Classifications and Analysis of Caching Strategies in Information-Centric Networking for Modern Communication Systems
ABSTRACT
Information Centric Networking (ICN), a paradigm shift in network design that prioritizes content distribution over host-centric methods, arises in this dynamic environment. Integrating built-in network caches into ICN is essential for optimizing content distribution effectiveness, which raises hit rates, boosts throughput, and lowers transmission delays. This paper provides a comprehensive exploration and classification of ICN caching strategies across diverse domains, including the Internet of Things (IoT), Internet of Vehicles (IoV), Mobility ICN, Edge Computing, and Fog Computing. It further offers a detailed analysis of these strategies based on their proposed methods, identifying key trends, strengths, and limitations. Through a balanced performance assessment, the study evaluates these strategies using critical metrics such as cache hit ratio, efficiency, retrieval latency, security, and throughput. Furthermore, the paper highlights open challenges and presents future research directions to advance caching mechanisms, fostering the continued evolution of ICN for scalable and efficient content delivery for users.
1 Introduction
The traditional address-based communication, grounded in distinctive IP addresses, established the foundation for the host-centric framework of the Internet [1]. However, the advent of content delivery enterprises and streaming platforms, exemplified by entities like Amazon [2], Netflix [3], Prime Video [4], and Disney+ Hotstar [5], in conjunction with prominent social networks such as Facebook [6], Instagram [7], and YouTube [8], swiftly transformed the landscape, marking a new era characterized by content-centric communication. As we delve into the second phase of this evolutionary process, it becomes apparent that content delivery platforms no longer merely serve as basic information channels; instead, they function as catalysts, fundamentally reshaping the essential nature of online interactions within the IP architecture [9, 10]. However, amid these advancements, it is imperative to scrutinize the limitations and challenges that the conventional IP-based internet infrastructure encounters in effectively delivering content, particularly due to network bottlenecks and slow content delivery when catering to large groups of audiences.
CDNs are introduced to address challenges inherent in traditional architecture by integrating replica servers into the distribution process [11]. These strategically positioned replica servers help alleviate network congestion, ensuring more efficient content delivery. However, with the ongoing increase in internet traffic and the growing demand for higher-quality service, implementing CDNs necessitates a substantial financial investment. Deploying these servers and the meticulous planning to ensure optimal locations with sufficient capacity are time-consuming processes [12, 13]. The rapid expansion of network traffic in recent years has led to constraints in the IT infrastructure and a shortage of storage space for existing CDN systems. Moreover, cloud computing provides adaptable resources, showcasing high scalability and the ability to manage extensive data loads [14-16]. This flexibility makes cloud computing an excellent choice for expanding CDNs and optimizing their workloads. However, insufficient attention has been directed toward the challenge of delays for end-users and data congestion when multiple cloud computing resources are concentrated in a single data center [17]. In contrast to conventional methods, P2P solutions have demonstrated significant advantages in content delivery and sharing applications. In P2P, each user contributes their resources to the streaming process. Nevertheless, suboptimal performance is achieved when numerous users simultaneously request data [18-21].
In addressing challenges related to content delivery, researchers are exploring a novel solution known as ICN [22-24]. The initiatives within the ICN framework aim to create an internet architecture that could potentially replace the current dominant IP-centric model. ICN has revolutionized internet architecture by introducing the concept of name-based routing, as Figure 1 shows consumers, producers, and CRs. In this diagram, consumers represent end-users or devices requesting content, while producers are entities that generate or provide content. CRs facilitate content delivery by managing the storage in their cache and retrieval of content objects. Together, these components form the backbone of ICN, reshaping how content is accessed and distributed across networks. In 2007, the DONA [25] proposed flat, self-unique names for information objects with integrated security and persistence features. Since then, various ICN research efforts [26] have emerged, including EU-supported projects like PURSUIT [27], its successor PSIRP [28, 29], and U.S.-backed initiatives like NDN [30] and CCN [31]. Additionally, projects such as MobilityFirst [32] and GreenICN [33] contribute to advancing ICN architecture.

1.1 Research Gap and Motivation
Despite increasing interest in ICN, most surveys focus narrowly on specific aspects of ICN caching. They often lack a comprehensive, cross-domain analysis of caching strategies, limiting their relevance across varied network environments. This results in a fragmented understanding of caching mechanisms and their broader applicability, creating a significant gap in the current body of research.
Caching strategies that work well in resource-constrained IoT environments, where connectivity is intermittent, may not be effective in high-mobility networks like vehicular networks, which require dynamic content distribution due to rapidly changing locations. Similarly, caching approaches optimized for edge computing, which utilizes localized resources and proximity to users, may not be suitable for fog computing, which involves hierarchical distributed computing and demands low-latency access. Therefore, a domain-specific analysis of caching strategies is crucial to fully understand their strengths, limitations, and applicability.
This paper addresses this gap by providing a cross-domain analysis of ICN caching mechanisms across various domains, including IoT, vehicular networks, mobility, edge computing, and fog computing. By exploring and classifying caching strategies within these contexts, the paper offers insights into their strengths and limitations and provides a more integrative assessment of their performance.
1.2 Our Contributions
- The paper emphasizes the core concepts of ICN and provides a classification and analysis of ICN caching strategies.
- The paper explores various caching solutions across multiple domains, including IoT, vehicular networks, mobile ICN, fog computing, and edge computing, systematically assessing their strengths, limitations, and applicability.
- A comparative analysis of existing surveys is conducted, highlighting their contributions and demonstrating how this study broadens the discussion of ICN strategies.
- Performance metrics, including caching efficiency, latency, cache hit rates, network security, and throughput, are analyzed to identify areas for improvement in network performance.
- Finally, the paper identifies open challenges and proposes future research directions, offering insights to advance the field of ICN.
1.3 Paper Organization
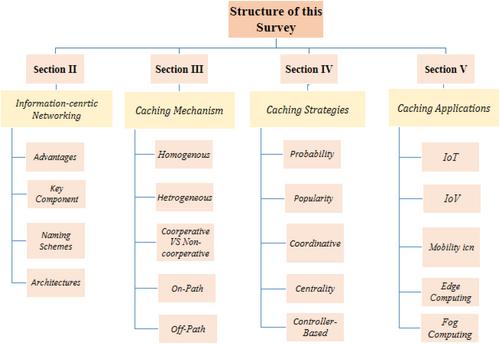
The remainder of the article is organized as depicted in Figure 2: Section 2 provides an in-depth discussion of ICN features, architectures, and naming schemes. Sections 3 and 4 sequentially present the categories of caching, followed by an examination of existing caching strategies. Section 5 explores the role of caching in diverse applications, including IoT, IoV, mobility, Edge computing, and Fog computing. Section 6 conducts a comparative analysis with existing surveys, while Section 7 presents recent research advances on key ICN performance indicators. Sections 8 and 9 discuss future directions and conclude the article, respectively.
2 Information Centric Networking (ICN)
ICN is a paradigm shift in networking where content is accessed by its name rather than its location. This section is organized as follows: firstly, the advantages of ICN are highlighted, showcasing its ability to improve content delivery, enhance security, and enable efficient caching mechanisms. Following this, the key components of ICN, including content-centric routing and in-network caching, are discussed. Lastly, the naming schemes of ICN are discussed, followed by an examination of its architectures to demonstrate the diverse approaches within the ICN framework.
2.1 Advantages
-
Content Centric Routing
Content-centric routing, a core feature of ICN protocols, revolutionizes network architecture by shifting the responsibility of name resolution from the application layer to the network layer [34]. This innovation proves particularly advantageous in fragmented networks, where traditional location-based addressing may falter due to irregular or intermittent connectivity disruptions. For example, in environments without fixed network infrastructure, where connections are ad hoc, ICN's content name-based routing allows content to be replicated based on its name rather than its physical location. This means content can be efficiently distributed without needing servers like DNS resolvers at the application layer.
-
Content-Based Access Management
ICN empowers controlling data access, restricting it to specific users or groups through content-based security measures [35]. This capability enhances secure exchanges among peer users, particularly in remote network regions. For instance, consider a financial institution utilizing ICN. With content-based access management, sensitive financial data can be restricted to authorized personnel only. This ensures that confidential information remains secure and accessible only to those with proper clearance, even in remote branches with limited connectivity.
-
Data Objects Integrity
ICN architecture revolves around named data objects, where various proposals within ICN incorporate the concept of ‘self-certifying data’ into their naming schemes [36]. This involves embedding cryptographic information about the data's origin, enabling authentication without external entities. For instance, in a distributed sensor network utilizing ICN, each sensor could embed cryptographic signatures in its data packets, allowing recipients to verify the authenticity of the data without relying on centralized authentication servers. Consequently, security and reliability are significantly enhanced within ICN architectures.
-
In-Network Caching
In-network caching, a fundamental aspect of ICN, involves storing frequently accessed content strategically within the network infrastructure [37]. This approach effectively handles large volumes of traffic, thereby reducing network congestion. For example, caching at access nodes can mitigate congestion in backhaul links by delivering content from nearby caches.
-
Dynamic Networking
In modern networking, ICN eliminates the need for a continuous end-to-end connection [38]. The characteristic of ICN eliminating the need for a continuous end-to-end connection promotes seamless integration of conventional network setups and fragmented alternatives. ICN enhances data retrieval and distribution by reducing dependency on constant direct connections in traditional, stable network environments, such as home Wi-Fi or LANs. Meanwhile, in dynamic and less stable networks, like mobile or ad-hoc networks in disaster recovery scenarios, ICN allows devices to intermittently connect without disrupting communication. Data can be cached and retrieved from multiple points, ensuring continuous access even when network paths are unstable. This versatility makes ICN a robust solution for various networking challenges, enhancing efficiency and reliability across different network types.
2.2 Key Components
-
Naming
In the realm of ICN, a significant derivation from conventional networking methodologies is observed, particularly in how data is identified and accessed. Unlike traditional networks relying on hierarchical URLs, ICN uniquely assigns identities to data based on their names rather than their physical locations [41]. This shift enables a more versatile and dynamic approach to data retrieval, wherein flat names are frequently utilized to represent data. However, in the earlier ICN architecture, such as CCN, a distinct hierarchical organization of names prevails, enhancing readability and accessibility for users. This characteristic underscores ICN's flexibility, accommodating both flat and hierarchical naming conventions to suit diverse network architectures and user preferences.
-
Caching
Caching is a notable feature in ICN networks, facilitating content storage directly within network nodes. Each content item has the potential to be cached along the delivery route within these network nodes. Consequently, when subsequent requests for the same content arise, it can be efficiently delivered through the caches of these ICN nodes [42]. Implementing in-network caching occurs within ICN nodes between the content consumer and the content producer. This strategic approach not only reduces the workload on the content producer but also enhances data availability. Furthermore, in-network caching is pivotal in balancing load within the network, thereby decreasing content retrieval latency.
-
Routing
Routing in the ICN framework represents a strategic approach to managing numerous requests for the same content originating from a diverse user set. The process adheres to a specific protocol, wherein only the initial request is transmitted to a potential content source, and subsequent requests are systematically recorded and temporarily stored within the memory of the ICN node [43]. When the data is received from the source, it is then disseminated to each requester through the same interface where their original requests were initiated. As a result, ICN can inherently efficiently execute multicast, optimizing content delivery to multiple users.
-
Mobility
In the domain of ICN, mobility remains unaffected by the absence of a fixed connection structure. ICN operates on a model where no established connections exist, meaning that users can move freely without disrupting their access to content [44]. ICN's request-driven approach treats each request independently, allowing seamless content retrieval for mobile users, regardless of their location or when the request is made. This design, crafted for mobility, ensures continuous and efficient data access in dynamic environments.
-
Security
ICN provides robust self-protected security by utilizing encrypted and self-certified content, ensuring that only authorized users can access the content [45]. Unlike traditional methods where the connection between the data producer and the consumer is secured, ICN employs a distinct security approach. In ICN, the content producer incorporates a signature directly into the content. Consequently, consumers and intermediate caching points verify the legitimacy of the content using specific keys published by the content producer.
2.3 Naming Schemes
-
Hierarchical Naming
Hierarchical naming involves the construction of a name by assembling various components to represent an application's function, resembling the structure found in web addresses [46]. This approach simplifies the creation of easily comprehensible names and supports the organized management of many names. Nevertheless, challenges arise when addressing very small entities.
-
Flat Naming
In contrast to hierarchical names, flat names lack inherent meaning or structure. Their unconventional nature makes them less intuitive for people to comprehend, as they don't resemble typical words [47]. These names present difficulties when naming frequently changing entities, as they are not well-suited for new or dynamic content.
-
Attribute-Value-Based Naming
A name based on attributes and values is similar to having a collection of specific details about something [48]. Each detail is associated with a name, a category indicating the type of detail, and a list of potential options (such as creation date, content type, year, etc.). When these details are combined, they form a distinct name for the item and provide additional information about it. This naming system proves beneficial when searching for items using specific keywords. However, ensuring a quick and precise match isn't always straightforward due to the possibility of multiple things sharing the same keywords.
-
Hybrid Naming
A hybrid name involves blending various naming approaches discussed earlier to optimize the network's performance, enhance speed, and ensure information security and privacy [49]. For example, incorporating features from one method can facilitate efficient searches by intelligently combining names; utilizing concise and straightforward names from another method can conserve space, and adding details aids in keyword-based searches while maintaining security. However, crafting these unique hybrid names can be challenging, particularly when dealing with dynamic entities like real-time information.
2.4 Architectures
-
Content Centric Networking (CCN)
CCN is acknowledged as one of the most popular and user-friendly architectures in Information Centric Networking [50]. In CCN, a client initiates an information request within the network by transmitting an ‘INTEREST,’ which travels through a series of routers or nodes. These nodes communicate with their neighboring nodes to locate the requested information. If the desired content is found at any of these nodes, it is then directed back to the requester. Importantly, in CCN's operation, all intermediate forwarding nodes store a copy of the requested data in their memory for potential future requests along the same path. In cases where the content is not discovered along the path, caching occurs at the central server.
-
Data Oriented Networking Architecture (DONA)
The DONA architecture is recognized as a notable platform within the domain of ICN, choosing flat names over hierarchical naming. This architectural choice presents numerous advantages, primarily focusing on the capability to cache information at the network layer. This is made possible through innovative concepts such as autonomous systems and LCD integrated into its design. The use of AS ensures the seamless retrieval of information, even in scenarios where nodes are temporarily unavailable due to mobility, as the information is cached within a node incorporated into the AS.
DONA's robust cryptographic capabilities empower users to authenticate their requests while it still relies on IP and routing addresses at both local and global levels [51]. A pivotal component in DONA is the unique server known as RH, which plays a critical role in resolving names as network operations progress. Integrated into the AS, RHs and routers operate under the network's routing policies.
In DONA, like CCN, data is registered and cached by RHs within the network. When a publisher node wants to make data available, it sends a “REGISTER” message alongside the data to an RH. The RH then stores a copy of this data locally and keeps track of its location. This caching process allows RHs to quickly provide the data to other RHs within the network hierarchy without needing to fetch it again from the original source. By notifying the entire RH hierarchy about the data's availability, DONA ensures efficient data distribution and retrieval across its network segments.
-
Publish-Subscribe Internet Routing Paradigm (PSIRP)
In PSIRP, when subscribers want to access information objects, they send a request to a rendezvous handler. This handler acts as a mediator, facilitating the process of finding and retrieving the requested data [52]. The request travels through the nearest router, which checks if the data is available either in its cache or directly from the publisher node.
At the same time, the publisher node registers the data with its own rendezvous handler. This handler then collaborates with the subscriber's handler to locate a match [53, 54]. Once a match is found, the data is routed through internal routers along the registered path to fulfill the subscriber's request.
-
Network of Information (NetInf)
The NetInf architecture distinguishes itself within the ICN landscape by utilizing a publisher/subscriber model facilitated by the NRS [55]. Subscribers access data by performing ‘look-ups,’ where publishers NDO with specific key attributes. To efficiently manage data transmission, NetInf utilizes the multicast DHT routing algorithm. This approach ensures that consumer nodes consistently receive updated lists of requests. The NRS stations are crucial in optimizing the delivery of NDO, ensuring efficient and reliable information retrieval across the network. The NRS stations play a pivotal role in optimizing the delivery of NDO.
-
Name Data Networking (NDN)
NDN comprises three fundamental components: producers, consumers, and NDN routers. Producers function as content distributors within the NDN framework. At the same time, consumers act as content subscribers, interacting with NDN elements such as CS, PIT, FIB, Faces, and the Forwarding Daemon to fulfill user requests for desired content [56, 57], as specified in Tables 1.
In the NDN architecture, communication occurs through INTEREST and DATA packets, as depicted in Figure 3.
| Functional components | Description |
|---|---|
| CS | The CS serves as a caching mechanism within NDN networks, preserving duplicates of DATA packets that traverse Content Routers. Each record in the CS is linked to a content name and its corresponding payload |
| PIT | The PIT is responsible for tracking and managing received INTEREST packets until the requested data arrives or the entry's lifetime expires. Each PIT entry is distinguished by a name prefix and retains a list of input Faces associated with the received INTEREST packets |
| FIB | The FIB operates as a name-based lookup table, associating each entry with a name prefix and featuring an ordered list of output Faces that specify the subsequent hop for data forwarding. In facilitating multiple paths for data delivery |
| Faces | Faces represent the network interfaces responsible for the transmission and reception of INTEREST and DATA packets. These interfaces can manifest in diverse forms, encompassing direct links between nearby network nodes through Ethernet, overlay communication channels connecting to remote nodes utilizing TCP, UDP, or WebSockets, or interprocess communication channels linking local applications on the same node |
| NFD | The NFD, created by the NDN team, undertake several crucial tasks. It incorporates NDN face abstraction, manages CR tables, implements the forwarding plane supporting various forwarding strategies, and manages the Routing Information Base (RIB), ensuring synchronization of routes in the RIB with the FIB table. The NFD holds a pivotal position in governing NDN network operations |
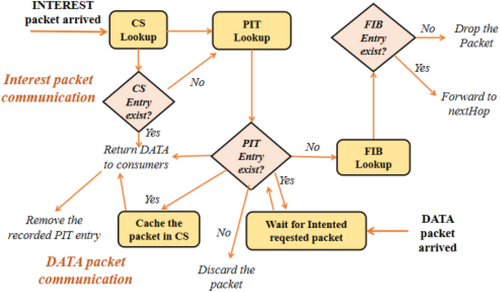
Initially, consumers send INTEREST packets to retrieve data. If the requested data is cached locally, intermediate nodes promptly respond with DATA packets [58]. However, if the data isn't cached, the intermediate node performs a lookup in its PIT. If no entry is found, a new PIT entry is created for the incoming request. Subsequently, the node forwards the INTEREST packet based on the FIB rule corresponding to the requested data name.
On the other hand, when a DATA packet arrives, the content router performs a lookup in its PIT. If a corresponding entry is found in the PIT, indicating that the data is awaited by one or more consumers, the entry is removed from the PIT, and the incoming packet is cached in the CS table. Subsequently, the cached packet is forwarded to the intended requesting consumers, adhering to the corresponding PIT entry. If no entry is found, then the DATA packet is discarded.
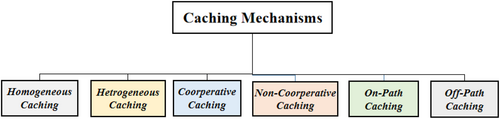
3 Caching Mechanisms
-
Homogeneous Caching
Inhomogeneous caching, content routers named CR1 and CR2 cache DATA packets as they pass by [23], maintaining the same cache size. For instance, both routers concurrently cache content chunks like prefix/c1, prefix/c2, and prefix/c3.
-
Heterogeneous Caching
In heterogeneous caching, not all content routers along the downloading path cache the Data packets. For instance, CR1 caches prefix/c1 and prefix/c3, while CR2 caches prefix/c2 [59]. Meanwhile, within this heterogeneous caching, each content router in the network has a different cache size.
-
Cooperative Caching
In cooperative caching, content routers within a network collaborate with other content routers, establishing cache states to cache and deliver more content chunks [60]. Cooperative caching can be further categorized into explicit cooperation and implicit cooperation. Implicit cooperation does not require content routers to convey cache states through an additional advertisement mechanism. Conversely, explicit cooperation mandates that content routers advertise their cache states to other content routers.
-
Non-Cooperative Caching
In non-cooperative caching, content routers within a network independently make caching decisions and do not share information about cached content with other content routers.
-
On-Path Caching
In on-path caching within a CCN or NDN environment, a DATA packet is cached along its path to the requester. This mechanism involves storing copies of requested content at intermediate routers or nodes situated along the path traversed by the request [61] for the desired content.
-
Off-Path Caching
In off-path caching, the caching of a Data packet depends on whether content routers along the delivery path choose to cache it or not. Off-path caching is feasible even when a centralized topology manager, such as RHs, is in place [62]. The authority to decide the location for caching a Data packet lies with the RH, who then dispatches a copy of the Data packet to the selected content router(s).
4 Caching Strategies
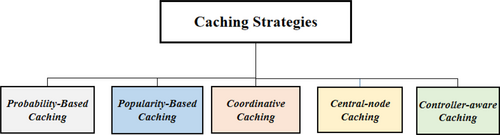
Over the years, various caching strategies have been developed to improve cache hit rates and minimize content retrieval delays. These strategies are typically categorized into Probability Caching, Popularity Caching, Popular-coordinative Caching, Central-node Caching, and Controller-aware Caching [63], as shown in Figure 5. In this section, we provide a detailed classification and analysis of these strategies, highlighting their strengths, limitations, and key challenges. Our analysis aims to evaluate the effectiveness of these strategies, identify key issues, and offer insights into potential solutions for enhancing ICN caching mechanisms.
4.1 Probability-Based Caching
-
CacheFilter
To mitigate data redundancy and support extensive content distribution in the network, the CacheFilter cache placement scheme is introduced in [64]. This scheme incorporates an additional field within the DATA packet known as the flag bit. A flag bit of 0 indicates that the content is already cached by a router within the network, while a flag bit of 1 signifies that the content needs to be cached.
-
Random Caching (RC)
RC is a method wherein nodes selectively cache incoming packets according to a predetermined static probability denoted as “p,” where 0 p 1 as discussed in [65]. The commonly selected value for p is often established at 0.5. This widely adopted value seeks to reduce data redundancy, achieving a balance that mitigates both excessive duplication and underutilization of available resources.
-
Prob(p)
The objective of Prob (p) is to decrease caching redundancy and improve efficiency. In Prob(p), each content router is programmed to cache a data packet with a certain probability, denoted as p in work [66]. Upon the arrival of a data packet at a content router, a random number within the range of zero to one is generated. If the generated random number is less than p, the content router caches a copy of the data packet. Otherwise, the data packet is forwarded without being cached.
-
Probcache and Probcache+
ProbCache incorporates two components in the packet headers: one in the Interest-packet header and the other in the Data-packet header. The ratio between them is denoted as the CacheWeight for specific content. Probcache computes both cache weight and TimesIn, which refers to the sum of time a packet is saved on the caching path, subsequently determining the caching probability at each content router using a defined equation as presented in [67]. A content router with a higher caching probability than others along the path will cache contents. ProbCache+ represents an enhanced version of ProbCache and, similar to ProbCache, calculates TimesIn and CacheWeight at each content router. A content router with a higher caching probability than others along the path will cache contents with greater likelihood.
4.2 Popularity-Based Caching
-
Leave Copy Down (LCD)
The purpose of LCD, as described in [68], is to reduce caching redundancy by introducing a caching proposal flag bit in the header of the data packet. The activation of the flag bit occurs when either the content source or a content router, having a replica of the corresponding content, receives a request. Utilizing this bit, a copy of the intended content is retained at the content router situated one level closer to the requester following each request.
-
Move Copy Down (MCD)
MCD, as discussed in [69], is employed to reduce caching redundancy, similar to LCD. In MCD, a duplicate of the content is transferred to the content router one level closer to the requester following each request.
-
Chunk Caching Location and Searching Scheme (CLS)
CLS, presented as an enhanced version of MCD in [70], aims to improve server workload efficiency. Consequently, CLS adopts a strategy where only a single replica of a chunk is maintained along the pathway connecting a server and a requester. Upon receiving a request, the chunk's copy moves one level closer to the requester. Conversely, during cache eviction, the chunk moves one level towards the server.
-
Chunk-Based Caching Scheme (WAVE)
The WAVE in the CNN framework is introduced by [71]. In this placement scheme, data packets are divided into uniform, fixed-sized fragments or chunks, which are then distributed across the network. WAVE's strategy combines the evaluation of content popularity and inter-chunk relationships as key factors in determining which content to cache. It strategically decides which specific chunks to cache based on the popularity of the content and the relationships between different chunks within the same content.
-
Most Popular Content (MPC)
A caching scheme called MPC was presented in [72]. This novel method entails edge devices actively monitoring and recording the frequency of requests for specific content names. These devices maintain a Popularity Table, essentially serving as a local repository that records the popularity metric for each content item. As the request counts accumulate, content names surpassing a fixed Popularity Threshold are recognized as popular. Once a content name attains this status, the hosting node for that content triggers a suggestion mechanism. This mechanism entails recommending neighboring nodes to cache the recognized popular content.
-
Dynamic Fine-Grained Popularity-Based Caching (D-FGPC)
Reference [73] has introduced an extended version of MPC named D-FGPC. D-FGPC incorporates a flexible popularity threshold function, determined by both the frequency of received INTEREST and the available cache capacity. Integrating this dynamic threshold function enhances the adaptability of the caching strategy employed by D-FGPC.
-
Popularity-Aware Closeness Caching (PaCC)
The goal of PaCC, as introduced by [74], is to systematically manage caching decisions by using the ‘PaCC’ field in the DATA packet. This aims to ensure efficient forwarding of content by identifying and utilizing the optimal router or node based on factors such as popularity and network characteristics, including hop distance.
-
Dynamic Popularity Cache Placement DPCP Scheme (DPCP)
The DPCP, as proposed in [75], is designed to manage the caching of data packets at a node efficiently. Upon the arrival of a data packet, a popularity calculation mechanism is triggered. This calculation incorporates the content's historical popularity in the last cycle and factors in the total number of requests in the current cycle. The DPCP scheme dynamically adjusts the threshold size through the AIMR algorithm, considering the current space occupation. Only content surpassing the current popularity threshold is cached, and the system strategically prioritizes the caching of content with a high probability of future requests.
-
Caching Popular and Fresh Content (CPFC)
The proposed CPFC caching decision scheme is introduced by [74]. It is a systematic approach for (CR) to manage the content cache effectively. Two significant metrics are employed by each CR: the Popularity metric, consisting of content prefixes and their corresponding request counts, and the Freshness metric, including content names and their respective lifetimes (times during which the content remains valid).
-
Two Layers Cooperative Caching (TLCC)
In the context of TLCC, as described in [76], CCN routers are grouped into Upper-Layer Group (ULG) and Lower-Layer Group (LLG) within an Autonomous System. CDULG caches received chunks based on hash comparison with the router's key range, while CDLLG caches chunks if the Local Popularity Count exceeds a threshold and the hash matches the router's key range.
-
DeepCache
Introducing the DeepCache framework in [77], highlighting the efficacy of LSTM-based models in predicting content popularity. The research addresses content popularity prediction as a seq2seq modeling problem and introduces the LSTM Encoder-Decoder model, a novel approach. Additionally, the DeepCache framework is presented for end-to-end cache decision-making.
4.3 Central-Nodes Based Caching
-
CRCache
Reference [78] introduced a caching placement scheme called CRCache. This approach involves making caching decisions by considering a comprehensive popularity metric determined by assessing the frequency of received INTEREST. This metric is thoughtfully combined with identifying popular routers within the network topology. Notably, routers with superior distribution are marked as popular routers in the CRCache scheme.
-
Edge Caching
Edge caching strategically places content closer to users by storing it in the latest content router along a distribution pathway, as introduced by [79]. The goal is to minimize the number of hops required to access a content source, resulting in reduced time for content delivery and decreased network traffic caused by the transmission of content requests.
-
BEACON
To optimize network resources, a betweenness-centrality-based content placement scheme called BEACON, introduced by [80], employs a time series Gray model to predict which content to cache and where to cache it.
-
Content Betweenness Centrality (CBC)
The objectives of CBC, as detailed in [81], aim to minimize the latency associated with content delivery, mitigate traffic and congestion through an increased cache hit rate, and simultaneously reduce server load. CBC indicates the betweenness centrality exhibited by each content router within the network. In this context, data packets are strategically stored at the content router deemed ‘important,’ showing the highest betweenness centrality rate along the delivery path.
-
Content Selection and Router Selection (CaRS)
Reference [82] proposes a CaRS caching strategy for network devices aimed at balanced content distribution. It selects cached contents based on Zipf's law, and to balance content distribution, routers monitor neighboring cache status using parameters like proportionate distance from the consumer, router congestion, and cache status.
-
Link Congestion and Lifetime Based In-Networking Caching Scheme (LCLCS)
The main purpose of LCLCS is to maintain an acceptable cache rate and notably optimize network delay. The LCLCS process, defined in [83], begins with a network analysis to identify ‘important’ content routers along the content delivery path. Subsequently, LCLCS utilizes the computed lifetime to make decisions regarding the eviction of currently cached content, ensuring adequate space for caching incoming content.
4.4 Controller-Aware Caching
-
Deep Learning-Based Content Popularity Prediction (DLCPP)
DLCPP, detailed in [84], proposed an auto-encoder-based popularity model implemented over the SDN controller to predict content popularity. It collected the data from the routers having spatial-temporal correlation to represent the flow of requested content at discrete intervals. Finally, a softmax classifier is employed to predict the popularity of content. Further, for popular placement, SDN selects a set of important routers with the help of the betweenness centrality approach.
-
Controller-Aware Secured Content Caching (CaCC)
CaCC, presented in [85], utilizes programmable switches with four key modules: “PARSER,” “CS,” “PIT” and “FIB,” and “Encryption and Decryption.” The CS module comprises an index list storing encrypted IDs of cached content and a CS server for storing the actual data, both stored in registers. Upon an INTEREST packet's arrival, the switch checks the index list for a match. If found, it retrieves the corresponding data from the CS server; otherwise, it checks the PIT entry. If no entry exists, it forwards the INTEREST packet following the FIB route, encrypting it before transmission. Upon receiving a DATA packet, it decrypts it and matches the content prefix with the PIT. If a match is found, it caches the content to the CS server and delivers it to a set of users simultaneously.
-
Centralized-Based Dynamic Content Caching (CDCC)
The paper [86] employed a CDCC caching scheme in which a heuristic algorithm utilized within the SDN controller plays a pivotal role in the efficient selection of cacher groups tasked with storing both popular and time-sensitive content. This method not only optimizes the allocation of caching resources but also enhances the overall performance of content delivery networks within dynamic network environments.
-
Centrality Content Caching (CCC)
CCC scheme, presented in [87], optimizes content caching across autonomous systems. The controller strategically determines optimal paths and installs them in forwarding devices. When an INTEREST packet reaches a CR, it checks its CS table. If no match is found, the CR consults its CIT for cached content within the autonomous system. If found, the request is directed based on the FIB route. Otherwise, it's forwarded to the controller, which verifies its CIT table for content information across systems. The controller sends the content if a match is found; otherwise, the request is redirected to content producers.
4.5 Coordinative Caching
-
ICC
ICC is a caching approach, presented in [88], designed for DONA, focusing on inter-domain cache cooperation, contrasting with intra-domain cache cooperation. In DONA, RHs can cache incoming DATA packets but don't share availability information with other RHs. ICC enhances cached content availability by having RHs advertise this information to their peering domains.
-
LCC
LCC, detailed in [89], is a hash-based caching mechanism for inter-domain cooperation. It hashes content names to unique content routers within a domain, effectively mapping content to selected routers for caching. A redundancy control scheme is introduced wherein domains coordinate with neighbors to determine cached content preferences.
-
Intra-AS Co
Intra-AS Co aims to minimize caching redundancy by enabling neighboring content routers to access cached content defined in [90]. Each content router maintains a Local Cache Content Table (LCCT) and an Exchange Cache Content Table (ECCT). The LCCT records content chunks cached locally, while the ECCT records content cached by neighboring routers. Additionally, content routers periodically share their local cache content information with directly connected neighbors.
-
Distributed Cache Management (DCM)
The purpose of DCM in work [91] is to maximize the traffic volume served from the caches. By DCM principles, a CM is installed to facilitate the exchange of cache states with other CMs. The determination of cached content placement and replacement depends upon the distributed online cache management algorithm employed by the CM.
-
CATT
CATT caches a Data packet at a single node along the downloading path within every network as discussed in [92]. Additionally, CATT introduces the content's expected quality to aid content routers in forwarding Interest packets. When content is cached or stored at a content router, its expected quality at that router is considered. Conversely, if the content is not cached at a content router, the expected quality at that router is Hop+1 calculated.
Summary and Lesson Learned
In Table 2, we have summarized the caching decision principles of various caching strategies. In the table, each strategy is categorized into its designated caching mechanisms, as previously discussed. The table provides a brief description of the decision mechanism for each strategy and highlights the key objective of each study. This structured overview enables a clear understanding of the different approaches to caching, facilitating easier comparison and analysis of their respective benefits and limitations.
| References | Method name | Caching strategy | Caching mechanism | Objectives | Limitations |
|---|---|---|---|---|---|
| [93] | CEE | Redundancy-driven | Homogeneous, cooperative, & on-path | Determine which demanded content aligns with the preferences of requesting users | Subjected to data duplication and limited content diversity |
| [67] | PopCache | Probability-driven | Heterogeneous & on-path | Assess the effects of attaching probabilities (0-1) to NDN packet arrivals | Suboptimal performance in cache hit rate due to static probability threshold |
| [71] | WAVE | Popularity-driven | On-path, implicit, & heterogeneous | Examine WAVE's caching strategy for popular content chunks and inter-chunk distances | WAVE may inefficiently utilize cache due to limited adaptability to popularity shifts and network changes |
| [64] | CacheFilter | Probability-driven | Non-cooperative | Enhance network performance by selectively caching desired content, optimizing content distribution efficiency | CacheFilter's static flag bit reliance may limit adaptability to dynamic content, affecting cache efficiency and content distribution |
| [72] | MPC | Popularity-driven | Cooperative, homogeneous, & on-path | Each node locally maintains the popularity table to decide whether to cache the requested content or not | Dependence on accurate popularity thresholds may lead to inefficiencies in cache utilization |
| [73] | D-FGPC | Popularity-driven | Implicit cooperation, & on-path | Employed the topological features in order to make the content caching decision | Experienced significant delays in content retrieval due to the router's low proximity to the requested users |
| [78] | CRcache | Central nodes-driven | On-path, & cooperative | Determine the selection criteria for important routers based on their content distribution power | Increased the average hop count because of caching on central nodes that could be distant from the consumers |
| [74] | PACC | Popularity-driven | Homogeneous, cooperative, & on-path | Assess the effectiveness of the closeness-aware metric based on provider hop-count distance from requesting users | It is a computationally expensive approach due to required updates at each forwarding node to determine the closeness-aware cacher |
| [80] | BEACON | Central nodes-driven | Implicit cooperation, & on-path | Study the correlation between request rate and discrete content arrivals for selecting popular content at CRs | Because of disregarding the historical records in the process of selecting popular content, a low cache hit rate was observed |
| [75] | DPCP | Popularity-driven | On-path, & cooperative | Evaluate the effectiveness of caching based on an exponential weighted moving average (EWMA) statistical distribution | DPCP does not identify the optimal placement for the most popular contents |
| [88] | ICC | Coordinative driven | Explicit cooperation, & on-path | Investigate the efficiency of inter-domain cache advertisement mechanisms to improve content availability | Scalability and coordination issues may arise in ICC due to inter-domain cache cooperation |
| [74] | CPFC | Popularity-driven | Cooperative, on-path, & homogeneous | Explore the relationship between popularity and freshness thresholds in content caching decisions | Suffered from a high cache miss rate due to the utilization of a fixed freshness threshold for making caching decisions |
| [87] | CCC | Controller-driven | Explicit, & on-path | Assess the impact of popularity tables on caching efficiency and content availability in distributed networks | No mechanism is designed to measure the optimal placement for each piece of content |
| [63] | CNIC | Coordinatively driven | Off-path, & heterogeneous | Investigate the effectiveness of coordinating with neighboring content routers to enhance content chunk delivery | Incurs computational and management issues due to operating in a distributed manner |
| [94] | PDPU | Popularity-driven | Explicit cooperation, & on-path | Assess the effectiveness of moving requested content one step closer to intended users as demand increases | Increases the average hop count due to the provider's distance from the content consumers |
| [85] | CaCC | Controller-driven | Heterogeneous, & explicit | Assess the efficacy of maintaining Hash-ID tables for popular content items in each mode | Constant encryption/decryption can cause latency, especially in high traffic |
| [82] | CaRS | Central nodes-driven | Cooperative, & homogeneous | Assess the efficacy of dynamic caching selection for achieving balanced content distribution in network devices | Scalability may be constrained by the computational burden of monitoring neighboring cache status |
- Note: This table summarizes various caching strategies, outlining their strengths and weaknesses based on their caching decision principles.
Based on our survey and comparative analysis, we have reached the following conclusions. Feng et al. [64], Laoutaris et al. [67], and Tarnoi et al. [65] employ probability-based caching strategies. However, due to the static probability threshold that remains unchanged over time, these strategies fail to adapt to the changing demands of users, resulting in a lower cache hit rate. Consequently, this limitation leads to decreased efficiency in resource utilization and may impact overall system performance. Additionally, a lower cache hit rate can lead to increased network retrieval delays and higher user access times.
Li et al. [71], Bernardini et al. [72], Ong et al. [73], and Zha et al. [75] have presented popularity-driven caching strategies, which make caching decisions based on user preferences. However, these strategies rely on single-variable-driven content popularity prediction, which may not efficiently capture the nuanced dynamics in user demands over time. This limitation can result in suboptimal caching decisions and reduced effectiveness in meeting user expectations for timely access to relevant content.
Wang et al. [78], Amadeo et al. [80], and Lal et al. [81] have introduced centrality-based caching strategies, where content is cached on high central nodes in the network. However, a potential drawback arises when the central node is distant from the user, leading to increased network retrieval delays. This limitation can degrade the overall user experience by prolonging access times for requested content, resulting in decreased user satisfaction and potentially higher miss rates.
Wu et al. [88], Wang et al. [90], and Eum et al. [92] have introduced coordinated caching strategies, where nodes make caching decisions based on their neighbors' status. However, this approach is vulnerable to several challenges, including manual configuration, scalability issues, and computational overhead. In NDN, entities operate in a distributed manner, requiring manual management of network configuration and flow rule creation. These complexities and potential drawbacks associated with coordinated caching strategies in NDN environments can increase network delays and impact overall efficiency.
Liu et al. [84], Ruggeri et al. [86], and Asmat et al. [87] have presented controller-based caching strategies, where nodes make controller-driven, different popularity algorithms-based caching decisions. However, there is no mechanism designed for this dynamic environment to select strategic placements for caching. This lack of a mechanism increases delays in the network and impacts the efficiency of the system.
5 Caching Applications
Caching is a fundamental technique in modern communication systems, optimizing performance by storing frequently accessed data at or near retrieval points. This approach minimizes latency, enhances throughput, and improves overall system responsiveness. To explore the relevance of caching, this section examines various caching strategies used across different applications (see Figure 6). These strategies rely on ICN frameworks, Machine Learning and Deep Learning models, and optimization techniques. The strengths and limitations of these approaches will be analyzed within the context of caching systems, with a particular focus on their methodologies.
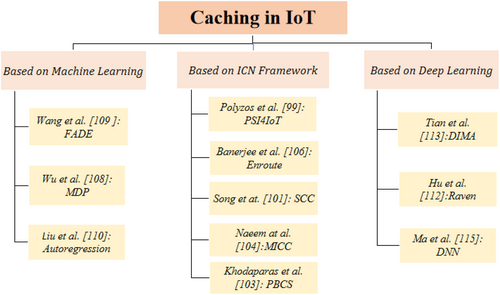
5.1 Internet of Things (IoT)
-
Caching Frameworks Based on ICN Networking
Polyzos et al. [97] present Publisher-Subscriber-Integration for IoT (PSI4IoT), an architecture based on the ICN paradigm, designed to enhance data management and security. The architecture employs an Access Control Provider (ACP) framework to ensure secure authentication and authorization, allowing only authorized users to access protected data. PSI4IoT integrates Proxy Re-Encryption (PRE) for secure data storage, where the device encrypts the data, which is stored with a designated publisher, and a Key Server re-encrypts it for the subscriber, ensuring the device's private key remains secure. Additionally, Hierarchical Identity-Based Encryption (HIBE) guarantees the integrity and verifiability of cached data. Together, these mechanisms optimize content caching, reduce latency, and improve the overall efficiency of IoT ecosystems.
Kurita et al. [98] proposed the Keyword-Based Content Retrieval (KBCR) architecture, which enhances the ICN paradigm for IoT applications. KBCR uses caching nodes to distribute requests based on keywords, initiating a search for relevant data across the network. Multiple responses are then aggregated into a single response, reducing redundant message transmission and improving content retrieval efficiency. This method minimizes latency, reduces network congestion, and enhances performance, making it ideal for resource-constrained IoT systems. Unlike NDN, which requires multiple request messages, KBCR sends a single request that is distributed and merged at intermediate nodes, significantly reducing the number of messages exchanged. Simulations show that KBCR outperforms NDN in large-scale networks, improving response time and scalability while requiring minimal additional processing for message merging.
Song et al. [99] proposed the Smart Collaborative Caching (SCC) scheme to improve the efficiency of information-centric IoT systems by tackling key challenges such as content storage, resource sharing, and node localization. This approach leverages the capabilities of ICN to streamline processes like cluster composition, content management, and position tracking through core actions, including caching, finding, joining, and leaving, all supported by specialized algorithms. Comparative evaluations against traditional methods, such as IP networks and ICN flooding, highlighted SCC's ability to significantly lower packet volume and transmission latency, especially in larger networks. Unlike ICN flooding, which generates excessive traffic and inefficiencies, SCC offers a more controlled and effective solution, reducing congestion and enhancing content retrieval. These advantages position SCC as a highly effective approach for scalable IoT applications.
Hua et al. [100] propose a novel caching design scheme characterized by three key innovative attributes. First, it introduces a Cluster-Based Approach (CBA), which leverages both in-network and end-user devices to cache content closer to the network edge, thereby optimizing content delivery as demand increases. Second, the scheme employs a Near-Path Approach (NPA), strategically positioning caching nodes along delivery paths to minimize latency and enhance retrieval efficiency. Finally, it integrates Reactive and Proactive Caching techniques (RPC) that work together to alleviate network congestion during peak periods. Simulations demonstrate that this design significantly enhances internal link load and path stretch metrics, outperforming eight popular benchmark techniques.
Khodaparas et al. [101] introduce a Pull-Based Caching Scheme (PBCS) aimed at improving content retrieval efficiency in IoT environments. In this method, nodes process data, extract key characteristics, and store the aggregated results locally via the cluster head (CH), instead of directly relaying data to cloud servers. The cached content is kept until its lifetime expires or a request is made, thereby reducing unnecessary transmissions and minimizing power consumption. By enabling local retrieval, the scheme significantly lowers latency compared to fetching content from the cloud. Simulation results show that PBCS increases cache hit rate by 40%, reduces retrieval time, lowers energy consumption, and enhances response times.
Ali Naeem et al. [102] introduce the Most Interested Content Caching (MICC) strategy for NDN-based IoT applications, aimed at improving content dissemination. MICC employs a time-based caching approach and utilizes the intuitionistic fuzzy mode (IFM) to dynamically adjust caching locations based on content interest frequency. Each router tracks content interest, optimizing caching performance metrics such as cache hit ratio and content eviction ratio. Simulations demonstrate that MICC outperforms other strategies like PCS, CCAC, and MPC in content retrieval efficiency, making it a promising solution for enhancing IoT and smart city performance.
Abkenar et al. [103] propose the Distributed Smart Clustering Caching Protocol (DSCCP) to enhance QoS in cache-enabled IoT networks. The protocol employs a smart clustering mechanism that enables Fog Nodes (FNs) to cache content locally based on channel conditions, reducing reliance on Central Nodes (CNs). By selecting optimal destination nodes for processing requests within service delay constraints, DSCCP effectively balances network delay, energy consumption, and overall benefit. Its novelty lies in maximizing network efficiency through intelligent clustering and local caching, outperforming traditional caching methods in responsiveness and resource optimization.
Banerjee et al. [104] proposed the ENROUTE algorithm, which integrates entropy-based techniques with caching to enhance content distribution in ICN. The algorithm uses entropy (EA) as a measure of link congestion and the condition of on-path caches, thereby optimizing routing and caching decisions. Nodes with higher entropy values store more popular content, while links with higher entropy are considered more congested. By improving cache entropy and selecting paths with lower entropy, the algorithm reduces delays and increases throughput. Simulation results demonstrate improvements in delay, cache hit rate, and throughput. Future research will focus on further refining content routing and caching strategies using entropy.
-
Caching Approaches Based on Machine Learning
The integration of ML-based models in IoT environments leverages predictive analytics to intelligently manage data storage and retrieval, optimizing resource utilization, enhancing system responsiveness, and enabling efficient real-time decision-making. Xiaoming et al. [105] present a Reinforcement Learning (RL) model specifically designed for edge-enabled IoT environments. This model addresses key challenges such as transmission latency and storage costs, aiming to maximize the Quality of Experience (QoE) by balancing content-centric caching quality with user satisfaction. Through its intelligent design, the model significantly improves resource utilization, system responsiveness, and real-time decision-making, demonstrating its potential to enhance IoT operations.
Wu et al. [106] propose a dynamic caching strategy that utilizes user request queues to optimize content delivery. They introduce a queue-aware cache update scheduling algorithm based on the Markov Decision Process (MDP), which aims to minimize the average Age of Information (AoI) delivered to users while accounting for content update costs. Additionally, they present a low-complexity suboptimal scheduling algorithm. Simulation results demonstrate that their approach significantly reduces the average AoI compared to existing strategies that do not incorporate user request queues.
Wang et al. [107] introduced the Federated Learning-based Cooperative Edge Caching (FADE) framework for IoT applications as a solution. This framework aims to enable fast training by decoupling the learning process from cloud-stored data in a distributed-centralized manner, allowing data training to occur on local User Equipment. By incorporating intelligent caching strategies, FADE optimizes the storage and retrieval of frequently accessed data at the network edge, reducing latency and improving response times. In terms of security and privacy, FADE ensures that sensitive data remains on local devices, minimizing data exposure to centralized servers, and leveraging federated learning to preserve user confidentiality. Trace-driven simulations show that FADE significantly outperforms the centralized DRL algorithm, demonstrating notable performance improvements.
Liu et al. [108] introduce an Auto-Regressive (AR) model tailored for IoT environments, supported by detailed mathematical derivations to highlight its effectiveness. By employing the least squares method, they develop a content popularity prediction model that accurately tracks trends in content popularity, enabling more efficient caching strategies in IoT networks. Simulation results confirm the model's effectiveness, showing notable improvements in cache hit ratios, reduced network traffic, and decreased content retrieval delays.
-
Caching Approaches Based on Deep Learning
The development of DL-based caching solutions for IoT represents a major advancement in optimizing caching efficiency and resource utilization within IoT environments. Zhang et al. [109] present an innovative approach that combines Deep Reinforcement Learning (DRL) with cooperative edge caching to address challenges related to varying data item sizes. The proposed method utilizes the Multi-Agent Actor-Critic (MAAC) algorithm to facilitate collaboration among edge servers, optimizing the caching process. This collaboration enables edge servers to efficiently manage and distribute content, resulting in improved cache hit rates and overall system performance. Simulation results demonstrate the approach's effectiveness, with significant improvements in cache hit rates and system efficiency compared to traditional caching algorithms.
Xinyue et al. [110] introduce Raven, an innovative learning-based caching framework inspired by the optimal Belady algorithm. Raven employs a Mixture Density Network (MDN) to learn the distribution of object arrival times without relying on prior assumptions, allowing for a probabilistic approximation of Belady's algorithm. The framework adapts its cache eviction decisions to the unpredictable and dynamic nature of object arrivals, taking into account factors such as randomness, time-dependent fluctuations, and the absence of fixed arrival patterns. Simulation results demonstrate that Raven outperforms existing algorithms by improving object hit ratios, reducing average access latency, and minimizing traffic to origin servers.
Tian et al. [111] introduce DIMA, a Distributed Intelligent Microservice Allocation scheme. DIMA equips each IoT device with a DRL agent, specifically a D3QN agent, along with a replay buffer. This setup enables the devices to make independent decisions on optimal caching and microservice replacement through interactions with the environment. Simulations demonstrate the effectiveness of DIMA, highlighting its superiority over existing baseline approaches. This innovative solution shows great potential for optimizing microservice caching in dynamic environments, leading to improved performance and resource utilization in IoT ecosystems.
Xu et al. [112] propose a Deep Q-Learning (DQL)-based approach in a software-defined model that integrates computing and caching functionalities. In this model, controllers manage resources from ICN routers and Mobile Edge Computing (MEC) gateways. Traditional algorithms struggle with the high complexity and dimensionality of the problem, as well as the challenge of balancing immediate and long-term rewards. The DQL-based joint optimization approach outperforms other schemes by increasing rewards and efficiently managing resource scheduling, even in dynamic network conditions. It demonstrates superior convergence, faster loss reduction, and more effective decision-making compared to methods that focus solely on caching or computing resources, highlighting the advantages of DQL within the IC-IoT framework.
Ma et al. [113] propose a dynamic caching scheme that leverages Neural Networks (NNs) to optimize content updates in Heterogeneous Networks. The scheme incorporates a queue-aware cache content update scheduling algorithm designed to minimize the average AoI for dynamic content delivery. By utilizing user request queue data, the method predicts and prioritizes the delivery of various dynamic content, ensuring timely and efficient updates. Unlike existing algorithms, the proposed framework anticipates user demands with greater accuracy, thereby improving responsiveness and operational efficiency. Comprehensive evaluations demonstrate that this approach significantly reduces AoI and enhances the overall performance of dynamic content caching systems.
Zhang et al. [114] introduce a dynamic content importance-based caching scheme (D-CICS) that selects and replaces content based on factors like modal type, popularity, size, and network conditions. Unlike traditional methods that focus solely on popularity, D-CICS uses a real-time evaluation model based on Deep Reinforcement Learning with Double Q-Learning (D3QN) to assess the importance of multi-modal content. The scheme incorporates lightweight caching and replacement policies that are specifically tailored for dynamic networks. By efficiently replacing and evaluating content, this approach reduces the risk of unauthorized access or misuse by minimizing unnecessary data transfers and ensuring that only relevant content is cached. This helps mitigate the exposure of sensitive information, thereby enhancing both the security and privacy of the system by limiting the exposure to authorized content only.
-
Caching Approaches Based on Optimization Applications
Weerasinghe et al. [115] introduced ACOCA, an optimization approach specifically designed for IoT ecosystems to maximize the cost and performance efficiency of Context Management Platforms (CMPs). ACOCA addresses the challenge of efficiently selecting context for caching while managing the additional costs associated with context management. It employs a scalable and selective agent for caching context, implemented using the Twin Delayed Deep Deterministic Policy Gradient (TD3) method. Additionally, ACOCA integrates adaptive context-refresh switching and time-aware eviction policies. A comparative analysis demonstrates ACOCA's superior performance in both cost and performance efficiency, establishing it as a promising optimization solution for IoT ecosystems (Figure 8).
Summary and Lesson Learned
Table 3 provides a summary of the various caching frameworks or algorithms implemented in IoT applications, along with an overview of the caching mechanisms used in each study. It offers a concise description of the decision-making processes for each IC-IoT framework and outlines the primary objectives of the respective studies. This structured summary enables a more straightforward understanding of the different caching strategies and facilitates easier comparison and analysis of their advantages and limitations.
| References | Method name | Caching mechanism | Objectives | Limitations | Category |
|---|---|---|---|---|---|
| [97] | PSI4IoT | Cooperative, & on-path | Investigate IoT security, emphasizing access control, secure proxies, and trust in ICN architectures | Challenges in ensuring compatibility with diverse IoT devices and protocols | ICN |
| [98] | KBCR | Cooperative | To enhance efficiency in IoT environments by aggregating multiple responses into a single response with the KBCR network approach | KBCR's keyword-based retrieval may expose sensitive information, highlighting the importance of secure dissemination to prevent unauthorized access or manipulation | ICN |
| [99] | SCC | On-path, & cooperative | Aimed at focusing on effectively managing increasing IoT device counts and fluctuating data transmission levels with the smart collaborative caching scheme. | SCC's scalability may be limited by coordination and communication overhead as device participation increases | ICN |
| [100] | CBA, NPA, & RPC | Explicit cooperative, & on-path | Implementing a cluster-based scheme to cache content closer to the edge network, leveraging both in-network and end-user devices | Affected by dynamic IoT network conditions, including demand shifts, device mobility, and topology changes, influencing caching and congestion strategies | ICN |
| [107] | FADE | Implicit cooperative | Decentralize the learning process from cloud-stored data and enable local data training on user equipment | Dependency on trace-driven simulations may limit the generalizability of FADE's performance to real-world IoT environments | Machine learning |
| [111] | DIMA | Implicit, & heterogeneous | Optimize microservice caching in dynamic environments by empowering each IoT device with a D3QN agent for independent caching decision | Training deep Q-networks in distributed settings may be computationally intensive and time-consuming | Deep learning |
| [112] | DQL | Implicit cooperative | Maximize efficiency by integrating computing and caching functionalities through optimized resource scheduling | Implementing joint resource scheduling in IC-IoT may face challenges with variable data and computational demands | Deep learning |
| [101] | PBCS | Non-cooperative | Optimize caching at cluster heads to reduce transmissions, power usage, and latency, boosting cache hits and cutting retrieval time | The cluster head reliance introduces failure points, affecting caching during hardware failures or unavailability | ICN |
| [102] | MICC | Explicit cooperative, & heterogeneous | Enhance content dissemination by strategically caching content based on interest frequency, using a time-based deployment strategy | Limited adaptability to rapidly changing interest frequency patterns may hinder MICC's effectiveness, potentially leading to suboptimal cache utilization | ICN |
| [104] | EnRoute | On-path, & implicit cooperative | The aim of integrating entropy-based techniques into caching and content routing is to improve delay reduction and enhance throughput during content delivery | Inaccurate entropy data may limit optimal caching and routing strategies, impacting content delivery efficiency | Machine learning |
| [112] | DQL | Implicit, & on-path | To enhance QoE in edge-enabled IoT environments through optimized content-centric caching and user experience | The computational complexity and resource requirements of deploying deep Q-learning in IoT networks may limit its adoption and scalability | Deep learning |
| [115] | ACOCA | Cooperative, & on-path | Aiming to maximize both the cost and performance efficiency of a Context Management Platform (CMP) in near real-time | ACOCA's effectiveness may be limited by data item variability, impacting caching decisions | Optimization technique |
| [110] | Raven | On-path | Optimize cache eviction decisions using a Mixture Density Network, with the aim of outperforming existing algorithms in production workloads | Training and maintaining the Mixture Density Network incurs computational overhead, limiting its scalability in high-throughput caching environments | Deep learning |
- Note: This table summarizes various caching strategies in IoT, along with their objectives and limitations.
IoT caching strategies employ various methods to enhance system performance and improve user experience. Based on our review and analysis, we conclude that scalability is a major challenge for IoT-based caching approaches, especially as networks expand in size and complexity. As the number of devices and the volume of data increase, traditional caching algorithms often become less efficient, making it more difficult to retrieve content effectively. Large-scale IoT networks, with their diverse devices and vast amounts of data, can overwhelm conventional caching systems. Researchers, including Zhang et al. [99], Kurita et al. [100], Liu et al. [101], Wu et al. [106], and Wang et al. [107], emphasize the necessity for scalable content distribution solutions that can efficiently manage growing network traffic and data loads.
Adaptability is a key challenge in the development of IoT caching strategies. Caching systems must be able to respond to real-time changes in content demand and varying network conditions, requiring solutions that can adjust dynamically. However, many traditional caching approaches are based on static models that assume relatively stable patterns of content access. This can lead to inefficiencies when demand fluctuates. According to Xiaoming et al. [105], Zhang et al. [110], and Liu et al. [116], numerous existing frameworks struggle to adjust to evolving user needs or network conditions, resulting in lower cache hit rates, increased delays, and suboptimal resource utilization. Therefore, implementing adaptable caching mechanisms is critical for improving performance in dynamic IoT environments.
Computational complexity presents a significant challenge for IoT caching strategies, particularly for those that incorporate resource-intensive techniques like deep learning or reinforcement learning. These algorithms often require considerable computational resources and memory, which may not be available in resource-limited IoT devices. For example, approaches such as DRL and deep Q-learning necessitate extensive processing power for both training and deployment, making them unsuitable for many low-power IoT devices Zhang et al. [109], Xu et al. [112]. Moreover, the high computational load associated with these models can cause delays, negatively impacting the system's responsiveness in real-time applications.
The key lesson learned from the reviewed studies is that effective IoT caching strategies must overcome several challenges, including scalability, computational complexity, and security. Caching systems must efficiently handle the increasing volume of data traffic and the growing number of devices while maintaining performance. Moreover, these systems need to be adaptable to real-time fluctuations in network conditions and content demand. While integrating advanced techniques like deep learning can enhance performance, it is crucial to balance these approaches with the resource limitations inherent in IoT environments to ensure their practical feasibility.
5.2 Internet of Vehicles (IoV)
The IoV refers to the network of interconnected vehicles that communicate with each other and with roadside infrastructure to enhance transportation systems. Figure 9 details caching in IoV, involving data servers that own and store data contents, Local Name Service Servers (LNSS) that cache domain names, and a set of NDN entities that forward frequent data chunks to roadside units. These roadside units, devices deployed along roadsides to enable communication between vehicles and the network, deliver data to vehicles with minimal delay. This setup significantly improves communication efficiency within the IoV framework [117, 118].
-
Caching Frameworks Based on ICN Networking
Zhang et al. [116] present a content caching strategy for the IoV that uses Heterogeneous Information Networks (HIN) to address data complexity and the rising demand for popular content. Their method predicts user interest, enabling dynamic caching that reduces network traffic and improves both QoS and QoE. Experiments demonstrate that their approach outperforms traditional methods in content prediction, user satisfaction, and network load reduction, offering better performance, scalability, and lower delays while minimizing reliance on edge computing.
Yang et al. [119] propose an NDN-based framework for CV applications, addressing scalability issues caused by rapid mobility and a large number of vehicles. They introduce the hierarchical hyperbolic NDN backbone (H2NDN), which organizes geographic locations into a hierarchical namespace and router topology. Within this hierarchy, traffic is redirected to higher-level routers, optimizing Interest packet forwarding with static FIB entries. These features significantly improve the efficiency and scalability of the H2NDN backbone, making it well-suited for CV applications.
Chen et al. [120] address the limitations of traditional TCP/IP stacks in IoV scenarios by focusing on spatial-temporal characteristics for data caching in Vehicular Named Data Networking (VNDN). They classify data into emergency safety, traffic efficiency, and entertainment messages, using these categories to determine caching decisions. Their expanded simulation platform shows that their caching strategy outperforms others in terms of hit ratio, hop count, and cache replacement times.
Chen et al. [121] enhance the security of the IoV system by leveraging Named Data Networking (NDN) and Blockchain technology. They utilize Communicating Sequential Processes (CSP) to model the system, ensuring critical properties such as deadlock avoidance, data availability, and protection against fake PIT deletions and Content Store (CS) pollution. These properties are rigorously validated through the Process Analysis Toolkit (PAT). To further reinforce security, the authors integrate Blockchain technology to safeguard the system against unauthorized modifications, ensuring data integrity through immutable transactions. This Blockchain integration fortifies the system against security breaches by providing a tamper-resistant layer that guarantees the authenticity of data exchanges within the NDN-based IoV architecture, enhancing the overall system's resilience to malicious attacks.
Saleem et al. [122] address challenges in VANETs, including communication reliability, security, and scalability. They propose a blockchain-based solution for secure V2V communication, referred to as BC-V2V. This method utilizes a K-Means dynamic clustering algorithm for cluster formation and an NDN approach for efficient content placement, ensuring secure and reliable content distribution. The blockchain framework protects the data exchanged between vehicles, preventing unauthorized access and ensuring the integrity of communications, making it a secure and reliable solution for content distribution in VANETs.
Amadeo et al. [123] propose the Freshness and Popularity Caching (FP-Caching) method to address the challenges of caching transient content in VNDN. This approach focuses on real-time data, such as road traffic updates and parking availability, which quickly lose relevance. While freshness is crucial for caching decisions, especially in safety and non-safety applications, the authors emphasize the importance of considering content popularity, particularly in cases of skewed distribution, such as Zipf-like behavior. This dual focus on freshness and popularity is key to optimizing caching strategies and improving VANET performance.
Zafar et al. [124] propose a hierarchical context-aware content-naming (CACN) scheme for NDN-based VANETs, enabling efficient content forwarding and caching using information from content names. The scheme simplifies communication and storage through an innovative coding technique and reduces latency with a decentralized context-aware notification (DCN) protocol. The DCN protocol broadcasts event notifications, prioritizing vehicles based on location and proximity. Simulations show the scheme's effectiveness in improving VANET communication.
Javed et al. [125] propose a solution for managing large-scale data generation and dissemination in IoV by introducing Vehicular Edge Computing (VEC). In this framework, Road Side Units (RLUs) act as edge servers for caching and task offloading, addressing the increased demands of vehicular applications. The approach includes a task-based architecture for content caching, focusing on content popularity prediction, cache placement, and retrieval.
Ismail et al. [126] propose a proactive caching scheme to reduce latency and improve service quality by utilizing local caches at both the vehicle and Roadside Unit (RLU) layers. This scheme uses high-rate data transmission in vehicular networks to enhance caching efficiency and minimize data costs. The study explores three scenarios: non-cooperative vehicles, cooperative vehicles, and RLU-covered areas, formulating caching placement as an optimization problem to minimize retrieval time.
-
Caching Approaches Based on Deep Learning
DL has emerged as a powerful solution to address these challenges. IoV applications heavily rely on caching, AI in edge networking, and computing to enhance their functionalities. To tackle these challenges, Li et al. [127] present a study introducing an ICN framework tailored specifically for IoV applications. This framework incorporates a novel deep Q-Learning (DQL) algorithm designed to meet user requirements and optimize caching outcomes, thus enhancing edge service efficiencies. The proposed algorithm shows promising results, contributing significantly to improved environmental learning within the IoV context.
Wang et al. [128] introduce the Cooperative Caching Strategy with Content Request Prediction (CCCRP) to reduce data traffic and improve content request responses in the IoV. The strategy clusters vehicles using the K-means method and predicts content requests using Long Short-Term Memory (LSTM) networks based on historical data. A reinforcement learning method is then applied to optimize caching decisions, enhancing the Quality of Service (QoS) for vehicle requests.
Xu et al. [129] emphasize the need for efficient content processing in the IoV context, particularly for smart city applications. They suggest using Edge Servers (ESs) to ensure quick service delivery and minimize latency for vehicular applications. However, repetitive processing of the same content for multiple users leads to resource inefficiency. To address this, they propose an edge content caching framework for smart cities, integrating RSUs and BSs with ESs. This framework uses a deep learning model, the spatiotemporal residual network (ST-ResNet), to predict traffic flow and apply probability theory to forecast future service demands.
Xu et al. [130] address the cooperative content caching problem using a Constrained Markov Decision Process (CMDP), focusing on content transmission mode and cache replacement to minimize latency. The approach employs Multi-Agent Deep Deterministic Policy Gradient (MADDPG), a Graph Attention Network (GAT)-based aggregator, and a hard-attention collaborator selector to optimize caching. Experimental results show that GAMA-cache outperforms other algorithms, improving service latency and content delivery success rates in real-world datasets.
-
Caching Approaches Based on Machine Learning
Yu et al. [156] propose the “P2P-FL” federated learning framework for predicting content popularity in the IoV, where vehicles collaboratively update machine learning models. They introduce a dual-weighted model aggregation scheme to minimize the impact of slow vehicles, improving model accuracy. To address privacy, they incorporate a variational autoencoder, which anonymizes data and ensures that only aggregated model updates are shared, preserving confidentiality while enhancing content prediction performance.
Kaci et al. [131] present ROOF-based Named Data Vehicular Networking (NDN) tailored for IoV, featuring intelligent Named Data Caching (iNDC). This machine-learning-based technique predicts content request rates and optimizes caching by retaining popular content on roadside units. iNDC also forecasts storage capacity needs for these units. Performance evaluations reveal that linear and ridge regressions excel at content popularity prediction, while k-Nearest Neighbors offer superior accuracy in predicting the capacity of new roadside units.
Herouala et al. [132] introduce the CaDaCa framework, which leverages data classification techniques. By analyzing real-time user browsing behavior, CaDaCa enhances caching decisions, leading to improvements in cache hit ratio, hop reduction, and overall caching efficiency. In comparison to traditional caching algorithms, CaDaCa exhibits superior performance. Its dynamic adaptation to changing user traffic patterns through data classification ensures continuous optimization of cache management, resulting in more efficient content retrieval and reduced network overhead in NDN-based environments.
Dutta et al. [140] enhance ICN performance in vehicular networks by tackling content availability and redundancy. They use the Monte Carlo Tree (MCT) algorithm for data retrieval and evaluate caching schemes like Level Copy Down and Cache Less for More. Performance evaluations in the ns-3 simulation environment demonstrate improvements in latency, hit ratio, throughput, and overhead metrics, showing the effectiveness of their approach in optimizing ICN caching strategies for better network efficiency in vehicular environments.
-
Caching Techniques Based on Optimization Applications
Gupta et al. [133] propose an innovative caching strategy to address challenges in vehicular networks, such as limited cache capacity and secure data transfer. Their approach uses a classified scheme, where selected edge nodes store data, and employs a two-level design with the Weighted Clustering Algorithm (WCA) to choose cache heads. Non-Negative Matrix Factorization (NMF) predicts consumer preferences for real user approval on edge nodes. Implemented in Matlab, the method improves cache hit ratio, reduces network delay, and minimizes data loss, making it suitable for the dynamic nature of vehicular networks.
Lam et al. [134] integrate software-defined edge techniques with Unmanned Aerial Vehicles (UAVs) for efficient multimedia content delivery, focusing on caching, resource allocation, multicasting, and 3D trajectory optimization. A service time-aware caching and power allocation (TCP) problem is formally defined and solved using modified genetic algorithms (mGA) to optimize content caching strategies, power distribution for multicast transmissions, and UAV waypoint planning, subject to strict constraints on storage, power, and service time. Simulation results demonstrate that the TCP method significantly enhances network throughput, minimizes service latency, and improves resource utilization efficiency in UAV-assisted content delivery systems (Figure 10).
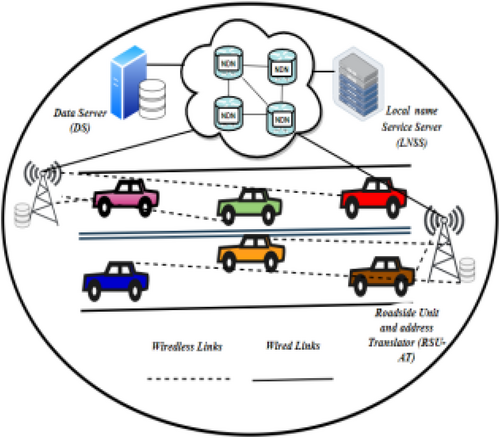
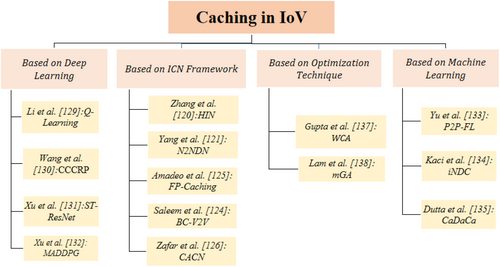
Summary and Lesson Learned
Table 4 summarizes the caching frameworks and algorithms utilized in IoV applications, detailing the specific caching mechanisms employed in each study. It provides a concise description of the decision-making processes for each Information-Centric IoV framework and highlights the key objectives of the respective studies. By offering a structured overview, it aims to facilitate a clear understanding of the various caching approaches, enabling easier comparison and analysis of their benefits and limitations.
| References | Method name | Caching mechanism | Objectives | Limitations | Category |
|---|---|---|---|---|---|
| [133] | WCA | Explicit cooperative | Design and assess a supportive caching framework with a classified scheme and WCA (Weighted Clustering Algorithm) to optimize cache performance in vehicular networks | The effectiveness of the caching structure may be influenced by factors such as network congestion and fluctuating vehicular traffic patterns | Optimization approach |
| [127] | Q-learning | On-path & cooperative | Optimizing caching and enhancing edge services in IoV through deep Q-learning in an Information Centric network | Complexity and computational overhead of deep Q-learning in resource-constrained IoV environments | Deep learning |
| [125] | VEC | Cooperative (implicit), & on-path | Design a task-based architecture for content caching that optimizes popularity prediction, cache placement, and retrieval in vehicular applications | Implementation complexity and resource demands in task-based content caching architecture for Vehicular Edge Computing (VEC) | ICN |
| [119] | H2NDN | Cooperative & on-path | Proposing a hierarchical hyperbolic NDN architecture (H2NDN) to enhance scalability and efficiency in supporting Connected Vehicle (CV) applications | Reliance on static FIB entries for Interest packet forwarding may be challenged by dynamically changing network conditions | ICN |
| [128] | CCCRP | Implicit & on-path | To develop a Cooperative Caching Strategy to reduce content acquisition delay and enhance Quality of Service (QoS) for vehicle requests | Using historical data for prediction in CCCRP may limit its accuracy in rapidly changing IoV environments | Deep learning |
| [131] | iNDC | Cooperative (implicit), & on-path | Leveraging Machine Learning techniques for efficient content caching and storage management in ROOF-based Named Data Vehicular Networking (NDVN) | Difficulty in generalizing machine learning algorithms performance across diverse edge caching nodes and environmental conditions | Machine learning |
| [129] | ST-ResNet | On-path, & cooperative | Develop an edge content caching framework using RSUs, BSs, and ESs, integrating deep learning for traffic flow prediction and future requirements forecasting | Computational complexity of deploying deep learning models on edge servers | Deep learning |
| [123] | FP-Caching | Implicit & on-path | Optimize content retrieval and VANET performance by balancing content freshness and popularity in VNDN | Managing diverse vehicular data types and balancing freshness with popularity in skewed distributions | ICN |
| [122] | BC-V2V | Cooperative, on-path, & heterogeneous | To develop and evaluate a blockchain-based trustable V2V communications and content placement optimization in VANETs | The complexity and overhead introduced by using blockchain technology in VANETs, which may increase computational and communication costs, affecting system performance | ICN |
| [132] | CaDaCa | Homogeneous, implicit, & on-path | Develop the CaDaCa cache strategy to optimize caching decisions in NDN by classifying data, enabling efficient prediction of user requests | Real-time model updates pose challenges for adapting to dynamic user behavior and traffic patterns, impacting caching accuracy | Machine learning |
| [124] | CACN | Implicit, on-path, & heterogeneous | Develop an NDN-based hierarchical context-aware content-naming (CACN) scheme to streamline communication and storage complexities in VANETs | Heightened overhead from hierarchical context-aware naming may impact scheme efficiency and scalability in large VANETs | ICN |
The rapid growth of Internet of Vehicles (IoV) networks presents significant challenges in terms of scalability and complexity for caching strategies. As the number of vehicles, sensors, and roadside units increases, managing content distribution efficiently becomes more challenging. Conventional caching approaches often encounter difficulties in handling the large volume of data and the diverse array of devices within IoV environments. Researchers like Zhang et al. [116], Yang et al. [119], Liu et al. [127], Wang et al. [128], and Saleem et al. [122] underscore the need for caching solutions that can scale effectively to meet growing demands. The constantly changing and highly mobile nature of IoV, along with fluctuating content request patterns, further complicates scalability issues. This leads to increased latency, lower cache hit rates, and a reduction in overall system efficiency.
Security and privacy are significant challenges in implementing IoV caching strategies, as these systems handle sensitive information such as traffic patterns, vehicle behaviors, and personal user data. Protecting the integrity, confidentiality, and authenticity of cached content while ensuring optimal system performance is essential. Researchers, such as Saleem et al. [122], Amadeo et al. [123], and Chen et al. [121], emphasize the importance of securing cached data against unauthorized access and tampering. However, these security measures often introduce complexities in real-world IoV environments. For example, while blockchain-based solutions can enhance security, they can also cause delays and add overhead, affecting the real-time efficiency of caching systems. Similarly, ensuring secure content distribution in decentralized networks, like NDN, presents additional challenges in maintaining both privacy and performance.
Advanced techniques like deep learning, reinforcement learning, and AI-based models often require significant processing power, memory, and energy, which may not be readily available in the resource-constrained IoV environment. Algorithms such as DRL and LSTM networks, for instance, rely on high computational capacity and memory, making them impractical for IoV devices with limited resources. This limitation can result in delays, reduced network throughput, and ineffective real-time decision-making. Research by Li et al. [127] and Wang et al. [128] highlights the difficulties in deploying deep learning-based caching strategies within IoV networks.
The key lesson learned from the reviewed studies is the necessity for caching strategies that are scalable, efficient, secure, and adaptable to real-time constraints. Effectively managing dynamic content requests in an IoV environment requires innovative solutions that balance performance with computational efficiency. Security is also paramount, as protecting sensitive data in a decentralized and highly mobile network presents unique challenges. Thus, IoV caching strategies must integrate scalable, secure, and resource-efficient approaches to optimize content delivery and overall system performance.
5.3 Mobile ICN
-
Caching Approaches Based on Machine Learning
Chen et al. [138] propose an adaptable model for predicting content popularity and modeling content requests by utilizing network features to capture content similarity through a multilevel probabilistic model. The method incorporates Bayesian Learning (BL) to infer model properties even with limited request data. This approach significantly improves content delivery, achieving an impressive 90% hit ratio in a case study focused on video prefetching. The work highlights the synergy between AI and MEC, contributing to optimized content delivery and enhanced user experience.
Sethumurugan et al. [139] propose a machine learning-based cache replacement strategy for MEC, utilizing RL to train a last-level cache (LLC) replacement policy. The approach leverages readily available LLC features without modifying the processor's control and data paths. The trained policy is analyzed with domain knowledge to optimize key features and interactions. The resulting Reinforcement Learned Replacement policy outperforms traditional methods like LRU and DRRIP in benchmark tests.
Dutta et al. [140] propose a method to improve content retrieval in ICN by predicting cache locations for Interest packets. They utilize a Support Vector Machine (SVM) algorithm to predict cache locations based on a simulation dataset. The prediction accuracy of different kernel methods is compared, and simulation results validate the effectiveness of the proposed approach. This study underscores the potential of machine learning in optimizing content retrieval strategies in ICN environments, demonstrating promising results for enhancing retrieval efficiency.
-
Caching Approaches Based on Deep Learning
Guo et al. [141] propose the QoS-DQN method, which integrates Quality of Service (QoS) optimization with deep-Q-network (DQN) for dynamic resource allocation and edge caching. This approach efficiently groups multimedia application packets into QoS flows, enabling optimized content caching at the network edge for low-latency delivery. What makes this method particularly adaptable is the use of reinforcement learning via DQN, which allows the system to adjust in real time to changes in network conditions and user demands. As mobile devices or vehicles shift between different network cells, causing fluctuations in network topology, QoS-DQN can dynamically reallocate resources, ensuring high-demand content is available at the edge. The key advantage of this approach is its ability to learn from past experiences, enabling it to continuously refine its caching decisions based on real-time data, including traffic patterns, content popularity, and network loads.
Wang et al. [142] present the DECOR scheme, which utilizes advanced Deep Reinforcement Learning (DRL) techniques to enhance caching efficiency and boost user experience. Initially, DECOR learns caching policies from a fixed dataset, providing it with an early understanding of content preferences and network behaviors. However, the key feature of DECOR lies in its capacity to dynamically adapt to real-time conditions by framing the cache replacement problem with a focus on minimizing delay. This capability allows the system to continuously adjust and optimize its caching strategies in response to fluctuating user demands and evolving network conditions. The system's ability to modify its caching decisions based on live inputs makes it highly versatile, especially in settings with rapidly changing network topologies, such as IoV or mobile networks, where users and devices are consistently on the move. As the network topology shifts and user demands vary, DECOR's online DRL model enables it to quickly adapt, ensuring that content is always stored at the most effective locations, reducing latency, and boosting overall performance.
Saputra et al. [143] present two proactive cooperative caching techniques under the PCC-Caching framework. The first method relies on a centralized content server to forecast content demands across various Edge Nodes (ENs), allowing for the early caching of content in locations predicted to experience high demand. However, this centralized approach poses challenges in terms of privacy and communication overhead, as it necessitates the aggregation and processing of large datasets from multiple nodes within the network. To overcome these limitations, the second strategy utilizes a Distributed Deep Learning (DDL) framework, where the content server gathers trained models from mobile edge nodes, combining them into a global model that is continually updated and redistributed. This distributed method reduces the amount of communication required and alleviates privacy concerns by keeping data at the local level. Moreover, it improves the system's adaptability to real-time changes in user preferences and network topology by enabling the system to learn and adjust dynamically based on distributed data.
Khanna et al. [144] tackle the issue of optimizing content delivery in Mobile Edge Computing (MEC) systems, which face challenges due to the dynamic nature of user mobility and fluctuating content demand. To address these issues, they propose the Federated Graph Reinforcement Learning (CFGRL) approach, which integrates graph neural networks, federated learning, and DRL. The use of graph neural networks allows the system to better understand the complex interconnections between network nodes, improving the accuracy of caching decisions. Federated learning preserves user privacy by enabling model training on distributed devices without sharing sensitive data, while DRL helps the system adjust its strategies in response to real-time shifts in network conditions and user behavior. By continuously tracking content popularity and adjusting caching strategies accordingly, CFGRL optimizes content delivery, reduces latency, and ensures privacy, making it highly effective in handling rapidly changing network topologies and fluctuating user demands.
-
Caching Techniques Based on Optimization Applications
Cao et al. [145] introduce the Cooperative MEC Caching (CMCC) approach to enhance caching efficiency by optimizing both computational and communication resources. Their method integrates nearby helper nodes to offload computational tasks, thereby improving caching performance in vehicular networks. By applying joint optimization techniques, they developed an efficient algorithm that delivers optimal solutions, particularly in partial offloading scenarios. Numerical results highlight the benefits of this cooperative scheme, demonstrating significant improvements in MEC performance within vehicular environments.
Ji et al. [146] propose the Hybrid Offloading and Cooperative Energy Efficiency (HO-CEE) method, which includes two offloading schemes using Hybrid Access Points (HAP). The first offloads tasks to the edge cloud for energy optimization via caching, while the second employs cooperative communication, with a nearer user relaying tasks from a farther user, enhancing Energy Efficiency (EE). Simulation results confirm that the cooperative scheme outperforms the noncooperative scheme, significantly improving EE and mitigating the near-far effect.
Kim et al. [147] propose the Mobile Edge Computing Caching System (MECCS), designed to optimize cache hits for popular video content in edge servers. Their approach addresses limitations in Video-on-Demand caching by incorporating a request model that accounts for Short-term Time-Varying (STV) popularity in live streaming. Using an exponential distribution for request rates, it improves cache hit rates and reduces backhaul traffic. Experimental results show MECCS's superiority over existing methods, particularly in live-streaming scenarios.
Li et al. [148] introduce the Delay Control Strategy Joint Service Caching and Task Offloading (DCS-OCTO) algorithm, which facilitates random online service caching without requiring prior knowledge of service popularity. The algorithm optimizes system delay while adhering to energy consumption constraints in MEC systems. Simulation results demonstrate that DCS-OCTO outperforms other algorithms in minimizing delay and energy consumption while considering access point storage and energy limitations.
Zhang et al. [149] propose the OCP-SBS method for large-scale user-centric mobile networks. Their approach jointly optimizes content placement, Small Base Station (SBS) clustering, and bandwidth allocation while considering radio resource constraints and network variability. This method minimizes file transmission delay and enhances network efficiency, achieving delay-optimal SBS clustering for cooperative caching.
Wang et al. [150] introduce the Joint Transmission and Cache (JTC) scheme to address backhaul bandwidth consumption in MEC servers. They consider video popularity and quality in their analysis, integrating Adaptive Bitrate (ABR) technology to dynamically adjust video bitrates based on network conditions. This approach maximizes system revenue while accommodating differentiated video quality requests, effectively balancing video popularity and quality to optimize caching strategies.
Ansari et al. [151] propose a Mobile Edge Internet of Things (MEIoT) framework aimed at enhancing the mobile user experience by optimizing caching. This framework integrates fiber-wireless technology, cloudlets, and software-defined networking to bring computing and storage resources closer to mobile IoT devices. By connecting IoT devices to proxy Virtual Machines (VMs) in nearby cloudlets, it enables real-time data caching and retrieval. To further reduce delays and energy consumption, the framework incorporates dynamic proxy VM migration methods, ensuring more efficient resource utilization and significantly improving overall performance (Figure 12).
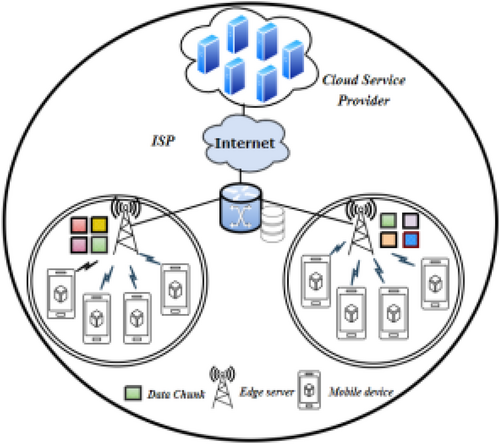
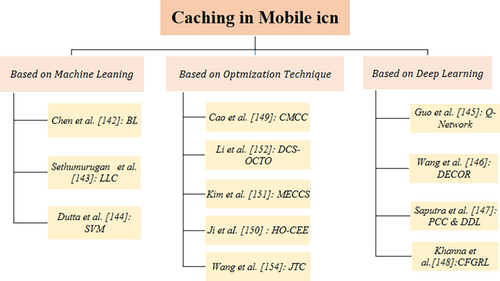
Summary and Lesson Learned
Table 5 provides an insightful overview of the various caching frameworks and algorithms used in mobile applications. It highlights the distinct caching methods employed in each study and offers an explanation of the decision-making processes in Information-Centric mobile caching networks. Additionally, the table underscores the main objectives of each study, providing a well-structured summary that facilitates the comparison and understanding of the mobility-based caching approaches.
| References | Method name | Caching mechanism | Objectives | Limitations | Category |
|---|---|---|---|---|---|
| [145] | CMCC | Explicit, & off-path | Enhance MEC performance by integrating computation and communication resources among nearby helper nodes through joint optimization techniques | Increased complexity in coordinating multiple helper nodes within MEC, potentially introducing overhead | Optimization approach |
| [138] | BL | Implicit cooperation | Demonstrating the collaboration between AI and MEC to optimize content delivery and enhance user experience | The model's generalization may be limited, leading to biased predictions in diverse environments | Machine learning |
| [146] | HO-CEE | Off-path, cooperative, & heterogeneous | Optimize energy efficiency and caching effectiveness in wireless-powered Mobile Edge Computing (MEC) systems | The schemes may not perform optimally in real-world scenarios with unpredictable network conditions | Optimization approach |
| [147] | MECCS | Cooperative, & off-path | To maximize cache hits for multiple live channels across collaborative edge servers in Mobile Edge Computing (MEC) environments | Generalizability of MECCS performance beyond specific experimental conditions may be limited | Optimization approach |
| [140] | SVM | Off-path, implicit, & heterogeneous | To leverage ML for optimizing content retrieval in mobile ICN environments through cache location prediction using SVM | Reliance on simulated data for SVM model training may not fully capture real-world complexities in ICN environments | Machine learning |
| [148] | DCS-OCTO | Explicit, & on-path | To balance average time delay and energy consumption in a three-layer Mobile Edge Computing (MEC) system | Implementing random online service caching without prior knowledge in dynamic networks may pose challenges | Optimization approach |
| [149] | OCP-SBS | Off-path, & implicit | Optimize content placement and bandwidth allocation in mobile networks for reduced file transmission delay by leveraging cooperative caching | Achieving delay-optimal SBS clustering may be challenging in heterogeneous and unpredictable networks | Optimization approach |
| [142] | DECOR | On-path & implicit cooperative | DECOR aims to enhance cache performance and improve user experience in mobile networks by utilizing advanced Deep Reinforcement Learning (DRL) techniques | Computational complexity in implementing advanced DRL techniques in mobile network environments may hinder real-time responsiveness and scalability | Deep learning |
| [150] | JTC | Explicit, heterogeneous, & on-path | To design a comprehensive scheme maximizing system revenue while considering resource limitations and differentiated video quality requests | Managing resource limitations and varying video quality requests efficiently poses a limitation | Optimization approach |
| [143] | PCC & DDL caching | Explicit cooperative & on-path | To enhance content demand prediction accuracy in Mobile Edge Computing (MEC) networks using proactive cooperative caching approaches | DDL-based framework complexity could limit real-time updates across mobile Edge Networks | Deep learning |
One of the key challenges that emerges from the studies is the growing complexity of coordinating multiple helper nodes, which can lead to additional overhead and complicate system management. As the number of edge nodes increases, it becomes more difficult to ensure efficient communication and resource allocation across the network. Effective coordination of these nodes is vital for enhancing caching performance and energy efficiency. However, as the system expands, managing these interactions demands more resources, further complicating the process [145, 147-149] illustrate the challenges posed by integrating multiple edge devices.
Another significant challenge in achieving optimal content delivery and caching performance in mobile networks lies in the reliance on static models and simulations, which struggle to capture the dynamic nature of real-world environments. For instance, machine learning-based approaches to cache location prediction often use static data for training, which limits their flexibility to adjust to fluctuating user demands, varying network conditions, and the mobility of devices. This limitation restricts their ability to perform well in real-time, leading to inconsistent performance and challenges in maintaining accuracy and efficiency in dynamic mobile edge environments [140], [142], and [146].
In conclusion, the key lesson learned from these studies is the necessity for adaptive and flexible caching strategies that can address the complexities of real-world mobile networks. The solutions must be able to handle the fluctuating demands of users, resource constraints, and constantly changing network conditions. Striking a balance between sophisticated algorithms and practical implementation is essential for enhancing the scalability, efficiency, and overall performance of MEC systems.
5.4 Edge Computing
-
Caching Frameworks Based on ICN Networking
Ullah et al. [154] propose Proactive Name-Based Content Prefetching (PNCP), a strategy that integrates ICN with EC to enhance content distribution. By proactively fetching dynamic content and utilizing ICN data structures like the CS, PIT, and FIB within the. NET framework, PNCP improves data locality and reduces network bandwidth demands. Experimental results show PNCP achieves higher cache hit ratios and lower delays, outperforming conventional edge systems and prior ICN approaches.
Wang et al. [155] propose the NDN-based IoT Edge (NIoTE) framework to enhance data communication efficiency in IoT edge environments. NIoTE integrates IoT with edge computing and clustering techniques to address the resource constraints of IoT devices. Through clustering, the framework enables resource sharing, collaborative data collection, request aggregation, and the establishment of the FIB. Its modular architecture ensures seamless integration with existing IoT infrastructures, supporting rapid deployment and scalability across diverse IoT environments. Experimental results confirm the effectiveness of NIoTE, highlighting substantial reductions in data communication latency and costs.
-
Caching Approaches Based on Machine Learning
Yu et al. [156] propose a Federated Learning-based Proactive Content Caching (FPCC) scheme. This scheme addresses the challenges of predicting file popularity amidst fluctuating trends and limited cache capacity by employing privacy-preserving federated learning, which aggregates user-side updates to build a global model. Using hybrid filtering with a stacked autoencoder (SAE), FPCC identifies and selects popular files for caching. Experimental results demonstrate that FPCC not only enhances cache efficiency compared to traditional algorithms but also ensures robust data privacy.
Fan et al. [157] introduce Popularity-aware cache (PA-Cache), a system designed to adapt to sudden surges in requests, which is essential due to the smaller cache sizes in edge networks. Unlike previous approaches, PA-Cache leverages a comprehensive set of content features to dynamically predict time-varying content popularity. To reduce the computational overhead of conventional DNNs, PA-Cache begins with a shallow network for rapid convergence, later transitioning to more robust DNNs as request volumes increase. This approach ensures both scalability and computational efficiency.
Cui et al. [158] propose CREAT, a system that integrates IoT devices, edge nodes, remote cloud, and blockchain to improve data processing, caching, and security in IoT environments. CREAT uses federated learning to allow edge nodes to train models locally without uploading sensitive data. To address communication bottlenecks, it employs techniques like K-Means for identifying important gradients and clustering-based quantization to reduce transmission data volume. Experimental results show that CREAT enhances cache hit rates and reduces data upload time, improving overall content caching efficiency.
-
Caching Approaches Based on Deep Learning
Ndikumana et al. [159] propose Deep Infotainment Caching (DIC), a deep learning-based approach for efficient edge caching in self-driving cars. DIC predicts cached content and vehicle proximity to multi-access edge computing (MEC) servers. The method includes content prediction models, a communication model for retrieval, a caching model, a computation model for serving content, and an optimization problem to minimize downloading delays. Simulation results show a 97.82% prediction accuracy for cached content and highlight significant delay reduction.
Kang et al. [160] propose Priority-Based Optimal Cache Placement (POCP), an ICN caching scheme that integrates content popularity and priority. Using a seq2seq LSTM model, POCP predicts content requests and communicates these predictions to the SDN controller, which optimizes content placement in MECs and core routers. This minimizes delivery costs while ensuring high QoE for prioritized content. Performance evaluations show POCP outperforms traditional caching schemes in terms of QoE satisfaction, cost efficiency, and overall effectiveness.
Zhu et al. [161] introduces the Edge-Graph Cache Replacement (EGCR) method, which utilizes a graph-based representation of cache access data and incorporates Graph Neural Networks (GNNs) for cache replacement, enabling dynamic adaptation to complex access patterns in real-time. GNNs model the relationships between cache data and access sequences as graph structures, capturing both spatial and temporal dependencies within the data. This enables the system to optimize cache decisions by learning from intricate patterns in access behavior. The approach significantly improves the Cache Hit Ratio, adapts to fluctuating workloads, and outperforms conventional cache replacement strategies.
-
Caching Techniques Based on Optimization Applications
Liu et al. [162] propose the Optimized Data Caching Model (ODCM), which integrates the benefits and costs of data caching while considering varying data popularity. The model formulates the caching problem in edge computing as an integer programming (IP) problem and uses the Page-Hinckley-Test (PHT) to assess data popularity. An approximation approach is introduced to efficiently find near-optimal solutions, aiming to optimize the service provider's revenue, especially in large-scale scenarios, with a detailed analysis of the approximation ratio.
Xia et al. [163] propose a solution to the collaborative edge data caching (CEDC) problem in edge computing environments, where edge servers at base stations face resource constraints. They model the CEDC problem as a constrained optimization issue from the app vendor's perspective and prove its NP-completeness. To address this, they introduce an online algorithm, CEDC-O, with proven performance bounds. The algorithm efficiently solves the CEDC problem across multiple time slots without requiring future information. Extensive simulations using real-world data show the algorithm's effectiveness in optimizing data caching in edge computing environments.
Xia et al. [164] address the NP-completeness of the Edge Data Caching (EDC) problem with two approaches: IPEDC, an optimal solution using Integer Programming for precise caching strategies, and AEDC, an approximation method for large-scale scenarios that balances solution quality and efficiency. Their extensive experiments show that IPEDC achieves optimal solutions, while AEDC efficiently handles large-scale challenges, outperforming four representative methods.
Xia et al. [165] introduce the Data, User, and Power Allocation (DUPA3) problem, aiming to optimize data, user, and transmit power allocations to maximize data rates and serve more users. They prove the NP-completeness of the problem and present a potential game framework, showing the existence of a Nash equilibrium. To solve the DUPA3 problem, they propose a decentralized algorithm, DUPA3Game, and evaluate its performance through theoretical and experimental analysis. This work lays the foundation for efficient resource allocation in MEC environments, ensuring fast data retrieval for users.
Gao et al. [166] propose a novel approach for efficient content caching and service placement in edge computing systems. They introduce a class of stochastic models, using Layered Queueing Networks (LQNs) to optimize service placement, followed by an enhanced Joint Caching and Service Placement (JCSP) model that incorporates caching components. Extensive simulations with real-world data show that JCSP outperforms baseline methods, offering a superior balance between system response time and memory consumption (Figure 14).
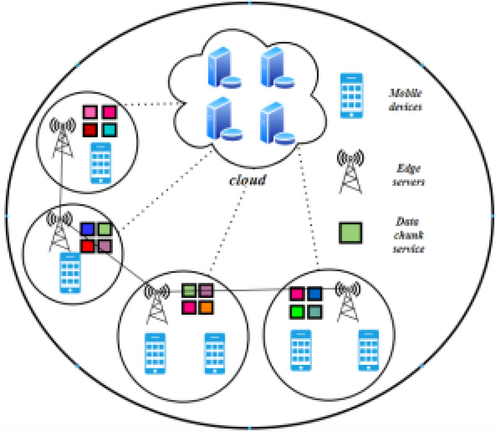
Table 6 provides a detailed summary of the caching frameworks and algorithms used in Edge Computing applications. It describes the caching mechanisms, decision-making processes, and the primary goals of each study, offering a structured overview that makes it easier to analyze and compare the benefits and limitations of these approaches.
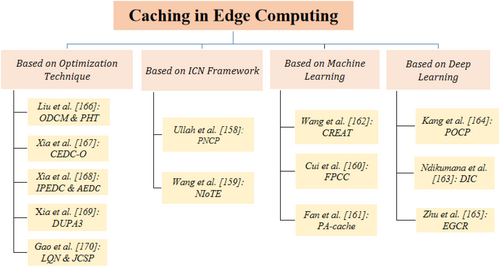
| References | Method name | Caching mechanism | Objectives | Limitations | Category |
|---|---|---|---|---|---|
| [162] | ODCM & PHT | Explicit cooperative | Optimize data caching in edge computing by balancing benefits, costs, ensuring minimal latency, and proposing approximation techniques | Reliance on approximation for near-optimal solutions and NP-completeness of the formulated IP problem pose scalability challenges | Optimization approach |
| [163] | CEDC-O | Cooperative | Model CEDC as an optimization problem, establish NP-completeness, and introduce the CEDC-O algorithm for caching optimization | CEDC-O effectiveness is influenced by real-world dynamics and application diversity, not fully simulated | Optimization approach |
| [154] | PNCP | Cooperative | Integrate ICN with edge computing in RAN via named-based prefetching using core ICN structures to improve cache hits and reduce delays versus traditional edge systems | Limited to name-based content prefetching within the RAN using ICN, potentially restricting its applicability beyond this specific context | ICN strategy |
| [164] | IPEDC & AEDC | Cooperative | Optimize caching strategies to minimize latency, introducing IPEDC and AEDC for balanced and efficient performance at scale | Effectiveness impacted by heterogeneous edge environments, potentially affecting caching applicability | Optimization approach |
| [156] | FPCC & SAE | Implicit cooperative | Develop FPCC using federated learning for accurate file popularity prediction while addressing privacy concerns | Complexity in federated learning implementation and privacy protection across nodes may pose limitations | Machine learning |
| [155] | NIoTE | On-path, cooperative, & homogeneous | Introduce NIoTE framework to address resource limitations, reduce latency, and communication costs through clustering and request aggregation | Performance impacted by clustering algorithm complexity and FIB maintenance overhead | ICN framework |
| [165] | DUPA3 | Cooperative caching | Address DUPA3 problem in MEC with decentralized algorithm DUPA3Game for resource allocation | The decentralized nature of DUPA3 may introduce coordination challenges and overhead, affecting its efficiency at scale | Optimization approach |
| [159] | DIC | On-path | Develop an infotainment caching method using deep learning for self-MEC servers, aiming to optimize content prediction and enhance user experience | Dependence on model accuracy and real-time data availability may limit reliability | Deep learning |
| [166] | LQNs & JCSP | Cooperative | Improve edge computing resource allocation with genetic algorithms and LQNs for accuracy and efficiency | Sensitivity to initial parameters may impact optimization in edge computing | Optimization approach |
| [157] | PA-Cache | Homogeneous, cooperative, & on-path | Develop PA-Cache for edge networks to optimize content caching by adapting to popularity changes and efficiently managing request fluctuations | Potential limitation of PA-Cache, when dealing with extremely large-scale networks and highly dynamic content popularity patterns | Machine learning |
The analysis reveals several challenges affecting the effectiveness of caching strategies. Scalability is a recurring issue, as many caching optimization problems are NP-complete, requiring approximation methods to balance computational demands and practical implementation. For instance, Xia et al. [163] propose strategies to address scalability concerns, but these remain computationally intensive for large-scale systems. Similarly, Cui et al. [158] explore decentralized resource allocation schemes to optimize performance, yet these face challenges with the coordination of multiple edge devices.
Finding the right balance between the complexity of caching algorithms and their practical deployment is another significant concern. Techniques like IPEDC and AEDC [164] show promise in reducing latency and improving performance but often rely on specific edge environment conditions, which can limit their generalizability. Furthermore, methods like PNCP [154] and DUPA3 [165] encounter difficulties when applied to real-world networks, where variability and dynamic conditions pose significant challenges to consistent performance.
The work by NIoTE [155] stresses the need to address resource limitations and latency concerns through clustering and request aggregation. However, this approach introduces overhead in managing FIB structures and cluster dynamics. Similarly, DIC [159], which uses deep learning for content prediction, depends heavily on accurate real-time data, a limitation that can reduce its reliability in dynamic network environments.
These observations highlight the importance of developing flexible caching strategies that can adapt to changing content popularity, network conditions, and resource availability. Approaches like PA-Cache [153], which incorporate mechanisms for real-time adjustments, offer promising solutions to such challenges. By finding a practical balance between algorithmic design and real-world feasibility, future caching strategies can improve scalability and operational efficiency, leading to more robust and effective edge computing systems.
5.5 Fog Computing
-
Caching Frameworks Based on ICN-Networking
In the realm of Fog computing, two notable studies emphasize the effectiveness of ICN caching strategies. Ammar et al. [169] introduce 3Q, a low-complexity caching strategy seamlessly integrated into an ICN-based Edge/Fog architecture. This strategy focuses on efficiently managing service instances and source codes while minimizing overhead, achieving performance levels comparable to optimal strategies. Similarly, Alghamdi et al. [170] propose an innovative Content-Aware CDN (CA-CDN) architecture within Fog computing that leverages ICN principles to optimize content delivery. Their approach integrates a content-aware routing protocol, resulting in significant performance improvements over alternative methods. Figure 16 presents the classifications of caching in Fog Computing.
Ibrahim et al. [171] propose the Fog-based Browser (FBB) framework, which enhances QoS and reduces latency by positioning cloud capabilities closer to end devices. Their approach demonstrates significantly faster web page load times, with experiments showing latency reductions of up to 85%, thus improving the overall user experience. To address security concerns, the FBB framework likely incorporates secure communication protocols, such as encryption for data transmission between edge devices and the cloud, ensuring the confidentiality and integrity of sensitive data.
Hassan et al. [172] propose the Vehicular Multi-layer Caching (VMC) system, which enhances content sharing among vehicles in urban areas by integrating data centers, fog controllers, and edge nodes. Their transient caching approach dynamically adjusts cache offloading based on traffic intensity, optimizing content availability across various fog configurations. To ensure security and privacy, the system uses encryption for secure content transmission and implements access control to restrict data retrieval and storage to authorized users. By relying on localized caching, it minimizes data transfer, reducing the exposure of sensitive vehicle and user information.
-
Caching Techniques Based on Optimization Applications
Shahid et al. [173] introduce the Energy-Efficient Fog Caching (EEFC) approach, which optimizes content distribution in Fog networks by categorizing Fog nodes into clusters and employing caching strategies based on energy and capacity. Gateways manage content requests, forwarding them to the appropriate clusters, while active nodes are selected dynamically. Popular content is cached efficiently, and load balancing algorithms ensure equitable workload distribution. Their approach demonstrates significant reductions in energy consumption and latency compared to traditional methods.
Talaat et al. [174] introduce the Effective Cache Replacement Strategy (ECRS), a load balancing technique for real-time Fog Computing environments. ECRS enhances cache utilization by integrating optimization-based prefetching policies and organizing Fog nodes into regions managed by master nodes. Using a reactive routing protocol and a table-driven strategy, ECRS improves data access, maximizing cache hits and reducing access latency, thereby enhancing Fog computing performance.
-
Caching Approaches Based on Deep Learning
Bhandari et al. [175] developed the Deep Learning Caching Control (DLCC) algorithm to predict content popularity across various categorical classes. Using a 2D CNN model trained on a 1D dataset, the algorithm effectively forecasts the popularity of future data. Based on these predictions, DLCC implements a caching strategy that stores data from the most popular class in the cache memory of nearby Fog Access Points (F-APs). The performance of this caching policy is evaluated using metrics such as DL accuracy, cache-hit ratio, and system delay, demonstrating its effectiveness in optimizing cache resource utilization and reducing latency.
Hasan et al. [176] introduce an innovative content management and placement framework that utilizes Quantum Memory Modules (QMM) for storage. Their Deep Learning-Associated Quantum Computing (DLAQC) framework integrates a DL agent at the network edge with QMM, employing the Self-Organizing Maps (SOMs) algorithm to prioritize and effectively store cached content. Similarly, Huang et al. [177] propose a D2D-assisted fog computing architecture that integrates FL and DNN to adapt to user preferences, aiming to reduce content fetch delays and ensure QoS. They introduce the Cluster-based User Preference Estimation (CUPE) algorithm for optimized content caching placement, leveraging deep learning to enhance caching efficiency and system performance.
-
Caching Approaches Based on Machine Learning
Wu et al. [178] propose a federated learning-based approach to predict content popularity, enhancing content caching in fog computing by incorporating user preferences and contextual data. Their method utilizes the SVRG algorithm for local model training and combines it with DANE for constructing a global model, improving content prediction while reducing computational overhead. In terms of security and privacy, the method leverages federated learning to keep sensitive user data on local devices, avoiding transmission of raw data over the network. Only aggregated model updates are shared, which protects user privacy by reducing the risk of exposing personal information and ensuring secure and efficient content caching.
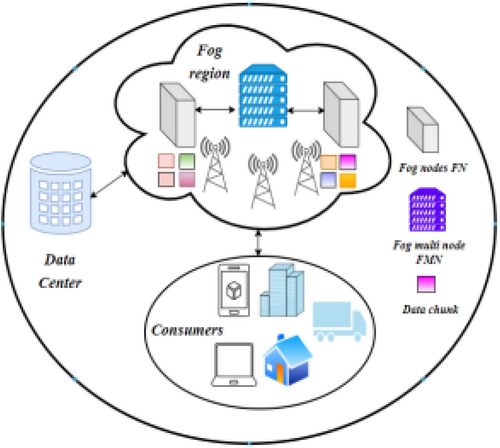
Summary and Lesson Learned
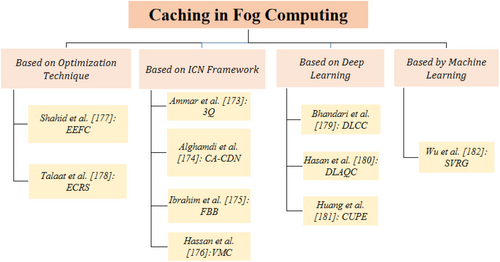
Table 7 summarizes the caching frameworks or algorithms utilized in Fog Computing applications, detailing the caching mechanism employed in each study. The table provides a concise description of the decision mechanism for each Fog-based caching framework. Additionally, the table clarifies the primary objectives of the respective studies. By presenting this structured overview, the aim is to facilitate a clearer understanding of the diverse caching approaches, thereby simplifying comparison and analysis of their respective benefits and limitations.
| References | Method name | Caching mechanism | Objectives | Limitations | Category |
|---|---|---|---|---|---|
| [175] | DLCC | On-path, implicit, & heterogeneous | Formulate a DLCC algorithm to predict content popularity using a 2D CNN model trained on 1D data and optimize caching at F-APs | Data set limitations, network dynamics complexity, and resource constraints at F-Access Points (F-APs) | Deep learning |
| [176] | DLAQC | Implicit, homogeneous, & on-path | Develop an efficient framework for content management and placement in fog networks by leveraging Quantum Memory Modules (QMM) and integrating Deep Learning (DL) | Challenges in integrating deep learning with QMM, including computational complexity and resource requirements, may impact effectiveness | Deep learning |
| [169] | 3Q | On-path, & implicit cooperative | Aimed at efficiently handling caching of service instances and their source codes while minimizing overhead without requiring explicit node cooperation | The performance of the 3Q strategy under varying workload conditions could be a limitation | ICN |
| [177] | CUPE | Cooperative, on-path, & heterogeneous | Propose D2D fog computing with FL and QoS-aware caching, integrate DNNs for local user preference perception, ensuring ID privacy in distributed learning | The scalability and efficiency of the D2D-assisted fog computing architecture may be hindered, especially in addressing the needs of large-scale and dynamic networks | Deep learning |
| [171] | FBB | Homogeneous, on-path, & implicit | Develop a novel CDN architecture within the fog computing environment to enhance content delivery efficiency by capitalizing on the proximity of Fog nodes | The applicability of the Fog-based CDN architecture may be limited by resource constraints or network heterogeneity in real-world deployment scenarios | ICN |
| [173] | EEFC | Explicit, & on-path | Minimize delay and energy consumption in fog network content distribution by clustering nodes based on service type and selecting active nodes based on energy status and capacity | The effectiveness of clustering and node selection strategies may be affected by network topology and node heterogeneity, necessitating additional investigation | Optimization technique |
| [174] | ECRS | On-path, implicit, & homogeneous | Introduce a load balancing technique for real-time fog computing environments utilizing Effective Cache Replacement Strategy (ECRS) and routing | The ECRS approach may introduce computational and memory overhead on Fog nodes, potentially impacting system performance | Optimization technique |
| [178] | SVRG & DANE | On-path, & heterogeneous | Develop a context-aware popularity prediction policy based on federated learning to predict content popularity while reducing computational complexity accurately | The scalability and generalizability of the federated learning-based model integration approach may pose challenges in diverse network environments | Machine learning |
| [170] | CA-CDN | Explicit, homogeneous, & on-path | Develop a fog computing-based CDN framework to enhance Quality of Service (QoS) and reduce latency for cloud services by bringing cloud capabilities closer to end devices | The efficacy of the fog computing-based CDN framework may be constrained by network topology and fog node distribution, potentially affecting its adaptability and performance in varied environments | ICN |
| [172] | VMC | Implicit cooperative | Aimed at developing a comprehensive multi-layer caching system that enhances data availability and communication in vehicular fog computing environments | The system's performance in dynamic and unpredictable scenarios, such as sudden traffic surges or network failures, to ensure its robustness and reliability in real-world deployments | ICN |
In our exploration, strategies like Bhandari et al. [175] DLCC, to cooperative caching strategies like Huang et al. [177] CUPE, which leverage federated learning and quantum memory modules. Despite their potential benefits, each approach faces limitations that must be carefully considered. For instance, while DLCC aims to predict content popularity and optimize caching at fog access points, it faces challenges related to data set limitations, network dynamics complexity, and resource constraints at F-APs. Similarly, CUPE's proposal of D2D fog computing with federated learning and QoS-aware caching may encounter scalability and efficiency issues in large-scale and dynamic networks. Additionally, other mechanisms such as Talaat et al. [174], and Hasan et al. [176], face challenges related to computational complexity, resource requirements, and potential overhead, underscoring the need for comprehensive evaluation and adaptation to real-world fog network environments.
A crucial lesson learned from exploring caching mechanisms in fog computing is the importance of addressing scalability and adaptability concerns. While innovative approaches like DLCC and CUPE offer potential solutions for optimizing caching efficiency, their effectiveness may be hindered by scalability challenges and network dynamics. For example, DLCC's reliance on deep learning for content popularity prediction and caching optimization requires careful consideration of scalability and resource constraints at fog access points. Similarly, CUPE's proposal highlights the need for scalable solutions that can address the needs of large-scale and dynamic networks. By acknowledging these scalability concerns and designing adaptive caching mechanisms, researchers and practitioners can pave the way for more robust and efficient fog computing systems.
6 Comparison with Existing Surveys
This section comprehensively examines current surveys focusing on ICN caching. Our objective, through a thorough exploration of these survey papers, is to identify knowledge gaps and extract collective insights in the field. We emphasize the novelty and key contributions of our review paper within the realm of ICN caching.
Recent literature, such as [179-182] has explored ICN caching solutions within specific applications, discussing and examining their strengths and limitations. While these studies offer valuable insights, they often remain confined to particular domains, lacking a broader perspective on the applicability of different caching strategies. Notably, there is a gap in the literature regarding the comprehensive classification of proposed caching methods based on their distinct mechanisms and a detailed assessment of their potential implications across diverse contexts.
By covering diverse areas and offering insights into various designed caching methods, our objective is to deliver a comprehensive understanding of ICN caching, thereby significantly impacting the ICN caching domain (Table 8).
| References | Topic | Contribution | Remarks | Application |
|---|---|---|---|---|
| [183] | In-network caching in ICN for different applications: a survey | This survey comprehensively reviews recent caching approaches, detailing their concepts, strengths, and limitations in different contexts | This survey's challenge is its limited practical testing, which makes comparing it with other surveys difficult | IoT, IoV, Mobility |
| [184] | A comprehensive survey of ICN: content caching strategies perspective | This survey thoroughly compares and analyzes caching strategies, detailing their purpose, decision-making, differences, advantages, and disadvantages | A survey limitation is the significant focus on caching methods without adequately exploring their application in diverse contexts | ICN |
| [179] | In-network caching in ICN-based vehicular networks | This survey reviews existing ICN caching strategies and replacement policies in vehicular networks and evaluates their performance using ndnSIM in different scenarios | Not examining how caching strategies impact ad hoc Internet of Vehicles (IoV), potentially missing valuable insights about caching performance in larger network environments | Internet of Vehicles (IoV) |
| [180] | A survey of ICN content naming and in-network caching and beyond networks | This survey reviews recent content naming schemes and in-network caching solutions, categorizing them by technologies and principles, and suggests research directions for the community | A survey limitation focuses primarily on content naming schemes and in-network caching, potentially overlooking important aspects of caching in diverse applications | Mobile ICN |
| [181] | ICN challenges and opportunities in service discovery: a survey | This survey outlines the ICN concept and its features. It examines different ICN-based architectures, detailing their strengths, weaknesses, and challenges | A survey limitation is the exclusive focus on discussing the challenges of ICN architectures, which overlooks the significance and importance of in-network caching | ICN |
| [185] | A performance analysis of caching schemes in ICN-based IoT | This survey explores ICN/NDN-based caching strategies for the IoT, analyzing them through simulations to find the best solution | A survey limitation is the absence of comparison to other surveys | Internet of Things (IoT) |
| [186] | A survey of edge caching: key issues and challenges | This survey aims to comprehensively and systematically examine edge caching techniques. It provides an overview of edge caching, highlighting key issues | A survey limitation is failing to categorize caching schemes or techniques into different caching mechanisms | Edge computing |
| [187] | Applying ML techniques for caching in edge networks: a comprehensive survey | This survey examines recent literature and develops a taxonomy of caching strategies driven by machine learning in edge networks | The survey limitation is its concentration on discussing specific types of learning-based caching | Edge computing |
| [188] | Caching methodologies in (CCN): a survey | This survey paper provides an overview of popularity-based caching approaches in information-centric networks in recent years | The survey heavily relies on popularity-based approaches without thoroughly examining their effectiveness or limitations in real-world scenarios | CCN |
| [189] | Machine-learning-based IoT data caching | This survey paper covers caching basics, challenges, recent advancements, and strategies. It explores using machine learning for IoT caching potential | The survey covers basics, challenges, and current methods but doesn't discuss caching mechanisms or algorithms or compare with the latest developments | Internet of Things (IoT) |
| [182] | A survey of deep learning for data caching in edge networks | This survey categorizes content caching problems, reviews deep neural network structures, and compares state-of-the-art DL-based caching strategies | The survey does not compare the current work with the latest developments | Edge computing |
| [190] | Information-centric networking solutions for the IoT: a systematic mapping review | This survey provides a systematic mapping review of ICN-IoT research, focusing on strengths, weaknesses, and open research issues | The survey's limitation is its focus on specific caching schemes, potentially overlooking other relevant approaches in diverse contexts | Internet of Things (IoT) |
| [191] | Convergence of information-centric networks and edge intelligence for IoV | The survey thoroughly explores integrating edge intelligence, including AI and ML, with ICN for IoV solutions | The survey is limited by its lack of comparison with advancements made in recent surveys | Internet of Vehicles (IoV) |
| [192] | A survey of information-centric networking | The survey presents an overview of ICN functionalities: in-network caching, routing, and security, alongside a review of recent related work | The survey is limited by neglecting the impact of in-network caching across multiple prominent applications | ICN |
To the best of our knowledge [183], explores caching approaches across different applications; however, it falls short in assessing these approaches, examining their potential benefits and implications, and benchmarking its findings against established literature in the field of ICN caching. To address these issues, we analyze and detail the potential strengths and implications of various caching methods across different contexts, providing a comprehensive analysis and comparison of existing surveys with our research. Furthermore, this paper also classifies the caching solutions based on their employed caching decisions. Our goal is to facilitate a more comprehensive and detailed understanding of ICN caching by offering extensive coverage, identifying novel areas, and providing insights into performance assessment methodologies, thereby making a notable impact in the ICN caching domain.
7 Performance Assessment
Evaluating the performance of ICN caching is vital for assessing the efficacy of caching strategies across various domains. In the IoT domain, techniques like SCC and PSI4IoT leverage advanced machine learning algorithms to optimize cache utilization, minimize energy consumption, and effectively manage dynamic data and network topologies. SCC achieves this through optimized caching, resource sharing, and node localization, while PSI4IoT enhances security and caching efficiency with secure authentication, Proxy Re-Encryption (PRE), and Hierarchical Identity-Based Encryption (HIBE), ensuring faster and more secure content retrieval in IoT environments.
In the IoV domain, methods like Q-learning and the Weighted WCA optimize cache hit ratio and reduce latency by adjusting cache placement based on real-time traffic and network conditions, improving content retrieval efficiency. VEC and H2NDN enhance throughput and scalability by leveraging edge computing and distributed caching to address vehicular mobility and congestion. Deep Q-learning improves edge service efficiencies and optimizes caching outcomes. A classified caching scheme with NMF predicts user preferences, improving cache hit ratio and reducing delays. Additionally, VEC-based frameworks enhance content retrieval through task-based caching, focusing on popularity prediction and cache placement.
In the MEC domain, strategies like HO-CEE and CMCC improve energy efficiency and caching performance. HO-CEE reduces energy waste through hybrid offloading and cooperative communication, while CMCC enhances caching by optimizing task offloading and reducing network congestion. DECOR, using Deep Reinforcement Learning (DRL), optimizes cache management by predicting content popularity, and SVM improves content retrieval by predicting cache locations. Together, these methods optimize resources, reduce energy consumption, and boost content delivery speed.
In Fog computing, methods like DLCC and DLAQC leverage deep learning and quantum memory to predict content popularity, enhancing the cache hit ratio and energy efficiency by prioritizing the most relevant content. Fog-based CDNs, such as FBB and CA-CDN, reduce latency and increase throughput by positioning Fog nodes closer to end devices, improving content delivery speed. VMC and CUPE optimize content caching and placement by dynamically adjusting to traffic conditions and user preferences, thus improving content availability and QoS. These methods collectively optimize resource utilization, reduce delays, and enhance the overall efficiency of content management in Fog computing environments.
The hit ratio indicates how frequently requested content is found in the cache, directly influencing system performance [193]. In the context of ML and DL applications, enhancing the hit ratio involves selecting the right content to cache, ensuring that the most frequently requested data is readily available. By analyzing data request patterns, the system can strategically cache relevant content, which accelerates model training and inference by facilitating faster access to data. In edge computing, this targeted content selection not only reduces miss rates but also minimizes retrieval delays, enabling quicker access to critical information. Therefore, achieving a high cache hit ratio in ICN caching hinges on the ability to dynamically and intelligently determine which content should be cached.
When employing Machine Learning or Deep Learning algorithms to improve cache hit rates, key features such as requested content and request frequencies across different time frames, as well as IoT-specific features like sensor data, device connectivity status, data access patterns, and request frequencies, are provided to the model for training [194]. These features enable the model to predict which data is more likely to be accessed again, allowing it to determine which data should be cached and which should not. By training the model on these datasets, the system can dynamically adjust its caching decisions, optimizing hit rates and minimizing miss rates.
Retrieval Latency
Retrieval latency refers to the time required to fetch content from the cache, which plays a critical role in determining the responsiveness and effectiveness of ICN caching, particularly in real-time applications [195]. Achieving low latency is heavily dependent on selecting the optimal placement for cached content. Proper placement ensures that the most relevant data is quickly accessible, thereby reducing retrieval delays. In edge computing, this optimal placement enables rapid data access, facilitating efficient real-time processing. Similarly, in IoT, it ensures timely data retrieval, supporting effective and prompt decision-making.
By employing Machine Learning or Deep Learning techniques, content placement prediction is influenced by various factors, including the proximity of delivery nodes and data delivery rates. Additionally, IoT-specific features, such as device connectivity status (e.g., Wi-Fi or cellular connection) and network congestion levels (e.g., traffic load, bandwidth utilization), as well as IoV characteristics like vehicle mobility patterns (e.g., speed and direction), are integrated into the prediction model. These features enable the system to predict the optimal placement of cached content, helping minimize delays and optimizing overall system performance.
Cache efficiency refers to the intelligent selection of content and its optimal placement within the network to maximize performance while minimizing resource waste [196]. In IoT, efficient caching enables quick data retrieval, ensuring smooth operation across interconnected devices and networks. Similarly, in IoV, cache efficiency enhances communication between vehicles and infrastructure, leading to safer and more reliable transportation systems. In the context of Machine Learning, cache efficiency is achieved by predicting and selecting the most relevant content to cache. By aligning content placement with network demands and usage patterns, resource consumption is minimized while ensuring that crucial data is readily available when needed. This approach optimizes cache decision-making and network performance, ultimately improving system efficiency across domains.
Energy Efficiency
Energy efficiency in caching aims to reduce energy consumption by making smart caching decisions based on the available network resources, ensuring that energy is utilized effectively when delivering content to users [197]. In IoT, this approach helps lower power usage, leading to longer battery life for devices and enhancing their durability. In edge computing, energy-efficient caching facilitates real-time applications by reducing the overall energy requirements, allowing for high performance without excessive energy demands. In the context of Machine Learning, energy efficiency is realized by forecasting which content is most likely to be requested. By minimizing unnecessary data retrieval and processing, ML algorithms contribute to power optimization, ultimately improving system performance, reducing costs, and fostering a more sustainable network infrastructure. This results in more energy-efficient caching across various domains.
Security
Security in ICN caching is crucial for maintaining data authorization and integrity [198]. In IoT, this involves implementing access controls and cryptographic techniques to prevent unauthorized access and tampering, ensuring secure data transmission between devices. In IoV, security protocols such as encryption, authentication, and intrusion detection safeguard vehicle-to-vehicle and vehicle-to-infrastructure communications, minimizing the risk of malicious attacks. Strengthening security in ICN caching is essential for ensuring proper authorization, protecting data integrity, and upholding the overall reliability and trustworthiness of networks across various domains.
Throughput
Throughput refers to the rate at which data is successfully delivered within a network, and in caching, it is greatly influenced by placing content closer to the end-users or devices [199]. By positioning content nearer to users, delays are minimized, and data transmission speeds are improved. In edge computing, caching data at local edge nodes speeds up access to real-time services, further enhancing throughput by reducing the distance data needs to travel. In IoT, placing cached data closer to IoT devices enhances the efficiency of data retrieval, which is essential for time-sensitive tasks like monitoring or control. Machine Learning optimizes throughput by predicting the most in-demand data and enabling strategic content placement at optimal locations, such as near edge nodes or local servers. Together, these techniques ensure faster and more efficient data retrieval, maximizing throughput across diverse networks.
Table 9 analysis reveals that most research efforts focus on improving key performance metrics such as hit ratios and retrieval delays in decentralized environments. Techniques like PaCC, DPCP, BEACON, CPFC, and DCM, mentioned in Section 3, utilize distributed caching strategies to achieve these improvements. Although these approaches perform effectively in localized decision-making, they encounter significant challenges in terms of scalability, real-time adaptability, and security due to the decentralized nature of caching decision processes. This underscores the need for further exploration of centralized caching techniques, which can provide better control, more efficient decision-making mechanisms, and enhanced security features, paving the way for innovative and impactful future research.
| Author | Year | Tool | Network | Hit ratio | Delay | Cache efficiency | Energy efficiency | Security | Throughput |
|---|---|---|---|---|---|---|---|---|---|
| Amadeo et al. [74] | 2022 | ndnSIM | De-centralized | ||||||
| Amadeo et al. [80] | 2021 | Matlab | De-centralized | ||||||
| Zha et al. [75] | 2022 | Mininet | Centralized | ||||||
| Zhang et al. [114] | 2024 | PyTorch | De-centralized | ||||||
| Lam et al. [134] | 2024 | Python | De-centralized | ||||||
| Amadeo et al. [74] | 2020 | ndnSIM | De-centralized | ||||||
| Liu et al. [85] | 2022 | SPIRENT | Centralized | ||||||
| Asmat et al. [87] | 2020 | Ns-3 | Centralized | ||||||
| Wu et al. [108] | 2022 | Python | De-centralized | ||||||
| Xu et al. [130]. | 2024 | Python | De-centralized | ||||||
| Zhu et al. [161] | 2024 | Tensor Flow | De-centralized | ||||||
| Banerjee et al. [104] | 2022 | ndnSIM | De-centralized | ||||||
| Xinyue et al. [110] | 2021 | Matlab | De-centralized | ||||||
| Wang et al. [128] | 2021 | Matlab | De-centralized | ||||||
| Khanna et al. [144] | 2023 | PyTorch | De-centralized | ||||||
| Ndikumana et al. [159] | 2020 | Python3 | De-centralized | ||||||
| Hasan et al. [176] | 2022 | Google Collab | De-centralized | ||||||
| Wang et al. [142] | 2023 | Python | De-centralized | ||||||
| Gao et al. [166] | 2022 | JMT | De-centralized | ||||||
| Tian et al. [111] | 2022 | PyTorch | De-centralized |
In this research, we extensively investigated the application of deep learning and machine learning techniques for caching across different domains. Methods like DRL, Q-Learning, and Federated Reinforcement Learning, mentioned in Section 4, are designed to improve scalability in content delivery networks. However, these techniques are limited by the absence of real-time experiments. As indicated in Table 9, most deep learning-based caching solutions are developed using Python and PyTorch, typically relying on static or simulated datasets. The lack of real-world data and the absence of real-time testing restrict the practical implementation and thorough evaluation of these methods in dynamic, real-world environments.
To tackle these challenges, it is essential to examine the integration of ICN networks with modern internet frameworks such as Software Defined Networking (SDN). SDN offers centralized control and programmability, enabling adaptive caching and routing decisions that respond to network conditions, traffic, and security requirements. Additionally, SDN can seamlessly integrate with virtualization, which abstracts physical resources, allowing for the creation of flexible, scalable virtual networks. The combination of SDN and virtualization can substantially improve the scalability, efficiency, and throughput of ICN delivery networks, thereby enhancing the user experience.
Furthermore, developing simulation platforms such as ndnSIM, which offer a configurable NDN environment to explore and implement machine learning and deep learning methods, can improve network performance and support real-time testing with innovative technologies.
8 Conclusions
This review thoroughly examines the transformative impact of ICN on network architectures. It highlights the key components of ICN, diverse naming schemes, and various ICN-based content-centric architectures. Caching within the ICN framework is pivotal for achieving enhanced content distribution, optimized data delivery, and reduced server workloads. This paper provides a systematic categorization and analysis of ICN-based caching solutions across various contexts, including IoT, IoV, Mobility, Edge Computing, and Fog Computing, assessing their potential and implications. By offering a comprehensive evaluation of caching methods and algorithms, this review aims to contribute to optimizing data delivery and overall network performance in ICN environments.
Furthermore, the paper emphasizes the need to enhance the experimental validity of existing surveys, particularly concerning centralized caching strategies. Our specific focus is on improving retrieval latency and cache hit rates to address current challenges in the caching domain effectively. This emphasis aims to steer future research efforts towards developing more efficient content distribution mechanisms within ICN networks.
In summary, this paper underscores the pivotal role of caching mechanisms in enhancing content distribution efficiency within ICN networks. It provides a clear roadmap for future exploration and improvements in this dynamic field, thereby paving the way for more streamlined and effective data delivery approaches in the digital age.
8.1 Future Directions
In this survey, I have examined a range of caching techniques within the domains of IoT, IoV, mobility networks, and edge and fog computing, with a particular focus on the application of ML- and DL-based models, ICN frameworks, and optimization models to improve content delivery, network efficiency, and resource management. The survey covers optimized caching strategies, multi-layered architectures, and adaptive algorithms, all aimed at enhancing performance in dynamic and resource-constrained environments.
Looking ahead, one key future direction is the use of hyper-relational interaction modeling for multi-modal trajectory forecasting in intelligent connected vehicles (CV) [200]. This method optimizes caching strategies by examining the interactions between vehicle movements, traffic patterns, and environmental influences. By predicting vehicle trajectories and network conditions in real-time, caching systems can dynamically manage cache placement and prioritize time-critical applications, thereby reducing latency and network congestion and improving overall system performance in IoV and mobility networks.
Another significant avenue is the fusion of hyperspectral and LiDAR data through Vision Transformers [201, 202]. By merging spatial, visual, and sensor data, this technique enhances environmental mapping and localization accuracy. This enables caching systems to better adapt to the specific environmental context, optimizing cache placement and routing decisions. As a result, it leads to faster content access, reduced transmission overhead, and improved network performance in smart cities and mobility networks.
The use of multi-modal deep learning for mobile traffic prediction [203] offers substantial potential for real-time decision-making within caching systems in IoT and IoV networks. By incorporating data from vehicle speed, traffic conditions, weather, and IoT sensors, deep learning models can predict congestion points and optimize content delivery. This flexibility allows caching strategies to adjust dynamically to changing traffic patterns, ensuring more reliable and faster content access in VANETs, smart cities, and IoV networks. Table 10 displays the abbreviations used in this paper.
| Abbreviation | Definition |
|---|---|
| CDNs | Content Delivery Networks |
| P2P | Peer 2 Peer |
| CRs | Content Routers |
| RHs | Resource Handlers |
| NRS | Network Resolution System |
| NDO | Name Data Object |
| DHT | Distributed Hash Table |
| CS | Content Store |
| PIT | Pending Interest Table |
| FIB | Forwarding Information Base |
| NFD | Network Forwarding Daemon |
| CDULG | Content Delivery Upper-Layer Group |
| CDLLG | Content Delivery Lower-Layer Group |
| SDN | Software Defined Networking |
| FNs | Fog Nodes |
| TNs | Transmission Nodes |
| ESs | Edge Servers |
| CN | Central Node |
| RSUs | Roadside Units |
| BSs | Base Stations |
| SBS | Small Base Station |
Additionally, the integration of ICN with SDN [204, 205] represents a crucial future direction. This integration enables a programmable environment for dynamic cache management, optimizing cache placement based on real-time demand and network conditions. It also supports the implementation of advanced security protocols, improving both network performance and resource utilization while enhancing security measures. The synergy between ICN's content-focused design and SDN's flexible, programmable control plane will lead to robust and efficient caching strategies, particularly in the highly dynamic and decentralized settings of IoV, smart cities, and mobility networks.
Author Contributions
Firdous Qaiser: conceptualization; validation; software; writing – original draft. Khoula Said Al Harthy: investigation; validation; formal analysis; visualization; funding acquisition. Mudassar Hussain: conceptualization; methodology; project administration; data curation; writing – original draft. Jaroslav Frnda: conceptualization; validation; software; resources; funding acquisition. Rashid Amin: investigation; writing – original draft; visualization; supervision; resources. Rahma Gantassi: data curation; formal analysis; visualization; investigation; methodology; writing – review and editing. Muhammad D. Zakaria: formal analysis; validation; investigation; data curation; methodology.
Acknowledgments
To be added later.
Conflicts of Interest
The authors declare no conflicts of interest.
Availability of Data and Material
There is no associated data with this submission.
Open Research
Data Availability Statement
Data sharing is not applicable to this article as no new data were created or analyzed in this study.




