link. However, the UCR channel requires the rate of X1 to be constrained only by the achievable rate of Tx1-Rx1 link. In the case of weak interference, the Tx1-Rx1 link offers larger achievable rate than the Tx1-Rx2 link. Rx2 cannot decode X1 if the rate of X1 is larger than the achievable rate of Tx1-Rx2 link.) Therefore, the focus of SSMD mode is on the case |a12 | ≥|a11|.
4.1. Capacity Results with Full Multiuser CQI
4.2. The UCR Strategy with Partial Multiuser CQI
Major difference between the SSMD mode and the individual decoding mode is that the secondary user has improved achievable rate due to the availability of primary user′s codebook. However, on the primary user′s side, there is no difference between these two modes. The spectrum access and power allocation strategy for the SSMD mode should also obey Criterion 1 so as to fulfill the requirement of outage probability. Therefore, the UCR strategy for SSMD mode is the same as that for the individual mode, and the transmit-power P2 is limited by (14). The secondary user′s transmission rate is restricted by the result produced by applying (14) in (21).
Apart from (21), numerical results for the SSMD mode is the same as those for the individual decoding mode. Moreover, (21) is also a well-known result in the domain of multiuser information theory. Therefore, we do not provide a numerical example for this mode.
5. The PSMD Mode
This mode is referred to as a scenario where the secondary user does not know the primary user′s codebook, but share its own codebook through upper-layer protocols. In this case, the primary user has a chance to decode the secondary user′s message, and thus has the potential to cancel the interference caused by the secondary user. On the other hand, the secondary user has to deal with the interference term (a12X1) as noise.
5.1. Capacity Results with Full Multiuser CQI
Theorem 1. Suppose |a21 | ≠ 0 and ρ = 0, the secondary user′s achievable rate is
Proof. For the case of ρ = 0, the results (4) and (23) show that the secondary user′s transmission rate should fulfill
Theorem 1 gives the secondary user′s achievable rate subject to zero capacity-penalty to the primary user. It can be observed that R2 would be almost zero if the channel gain |a21| is deep fade. This result is inconsistent with the original idea of UCR which takes advantage of the case |a21 | ≈ 0. In other words, it is not wise to always target on zero capacity-penalty to the primary user. Below provides two criteria to handle the issue of capacity penalty.
Criterion. The pay of capacity penalty offers improvement of the sum rate of UCR, that is, max (R1 + R2).
Criterion. The capacity penalty is tolerable to the primary user, for example, ρ ≪ 1.
Theorem 2. Suppose the following channel condition:
Proof. The result (23) indicates that the pay of capacity penalty will not improve max (R1 + R2) if the primary user wants to reliably decode the secondary user′s message. Hence, the only case to have an improved max (R1 + R2) is to deal with the interference term (a21X2) as noise, for which R2 is only limited by (25). Moreover, the following inequality has to be satisfied so as to fulfill Criterion 2:
-
(1) For the channel condition (26), Tx2 can talk to Rx2 at a rate (25) without causing capacity penalty to the primary user. The transmit power P2 is limited by the secondary user′s local power constraint.
-
(2) For the channel condition (29), Tx2 can talk to Rx2 at a rate (25). The transmit power P2 is limited by (11) to keep the capacity penalty ΔC1 under an acceptable level.
-
(3) For channel conditions other than (26) and (29), Tx2 can talk to Rx2 at a rate (27) without causing capacity penalty to the primary user. The transmit power P2 is limited by the secondary user′s local power constraint.
5.2. The UCR Strategy with Partial Multiuser CQI
Section 5.1 shows that the spectrum access and power-allocation strategy for the PSMD mode requires the full knowledge of |a21|. Here, we present a new UCR strategy under the assumption (A4). The main idea is summarized as follows.
Define a threshold of probability denoted by ϵ. Based on Theorems 1 and 2, the secondary user will access the primary spectrum for the following three cases.
Case 1. Suppose
Case 2. Suppose
Case 3. Suppose
Finally, for cases other than (31)–(33), the secondary user will not enter the primary spectrum.
5.3. Numerical Example
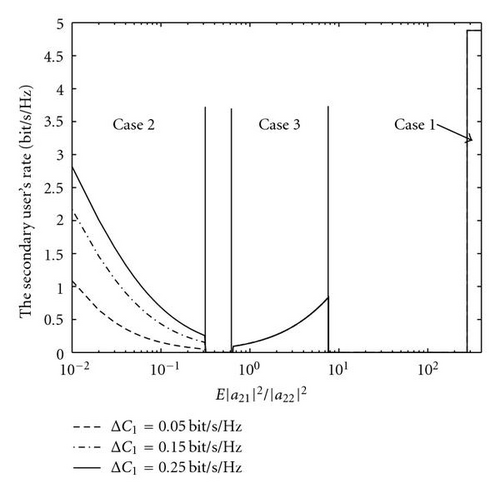
Equations (31)–(33) show that the proposed UCR strategy is based on the statistical relationship between |a21| and |a22|. Considering |a21| to be Rayleigh as a numerical example, we investigate the performance of the proposed approach.
Case 1. The key issue of this case is to find out the relationship between E(|a21|2) and the threshold of outage probability 𝒪t, and then to link this relationship to the spectrum-access strategy. The following result is derived for this issue.
Corollary 1. Given a threshold of the primary user′s outage probability 𝒪t, the condition for (31) to be satisfied is
Proof. We first rewrite (31) into
Case 2. The key issue of this case is to find out the relationship between and the primary user′s capacity penalty and outage probability. The derived result is summarized as below, which offers a criterion to configure the power P2.
Corollary 2. Given a probability ϵ and a threshold of outage probability 𝒪t, the condition for the secondary user to operate in Case 2 is
Proof. The first criterion for the secondary user to operate in Case 2 is (32). Following the derivation in [18], we can easily justify that (32) is equivalent to
Once is determined by employing (38), we can calculate maximum of the secondary user′s power as .
Case 3. This case includes three issues: (1) to find the relationship between E(|a21|2) and ϵ by solving (33); (2) to determine the scaling factor ℒ in (34); (3) provided the condition (33), Theorem 1 shows that the secondary user will suffer capacity outage for the case of |a21|2 > λ1 | a22|2. Then, we should calculate the outage probability to the secondary user. Note that, in Case 3, the primary user does not suffer capacity outage.
Corollary 3. Given a probability ϵ, a necessary condition for (33) to be satisfied is
Proof. See the appendix.
Usually, the probability ϵ is expected to be sufficiently large, for example, ϵ > 90%. In this situation, we can use (40) to obtain γ11 > 15 dB. It means a necessary condition for Case 3 to happen is that the primary user operates in a high-SNR range. Provided the condition (40), the secondary user can employ (A.1) to relate E(|a21|2) to ϵ.
Corollary 4. Given the threshold of outage probability 𝒪1, a necessary condition for Case 3 to happen is (43).
Corollaries 3 and 4 provide an answer to the first two issues of Case 3. The last issue to concern is the probability Pr(|a21|2 > λ1 | a22|2) subject to the condition (33). The result is summarized as follows.
Corollary 5. Provided the condition (33), the probability for the event (|a21|2 > λ1 | a22|2) to happen is smaller than (1)/(γ11 + 1).
Proof. The probability for the event (|a21|2 > λ1 | a22|2) to happen is given in (37), which can be represented into
According to Corollaries 3–5, we summarize Case 3 as follows.
Step 1 .2. Utilize (40) and Corollary 5 to verify whether γ11 fulfills the required condition. if true, go to Step 2.
Step 2. Utilize (43) and (A.2) to verify whether E(|a21|2) is in the appropriate range; if true, go to Step 3;
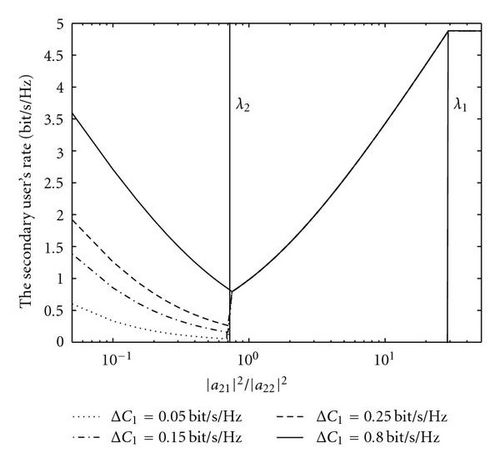
Next, we use a visual example to exhibit the performance. The system configuration is the same as the setup in Section 3.3. For the scenario with full multiuser CQI, Figure 5 shows the secondary user′s achievable rate as a function of the ratio |a21|2/|a22|2. Calculation of the achievable rate follows the conclusion in Section 5.1. For the scenario with partial multiuser CQI, Figure 6 shows the secondary user′s achievable rate as a function of the ratio E(|a21|2)/|a22|2. Calculation of the achievable rate follows the results presented in Corollaries 1–4 by setting the outage probability 𝒪t = 𝒪1 = 10% and the probability ϵ = 90%. It is observed that Case 1 will happen only for the condition E(|a21|2)/|a22|2 > 300, which often does not hold in practice. Case 3 requires the primary user to operate at a SNR larger than 15 dB (see Corollary 3). However, in this case, the secondary user cannot gain more than 1 bit/sec/Hz at P2/No = 16 dB. Finally, Case 2 shows a comparable performance with the corresponding scenario (|a21|2/|a22|2 < λ2) in Figure 5.
6. The TSMD Mode
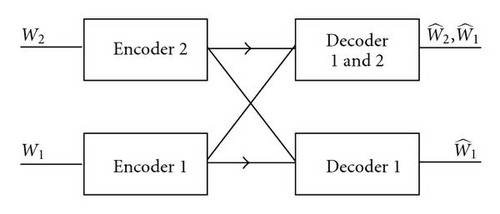
Figure 2(d) depicts the TSMD mode where each user knows the other′s codebook. Then, each user has the chance to decode the other user′s message so as to cancel the interference.
6.1. Capacity Results with Full Multiuser CQI
Capacity theorem about two-user GIC channel [11] has told us that the secondary user cannot reliably decode the primary user′s message for the channel condition |a12 | <|a11|. Hence, for the case of |a12 | <|a11|, the TSMD mode reduces to a special example of the PSMD mode.
6.2. The UCR Strategy with Partial Multiuser CQI
It has been shown in Section 6.1 that the TSMD mode reduces to the PSMD mode for the channel condition |a12 | <|a11|. Therefore, the UCR strategy here is proposed only for the condition |a12 | ≥|a11|.
Case 1 .1. Suppose
Case 2 .2. Suppose
Step 1 .1.2. Utilize (14) to determine max (P2) with respect to a given capacity penalty ΔC1.
Step 3 .3. Calculate the following result which is produced by replacing the term γ21 in (27) with (P2ℒ)/(No) ()
Step 4 .4. Determine the secondary user′s transmission rate via .
6.3. Numerical Example
Considering |a21| to be Rayleigh distributed, we derive the following results for Case 1 and Case 2, respectively.
Corollary 6. A sufficient condition for Case 1 to happen is
Proof. Equation (54) can be straightforwardly obtained through calculation of (49) and Pr(ℒ≤|a21|2) ≤ ϵ.
Corollary 7. A sufficient condition for Case 2 to happen is
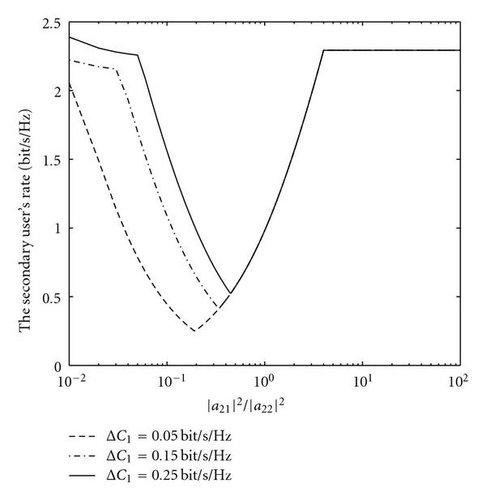
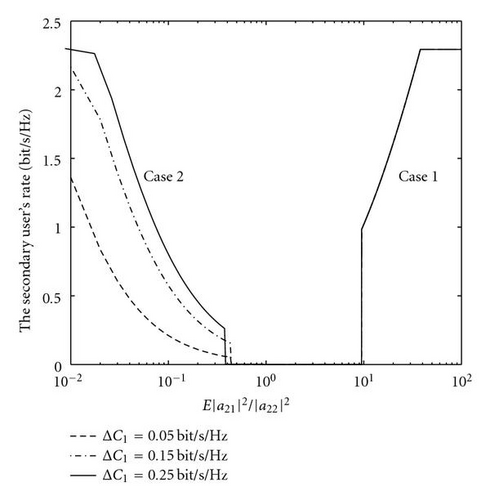
Proof. (55) can be straightforwardly obtained through calculation of (51) and Pr(ℒ≤|a21|2) ≤ ϵ. Figures 7 and 8 show a visual example for scenarios with full or partial multiuser CQI, respectively. The system configuration is almost the same as the setup in Section 3.3, but we set |a12|2 = 4 to fulfill the condition |a12 | >|a11|. For the scenario with partial multiuser CQI, we set 𝒪t = 10% and ϵ = 90% as an example. It is observed that Case 1– Case 2 in Figure 8 offers comparable performance with the corresponding scenario in Figure 7.
7. Conclusion
In this paper, we have investigated two-user Gaussian UCR systems by assuming the availability of full multiuser CQI or partial multiuser CQI. Provided full multiuser CQI, we have studied the fundamental relationship between the secondary user′s achievable rate C2 and capacity penalty to the primary user ΔC1 in four carefully classified UCR modes. For the scenario with partial multiuser CQI, we first established a new physical-layer model through exploitation of the location-aided approach. Then, new spectrum access and power allocation strategies have been investigated in terms of C2, ΔC1, and capacity outage probability. Numerical examples are provided to show the performance of the UCR with full multiuser CQI and the proposed approach with partial multiuser CQI.
Acknowledgments
The authors would like to thank the editor, Dr. Ronald Raulefs, and anonymous reviewers for their extremely constructive and supportive comments. This work has been performed in the framework of the ICT project ICT-217033 WHERE, which is partly funded by the European Union.




